What should I do?
-
Hello everyone,
in the sake of my wife I wanted to trade in my 2 Switch Setup to a one Switch Setup.
But I have a question, the switch I got is a MikroTik Switch with installed RouterOS.
Im not very familiar with VLANs but what I know is that I can "split up" one physical connection into multiple. Thats fine but here is my setup:LAN -> Switch -> LAN (Wifi etc.)
VMNET -> Switch -> Server NetI want to archive the same with also the same amount of connections mean I dont want to have one single Connection I want to have 2 to the new Switch.
The MikroTik can use bridging to group some ports together my Idea was to Bridge one 10G port with 4 Others and one 10G Port with 7 Others so I can split them.
I reed somewhere that it would be better to use VLANs but I´m not quite sure how to archive the same setup with VLANs.Someone got some experience here?
Kind regards,
-
@sysadminfromhell said in What should I do?:
The MikroTik can use bridging to group some ports together
Don't know, what they call "bridging" in this context, but there should be an option to segment the switch, so that you can pool some ports to a virtual switch. So the switch would behave like multiple switches in fact.
There is no VLAN needed for this if you connect it with two separate network cables to two pfSense NICs. -
@viragomann yes that’s bridging but I just figured out that only one of these virtual switches can be hardware offloaded / accelerated. Do you have any experience with non hw offloaded virtual switches or similar? I have now the fear that the performance will be really bad in one of the virtual switches. Kind regards
-
@sysadminfromhell
You can configured all ports you want to have within a "virtual switch" as VLAN, so that this VLAN is only inside the switch.This means, say you want to connect ports 5 - 8, set all these ports for tagging incoming packets (PVID) for say VLAN 10 and add them also to VLAN 10 as untagged.
So from outside port 5 - 8 behaves as a separate dumb switch and they are segmented from all other ports.
-
@sysadminfromhell said in What should I do?:
Do you have any experience with non hw offloaded virtual switches or similar
Huh?? Any vlan capable switch can do what you want. Put ports 1,2,3 in vlan X, put 4,5,6 in vlan Y. etc. or port 7, 12 and 24 in vlan Z, etc..
They can all have uplinks to different interfaces in pfsense that are not tagged.
I do this..
Here..
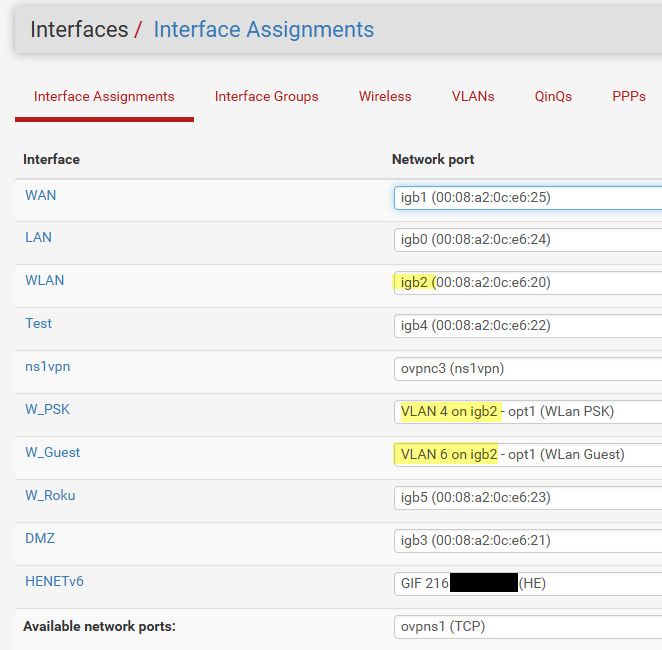
So the only interface that I run tags to pfsense on is igb2.. it carries 3 different networks.. it goes to port 5 on my switch.
Igb0 goes to port 4 on my switch, and this is vlan 9 on my switch.. Igb4 goes to port 8 on my switch and this is vlan 7 on my switch, igb3 goes to port 6 on the switch and is vlan 3.
The only "vlans" that pfsense has is 4 and 6 which are tagged because they share the same physical port and that I run my wlan network on igb2, which is vlan 2 on the switch.
Put the ports you want on your lan in a vlan on your switch vlan 1 is fine.. then whatever interface you want to use for vmnet make this vlan 2 for example and put all the ports you want on this network in that vlan.. The only time you need to tag a vlan is when your going to carry more than 1 network over the same physical interface.
The only vlans pfsense has to be aware of is ones where you are going to have more than 1 come in on the same physical interface. If your just going to put a network directly on an interface in pfsense.. Say for example my igb3 interface above - that network is just on the interface. But to the switch the port that comes in on is on my vlan 3.. any other ports I put in vlan 3 on the switch will be isolated from any of the other vlans on the switch. But none of it has to be tagged - and pfsense has no clue that is vlan 3 on the switch, etc.
On the switch..
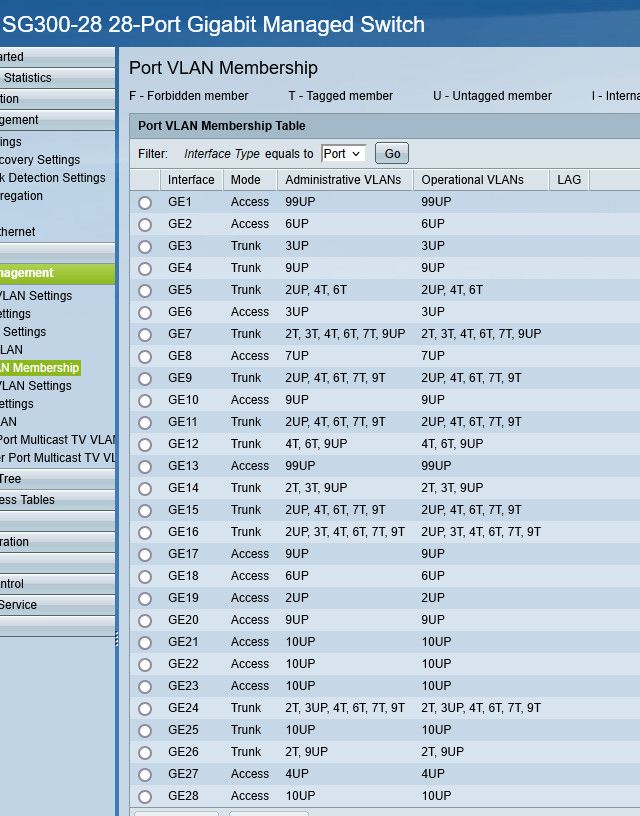
The ports that are trunked and have multiple vlans on them run to another switch, or an AP.. Or one of my nas interfaces so I can put different vms I run on that nas into whatever network I want, etc.
See ports 1 and 13 that I have on vlan 99 on the switch... My wan (modem) comes into port 1 and pfsense wan igb1 is connected to port 13... This isolates my wan traffic from all other networks on the switch.. Pfsense has no idea its vlan 99 on the switch, etc.
What exact mikrotik device do you have - they have routers, they have switches.. And I think devices that can be either depending if you run their router os or the switch os, etc.
If you need to do routing on their hardware you run the router os, if you just need switching you can normally run just the switch os.. But all the ports should be able to be put into a vlan on any of their products from my understanding. I can do routing on my switch, but currently just using it for layer 2 "vlans" and it doesn't do any routing.
-
@johnpoz so if I understand correctly what I could do would be:
ix1 - ix5 (VLAN: 1) ix5 -> (untagged) Uplink pfsense
ix6 - ix 12 (VLAN:2) Ix12 -> (untagged) Uplink pfSenseThat would work?
Kind regards
-
@sysadminfromhell yeah - the only time pfsense needs to know about a "vlan" if it needs to understand tagging.
if you just setup native networks on your interfaces.. You can isolate them on your switch by just putting them in different vlans on the switch.
To pfsense its no different than if the ports were connected to 2 different physical switches. Your just creating 2 "virtual" switches by putting specific ports into different vlans on the switch.
This is the whole point of vlan capable switch.. Traffic being tagged is only used when you need to carry more than 1 vlan over the same physical wire. The tag allows either the router or AP or other switch to know this traffic is network X, this other traffic is network Y.. If you don't plan on running more than one "vlan" over the same physical wire you can still put different ports on your switch into different "vlans" and isolate them from other vlans on the switch, etc.