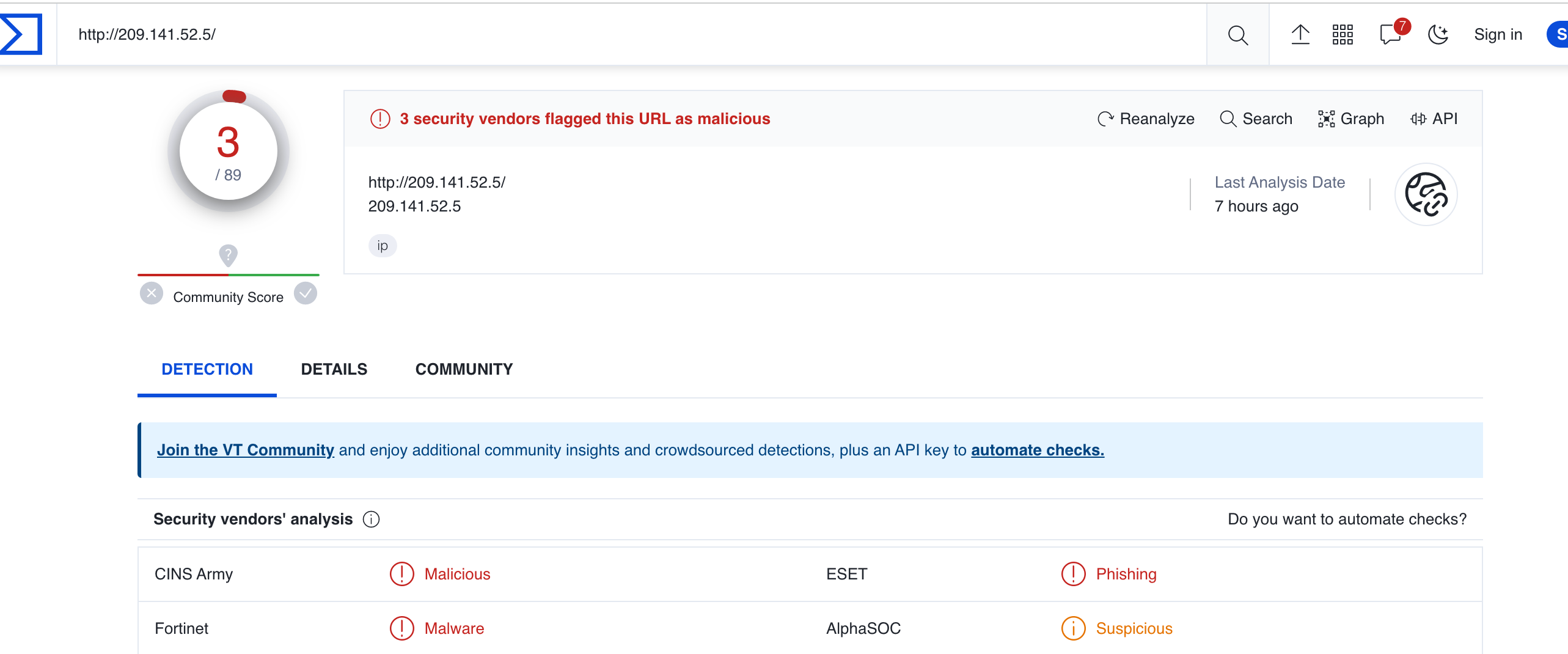
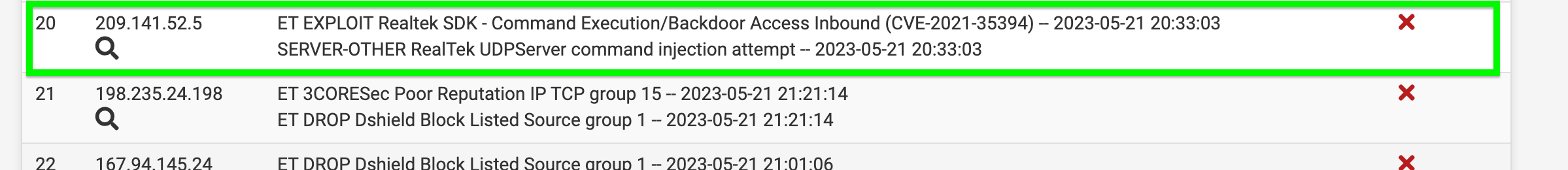
ET EXPLOIT Realtek SDK - Command Execution/Backdoor Access Inbound (CVE-2021-35394)
-
Hello Fellow Netgate Community members,
I wanted to ask if anyone else has started to notice this "Command Execution/Backdoor Access" CVE being exploited?
(SNORT stopping CVE-2021-35394)I have seen this several times from this IP address
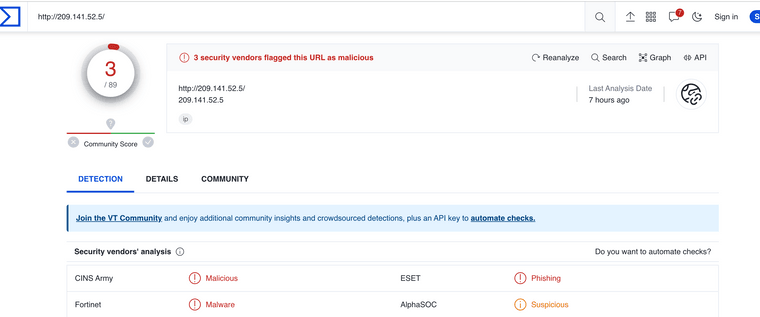
(Virustotal flagged this IP)https://nvd.nist.gov/vuln/detail/cve-2021-35394
How is this CVE being used with the 2100-MAX to my understanding it has no Realtek NIC, does the Raspberry PI have this NIC?
-
As usual :
pfSense is not a develop system, it does not have a - or this - SDK.
To use the SDK, it has to be installed, and a user should have access to pfSense to 'execute it'.
And for good manners : using a Realtek NIC has its own potential load of issues, not really 'CVE', it's more a 'not done' thing.I don't think Netgate ever used Realtek NICs.
-
@jonathanlee Hackets/bots will fling random exploits at IPs to see what they can find. I view it as, if they try X they may try other things but they’re blocked now.
You can always just block the IP by firewall rule but it will be another IP/exploit tried tomorrow.
-
@steveits in cyber security class we learned how to actually use decoy IP address when we got blocked. It was an amazing class. The bug I found durring this was that I could use a decoy address that matched the target and get the IPS to block itself. That Lab I got a really good grade on. It's the double edge sword of enumeration, as if they have the IPS block scans it would block itself they would set it to ignore on that address because it would bring the system down, so you have to make special rules for when that was abused. If it was set to ignore you could scan the Network and see what ports are open. What would be a good security rule to stop that? I set my inbound to block my IP address, my IP only goes outbound.
-
@gertjan I wonder why this is being exploited on my network, I don't think I have a realtek NIC card on anything.
-
@jonathanlee said in ET EXPLOIT Realtek SDK - Command Execution/Backdoor Access Inbound (CVE-2021-35394):
I wonder why this is being exploited on my network
I think you're misunderstanding. The alert does not mean there was a successful attempt, or that you are vulnerable, it generally means the hacker connected to 38 million IP addresses today to try this hack, and one of them was yours. Or else tried 1000 hacks on your IP to see if any worked before moving on.
-
@steveits The firewall stomped it out

-
Hey JL,
I have this pop up every now and again, the ip addresses seem random but always use the same port number, something 9030 or 9040...
As mentioned, pfsense / snort blocked it. I feel sorry for the people that use the default router from their ISP and don't have a router / firewall like pfsense!

-
@ASGR71 Yes but to be fair 98% of them don’t have any inbound ports forwarding. Some for games or uPnP I suppose.
Sine I don’t see I mentioned it above, if one runs Snort or Suricata on WAN, that runs outside the firewall so will block all sorts of things that would get blocked anyway. Running it on LAN avoids a lot of scanning plus will show internal IPs in the alerts.