Can I (how do I) exempt traffic from certainIP's from being scanned
-
Hi
when I use Suricata, even on a 8200, it slows down my nightly backups from the company to a NAS on my home. Downloading files from internet etc doesn't seem to slow down BUT this specific task (backup from QNAP to QNAP over the internet is slowed down).
So can I exempt certain IP's from "entering" the suricata scan?
-
@manilx said in Can I (how do I) exempt traffic from certainIP's from being scanned:
So can I exempt certain IP's from "entering" the suricata scan?
Sure you can...either create a pass list or suppress a rule (qnap) for a certain IP.
-
@nollipfsense I have put an alias with the IP's in a new Pass List.
Where do I assign this?
-
@manilx said in Can I (how do I) exempt traffic from certainIP's from being scanned:
@nollipfsense I have put an alias with the IP's in a new Pass List.
Where do I assign this?
Pass Lists are assigned under the INTERFACE SETTINGS tab in Suricata. Once you assign a Pass List and save the change, you must restart Suricata on that interface to activate the change.
-
@bmeeks Did the following, which I guess is correct:
created passlist:
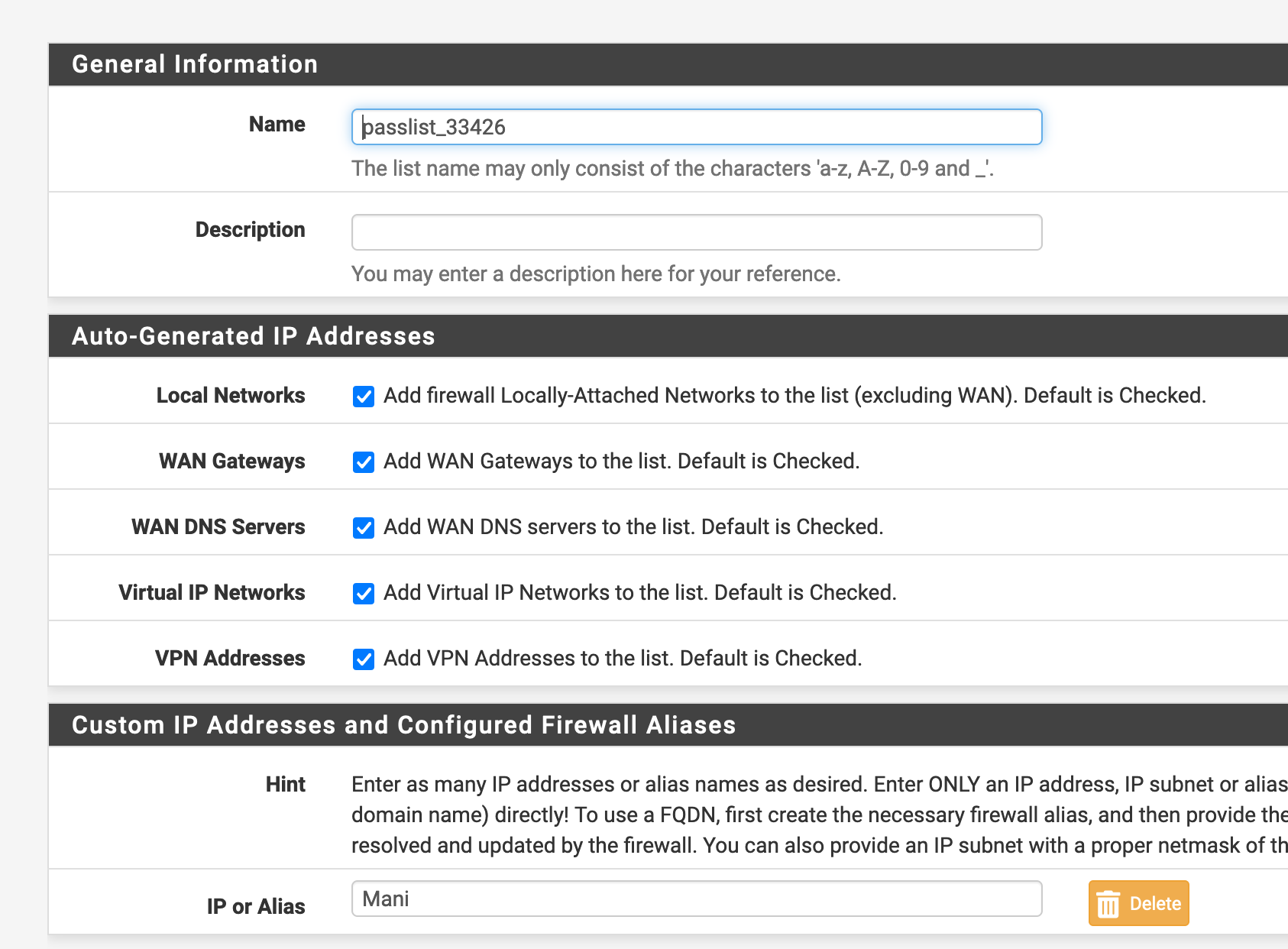
added it under the respective interface:
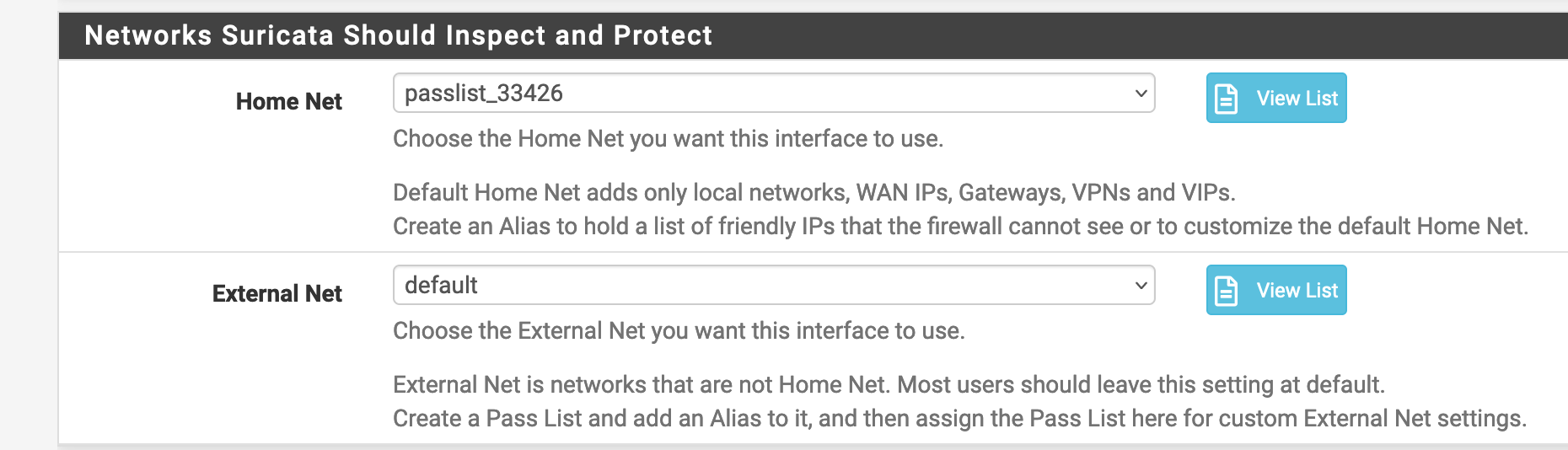
-
@manilx:
No, you have assigned it to the $HOME_NET variable. That is very wrong. Never modify HOME_NET unless you are very experienced with an IDS/IPS and have a very specific reason for doing so. Making the change you put in place there has likely totally neutered your IDS/IPS.Are you using Inline IPS Mode or Legacy Mode Blocking? If using Legacy Mode (which is the default), then you will see a Pass List drop-down box to configure. If using Inline IPS Mode, then Pass Lists are not used and the drop-down will be hidden.
With Inline IPS Mode, you must create custom PASS rules for Suricata on the RULES tab. PASS rules are evaulated first, and traffic matching a PASS rule is exempted from any further processing by Suricata. You can find the proper syntax for PASS rules with a simple Google search. Just be careful that your rule is very specific in terms of the IP addressing. It will be very easy for an improper rule to essentially result in bad traffic bypassing the IDS/IPS.
-
@bmeeks I have IPS Mode.
Disabled my settings.Created a new passrule with only the alias.
Sorry but I don't see how to create the pass rule :(
Can you help. I just need this passrule/alias applied. No suricata scanning on those incomming IP's. (I have suricata checking the WAN interface, yes I know, matter of debate ;) )
-
@manilx Found this pass rule you posted in another post:
pass ip 1.2.3.4 any <> any any (msg:"pass all traffic from/to 1.2.3.4"; sid:100000;)No I only need to know where to put this....
-
@manilx:
You are still stuck in the Pass List mode based on the last screenshot you posted. PASS rules have nothing to do with Pass Lists. Pass Lists are used to prevent IPs from ever getting blocked in Legacy Blocking Mode. That's all they do. They do not exempt IP addresses from scanning. I thought at first reading you wanted to be sure your Alias IPs were never blocked.PASS rules are actual Suricata text rules just like the rules you might download and enable from Snort VRT or Emerging Threats. They just have the rule action PASS instead of ALERT or DROP. Here is a link to the official Suricata documentation describing PASS rules: https://suricata.readthedocs.io/en/suricata-6.0.0/performance/ignoring-traffic.html#pass-rules.
Because PASS rules are native Suricata constructs, they do not understand pfSense aliases. You cannot use an Alias name in Suricata rules. The best you can do is custom rules with specific IP addresses or subnets.
You create custom rules by going to the RULES tab and selecting Custom in the Category drop-down. Then type in your custom rules in the text box that appears and save them.
-
@manilx said in Can I (how do I) exempt traffic from certainIP's from being scanned:
I have suricata checking the WAN interface, yes I know, matter of debate ;)
You are wasting a lot of CPU cycles doing that. Suricata is seeing and scanning all the Internet "noise" hitting your firewall. Every CPU cycle consumed to scan traffic that is going to be blocked by firewall rules later on is a CPU cycle that could have been used to improve throughput by reading/writing buffers associated with the NIC transferring data (in other words, throughput).
Let the firewall do its job on the WAN side and block most or all of the noise. Then Suricata has less work to do and throughput should improve.
-
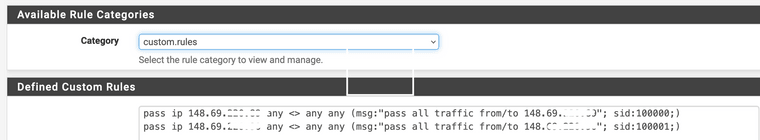
@bmeeks Found it!!!!
Added 2 rules for both IP's I want excluded:
pass ip 1.2.3.4 any <> any any (msg:"pass all traffic from/to 1.2.3.4"; sid:100000;) -
@bmeeks I've so much contradictory info on this.....
I guess I settled with the opinions that it would be OK to scan the WAN if one does have ports open, which I have. -
@manilx said in Can I (how do I) exempt traffic from certainIP's from being scanned:
@bmeeks I've so much contradictory info on this.....
I guess I settled with the opinions that it would be OK to scan the WAN if one does have ports open, which I have.Here's the bottom line on open ports. First, you should not be depending on Suricata to protect your firewall. If your firewall has issues, then you are hosed. Suricata and any IDS/IPS is for protecting the networks behind the firewall -- not for protecting the firewall itself.
In pfSense, nothing can get to your internal networks without first passing through the IDS/IPS when you are running the IDS/IPS on an internal interface. So, you give up no protection by running on the internal interface.
The only reason to consider running the IDS/IPS on the WAN would be a situation where you have very limited RAM and want to protect a number of internal interfaces. In that scenario, running an IDS/IPS instance on each internal interface might run you out of available RAM. But the better solution would be to upgrade RAM. Another possible reason to run a single WAN instance would be if you had an anemic CPU and didn't have enough horsepower to run multiple instances. Again, though, upgrading the hardware would be a better choice.
Running on the WAN brings two big negatives in my view. First, you uselessly scan all the Internet noise the WAN firewall rules are likely going to drop anyway. You scanned traffic and wasted CPU cycles for nothing. You also fill up your alert logs with that scanned noise. Second, you can only see the WAN public IP for all internal hosts due to NAT. So, tracking down which internal host is a problem is difficult at best. When you run on the internal interfaces, then all the native IPs show up and locating a problem host is easy.
-
@manilx said in Can I (how do I) exempt traffic from certainIP's from being scanned:
@bmeeks Found it!!!!
Added 2 rules for both IP's I want excluded:
pass ip 1.2.3.4 any <> any any (msg:"pass all traffic from/to 1.2.3.4"; sid:100000;)Make sure you incremented the SID for each rule so that you do not have a duplicate SID!
-
-
@bmeeks Thanks for this precise description.
OK reverted to scanning LAN ;)