Policy-based routing isn't pushing traffic through the correct gateway
-
Hi,
I know this keeps getting asked but I'm really stuck.
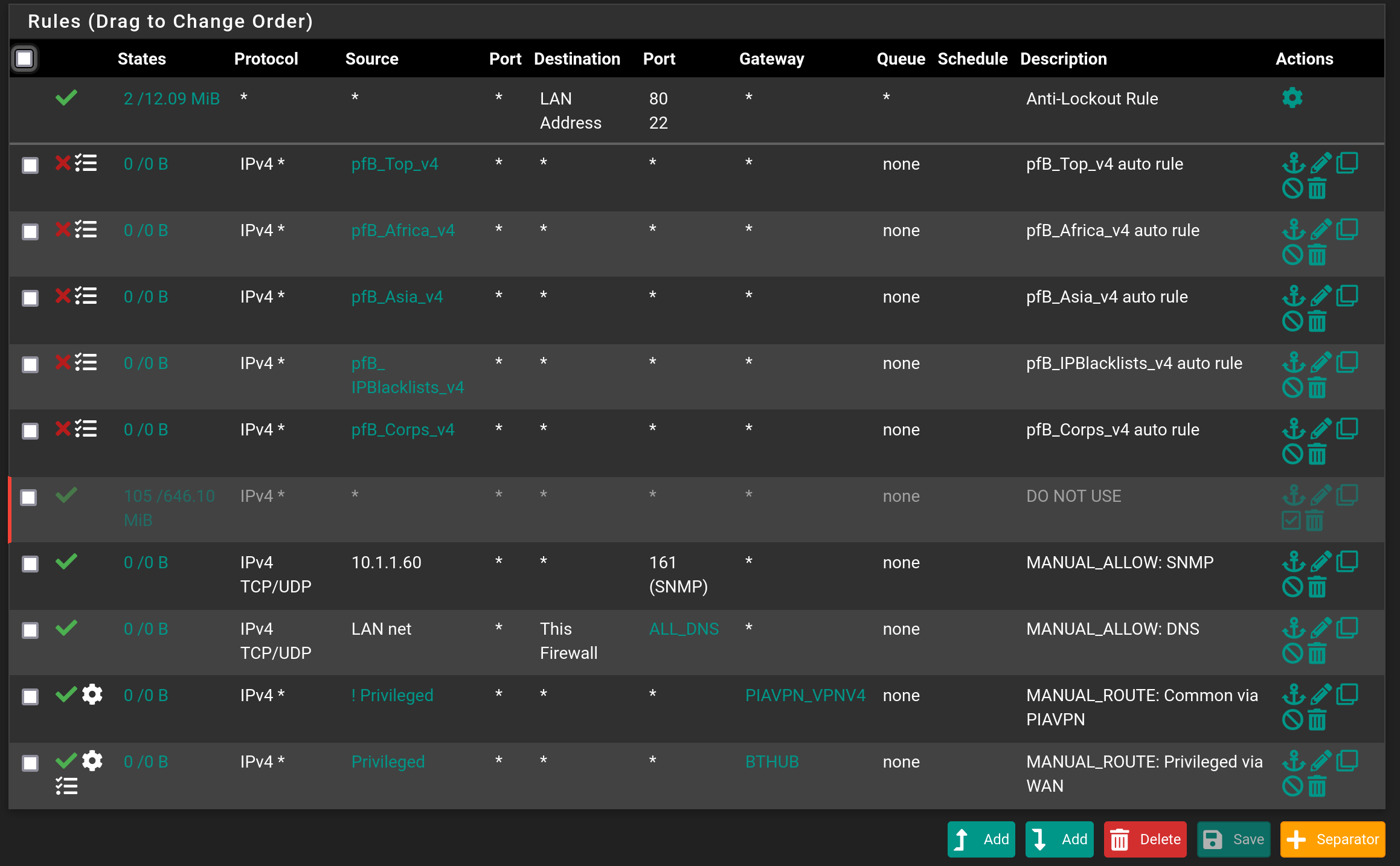
I keep going back here to double check my work but it seems fine!Basically, if a host matches a group I call privileged, the gateway is direct to WAN. If it does not, the gateway goes through the VPN.
But my public IP is shown when I used:
curl ipecho.net/plainI can push traffic through the correct interface by doing this on the firewall shell:
curl --interface ovpnc4 ipecho.net/plainThere's no errors in the openvpn client log, and I turned the gateway monitoring off for it.
I have tried turning off pfblockerng, but that doesn't help either.
Can someone please help me?
-
@ctuchik
Enable the logging in both concerned rule and check then, which is applied to the traffic.Consider also to flush the states.
-
@ctuchik Where did you run curl?
-
@viragomann OK logging enabled on both, I am looking in
Status > System Logs
Then filtering the log for the ID of the rules.
Is this area up to the second after a refresh? There isn't much in there.
I flushed the states too, but it doesn't seem to fix anything.DNS, speedtests, curl = nothing works unless the host is made a member of the "Privileged" Alias. Traffic simply won't route through the VPN unless I hop on the firewall using ssh and do a curl through it, specifying the interface to use.
@bob-dig: curl is being run from a host that is a member of the "Privileged" Alias, one that is not, and also in an ssh shell of pfsense as well.
-
@ctuchik said in Policy-based routing isn't pushing traffic through the correct gateway:
unless I hop on the firewall using ssh and do a curl through it, specifying the interface to use.
Then it is an oubound NAT problem. You have to configure it accordingly.
-
@bob-dig In case I get reprimanded for what seems like outbound NAT not being in manual mode: This firewall is virtual, and I did try a VM snapshot, moving to manual, copying the correct rule and changing the interface to openvpn instead - this fixed nothing.
Here is how that looks at the moment:
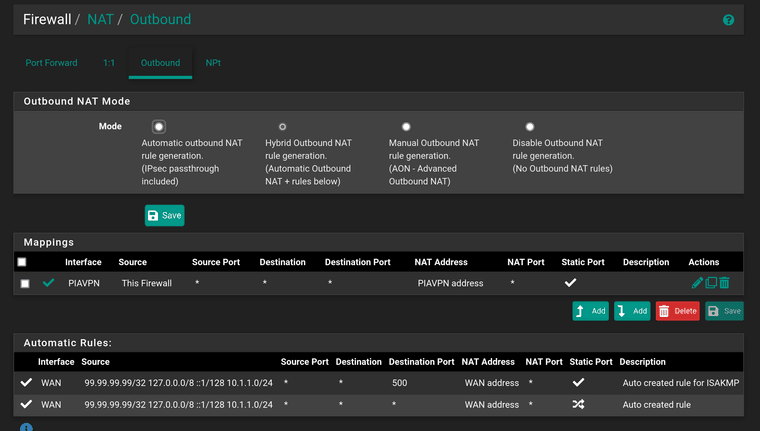
Perfectly happy to do it again though?
-
@ctuchik With that screenshot shown, it is no wonder, that it is not working. For OpenVPN you need to make some rules like it is described in the tutorials.
You could try to replace "this firewall" with any, for testing. -
Is it relevant to mention the hypervisor hosting pfsense is in a DMZ behind a router that is connected directly to the Internet?
*EDIT OK will try that.
-
@bob-dig It's working, you were right and I'm grateful you helped :)
If you wouldn't mind helping me learn how this fixed my issue?
I vaguely understand the rule to mean this: "any outbound traffic on this interface should be translated as if it has come from the current VPN address", so since I mentioned "this firewall ", doesn't that cover everything already? -
@ctuchik It covers only the firewall itself. "Any" is not advised though, you should define all the source networks (LANs) you like to use with the vpn.
-
@bob-dig OK got it, thanks again.