pfSense WireGuard and the the Android Client
-
It is sold and works now. The problem was a Key missmatch I guessed. Here my Settings.
pfSense configuration:
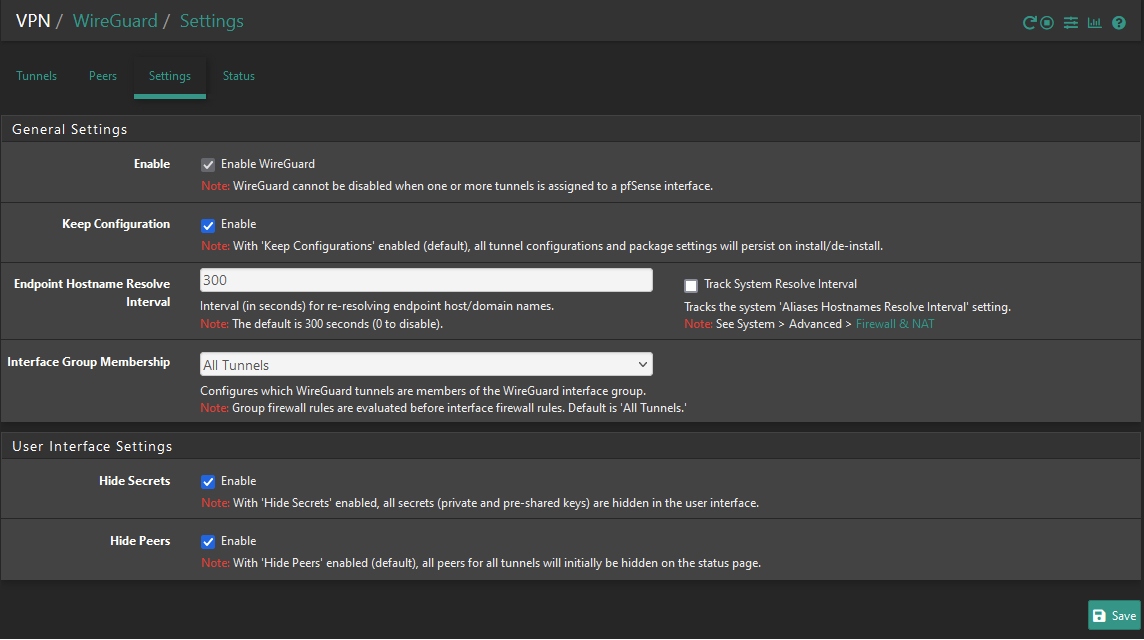
General Settings:
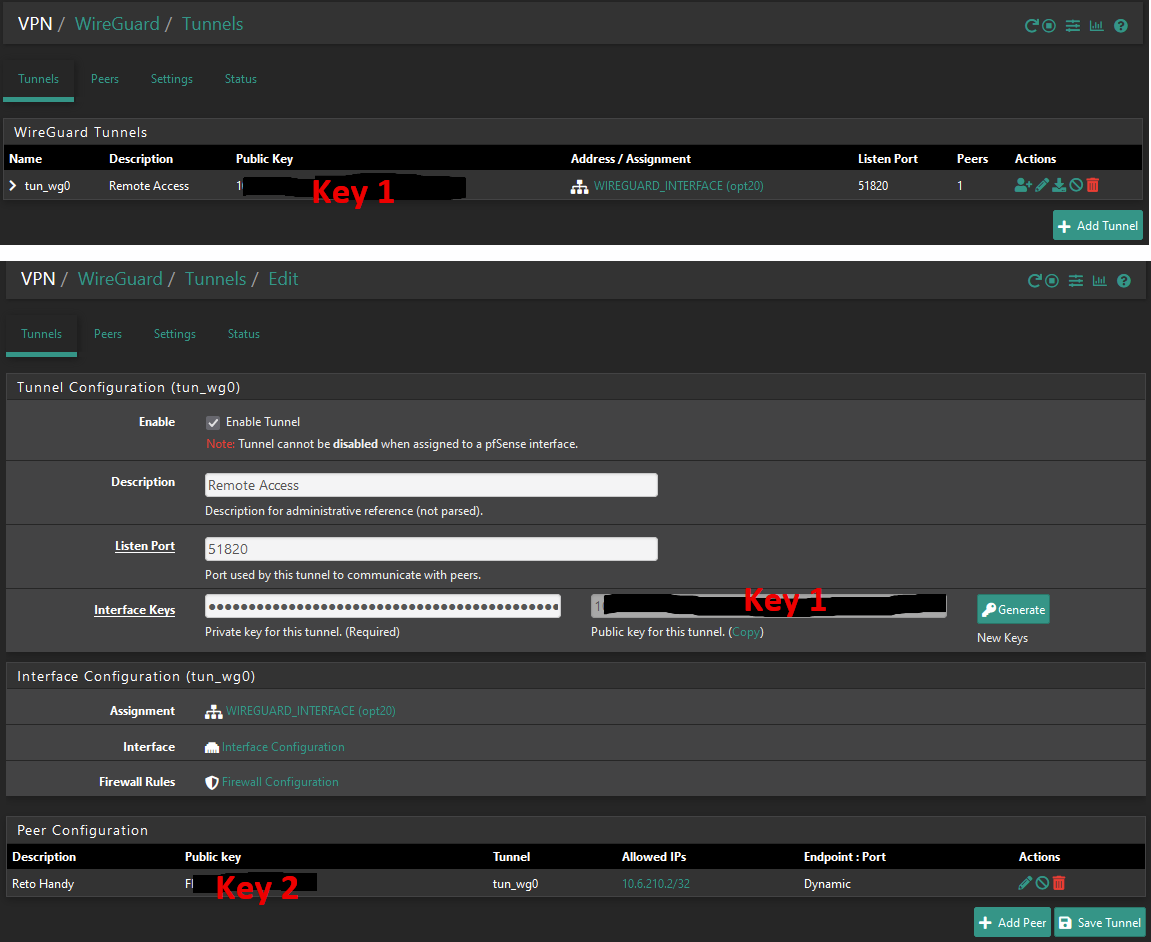
Tunnel Setting:
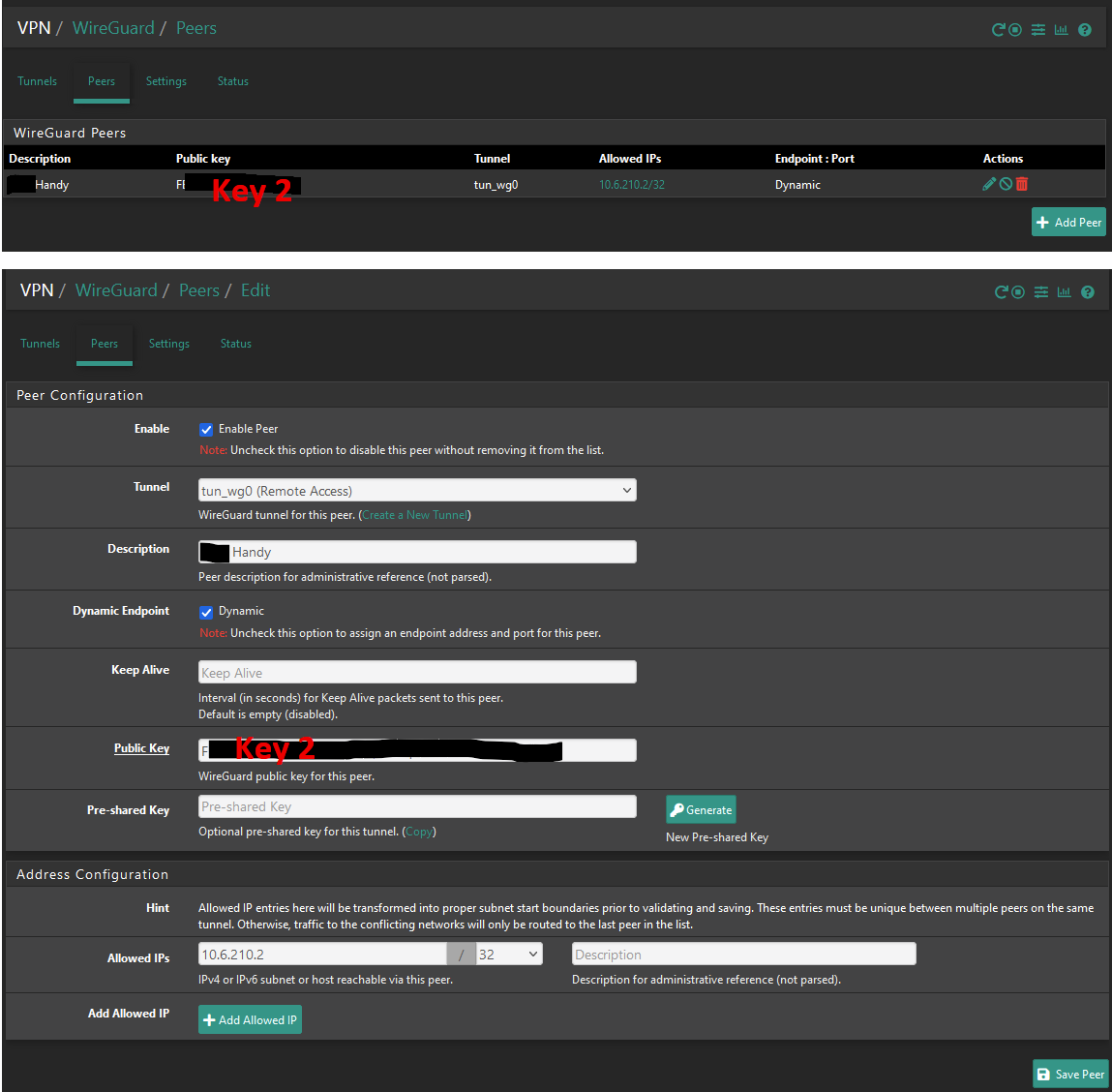
Peer Setting:
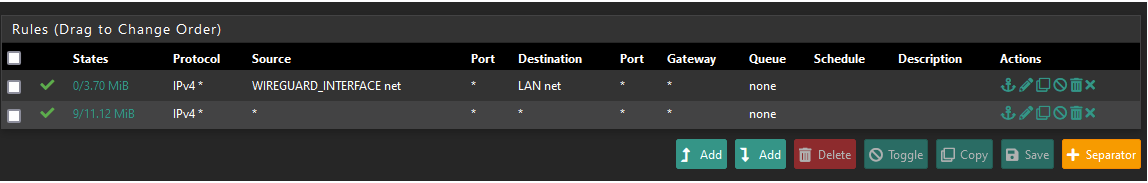
WireGuard Roule(s):
WAN Roule:
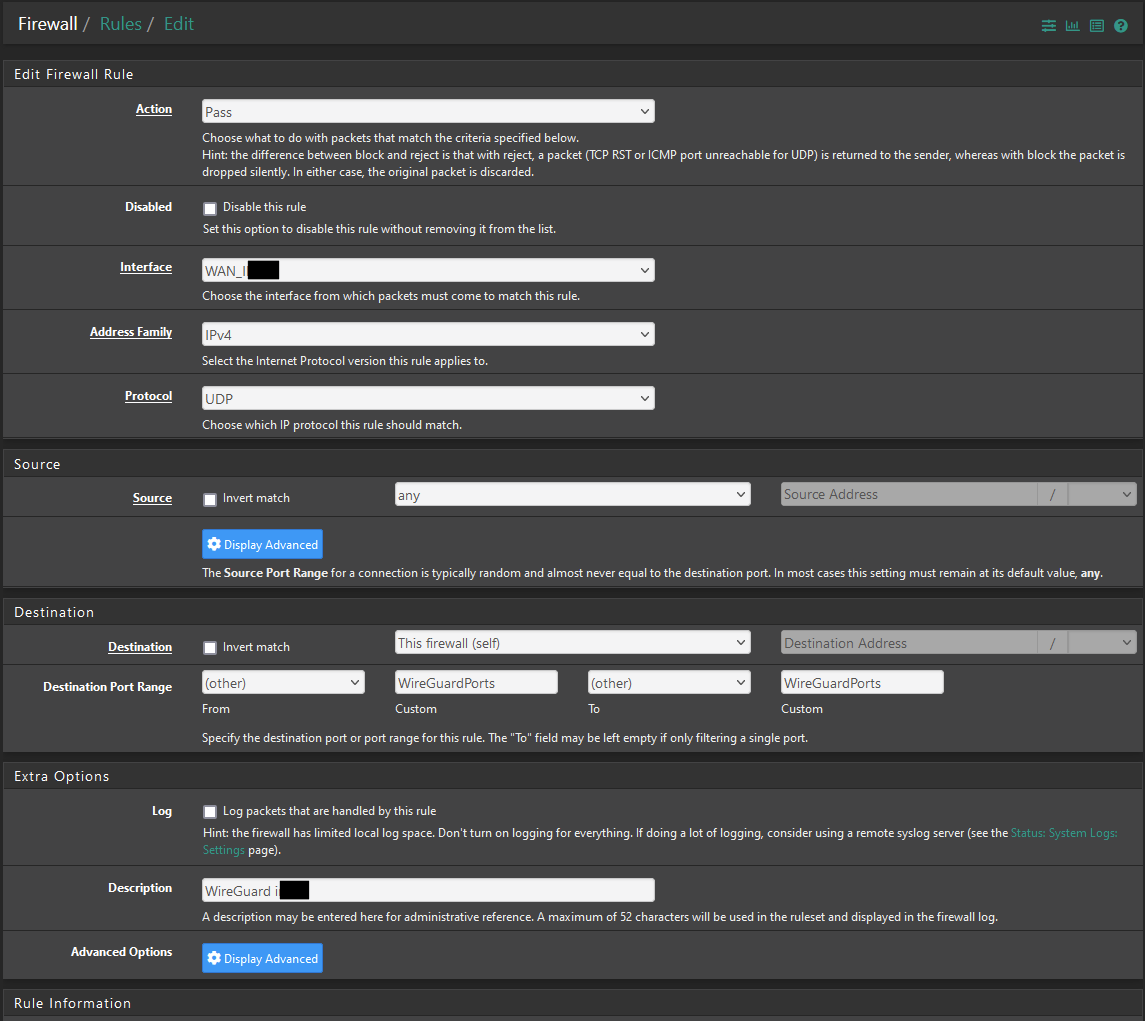
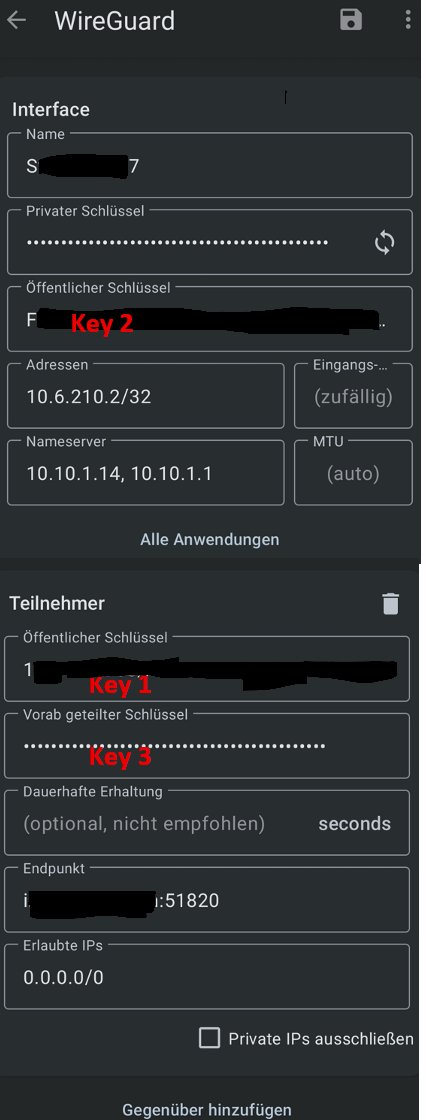
Key1: Public Key from Tunnel Setting pfSense
Key2: Public Key From Client (here Android).
Key3: Preshared Key: optionalNow the Android Client Settings:
-
Tunnel Subnet is:
10.6.210.0/24
The IP-Adress 10.6.210.1 must be entered ind the Wireguard Interface (here OPT20). This interface must be Assigned.
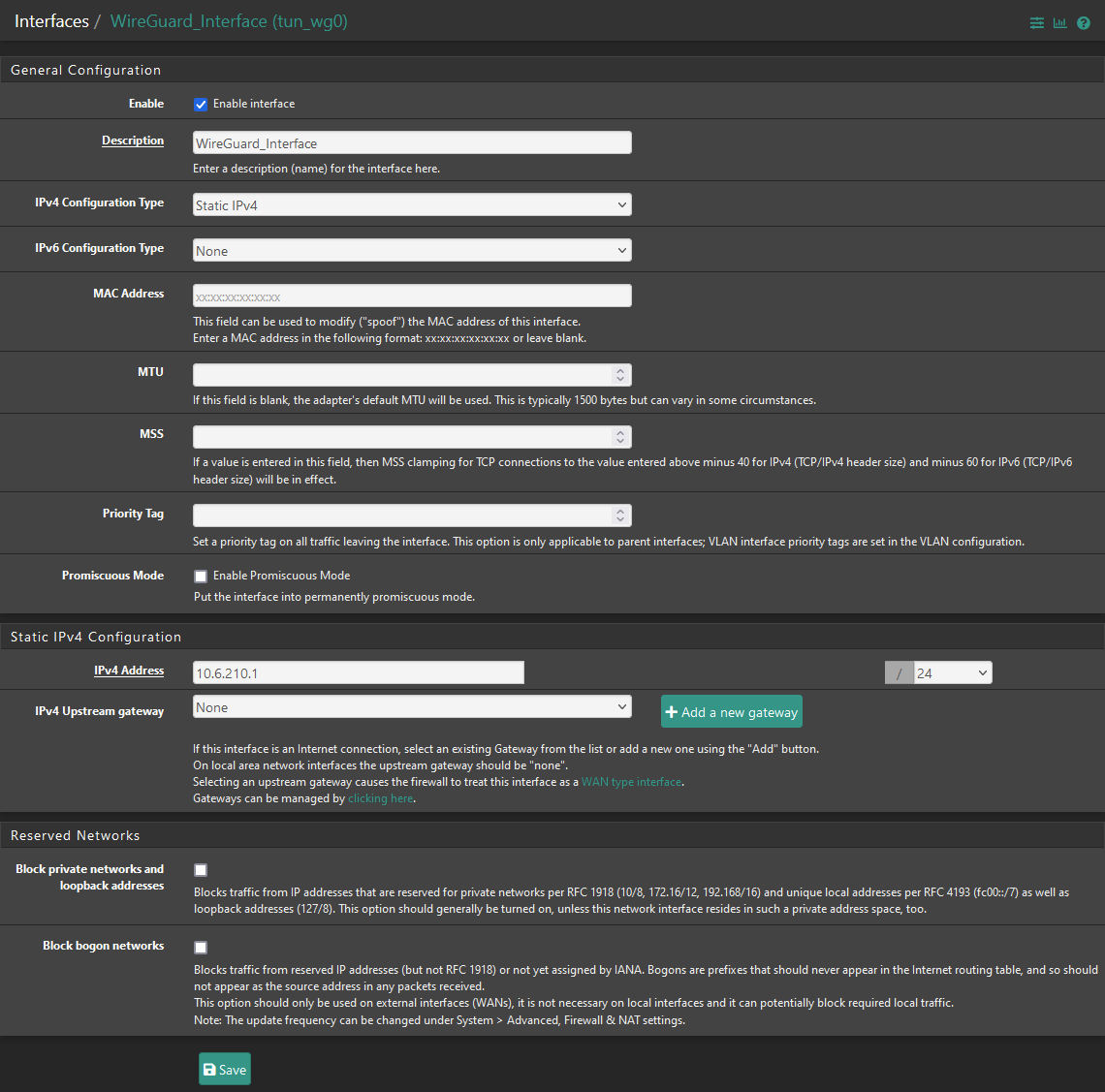
All other Addresses 10.6.210.2 - 10.6.210.254 are for the peers
No firewall roules are needed for the interface. Only roules for the WireGuard Group (see post before).
-
@sigma said in pfSense WireGuard and the the Android Client:
WAN Roule:
Better chose "WAN address" instead of "This firewall (self)", especially on WAN.

-
@Bob-Dig
Ok Thanks for the hin. I think a security reason. But Why? What's the difference? -
@sigma said in pfSense WireGuard and the the Android Client:
What's the difference?
One is only the WAN-address, the other is every interface pfSense has to offer. So no need to use the latter in a WAN-rule.
-
@Bob-Dig
Ok, that make sense. I change all "this firewall" to the wan devices for which the roule is needed. I have 3 WAN devices (10Gbit Fiber, DSL and 5G Backup). On the 2 wired I have VPN roules (OpenVPN and Wireguard). And then are there some LAN Subnets some with VLAN's some direkt interfaces on the appliance. In the meantime the whole thing is a bit complex for a home firewall ;). I expect a 25Gbit's also synchronous internet connection this year and so I channged from a virtual pfSense to an appliance which is much more performant. With this lines I can do some interesting tests with VPN, so I heards from WireGuard and now I'll test it.With wireguard I also found out that it seems to have problems to resove internal DNS names. I provide the internal DNS server in the DNS files of wirequard config. But it seems not to work. So local SMB shares could not be connected by their names over the WireGuard VPN. But it works fine with OpenVPN. Connect SMP shares with ip address works fine. I saw here some posts with the same problem. I'll have a look to this postings later. At the moment it's ok, WireGuard basically works and I can do some speedtests.
-
@sigma said in pfSense WireGuard and the the Android Client:
With wireguard I also found out that it seems to have problems to resove internal DNS names. I provide the internal DNS server in the DNS files of wirequard config. But it seems not to work.
Working fine here. Try 10.6.210.1 as DNS-server.
-
@Bob-Dig
The tunnel Gateway as DNS? I try it. -
@Bob-Dig
Don't works. The firewall don't knows the dns names, so i normaly use the AD server as DNS server, so all internal hosts could be resolved. But WireGuard works not this way.
I made now 2 host overrides in the DNS Forwarder and now the hosts will be recogniced. But I think it also should go the other way round. -
This post is deleted!