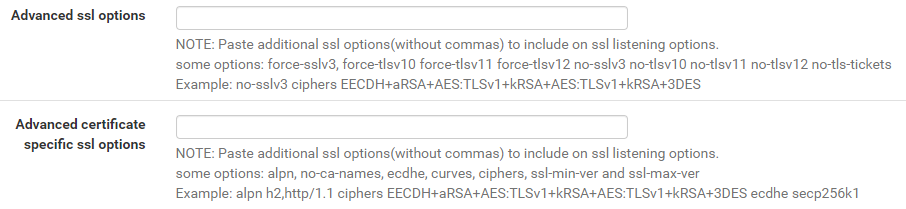
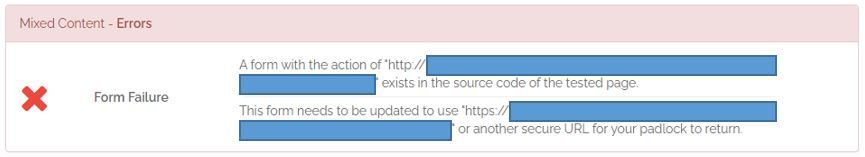
TLSv1 Issues and Cipher Suggestion for site that perform transaction please. Mixed Content Issue as well.
-
@wakson005
I have this in my global advanced settings, not in the frontend:ssl-default-bind-ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK ssl-default-bind-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256 ssl-default-bind-options no-sslv3 no-tlsv10 no-tlsv11 no-tls-tickets tune.ssl.maxrecord 1370It does TLS 1.3 if the client supports it, but requires at least 1.2.
Regarding the mixed mode issue, did you configure an http to https redirecting in the frontend?
-
@wakson005 yeah as @viragomann points out if you have some link inside your form that your hitting via https that points to http that is a problem with the code and not really a haproxy thing.
I use these settings in my haproxy
ssl-default-bind-ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES256-GCM-SHA384 ssl-default-bind-ciphersuites TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256 ssl-default-bind-options prefer-client-ciphers ssl-min-ver TLSv1.2 no-tls-tickets ssl-default-server-ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES256-GCM-SHA384 ssl-default-server-ciphersuites TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256 ssl-default-server-options ssl-min-ver TLSv1.2 no-tls-ticketsAnd have set to Intermediate for compatibility mode - modern was giving me a less than perfect A+ score on the qualys test https://www.ssllabs.com/ssltest/
-
@johnpoz said in TLSv1 Issues and Cipher Suggestion for site that perform transaction please. Mixed Content Issue as well.:
modern was giving me a less than perfect A+ score on the qualys test https://www.ssllabs.com/ssltest/
I got the + not until additionally activating HSTS as far as I remember.
-
@viragomann yeah had that - was driving me nuts for the longest time.. but if you disable 1.2 which is what modern does you can not get an A+
So for example here is current
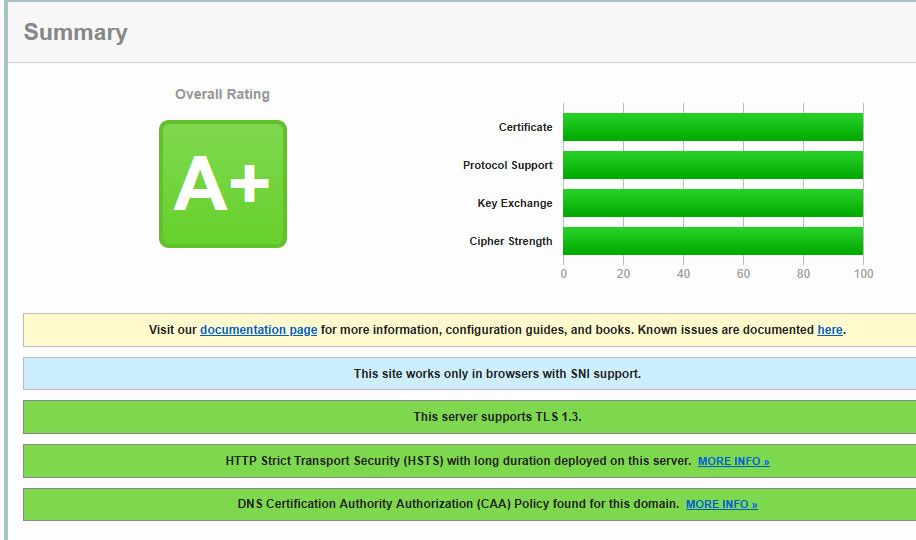
If I change to modern.. And change my min settings to 1.3 only I only get an A ;)
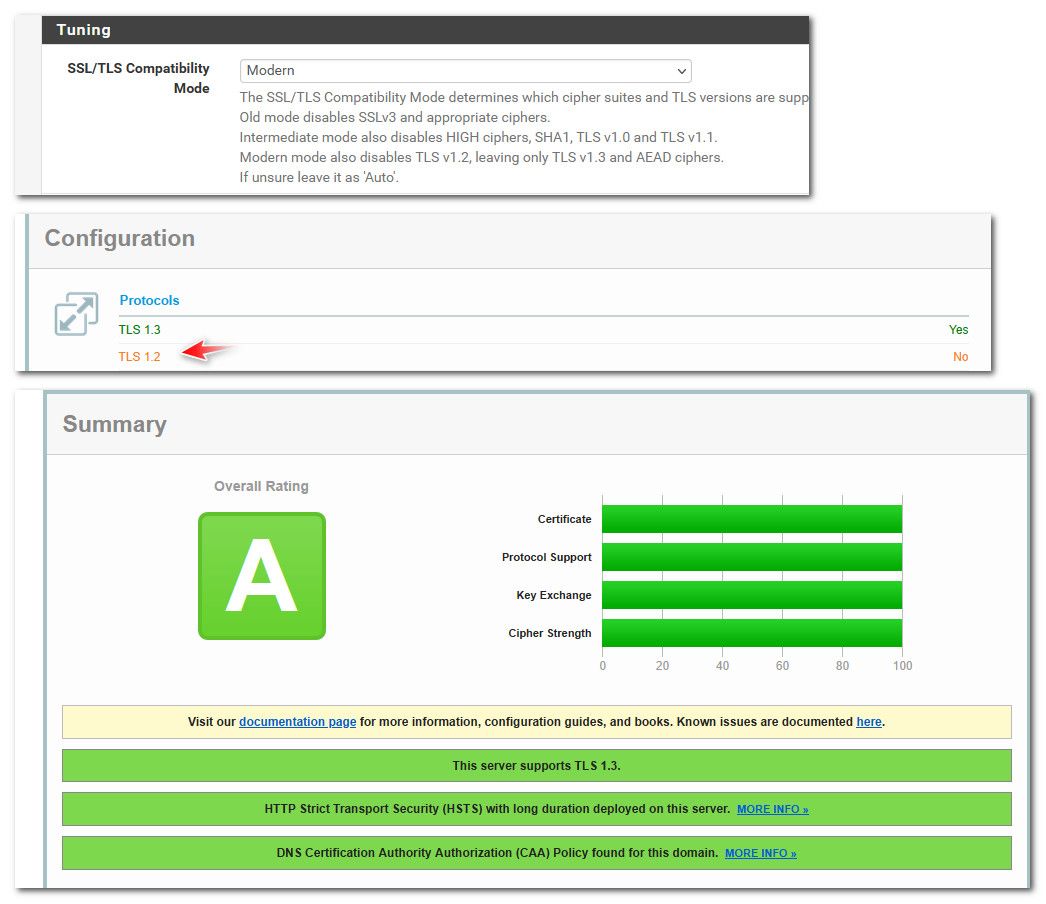
I should prob just leave 1.3 as min only - but like to see the A+ heheh yeah I have hsts set, that was the first thing I looked at when not getting A+, seems to be a bug in their scoring if you ask me
-
@johnpoz said in TLSv1 Issues and Cipher Suggestion for site that perform transaction please. Mixed Content Issue as well.:
but if you disable 1.2 which is what modern does you can not get an A+
Didn't try that. It's not an option for me.
But hey, 4 x 100%! I only got 90 for key exchange and cipher strength.
I consider to take over your cipher settings. :-)
:-) -
@viragomann hmmm - I did change them to get the 100, because yeah the 90 bugged me as well.. I just don't recall exactly what I changed.. But pretty sure I grabbed these setting from some site like you linked too - not sure if was that specific one or not.
-
Thanks really appreciate the great reply! It is almost weekend and finally have some time to review the content you guys posted.
Really love that A+ rating too lol definitely need to look where to place that global setting instead of every single frontend lol.
-
I just setup a Force HTTPs redirect on my frontend now. That fixed some padlock issues and let the site display properly on IE, Firefox, & Opera. For some reason google never complain even without force HTTPs.
-
Looking into where to place that global setting for the ciphers. Can't seem to find that screen is it only in PFSense+ version (currently using community edition) or different HAProxy package release?
-
Also the "SSL/TLS Compability Mode" I don't seem to see it for some reason in my settings maybe I'm not in the right screen?
I see this under tuning...
scrolling down:
Now that i think about it my HSTS maybe the issue? Only see HSTS on my HAPproxy >> Backend.
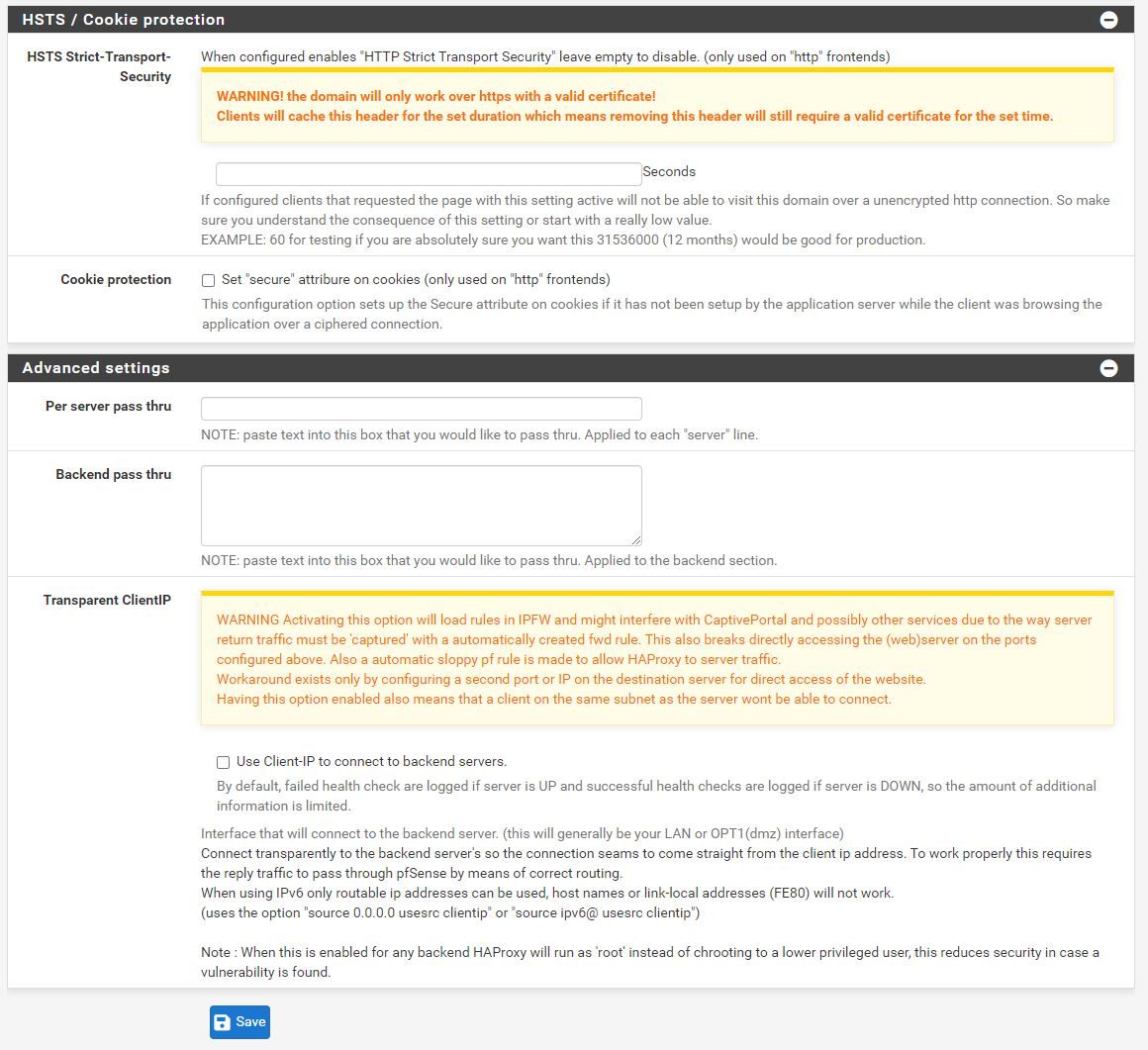
-
-
I think this is the global setting as it wasn't too obvious to me:
Input global setting here:
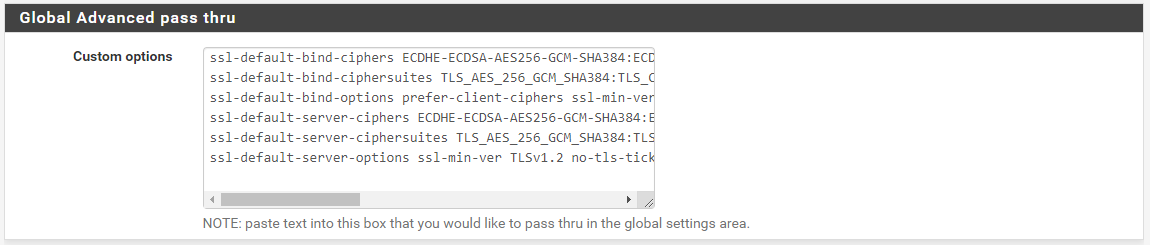
will output this later on:
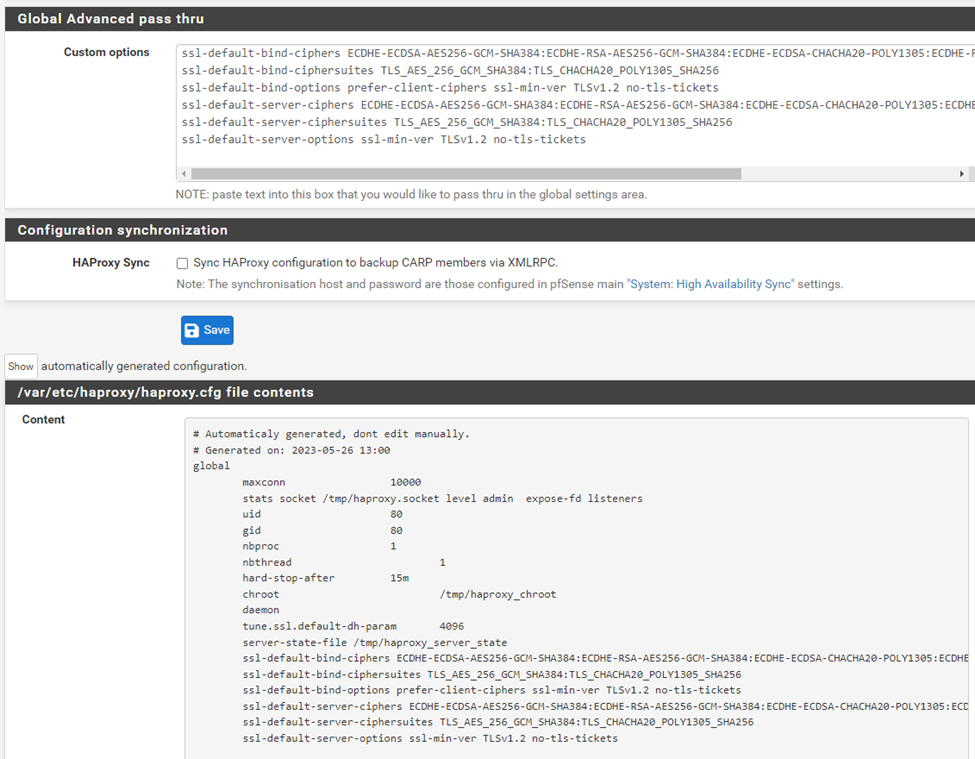
-
Got it to A at least now :)
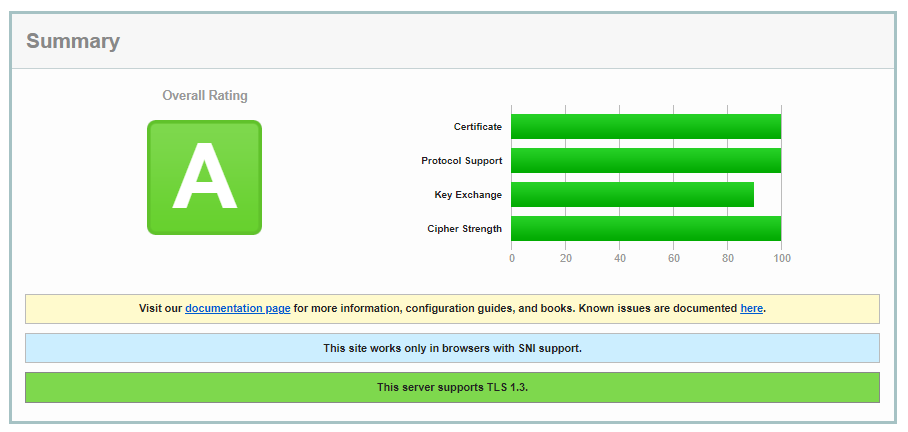
Seem missing A+ because of the Key Exchange. Do you guys know how to change that?
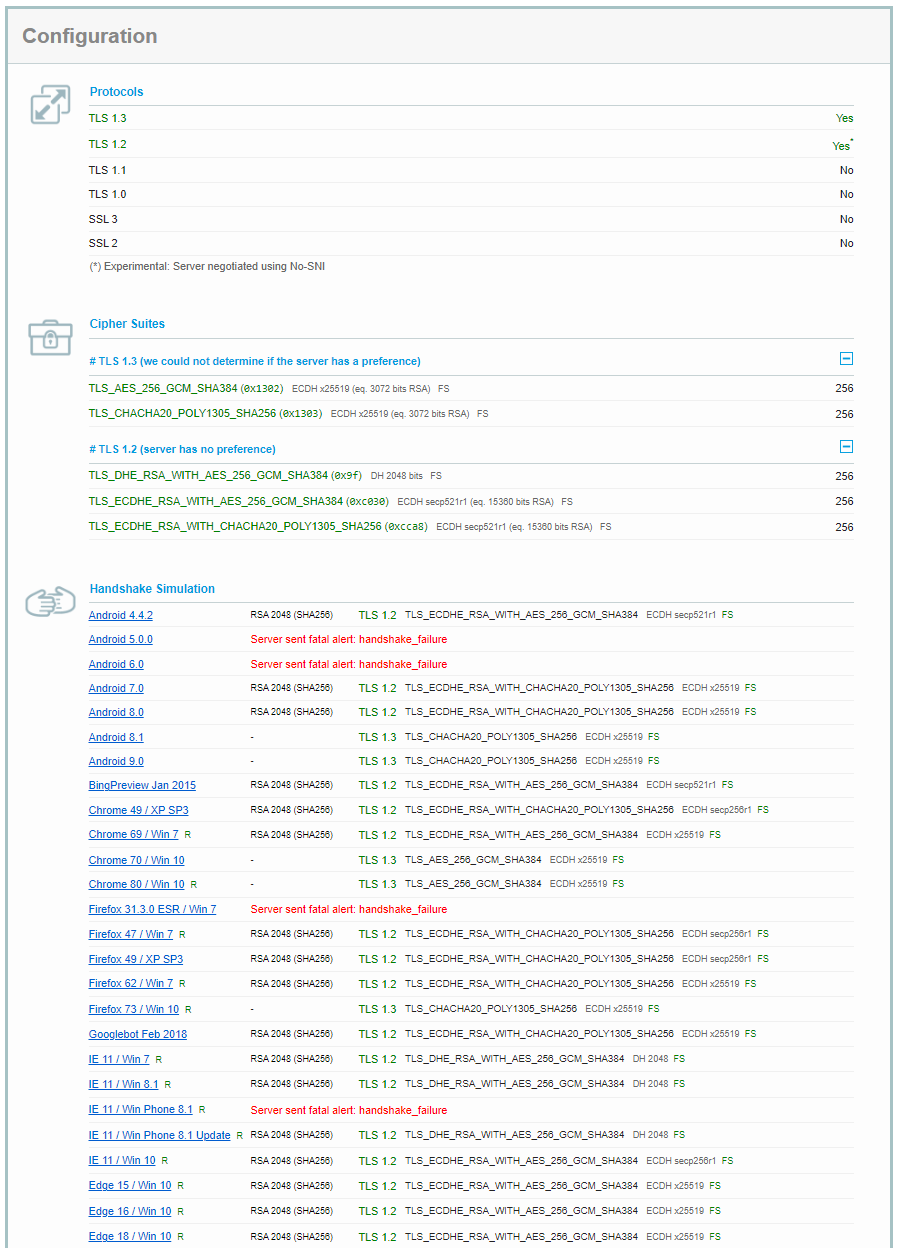
I set my private key to RSA 4096 but I assume the exchange key is a different key probably set elsewhere?
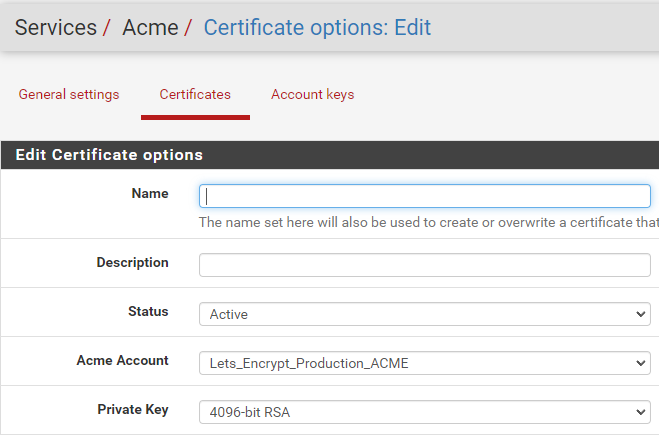

-
@johnpoz said in TLSv1 Issues and Cipher Suggestion for site that perform transaction please. Mixed Content Issue as well.:
I should prob just leave 1.3 as min only - but like to see the A+
https://www.ssllabs.com/ssltest/analyze.html?d=test%2ddomaine.fr&s=5.196.43.182&latest
Not full green bars, accepting 1.3 and 1.2, still A+
I guess full green bars is suspect, so you get capt ;) -
@Gertjan If it is for personal use only 1.3 is fine but if the site is a hosting site removing 1.2 will block lots of people from accessing the site. Which is clearly a separate issue and a case by case usage of the site.
Where do you change the setting in pfsense/haproxy to get a RSA 4096 key exchange?
-
Thanks everyone this is perfectly resolved and I am now getting A+.
I suspect the mixed content for the form is coming from the backend not having SSL enable so the content is transfer unencrypted internally only. Which can easily be fixed by encrypting all internal servers. Hopefully this is the case as the app is modern and created within last year and has both http and https capabilities but as the internal server is a test server running on http it is complaining as it is only accepting http as no SSL is setup yet. Probably need to set that up too eventhough it is just for internal usage and testing purpose.