Problem configuration OpenVPN
-
@gertjan Thanks for your help,
I'll test tomorrow and I'll come back to you for an update -
@gertjan @gertjan Hello again, I'm coming back to you because I had the opportunity to do some tests again today and it's not better than before.
I reset everything to start on a new configuration to follow what you told me.
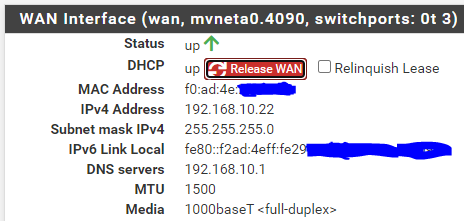
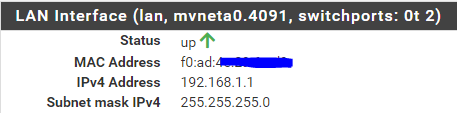
I have my LAN at 192.168.1.1 with the same DHCP as you, for the WAN I have
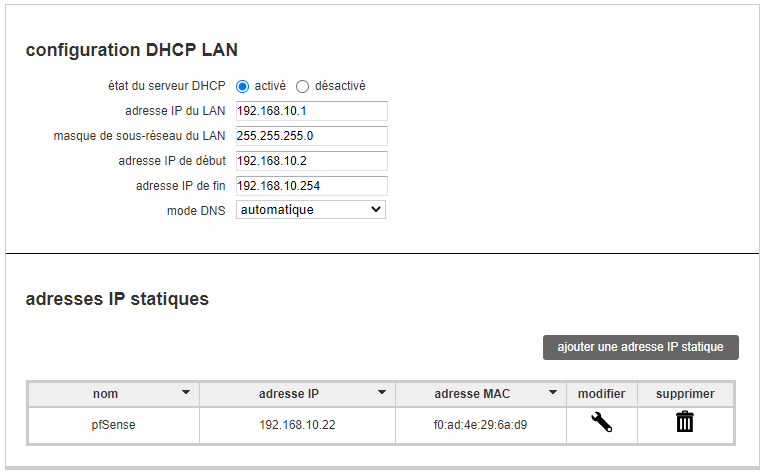
my address in 192.168.10.22 assigned in DHCP by my box and I changed the LAN network of my router to 192.168.10.1I also created a static DHCP address for the pfsense and a nat rule for
the UDP protocol.
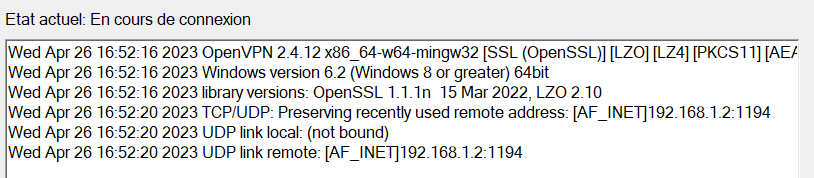
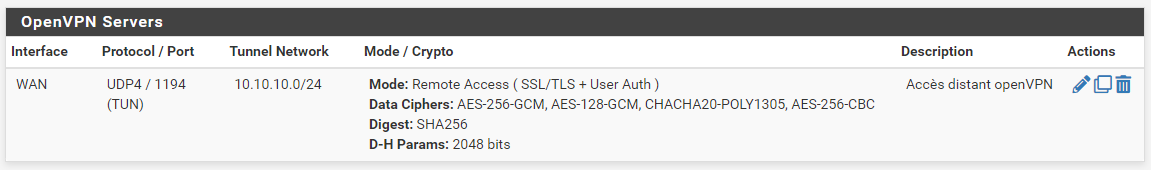
I re-created a CA and a certificate as well as a VPN server and a user but I still have the same error which is starting to drive me crazy.
-
@kilian77 I realized without doing it on purpose that if I did the wifi test my configuration worked, so the problem may be coming from my router?
-
@kilian77 said in Problem configuration OpenVPN:
I have my LAN at 192.168.1.1 with the same DHCP as you, for the WAN I have
my address in 192.168.10.22 assigned in DHCP by my box and I changed the LAN network of my router to 192.168.10.1If this 'router' is your ISP router, then, yes, ok.
Keep in mind : pfSense is also just a 'router'.Your Livebox setting look ok to me :
I have :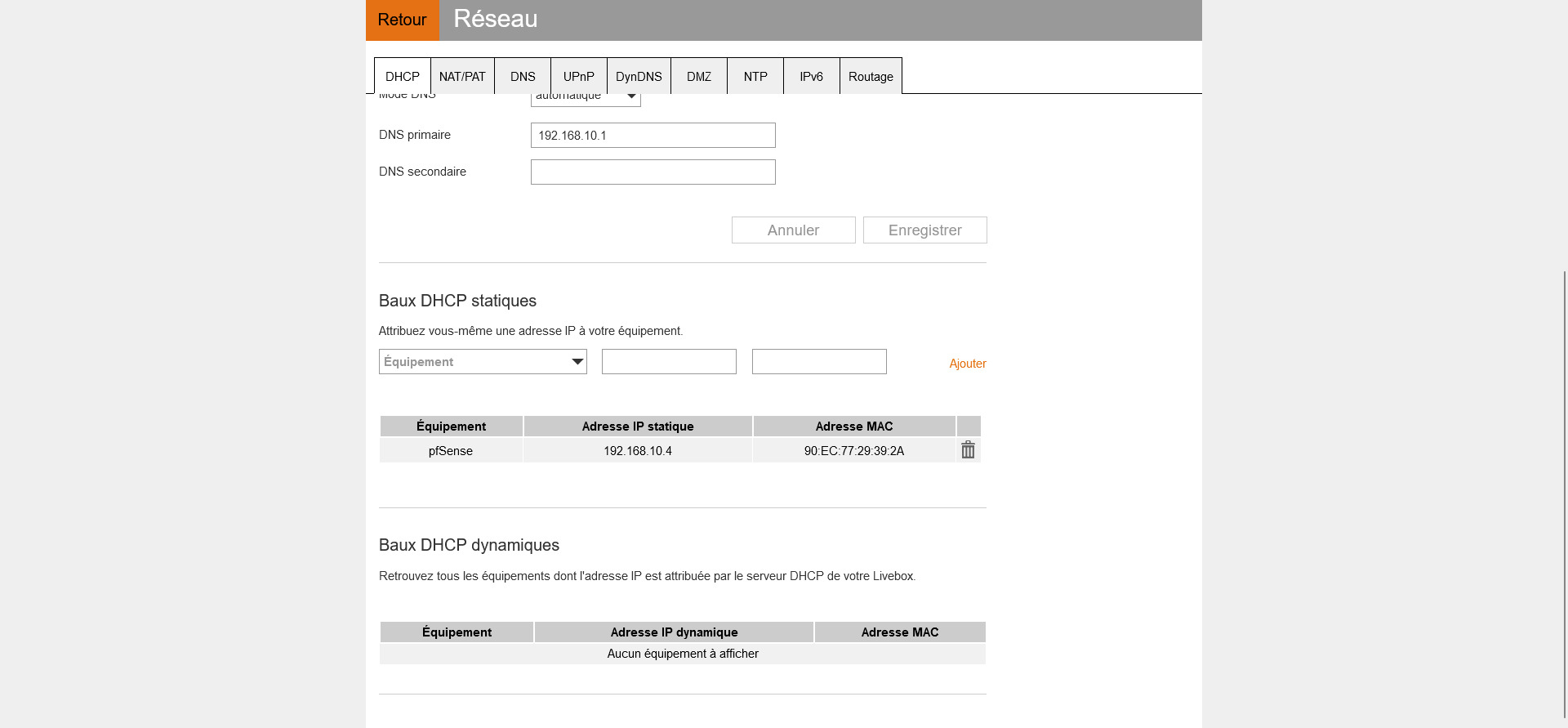
My pfSense uses 192.168.10.4 (yours 192.168.10.22).
"90:EC:77:29:39:2A" is the MAC of my pfSense WAN NIC.I can see that my Livebox (ISP router) NATs traffic that comes into my ISP router's WAN port, with destination 'port 1194' and protocol UDP, to the WAN IP 192.168.10.4, my pfSense WAN.
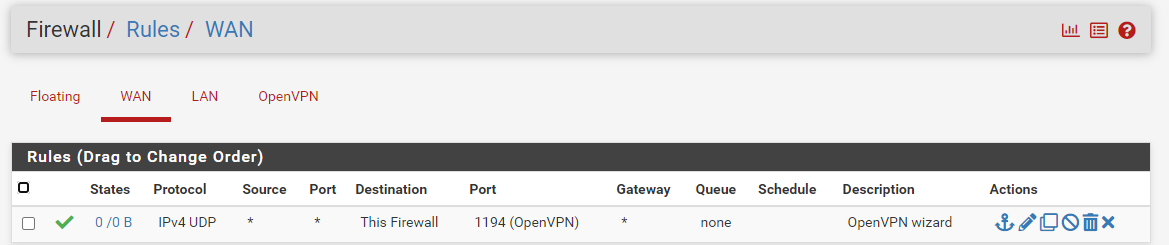
In pfSense, it matches the first rule :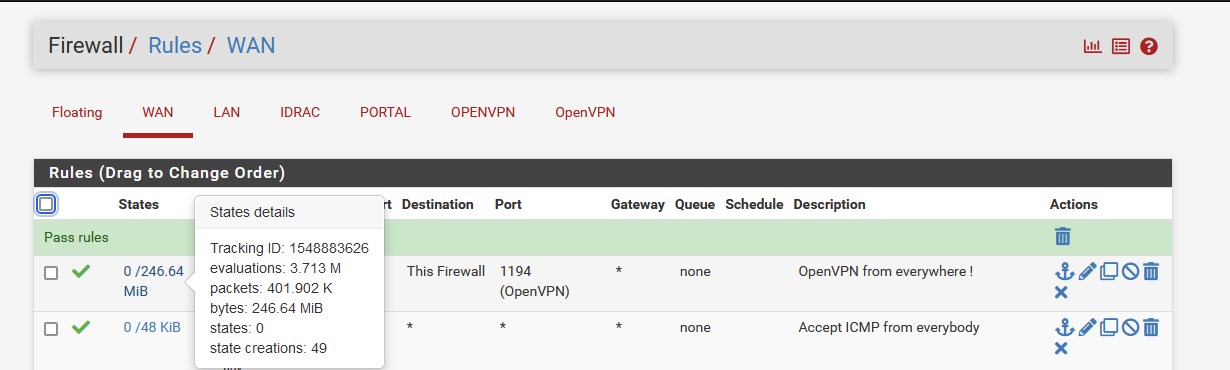
so the traffic enters 'pfSense' , and there, in pfSense, on the WAN interface, the openvpn process welcomes these packets as it set iself up as process listening on WAN, port 1194, protocol UDP.
@kilian77 said in Problem configuration OpenVPN:
I realized without doing it on purpose that if I did the wifi test my configuration worked, so the problem may be coming from my router?
When testing, use, for example, a Phone, and stop the Wifi. Use 4G/3G only.
Use the WAN IPv4 of your Livebox as a destination.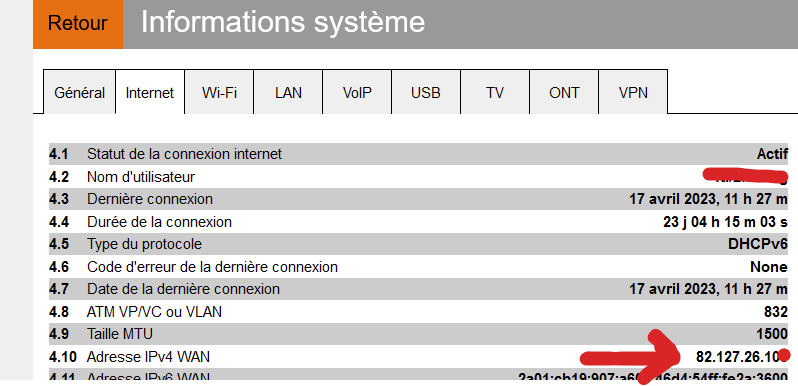
-
@gertjan As you can see, on my side the traffic does not pass :
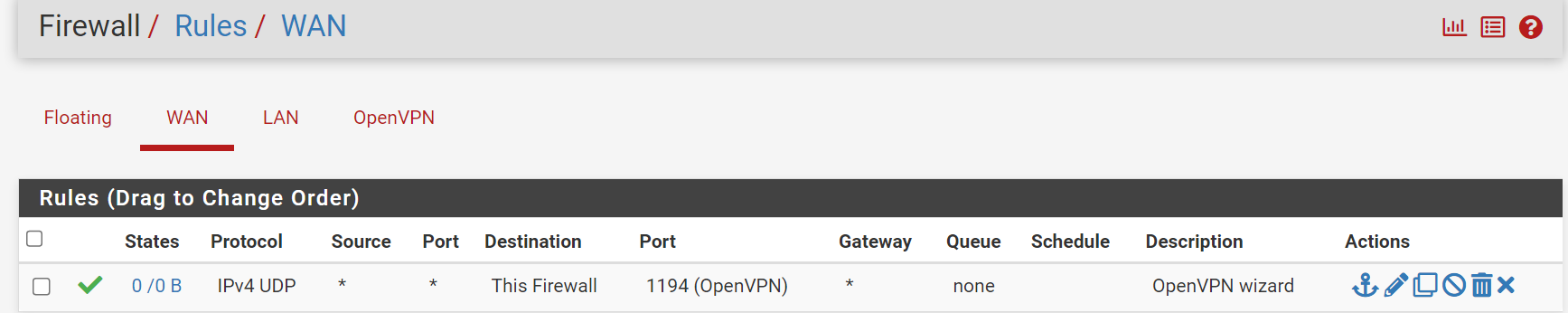
but also when you tell me to use the WAN of my livebox, I inform it where? -
@kilian77 said in Problem configuration OpenVPN:
the traffic does not pass
It's not 'does not pas'.
See for yourself :
Check :
and re try.
Now check the
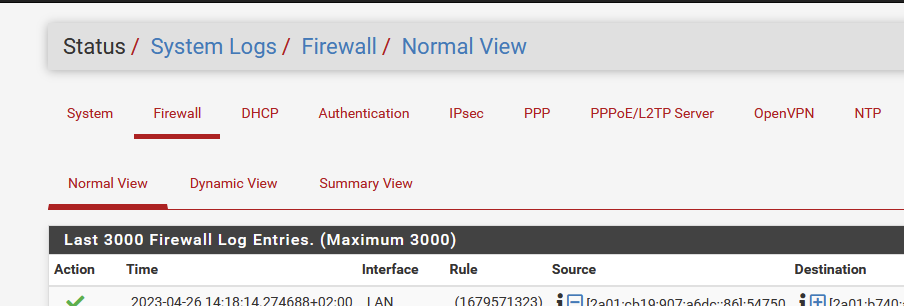
do you see any packets blocked on the WAN ?
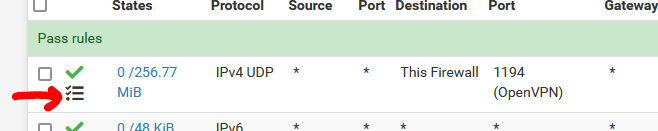
Probably not.Check the packet counter hit box of the firewall rule on your WAN :
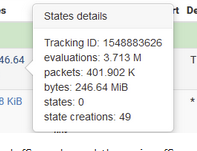
If it's 0/0 then tat means : nothing ever reached the WAN interface of pfSense.
Maybe stupid, but important : pfSense can not pass or block what doesn't even reach pfSense.
What is your WAN IP (mask the last digit) ? VSDL ? ADSL ? Orange Fibre ?
I've being NATting my Livebox 4 adsl, 5 (Pro) adsl and now 6 (Pro) using fibre, for years.
It works. -
@gertjan hello, without having done anything I am no longer at 0
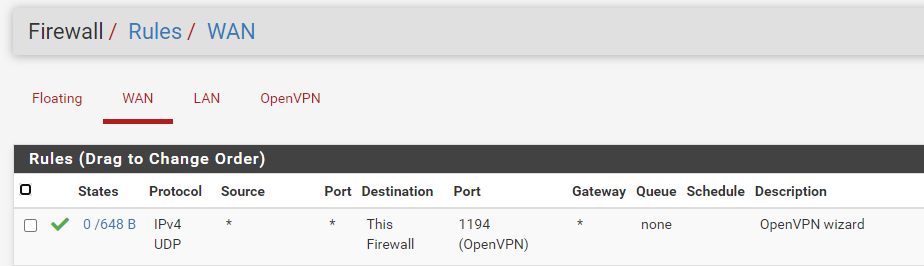
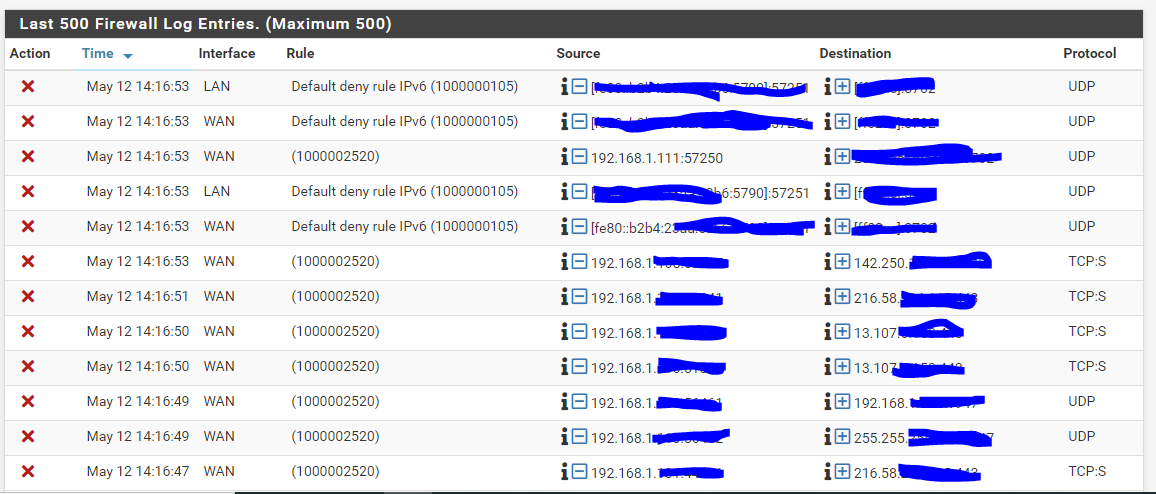
I use a livebox 4 or a livebox Pro V4 both in fiber.
-
Who is 192.168.1.111 ?? Who is this ? a pfSense LAN (right ??) device - why should it connect to the pfSense WAN ?? Going 'out' to get back in ? To where ? to some pfSense LAN device ? The device 192.168.1.111 is already on the pfSense LAN, and it can connect to every device without the need to 'pass by pfSense'.
Tip of the day : make the OpenVPN pas rule log :
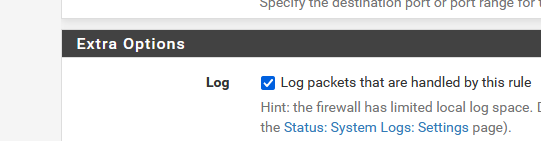
=>
Now you can see what / who is using the OpenVPN pass rule. -
@Gertjan Hello, sorry for this late return, I was absent, suddenly in my logs you can always see that there are lots of things and my public ip is 92.170.84.1XX.
I added the option for the logs but the rule fell back to 0/0 B.

-
pfSense uses 192.168.10.22 - and it obtained this IP using DHCP.
I was given to pfSense by your Livebox.You have other devices connected to the Livebox : why ?
I've only one device connected ** : pfSense. So nothing tries to connect to my pfSense from 'the outside'.** : ok, I've one other device : the Orange TV box - but that box only connects to the outside world (the Internet : the Orange TV servers), and it's nothing roaming around locally, on its LAN.
So : 192.168.10.9 - 192.168.10.10 - 192.168.10.3 : these are local broadcasts on there Livebox LAN, the pfSense WAN sees these inoffensive packets and blocks them.
Consider stopping the logging of the "Default deny rule IPv4", as it logs just broadcast noise.
-
@Gertjan
ok but i still don't understand what is blocking my vpn -
@kilian77
Your WAN firewall rule (placed at the top - f you have more then one WAN rule) is logging ?
Do the counters go up ?If : no logs and/or the counters stay the same : that means traffic isn't reaching pfSense.
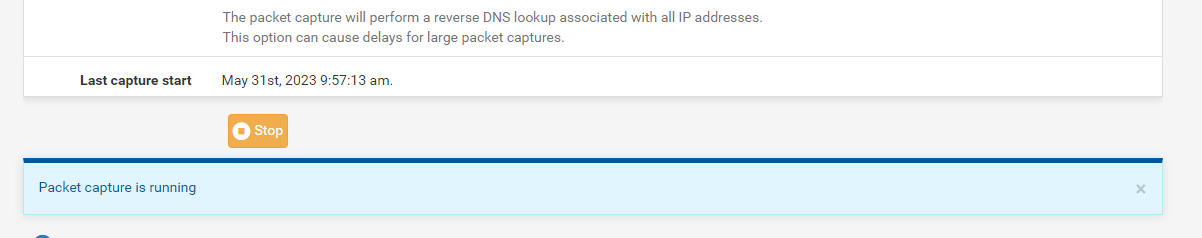
You can also test with this :
The pfSense packet capture :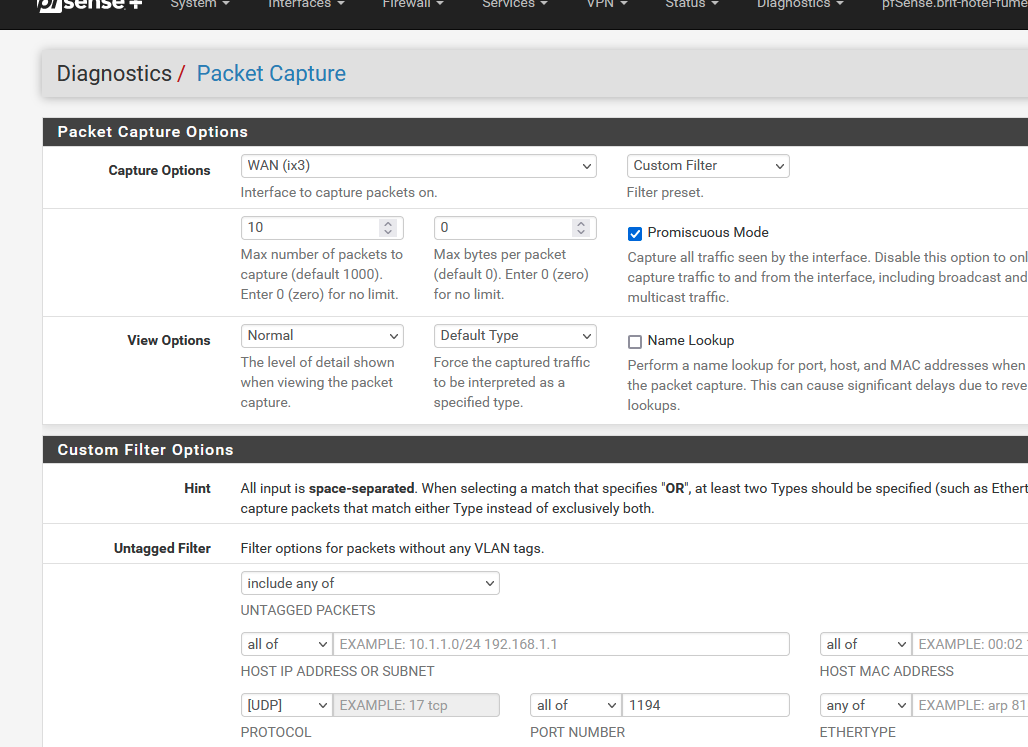
I've selected my WAN (ix3), protocol UDP, and port 1194.
I wanted '10' packets.
The result was shown in a couple of seconds, as I was the using OpenVPN server at that moment => I had to use OpenVPN to connect to my 'work' Livebox, as pfSense to do this test ;)So : can you capture traffic ?
If not : check Livebox.This is probably not needed, but I've set it :
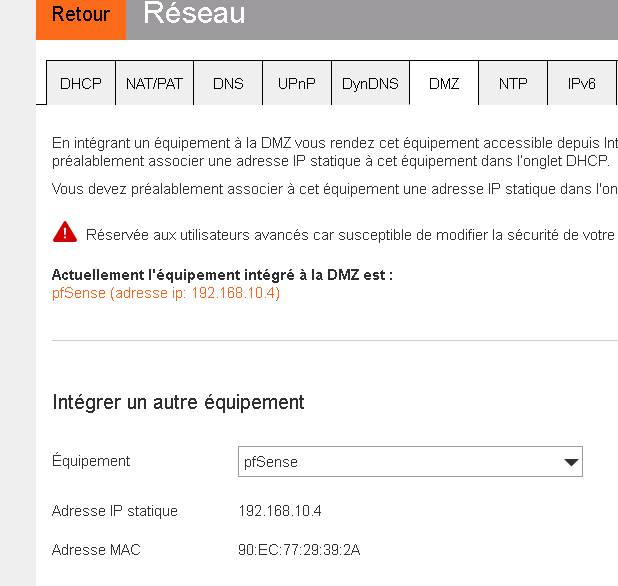
as pfSense is my only Livebox LAN device, I asked Livebox to redirect all incoming traffic to the DMZ : pfSense3
-
-
Well, all depends what you are the conditions of the capture.
But if you set up the conditions as I did : nothing reaches pfSense - so nothing to capture.
The OpenVPN server never receives any traffic.Something to test your livebox NAT firewall skills :
First :
Can you access your pfSense from LAN using : http://192.168.10.22( and for my won curiosity : why 192.168.10.22 ? 192.168.10.1 == ok - If you have to, 192.168.10.254 - but why 10.22 ?? Strange IP like that, that smell's troubles from x miles away )
if so : go lvebox, and NAT port 80 TCP to 192.168.10.22.
From now on, with your phone - phone NOT connected to Wifi ( !! ) you can access pSense GUI from 'the Internet'.
Do this for testing, don't leave this Livebox NAT rule in place.
I just did this test on my side :
First : Livebox : port 80 and 443 TCP :

Next : pfSense : idem :
I called my neighbor, and asked if they could try http://82.127.26.10x
He said there was a certificate error (that's normal, as my pfSense is redirecting port 80 to port 443) but when he clicked on "Go ahead anyway" he saw the pfSense GUI.Btw : if any of the other devices connected to the Livebox uses uPNP, that I can image that NATting doesn't work, as destination ports are already used by other devices : solution : de-activate uPNP.
Double check that your WAN IP is not some kind of NATted IP (CGNAT) .... I think Orange doesn't do that .... but anyway : check.
And finally, for 'reasons' Orange can 'firewall' you from their side. Never saw them doing that myself ... but, hey, why not .... we see every day something new ;)
-
@Gertjan So, yes I can access the interface with the address 192.168.10.22.
The address is 10.22 because I already have other devices that have IPs generated before 22, that's all.
the NAT test is inconclusive
-
@kilian77 if the wan router in front of psfsense is using 192.168.1 as its network, then pfsense wan would need an IP on the 192.168.1 network.
How exactly do you have things connected.. Your showing traffic hitting your wan coming from 192.168.10 addresses..
internet -- isp router -- 192.168.1 -- (wan) pfsense (lan) - 192.168.x
Yes your pfsense lan has to be a different network than the wan.. But the wan has to be in the 192.168.1 network if that is the network your isp device is using..
-
@johnpoz
Hello, no my ISP router is also in 192.168.10.X -
@kilian77 said in Problem configuration OpenVPN:
Hello, no my ISP router is also in 192.168.10.X
What do you mean by 'also' ?
Can you make a drawing with all the IP addresses / networks / Network names on every router side ?
-
So you changed it from the 192.168.1 it was using?
Yeah a drawing would be helpful your not plugging everything into a dumb switch - ie both wan and lan?
-
@johnpoz my ISP router: 192.168.10.1
my pfsense WAN port: 192.168.10.22
my pfsesne LAN port: 192.168.1.1