firewall all ports blocked
-
hello.
i have blocked all the ports in the firewall of a captive portal opening only ports for whatsapp. The problem is that it gives me an error when connecting since the captive portal does not connect well. I have opened ports 8000,8001 and 8002 so that it connects to the captive portal ip but it still doesn't work.
Is there any other ip port that I have to open?
THANK YOU -
@Andoniar78
Which error?
Consider to allow at least DNS for name resolution. -
@Andoniar78 said in firewall all ports blocked:
Is there any other ip port that I have to open?
For the portal to work, you have to have at least one rule :
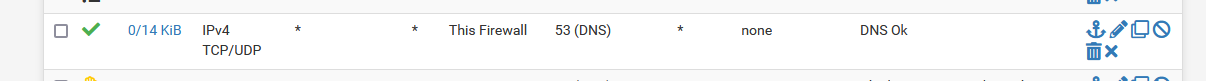
The second, last & 'hidden' rule will block everything.
Now you can connect to the portal.
But you can't 'do' anything.If you want certain apps to function, you need to know the ports they use. If possible, combine these with the IPv4 they use.
@Andoniar78 said in firewall all ports blocked:
I have opened ports 8000,8001 and 8002
Not needed.
As said above, just the TCPv4 UPD and TCP, destination (to the firewall) port 53 will do.
I was able to connect to my portal using just that one rule.Btw : Whatsapp == facebook.
That means an awful lot of IPv4 addresses, probably entire networks. -
@Gertjan
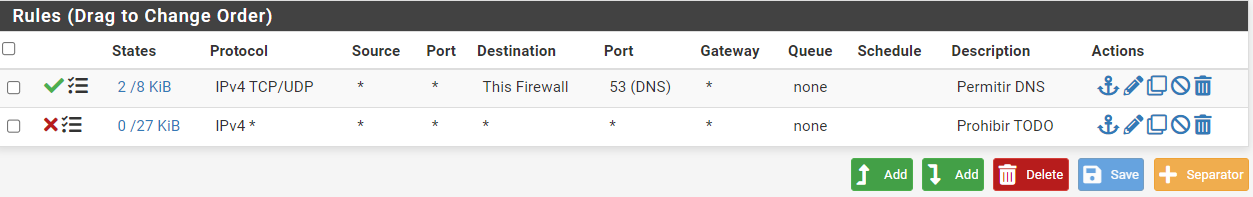
no working this way...
what do you mean with "hidden" rule?THANK YOU
-
@Andoniar78 please look here
I would suggest you validate the captive portal works before you try and block whatever it is you want to block.
-
@Andoniar78 said in firewall all ports blocked:
what do you mean with "hidden" rule?
PfSense and most firewalls have a default rule on all interfaces to “block all” therefore only traffic that is allowed via rule is allowed. This is why LAN has added “allow all” rules but WAN has no added rules out of the box.
-
@Andoniar78 said in firewall all ports blocked:
what do you mean with "hidden" rule?
pfSense is - among others - a firewall.
A whole lot of nice screens, but never forget to look at this file : /tmp/rules.debug as that copy was loaded into the firewall.You'll find in there the rules that are defined as the 'last rule' for every interface :
#--------------------------------------------------------------------------- # default deny rules #--------------------------------------------------------------------------- block in inet all ridentifier 1000000103 label "Default deny rule IPv4" block out inet all ridentifier 1000000104 label "Default deny rule IPv4" block in inet6 all ridentifier 1000000105 label "Default deny rule IPv6" block out inet6 all ridentifier 1000000106 label "Default deny rule IPv6"which stands for : nothing gets in, neither out.
For IPv6 and Ipv6.