How to enable IPS - Blocked Offenders is enabled
-
I used to be able to do this in Inline mode but its no longer an option for me.
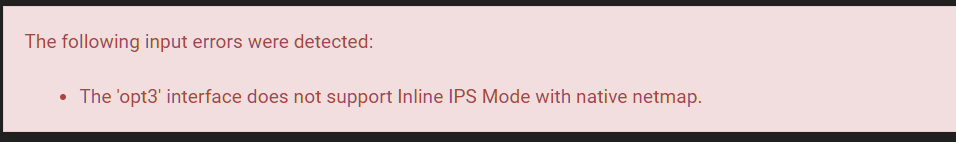
There are several categories i want to switch to Drop. I used the SID Mgmt link but the Drop SID List option is no longer available. I am currently using Legacy Blocking mode but there doesn't seems to be a way to mass-enable multiple categories. Essentially all my rules are set to Alert regardless that I have Blocked offenders checked off.
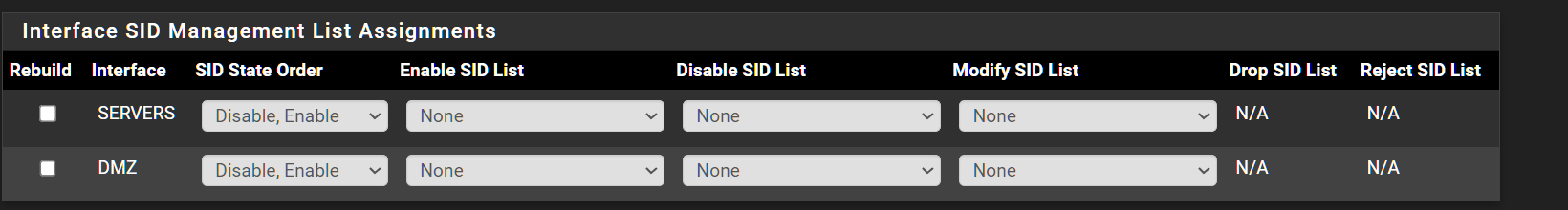
-
@michmoor said in How to enable IPS - Blocked Offenders is enabled:
I used to be able to do this in Inline mode but its no longer an option for me.
As I am informed or better was reading about there
are still some NICs that can be used together for the inline mode, I mean working well with them.So could you tell perhaps a bit more about
your interfaces (NICs)? -
This is a Netgate 6100
-
Which IDS package are you running -- Snort or Suricata?
If Snort, then it thinks the NIC is not native-netmap compatible. That determination is made by comparing the physical NIC driver name to a list in the PHP code. If there is no match, the error you posted in red is printed. Which type of NIC driver is showing as being used for OPT3 on your SG-6100?
If the IDS thinks your NIC does not support native netmap mode, then it will hide non-applicable Inline IPS Mode options. That is what you are seeing on the SID MGMT tab (that's why Drop SID List is blank).
If you are running Suricata, then you can enable the option for Block on DROP Only in Legacy Blocking Mode on the INTERFACE SETTINGS tab. That mode emulates Inline IPS Mode in terms of letting you specify different rule actions for various SIDs. Note this mode does not literally behave the same as Inline IPS Mode. It simply lets you emulate the same rule actions. With this optional Legacy Blocking Mode enabled, only rules whose action verb is DROP will generate a Legacy Mode block. This option is only available for Suricata. Snort cannot perform the same way with Legacy Mode Blocking due to the way the binary is plumbed.
-
@bmeeks
I am running Suricata.How do i find out what NIC drivers the system thinks it sees?
This is a LAGG interface.Running pciconf -lv i get the following output
igc2@pci0:6:0:0: class=0x020000 rev=0x03 hdr=0x00 vendor=0x8086 device=0x15f3 subvendor=0x8086 subdevice=0x0000 vendor = 'Intel Corporation' device = 'Ethernet Controller I225-V' class = network subclass = ethernet igc3@pci0:7:0:0: class=0x020000 rev=0x03 hdr=0x00 vendor=0x8086 device=0x15f3 subvendor=0x8086 subdevice=0x0000 vendor = 'Intel Corporation' device = 'Ethernet Controller I225-V' class = network subclass = ethernetEDIT: The IPS - Connectivity policy that i have set still has all actions set to alert. How can this be changed? I am set to Block on Drop.
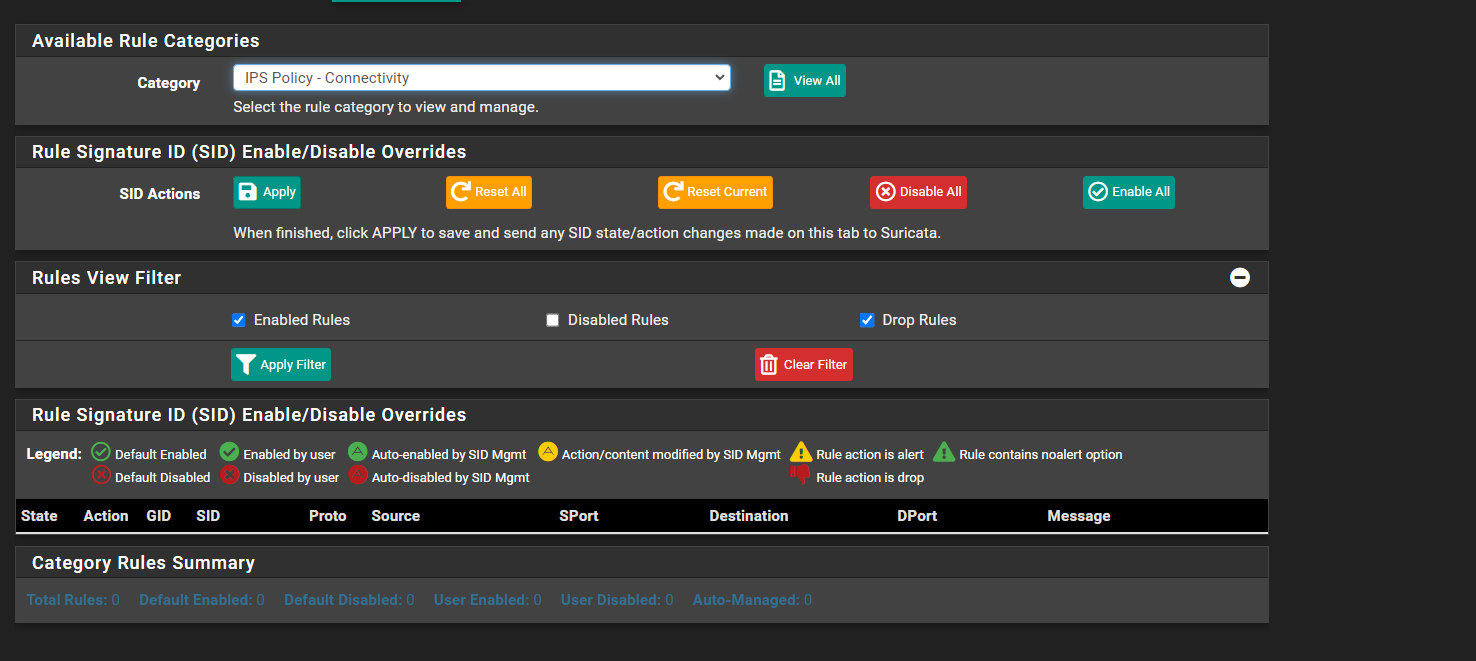
Is the logic here that the Connectivity setting is all about alerting and not dropping?
edit: i have attempted to change from alert to drop usingpcre:"pcre:connectivity-ips\s*drop"doesnt work.
-
Several things I need to address in your reply.
-
Looking at the PCI configuration info it appears the SG-6100 is using the
igcNIC driver for the Intel I225-V chip. Theigcadapter is supported for native netmap operation, but not when used in a LAGG setup. That LAGG interface is a virtual construct of FreeBSD and not a physical interface. Netmap will not run on a LAGG in native mode. There is work going on to improve netmap performance on virtual interfaces running in emulation mode. But none of those patches have been accepted fully into upstream so far as I can tell. They definitely are not currently in the FreeBSD branch used by pfSense. Klara Systems and the OPNsense team are working on these improvements. -
You appear to have a fundamental misunderstanding of what the Snort VRT IPS policies are about. Each configurable IPS policy has both ALERT and DROP rule actions. Which rule in a policy gets assigned which action is determined by the policy author. The choice is influenced by several factors including how likely the rule is to false positive. The same rule SID may have an action of ALERT in one policy and an action of DROP assigned in another policy. If you have not yet, go read this old Sticky Post I created for Snort Inline IPS Operation. It applies to Suricata as well: https://forum.netgate.com/topic/143812/snort-package-4-0-inline-ips-mode-introduction-and-configuration-instructions.
-
If you want to use an IPS policy, then follow the instructions in the Sticky Post link above. If you want to block traffic on your LAGG interface, you are going to be limited to Legacy Mode blocking. You can use the optional Block on DROP Only mode with that to allow you to have both ALERT and DROP rules configured. This Sticky Post describes that mode: https://forum.netgate.com/topic/119237/about-the-new-block-on-drops-only-option-in-suricata-4-0-0.
-
-
@bmeeks I meant to update this thread before your response. Beat me to the punch.
My misunderstanding is really how to work with the GUI in regards to IPS/IDS. Some of the elements aren't exactly clear so it did require poking through several threads here to understand how the pieces work.