Using a imported Lets Encrypt cert giving "certificate not from a trusted source" on login page
-
I have my captive portal working with non-ssl and today I have been trying to get the SSL certificate process working. My SSL certs come from Let's Encrypt and NGINX proxy manages the certs for me. I exported the cert for the url to the login portal with a CN of:
cplogin.vargofamily.com
Imported the cert1.pem and privkey1.pem from the download key from NGINX proxy manger and imported into the certificate manager in pfSense:
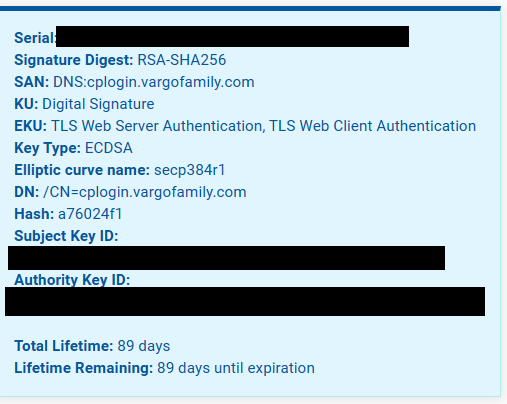
When attempting to login with Android I get the following message:
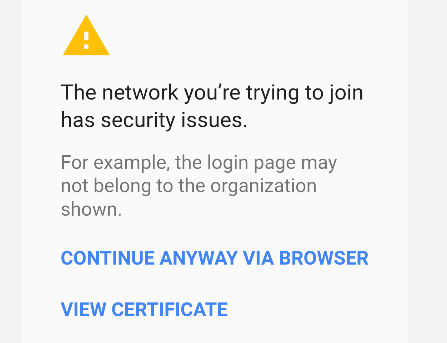
And when I look at the cert this is what baffles me:
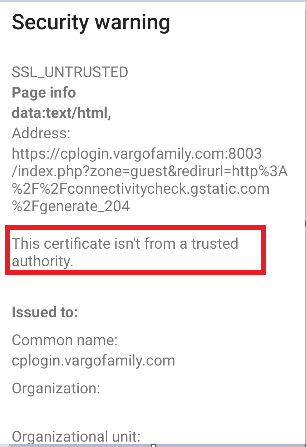
This cert isn't from a trusted authority. But yet it's signed by Let's Encrypt.
Am I missing something here? I also tried with my wildcard cert which I use internally just fine with my lab and have the same messages about the cert and it also is a Let's Encrypt generated cert.
-
@ronv42 That warning would be from your browser.. if your browser doesn't trust lets encrypt CA. Maybe it was removed from your trusted CAs. Or the trust altered?
You need to look at your trusted Authorities in your browser or your overall system, depending if you browser keeps it own trust store, or uses the system store.
If you look at your certificate you can see the trust chain.
So for example here is a lets encrypt cert I use for one of my sites - see signed by R3, R3 was signed by X1.. Browser (firefox) trusts X1, so in turn it trusts R3 (the intermediary CA).. So in turn it trusts the cert signed by R3..
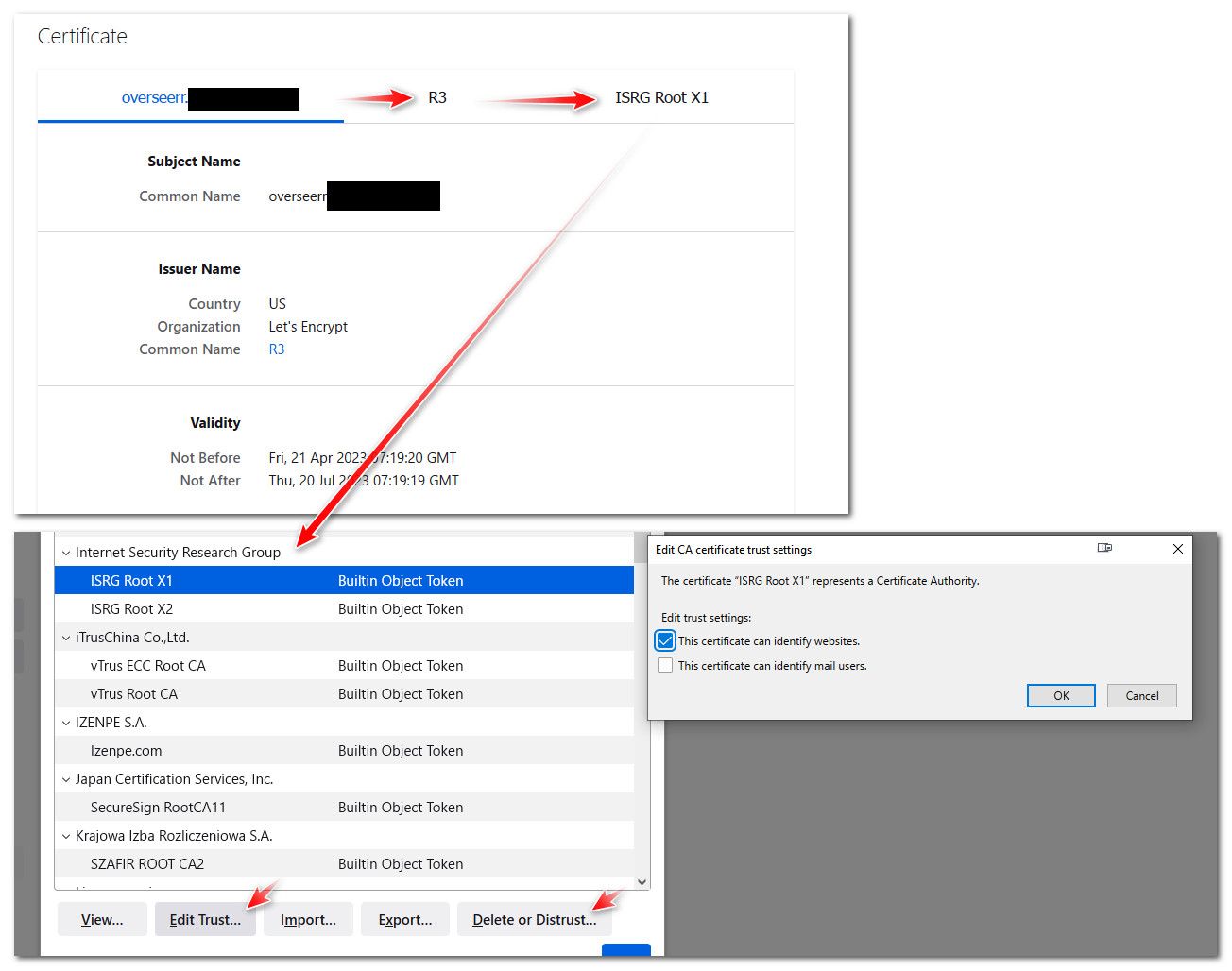
You need to look to why your browser doesn't have the CA from ISRG listed, or doesn't trust it.
-
@johnpoz Thanks, I will do some more exploration today. I know that in the downloaded zip of the certs there is the:
cert1.pem
chain1.pem
fullchain1.pem
privkey1.pemThe import into I pfSense only asked for the cert and private key. When I import into other applications like Synolgoy they ask for private key, certificate, and intermediate key chain.
More fun on a Saturday...
Solved it. Needed to use "fullchain1.pem" for the certificate field. Problem went away. It was your detailed walk though example that lead me to think to this.
Thanks again @johnpoz