Very simple vlan tip
-
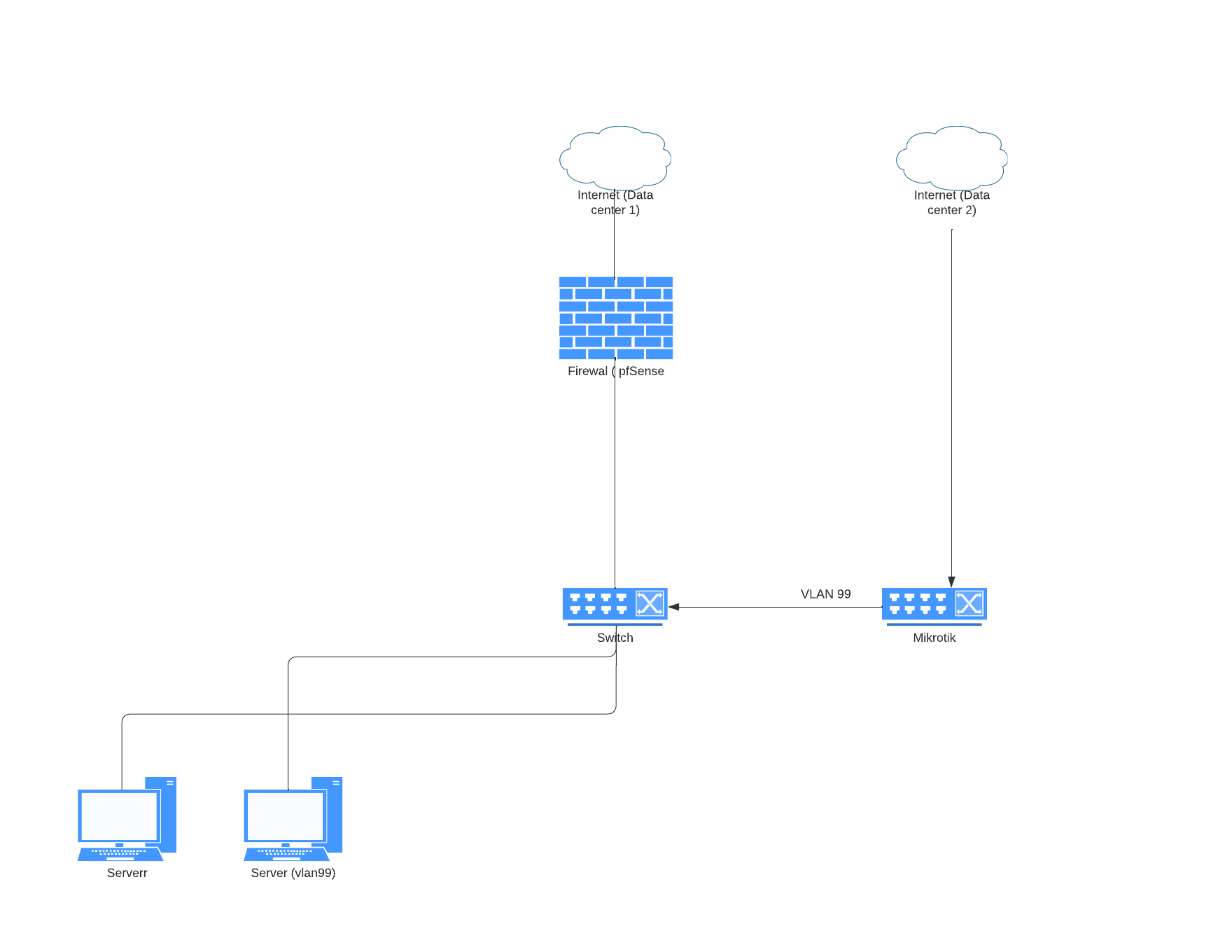
Goal: have a private connection between two data centers (switch-to-switch) - without interrupting any other stuff or doing any routing. It works without VLAN today, but broadcast traffic is everywhere.
Could anyone tell me how the layout for trunk/tag/untag the ports on Switch 1 (Data center 1) and Switch 2 (Data center 2)? Let's assume port 10=data center 1 and port 20=data center 2. I assume the link port 10 to port 20 would be considered trunk-port, but in this case (with only one vlan supposed to go through), I also assume I could have both ports as Tagged vlan99? That would block everything from passing between the two.
I do need to keep the servers in data center 1 to access the internet in data center 1 even if a server there gets access to VLAN99, so dual membership for them..
-
You don't route VLANs. You route subnets. Route the traffic between sites and recreate the VLAN at the other end. I assume you have different subnets at each end.
-
@fireix said in Very simple vlan tip:
but broadcast traffic is everywhere.
Well yeah if you just connect vlan 99 into a dumb switch or one with out vlans setup then yeah multicast and broadcast is going everywhere because you have one big L2 there.
You need to setup the switch in DC 1 to isolate your L2 networks. Be it you route between the L3 networks you put on them is up to you. But sure you could put devices in dc1 either on the vlan you setup on this switch and vlan 99..
-
@johnpoz For a long time, I had 10 Gbps on a private subnet shared between the two data centers (same network). But then I had to try to do routing in DC2 - it worked great (only traffic I wanted went over it) until I tested speed. It destroyed the speed of Mikrotik completely
 iperf reported 10 Gbps speed before routing, but once I put an IP on that on the other side - in DC2 - it went down to 300 Mbit maximum (and 100% cpu usage on Mikrotik) since enabling this outside the bridge destroys in-built performance.
iperf reported 10 Gbps speed before routing, but once I put an IP on that on the other side - in DC2 - it went down to 300 Mbit maximum (and 100% cpu usage on Mikrotik) since enabling this outside the bridge destroys in-built performance.When I cleared all settings and tried to get it back to single broadcast domain (at least better than reducing speed for the backup-traffic- connection), it seems like some switches in DC1 wants to send wrong traffic to Mikrotik in DC2 and cause issues with the normal operations in DC1 since that's not the way to send data. I can't get any traffic to access the earlier private shared subnet behind Mikrotik (only from DC2 to DC1 works 100% and only ping from DC1 to Mikrotik in DC2 works).
-
Instead of focusing on VLAN, I have focused on trying to get routing up and.
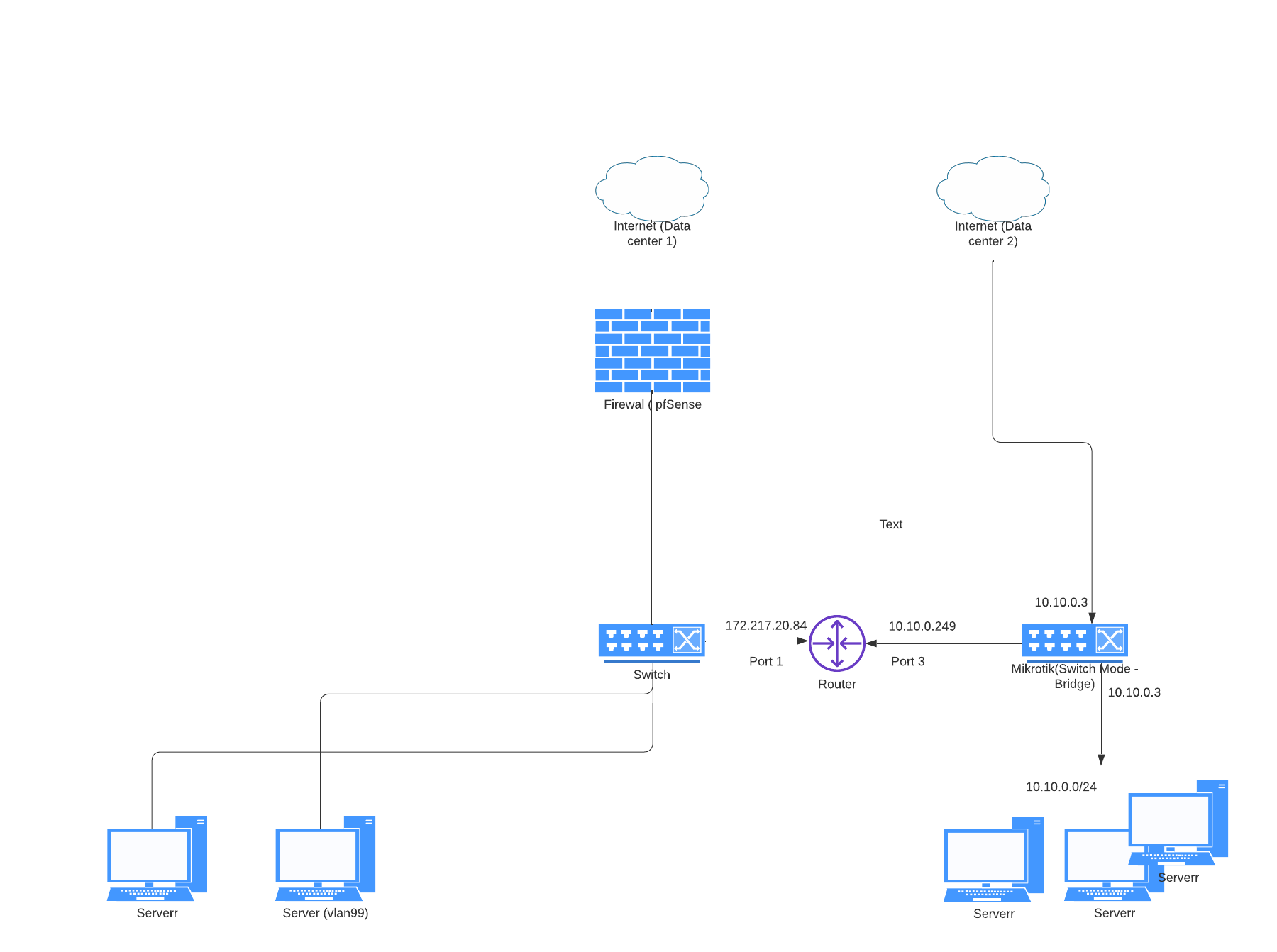
I had a small Mikrotik router laying around with 10 Gbps fiber and I put it on one of the data centers, between the switches in the to places as you see on drawing. I used DHCP to get the IP you see on Port 3 of the Router. So far so well.
I can ping the DC2's Switch IP-address 10.10.0.3 from DC1/router in DC1 without issues and I can run bandwidth-test between the two switches in the two data centers. However, I can't ping from Router against any IP-addresses in the 10.10.0.0/24 network at all (except the bridge IP on SW2 10.10.0.3) - even though I have been given a router DHCP IP-address in correct subnet.
Am I correct that I do need to both do some nat/masquerading and firewall rules to accomplish this - should it be the only thing missing?
PS: The mikrotik is in bridge mode with all ports - including the one that connects to Port 3 on router - is on the same bridge. Equipment inside the data center can ping the bridge-IP.
-
@fireix Seems like I'm onto something...
input: in:bridge out:(unknown 0), connection-state:new src-mac dc:2c:6e:a4:ce:df, proto UDP, 10.10.0.249:5678->255.255.255.255:5678, len 193
Log from switch in DC2: This occur during ping from DC1 - so it has passed the router I inserted and arrives at the switch in DC2! But it doesn't actually reply on those pings...
-
Solved it



No fw rules/nat needed it seems. I pulled out the connecting ports in 10.10.0.3 switch from the bridge interface in DC2 and created a private 192.168.4.10/192.168.4.20 router-to-router(switch) on each side. And added route from each oposite sides network to eachothers gw.
Can't find any issues so far :)