Can't access LAN over Wireguard
-
-
@Samalpetey I didn't use that video when I set up my remote access, I prefer reading instructions rather that being told by someone who could have done a video lasting 60 minutes but fast-talking made it in 27 :)
What I found interesting was that a client could specify the allowedIPs to be used. Surely pfSense must have a way of controlling the allowedIPs, basically blocking wherever a client tries to go (but isn't allowed). So perhaps Firewall / Rules / Wireguard tab is needed to let through / block the remote access network clients?
And maybe try and find other instrctions and compare them to the video could be a way forward?
-
@pst said in Can't access LAN over Wireguard:
perhaps Firewall / Rules / Wireguard tab is needed to let through / block the remote access network clients?
I just checked my wireshark rules and I have pass rules for traffic between my remote access network (src) and my LAN (dest).
-
@pst When I disable the pass rule I can't access my LAN which proves the rule is needed. (I also removed my "odd" peer configuration so now it only contains one allowed IP)
-
@pst Mm, I've already got that set up, see below image. On the client side, allowedIPs just specifies which IPs are being sent through the tunnel. In my usecase, the clientside allowed IPs are set to 0.0.0.0/0, which should route all traffic through the tunnel.
That's what's bizarre to me here. Clients are handshaking, NAT and firewall rules are set... so I don't understand what's stopping it working.
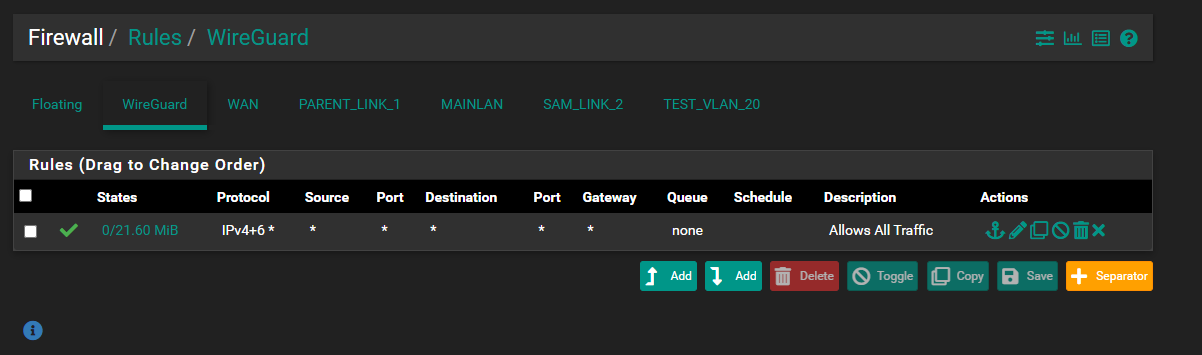
-
@Samalpetey
Sniff the traffic with the Packet Capture utility on the WG interface, to see if the packets come over the VPN, when accessing a LAN device.
If you see access packets, sniff the traffic on the LAN interface as well to check out if the packets are passed by pfSense. -
@Samalpetey I aligned my rules with yours and it still works.
How are you accessing the LAN machines? FQDN or IP address? Is DNS working? I remember having to allow DNS queries from the remote access network specifically.
Is your tunnel connected to an interface? Mine is with static IP address (10.1.1.1/24), no uplink gateway,
-
@viragomann Hm, this is even weirder now. Thanks for the advice by the way! First time sniffing traffic but it was fairly simple. I ran the packet sniffer to detect icmp v4 traffic over the wireguard interface, then over the bridge that is my main LAN interface. I can see ICMP traffic on both interfaces, from 10.66.66.2 (wireguard client) to 10.247.1.13 (device I want wireguard client to reach).
Of note: In the past I made a test lan (10.247.2.0/24) and everything on said lan was able to ping 10.247.1.13 just fine, so I don't think it's a device firewall issue. I've attached my packet captures below, both taken while running a continuous ping on my laptop (10.66.66.2) to 10.247.1.13.
-
@pst Ip address for LAN, dns is working fine though. As I outlined earlier, my tunnel was not set to an interface, but was working identically on and off an interface. I have however now assigned it to its own interface in order to sniff traffic.
-
@Samalpetey said in Can't access LAN over Wireguard:
Of note: In the past I made a test lan (10.247.2.0/24) and everything on said lan was able to ping 10.247.1.13 just fine, so I don't think it's a device firewall issue.
From where?
From inside the LAN, I guess. My suspect is, that traffic from outside is blocked, as mentioned. The system firewalls differ access from local network and from outside.You had captured ping requests only on LAN. Not even any reply from 10.247.1.13 at all.
So either the 10.247.1.13 is blocking access from outside or the traffic is routed to anywhere else, but the firewall. -
@viragomann AHA! I figured it out now! So, that client (10.247.1.13) used to have my wireguard server running on it, and I never uninstalled it. So I THINK that ubuntu server had static routes set up for traffic on the 10.66.66.1/24 subnet, and was sending traffic to those subnets into the void. After uninstalling wireguard on the server, pings are now working between my windows machine connected via wireguard and the server at 10.247.1.13. Still can't ping windows to windows, but I'm guessing that's a firewall issue and I can look at that in my own time.
Thanks for the help folks! I think we can consider this resolved now.