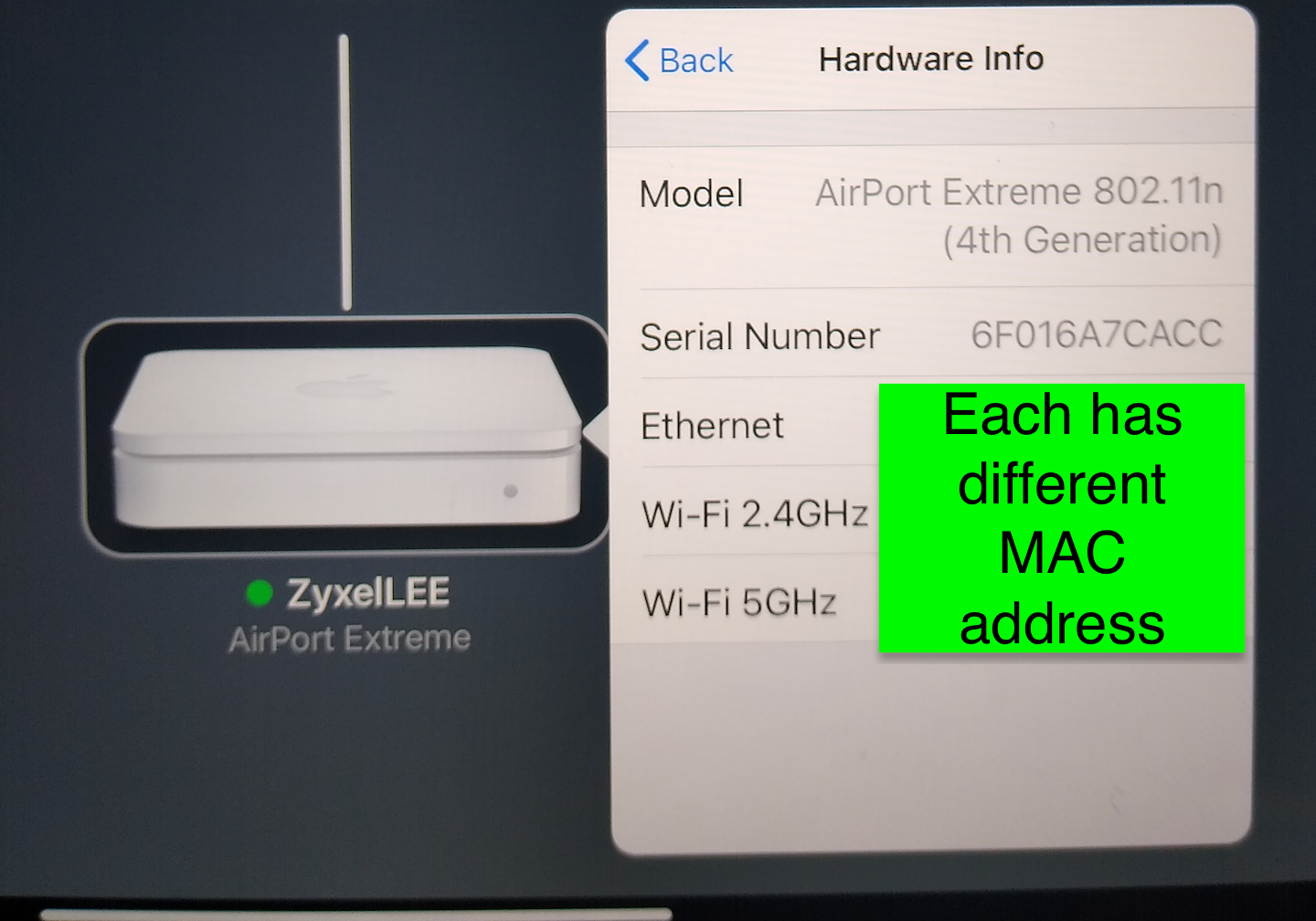
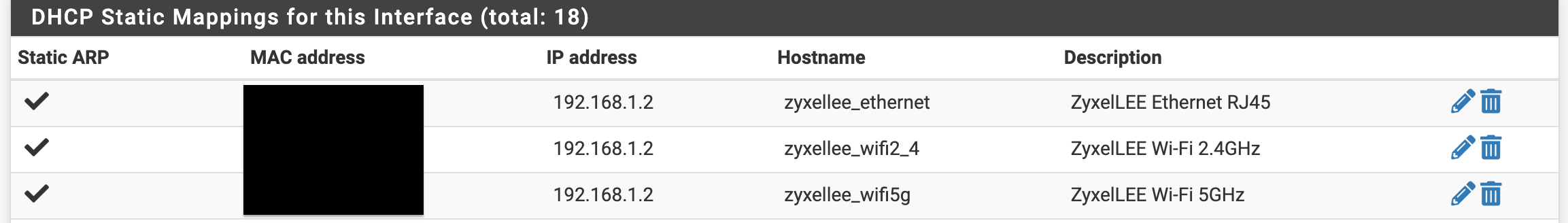
AP with onboard built in NAS abilities/multiple MAC Hardware Layer 2 addresses
-
@JonathanLee Each BSSID will get a similar MAC address with the last hex character being different. Represents each WLAN you have set up. Totally normal.
-
@michmoor Thanks for the reply, I understand that I am just wondering If I need to add a mac-ip pair for each of the hardware addresses on the AP if it is in bridge mode so the firewall does not have to do arp requests over and over for the devices it would already know it.
-
@JonathanLee what problem are you trying to fix?
-
@michmoor less arp requests/multicasting broadcast storms
-
@JonathanLee tbh thats not really a problem. arp is what makes ethernet work. So to ask the question another way, is there something negatively impacting the usability of the network because of ARP?
-
Yeah, are you actually seeing more than one MAC address at pfSense?
If not then there's no point adding entries for them.
-
@JonathanLee said in AP unit has multiple MAC Hardware Layer 2 addresses:
ess arp requests/mulicasting
While you can trim down multicasting by some devices/OSes - or see your other thread where I block some multicast on my switch.. Arp kind of makes the whole networking thing work ;)
Depending on your arp cache on different devices some devices might arp for say their gateway more often then others. I think like the arp cache on windows is only like 30 seconds or some random below that.. While freebsd (pfsense) default to say a 20 min arp cache, etc.
But as mentioned already AP are going to normally have multiple mac address, one for the eithernet, one for each radio - and yeah if you create more SSIDs they will create a mac address for those, etc.
-
@stephenw10 I have seen the 5GHz pop up once and awhile under leases again it will only list the one MAC-IP pair at a time
-
@michmoor @stephenw10 @johnpoz
This config change actually speeds up my network drastically with noticeable speed increase on the LAN side browsing. No clue why, I assumed that the static arp table would not need it set at the firewall. Again I changed the AP to use IPv6 locally and off automatic maybe that caused the speed increase as I have no IPv6 from my ISP.
This is the weird part the arp table now lists hostnames for the other static mac-ip pairing like it is using both but won't list it in the GUI. It should match the correct host name right?
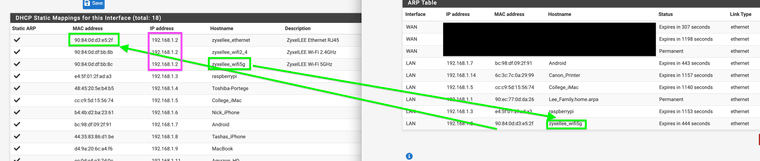
It appears to have swapped the host name and MAC mappings for what is statically assigned here. Is there anyway at all to log a BSSID mapping? -
@JonathanLee Your AP should not be pulling dhcp for any mac other than its management IP, which is normally on its ethernet.. Unless your doing wireless uplink, a mesh sort of AP..
And your AP using ipv6 for its management would have ZERO to do with clients speed that is for sure..
-
@johnpoz Thanks for information today. I did some good researching today. I did get it to mix up the hostname/ip-mac pair in the arp table. I always wondered about the bridge mode if it needed all the mac addresses for the AP
-
@JonathanLee said in AP unit has multiple MAC Hardware Layer 2 addresses:
Does pfSense require entry for all three MAC addresses for a AP unit like this?
Why are you worried about the MACs on the WiFi side of the AP? You'd normally use the LAN interface when configuring it, etc..
I don't know how much you know about WiFi, but the frames are a bit more complex than Ethernet, in that WiFi is essentially a bridge between the WiFi device and your LAN. The AP WiFi MACs are generally not a concern. Devices on your LAN will see the MACs of the WiFi device and not the AP.
-
@JKnott thanks for the reply I appreciate you looking at this.
Keep in mind I was mostly researching this today. This was my thoughts were durring this adventure until I learned form the forum that the PfSense only needs the RJ45 mapping, others said it depends on the AP also. It has an official bridge mode setting.
-
If my AP is in bridge mode, meaning DHCP issues come from PfSense does the Mac addresses on the AP need to be mapped onto the PfSense when devices send out Arp requests to find say the printer, example: devices on wifi sends out arp request for "who has 192.168.1.14" and the printer responded "I do here is my MAC address" again it responds to the AP MAC not what the firewall has listed for this AP. If this AP is in bridge mode does it create some kind of loop as the AP also still has a layer 3 address mapped to it for a different layer 2 address? Meaning could it do a broadcast storm as it is bridged and part of the same network. I know 100% the past I had many broadcast storms with this AP when it was plugged directly into the DSL modem a reset would fix it.
-
I only allow static IP addresses from the firewall, so if it's set to not allow unknown IP-MAC addresses in the static ARP table what happens when devices send out ARP requests to the AP's Wi-Fi 5GHz mapping and it has to pass that up to the firewall because it's set in bridge mode, again firewall only sees the local RJ45 connection MAC-IP mapping. It is doing static assignments.
-
Does the firewall see any other Arp table mappings for the other Mac addresses listed for the AP. If it's set to ignore unknown that could in theory cause weird Arp requests right? If it was not set to static addresses it would not be such a concern.
-
I have a NAS running on the AP that is functioning, this might be why I was thinking about the possibility of ARP storms "broadcast storms" occurring.
-
My AP also has timed access with Mac mappings directly on it that work.
This was my research today does this AP set to bridge mode need the other mappings for let's say to stop a ARP broadcast storm.
Thanks for your interest in this.
When I run arp -a on a device it sees the AP mapped to the firewalls MAC-IP pair set for the AP this is when it is facing out so that is why I started to research. If I am on a device and I run arp -a it shows the RJ-45 MAC-IP pair, the WiFi 2.5 and 5GHz macs are not listed. We know they are there because they are in use for wifi, and for when I use SMB for my NAS or for my other NAS it has to go into the WiFi to get to it not to the Firewall. The AP has the USB HDD attached.
The reason is for the new experimental ethernet layer 2 filtering testing.
-
-
@JKnott when I do an ARP -a it shows it mapped on the devices as the RJ-45 of the AP. I thought it would be on device side the Wi-FI MAC not the RJ-45 again, it's bridged right? Hence, why I think it could have broadcast storms looking for the WiFi or 2.4 or 5ghz MAC.
BSSID's would see the other MAC mappings within the perspective of the OS level. Why not track this on the firewall too? As we can do layer 2 filtering now.
Keep in mind I am just researching this for use with PfSense new experimentalnlayer 2 filtering
Do you know if pfSense can spot the BSSID that is in use in any way that you know of if it's in use on a Ethernet RJ-45 port? In Windows 10 you could swap out any device and it if had the same SSID it would connect to it didn't matter it had no BSSID lock down.
I did some research on this in the past with the BSSID reports and lock downs. Leading to, if pfSense is doing experimental layer 2 filtering why not start to research the BSSID's too and map them someway?
Ref my older research while in college:
https://answers.microsoft.com/en-us/windows/forum/all/lock-down-windows-10-devices-wifi-connection/1f29dfde-4508-4866-87cf-e0a330b71acehttps://learn.microsoft.com/en-us/answers/questions/573050/lock-down-windows-10-devices-wifi-connection-choic
-
@JonathanLee if your talking about someone creating a rouge AP (evil twin) and using something like wifi-pumpkin to have users connect to their AP vs the actual AP..
Your AP
MySSID, psk P@55W0rd!And someone fires up another AP with the same SSID and psk - there is nothing pfsense could do to prevent a client from connecting to that AP..
If you want to lock down a client to only connect to a specific BSSID, keep in mind someone setting up a evil twin AP would more then likely use the same BSSID (mac) as the official one..
How do you think pfsense could have anything to do with such traffic?
edit: your scenario of connecting to the wrong wifi, I had a friend that couldn't figure out why she couldn't print.. Well she was using default SSID "linksys" and was connecting to her neighbors wifi, not hers - heheh So no she couldn't print to the printer on her network ;)
-
I think you may be creating your own issues. Why are you so worried about ARP etc. If pfSense or any other device wants to access the AP for configuration, etc., it will do an ARP request and then get the MAC at that time. You can also configure the DHCP server to provide static mappings for the AP or any other device. This is what I do here. Any device I own, other than my main desktop computer and my pfSense box get their addresses that way.
Where would this loop come from? Having a different L2 address for a L3 address wouldn't cause a loop. The old address would be replaced in the ARP cache by the new. Broadcast storms are typically caused by a L2 loop.
As for the ARP cache, anything in it expires after a fairly short time, requiring a new ARP request. -
@JonathanLee said in AP unit has multiple MAC Hardware Layer 2 addresses:
when I do an ARP -a it shows it mapped on the devices as the RJ-45 of the AP. I thought it would be on device side the Wi-FI MAC not the RJ-45 again, it's bridged right? Hence, why I think it could have broadcast storms looking for the WiFi or 2.4 or 5ghz MAC.
You're way overthinking this. ARP -a will only show the devices that have connected recently, that is until the cache entry expires. If you don't see something in the cache, then ping it, it will now be in the cache. Again, if you have broadcast storms, it's likely because you created a loop when connecting the various devices. BTW, please say Ethernet or wired connection, rather than "RJ-45", so that you think the way everyone else does. You will never see BSSIDs in pfSense. That's a WiFi only thing.
-
@JKnott I thought maybe it could someway see the BSSID and the MAC as they are tied together. It could see it if I used I used a wifi card directly installed on the firewall itself I know that. I also found this on Netgate docs.
Per Netgate docs for wifi card:
"Due to the way wireless works in BSS mode (Basic Service Set, client mode) and IBSS mode (Independent Basic Service Set, Ad-Hoc mode), and the way bridging works, a wireless interface cannot be bridged in BSS or IBSS mode. Every device connected to a wireless card in BSS or IBSS mode must present the same MAC address. With bridging, the MAC address passed is the actual MAC of the connected device. This is normally a desirable facet of how bridging works. With wireless, the only way this can function is if all the devices behind that wireless card present the same MAC address on the wireless network."
https://docs.netgate.com/pfsense/en/latest/wireless/bridges.html
Scenario one: Device MAC passed to wireless AP MAC passed to AP Ethernet MAC to PfSense to manage with static mappings.
Scenario two: Device arps out for the AP connected NAS Arp request goes to the AP and AP responses to the device directly again this AP it's in bridge mode so does the AP send the Arp requests up to PfSense still? If so, PfSense says that does not match for my MAC in my static IP mapping for the AP for the NAS I have the Ethernet mapped what does PfSense do with that ARP request?
Scenario three: PfSense is set to dynamically assignment on DHCP. There is no static mappings they are dynamic.
Good research
 ️
️Again, they must present the same MAC on the wireless network, so in theory when in
bridge mode it should pass the actual Mac of the connected devices. Again my AP has a huge HDD that is used for my NAS for example and that is what I think use to cause the Strom and noise all the time. It's MAC is a different MAC and not the Ethernet MAC on that same device. The AP device doesn't care about it just let's users connect, it's the firewall that cares as the MAC does not match it's the Ethernet MAC for that device assigned to that IP. So when devices send ARPs out to find the NAS it's still statically assigned with a different MAC at that firewall. The firewall is hypotheticaly like "good day Mr ARP request I don't have that AP NAS mapping, hmmm but I have the Ethernet MAC mapped on this list." The AP's NAS is hypotheticaly like, "I am already past the bouncer, and traffic is flowing and IPs dancing already."Again with my set up the NAS works currently, but lots of unwanted noise.
You can see above the MAC-IP host names got mix matched when I was testing this. Why would they Mis Match the hostnames?It should stay with the Ethernet hostname as that MAC is mapped to that IP and hostname.
We can agree that, bridges do not break up broadcast domains only the routers do that.
To quote another airport extreme AP user that spoke with Apple support help desk on this, "According to the tech (apple support) the AirPort Extreme is "unpredictable" if you attempt to use USB drives when the router(AP) is in bridge mode.."
That is exactly what I have done. The AP is in bridge mode and it's using the USB drive huge HDD drive at the same time.
-
@JonathanLee said in AP unit has multiple MAC Hardware Layer 2 addresses:
I thought maybe it could someway see the BSSID and the MAC as they are tied together. It could see it if I used I used a wifi card directly installed on the firewall itself I know that. I also found this on Netgate docs.
You appear to be using an AP and not a WiFi card. This means there's no way pfSense can see the SSID.
-
@JKnott BSSID is what I am saying. That is the MAC mapping of that WiFi network.
"SSID, BSSID, and ESSID are all descriptions of wireless networks. However, these three terms have slightly different meanings which are described here. An access point is only one of many devices that make up a wireless network and the Basic Service Set Identifier (BSSID) refers to any device in the WLAN.
Basic Service Set Identifiers (BSSID) are 48-bit labels that identify which devices conform to MAC-48 conventions. These identifiers are usually linked with a wireless access points MAC address, like when the identifier is sent in an AP beacon but can not be seen without some type of signal analyzer or radio tool."
That's the MAC tied to my NAS usb drive within the airport extreme itself.
Ref: https://internetspeedtest.world/wiki/bssid
There for the reason for the mixed host name with multiple Mac IP mappings, and why I have configured pfSense this way it's for my airport extreme with NAS running in bridge mode. It just works better for me. Under normal non NAS APs, just one MAC would be needed here. However I need two layer 2 addresses because of the NAS for ARP requests to work for it.
Bridges work on the data link layer. This will send everything to the firewall even the ARP request to find the NAS.