New user Compromised pc - APT & keylogger
-
If it's as bad as you say, then I think you should get someone in who knows what they're doing to find where the compromises are and then fix them. If it was a single device, then reloading the OS is where you start. If you can't nail down where the problem is, then pfSense can't do much to help you. For example, pfSense would know nothing of passwords on computers. It would also know nothing about malware installed on your computers. All it can do is filter traffic, based on address, protocol, etc..
-
@smoses You can block IPs but it's kind of a bandage on the problem.
thoughts:
- Use Quad9 or similar DNS that blocks malware, on the PCs and/or forwarding on the router.
- You can enable Suricata. Do so on LAN not WAN so you can see which of your IPs are triggering alerts. I suggest monitoring alerts without blocking for a bit to not block valid traffic. Only enable rulesets that apply (e.g. not a web server if you don't have a web server).
- pfBlocker has various feeds for blocking CINS, DROP, Talos, ET, etc.
- As noted wipe and reinstall is safest. A true APT may embed in the BIOS or drive firmware.
Once an identity is stolen they don't have to be on the PC anymore. Consider freezing your credit, which is free at all 3 agencies, e.g. https://www.experian.com/freeze/center.html.
-
@JKnott - Sorry for the delayed response. I've reinstalled the os at least five times and it doesn't matter - still hacked and we replaced the router. I'd like to remove the worst pc but I'm unable to at the moment due to the user. It's router hacker credentials, with a form, keylogger and malware with our keystrokes, passwords included. I've been capturing network traffic and I know the majority of what needs to be blocked. Essentially not allowing any outbound traffic other than the specifics. Suricata should filter out the bad signatures and keylogger and then I should be able to set the passwords securely.
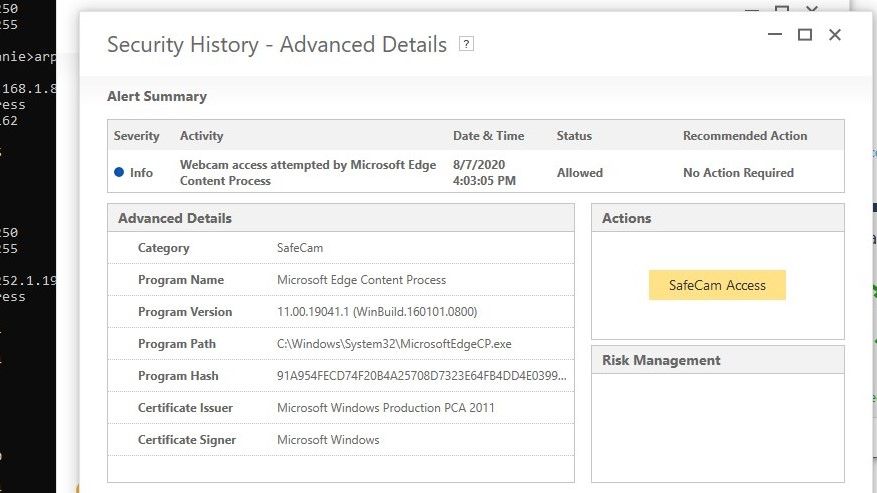
As a matter of fact, I created a usb drive to reinstall the os and used it for another device (cheapie) and the reimage file is corrupt from the infected pc and when I connected the cheapie device, it was 5-10 minutes before it was hacked with a MITM accessing my webcam. That bad.
Do you know if the community version software uses less cpu than the pro? -
@SteveITS - I've reinstalled the os at least five times already and it doesn't matter. I've replaced the router and would ideally like to remove the infected pc but due to the user at the moment, I'm unable to. I've been capturing network traffic and I know the majority of what needs to be blocked. Essentially not allowing any outbound traffic other than the specifics. Suricata should filter out the bad malware signatures, keylogger and then I should be able to set the passwords securely. I tried initially with windows firewall and it changed ports and it was like I did nothing, so it's malicious behavior.
As a matter of fact, I created a usb drive to reinstall the os and used it for another device (cheapie) and the reimage file is corrupt from the infected pc and when I connected the cheapie device, it was 5-10 minutes before it was hacked with a MITM accessing my webcam. That bad.
Do you know if the community version software uses less cpu than the pro? -
@SteveITS - I've frozen my credit. Thanks and when if I activate a new pc or anything with my SSN - it's immediately hacked and they have full control including cameras. My healthcare has notified me also as it's included. They haven't opened anything in my name, they're just using me currently and being peeping toms.
-
Hello, make sure you airgap that system with the major issues. I hope your ok. If you are overwhelmed you can always ask for help. I hope this community makes you feel safer. It's ok, we will get the bad guys. You're in good hands.
-
@JonathanLee - What do you mean by "airgap"? Thanks. I know I have to isolate the pc, use egress filtering and lock everything down except for isolated rules. I hate to admit that at the present moment I forgot how to do that and my networking book not in sight. I have alot that is connecting to the infected pc including a MITM, alot of unnecessary broadcasting, a ton of unnecessary DNS, simple discovery's, and a form attached to our router credential hackers - capturing everything we do. Kids in town have recently stalked me with what we watch and other businesses have told me it's visible. And a "dial" something with a multi-screen listed.
I'll take all suggestions of the simplest and easiest way to do that. Thanks in advance. As I'm typing, they like to highlight specific key words. Not a joke. -
@JKnott , @SteveITS , @JonathanLee - Does anyone know if the community edition uses less CPU than the professional edition of pfsense? I thought I bought a large enough HD (8GB) for the pro and without Suricata it's already using around 30%. They do what they want whenever they want to us, including showing me spyware is included (which they like to turn on the mic whenever they're "upset" with me). And they do know where I live. I can definitely go buy a new networking book but I'd hope that someone would just easily explain it here. Link it in whatever. The details.
-
@smoses “air gap” means no connection, no LAN, no wires or wireless. IOW why is this infected device so important that it can’t be disconnected?
CPU usage is not related to CE/Plus. It can be related to packages, bandwidth usage, and hardware.
-
@smoses I have no idea what you think you have going on.. I really don't buy any of this to be honest.
What is you want pfsense to do? Block some ports, block the internet? Out of the box no ports are allowed in. If you don't want the pc to go somewhere (IP) or network or Ports.. Then create a rule that blocks those on the lan interface.
I've been capturing network traffic and I know the majority of what needs to be blocked
You said you sniffed and know what to block? Ok then block it.. Lets see these pcaps, show us something other than simple paranoia to be honest.
5-10 minutes before it was hacked with a MITM accessing my webcam.
Man in the middle accessing your webcam?? Sure Ok ;)
From reading this thread - seems like someone watching too much mr robot if you ask me.
If you tell us what you want to block, be more than happy to help you accomplish that. Love to see this pcap showing us what you want to block..
So you run any antivirus on this machine? What is it infected with? That survives a clean OS install? Do you want some suggestions for anit-virus? Windows Defender doesn't show anything - what about malwarebytes? What software have you run to try and detect what is installed that is keylogging any send the info to them?
Best practice you should isolate this PC to its own vlan, so it can not talk to any of your other devices. This can be done physically or with a vlan capable switch.
this would be basic locked down network, where any device on this network couldn't do anything to any of your other networks.
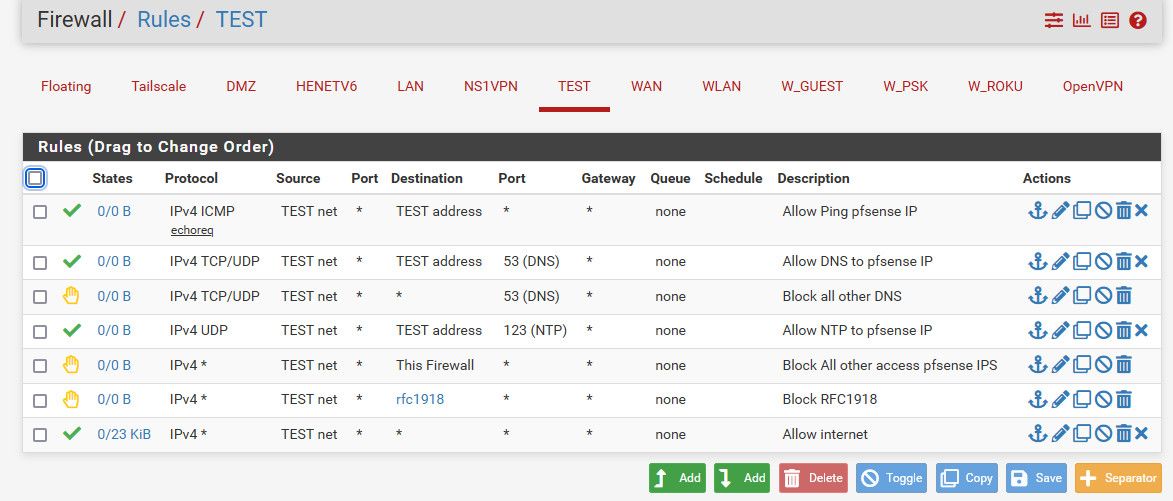
Then once you tell use what you want to stop the machine from talking to on the internet, we can show how to do that - the rules would go above the last rule that allows the internet.
First thing I would do is set that last rule to log - so you can see where the PC is going.. As a start.
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
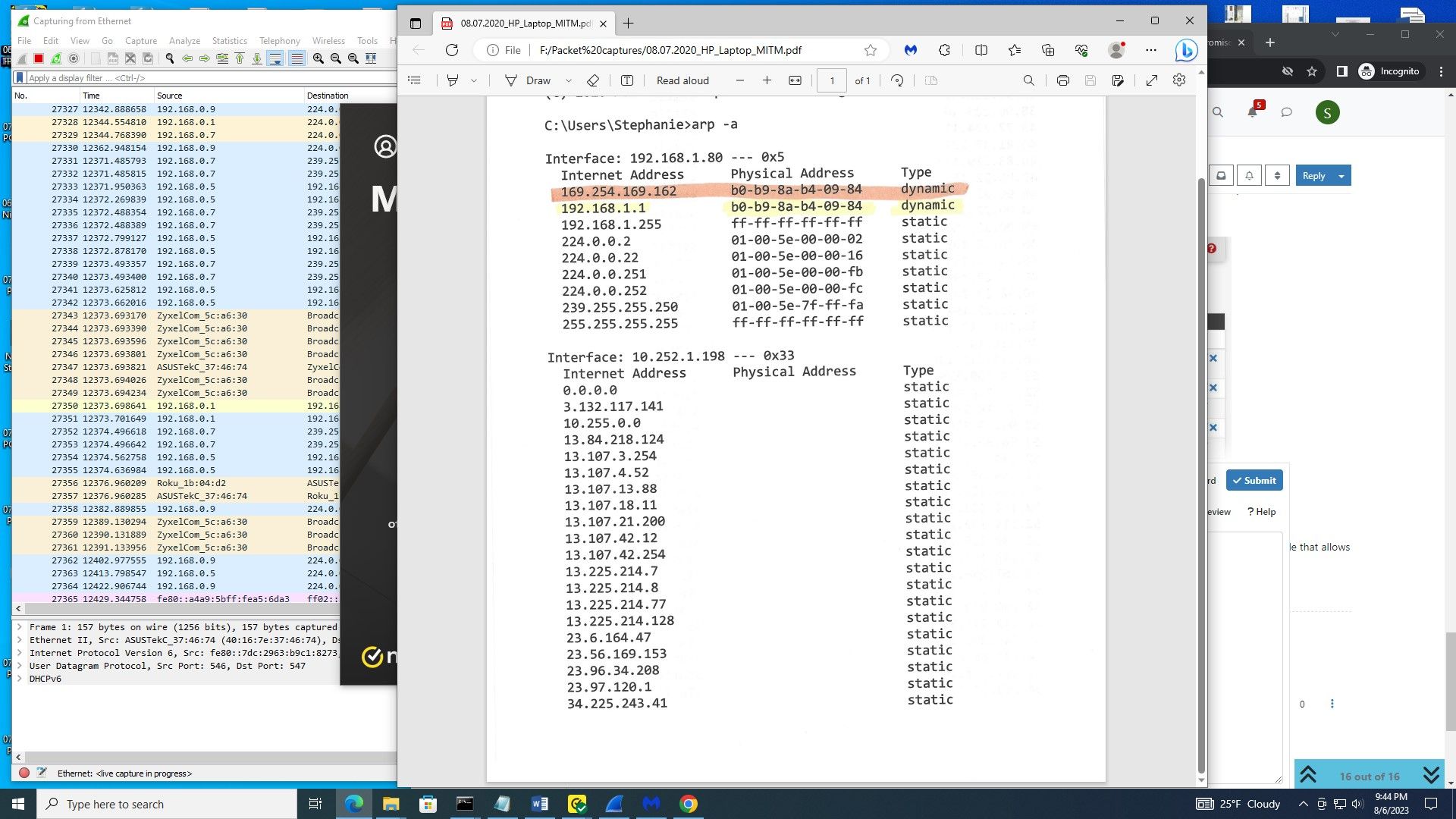
Sorry for the late response. I received the Norton alert within 10-15 minutes and did arp -a and it IS at least one, two MITM's. Sorry it's late.
-
POST /login.cgi HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 61
Origin: http://192.168.0.1
DNT: 1
Connection: keep-alive
Referer: http://192.168.0.1/
Upgrade-Insecure-Requests: 1admin_username=admin&admin_password=&admin_password=WITH OUR PASSWORD HERE HTTP/1.1 200 Ok
Server: micro_httpd
Cache-Control: no-cache
Date: Thu, 05 Nov 2020 06:41:16 GMT
Content-Type: text/html; charset=ISO-8859-1
Set-Cookie: SESSION=; expires=Thu, 01-Jan-1970 00:00:00 GMT; path=/; HttpOnly
Connection: close<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" />
<meta http-equiv="X-Frame-Options" content="deny" />
<title>CenturyLink Modem Configuration</title>
<link href="../_css/basic.css" rel="stylesheet" type="text/css" />
<SCRIPT LANGUAGE="JavaScript" SRC="../_js/jquery-1.6.4.min.js" TYPE="text/javascript"></SCRIPT>
<SCRIPT LANGUAGE="JavaScript" SRC="../_js/jquery.popupWindow.js" TYPE="text/javascript"></SCRIPT>I also have GA showing in the phone and pc and I haven't been there. My healthcare accounts in an iphone duplicated from 4, then 3, and then changed to show my dads iphone.
Our email address and router wan mac address is included in the form router credential hackers code. It's lengthy.
Believe me now? -
@smoses I DO have the keylogger and the ingenuine files screenshots that matches our network traffic. I DO have a IT degree and background. I'm not known to be wrong. Never had this before. Our devices have been on the network. Some of the network nasty-ness is specific to me with my name included.
I've tried multiple or all antiviruses, it's been to a pc repair with scans and nothing found. Only in the network traffic indicated from a hostile network. They've had full control. I can update Firefox. That doesn't fix the router hackers, people who can see it and are stalking our house because of it. That's why I posted it several times. I was told a different forum so it went in another forum. Who cares that much about multiple posts really? that's not the problem. -
@smoses so mac address of what your router, that is a netgear mac address. 192.168.0.1 - most likely your netgear router. A 169.254 is a APIPA address.. I have zero clue to what that is suppose to show or you want that to show - but it sure and the hell is not a MITM..
Your browser accessing your webcam? That is your proof - of what??
OMG - the RU black hats have infected my machine..
If you have a degree in computer science then show us what is going on - not just more nonsense... Your on your phone and you get some RU lang hits in a search engine? You on a vpn? You your language set wrong?
-
@johnpoz said in New user Compromised pc - APT & keylogger:
@smoses so mac address of what your router, that is a netgear mac address. 192.168.0.1 - most likely your netgear router.
also login.cgi is not a pfSense page.
-
@rcoleman-netgate said in New user Compromised pc - APT & keylogger:
also login.cgi is not a pfSense page.
Yeah brought that up in one of the other 3 posts with the same nonsense posted about this..
-
At this point I want you to do something for me: Take a photo of your router and post it here.
In your packet capture I see a number of things that could be in the middle and at aplay.
Zyxel
ASUSYour base IP range is 192.168.0.0
But your computer gets 192.168.1.0You have Netgear (not Netgate) hardware appearing and addresses related to that manufacturer in your posts.
Also a drawing of what is plugged in and how -- it doesn't have to perfect lines but it would need to be legible.
It seems to me as though you have many different pieces cobbled together and it is possible one of those is your root issue.
-
@rcoleman-netgate The double mac address is a mitm of another machine, that I made a windows reimage download usb drive on a "supposedly" clean machine which turned out to be the most infected. The other machine - as soon as I connected it to a different wifi, I received the Norton alert and I did the arp -a, showing duplicate mac addresses. I was not using anything to access my webcam. I used Norton VPN. I tried another VPN, same thing. It didn't make a difference. My cursor was moving also. They ARE MITMS. Back in the original network, there's a ton of CA network traffic and I'm causing data breaches. I'm not stupid. I wouldn't be posting anything on here if it weren't for the stupid derogatory comments which is typical in the IT field. I normally avoid it. I wouldn't post if I "had the language set wrong". They are my SSN hackers using my healthcare. I'm THE data breaches and gov has verified I am supplying tv shows and movies. I went to the FBI and spoke to two cybercrime agents in person, who also told me specific information and it's been correct.
My phones have been on our network over and over again. The pictures I'm forced to take of stalking, turned my USB drives into "rubber duckies" and my GOV accounts have been hacked with the librarian telling me and she took a picture.
Some credit rather than being talked down like I'm stupid, would be appreciated. Gov verified my searches are included and illegal surveillance of our house. Stores where my prescriptions are filled have told me, doctors have told me, yet - you're telling me it's "nonsense". I make perfect sense. My birth records are included with my entire family and I'm a business ID. My specific hackers and my PII IS a business ID. I CAN post the specific pictures. It'd be great to be asked that before the OH YEAH - SHOW US DUMMY. PROVE IT. YOU seem STUPID. I've also been told to not use this company as they are likely related to my hackers. The Marvel ARM 1U. That's me. Aries & Gemini lake, etc.
My healthcare pointed out "demotses" and that specific network traffic.
I appreciate the help. The actual help. It IS an AMD that IS the problem. I've used 5-7-8 different brands / manufacturers. The AMD IS the most problematic / infected. My Pentium hasn't been as infected as the AMD. Dell, HP, Asus, etc. I can also post the impostors of me and all the different locations of them also. and companies. I saved my conversations with Microsoft also. The AMD started conversations with Microsoft on it's own. As in the instant message Hub conversations - started on it's own. I sat and watched it. My parents, grandparents are Marvel characters, aunts, uncles, etc. I'd rather not give out my family tree without a lawyer. Other companies knew one, aunt MAY. The Embers MJ's - when it was open - is 15 minutes from me. -
@SteveITS - Thank you Steve. It's one of the names in our network traffic also. Perhaps not coincidentally.
-
@johnpoz The 192.168.0.1 was not a netgear router. I was at a coffee shop using wifi. As I said - a pc with a iso windows image that was done on the infected machine - that at that time was supposedly "safe".