Remote access issue: connected but traffic not passing back to clients
-
Hi, I'm facing an issue running OpenVPN for remote access.
Configuration scenario
- Two pfSense in HA
- Dual WAN setup (main fiber with some public IP addresses + 5G/LTE backup)
- CARP configured for all interfaces and additional public IPs configured as IP Alias (as suggested here: https://docs.netgate.com/pfsense/en/latest/highavailability/reduce-heartbeat-traffic.html)
- OpenVPN listens on one IP Alias of the WAN CARP
- User authentications via RADIUS (on a Windows server)
- VPN Client IP addresses assigned by RADIUS
- Topology > Subnet
The clients connects correctly and gets the IP from the radius server, I don't get any kind of error on both sides.
One the client is connected, it's unable to do any kind of communication with the server and the routed subnets pushed (correctly) by OpenVPN server.
Client are unable to ping even the OpenVPN server itself (first address of the tunnel pool).I've done some tcpdump and states monitoring: the packets seems to being routed correctly inside local LANs but the responses never reaches back the VPN client.
Could you help me figure out where is the problem?
OpenVPN config file (/var/etc/openvpn/server1/config.ovpn)
dev ovpns1 disable-dco verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 2.xxx.yyy.70 engine rdrand tls-server server 10.50.90.0 255.255.255.0 client-config-dir /var/etc/openvpn/server1/csc username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user ************** false server1 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'client-vpn.yyyyyyyyyyyy.com' 1" lport 1194 management /var/etc/openvpn/server1/sock unix push "route 10.50.1.0 255.255.255.0" push "route 10.50.10.0 255.255.255.0" push "route 10.50.12.0 255.255.255.0" push "route 10.50.20.0 255.255.255.0" push "route 10.50.30.0 255.255.255.0" push "route 10.50.40.0 255.255.255.0" push "route 10.50.95.0 255.255.255.224" push "route 10.50.99.0 255.255.255.0" push "dhcp-option DOMAIN zzzzzz.lan" push "dhcp-option DNS 10.50.1.201" push "dhcp-option DNS 10.50.1.202" push "block-outside-dns" push "register-dns" duplicate-cn remote-cert-tls client capath /var/etc/openvpn/server1/ca cert /var/etc/openvpn/server1/cert key /var/etc/openvpn/server1/key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server1/tls-auth 0 data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 data-ciphers-fallback AES-256-GCM allow-compression no persist-remote-ip float topology subnet explicit-exit-notify 1 inactive 7200Connection log on client (MacOS with Viscosity)
2023-06-28 18:05:07: Viscosity Mac 1.10.5 (1626) 2023-06-28 18:05:07: Viscosity OpenVPN Engine Started 2023-06-28 18:05:07: Running on macOS 12.6.6 2023-06-28 18:05:07: --------- 2023-06-28 18:05:07: State changed to Connecting 2023-06-28 18:05:07: Checking reachability status of connection... 2023-06-28 18:05:07: Connection is reachable. Starting connection attempt. 2023-06-28 18:05:08: OpenVPN 2.5.9 x86_64-apple-darwin [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [MH/RECVDA] [AEAD] built on Feb 22 2023 2023-06-28 18:05:08: library versions: OpenSSL 1.1.1t 7 Feb 2023, LZO 2.10 2023-06-28 18:05:08: Resolving address: client-vpn.xxxxxxxxxx.com 2023-06-28 18:05:08: Valid endpoint found: 2.xxx.zzz.70:1194:udp4 2023-06-28 18:05:08: TCP/UDP: Preserving recently used remote address: [AF_INET]2.xxx.zzz.70:1194 2023-06-28 18:05:08: UDPv4 link local: (not bound) 2023-06-28 18:05:08: UDPv4 link remote: [AF_INET]2.xxx.zzz.70:1194 2023-06-28 18:05:08: State changed to Authenticating 2023-06-28 18:05:08: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this 2023-06-28 18:05:08: [client-vpn.darsenadelsale.com] Peer Connection Initiated with [AF_INET]2.xxx.zzz.70:1194 2023-06-28 18:05:10: Options error: The command "block-outside-dns" or one of its parameters is invalid for this version of OpenVPN (2.5.9). Please edit the connection, make sure the command is valid, and try again. 2023-06-28 18:05:10: Options error: The command "register-dns" or one of its parameters is invalid for this version of OpenVPN (2.5.9). Please edit the connection, make sure the command is valid, and try again. 2023-06-28 18:05:10: Opened utun device utun10 2023-06-28 18:05:10: /sbin/ifconfig utun10 delete 2023-06-28 18:05:10: NOTE: Tried to delete pre-existing tun/tap instance -- No Problem if failure 2023-06-28 18:05:10: /sbin/ifconfig utun10 10.50.90.10 10.50.90.10 netmask 255.255.255.0 mtu 1500 up 2023-06-28 18:05:10: Initialization Sequence Completed 2023-06-28 18:05:10: DNS mode set to Split 2023-06-28 18:05:10: DNS Server/s: 10.50.1.201, 10.50.1.202 2023-06-28 18:05:10: DNS Domains/s: zzzzzzz.lan 2023-06-28 18:05:10: State changed to ConnectedRoute table on client, after connection (all subnets correctly pushed)
Internet: Destination Gateway Flags Netif Expire default 172.20.0.126 UGScg en0 default link#21 UCSIg utun10 10.50.1/24 10.50.90.1 UGSc utun10 10.50.10/24 10.50.90.1 UGSc utun10 10.50.12/24 10.50.90.1 UGSc utun10 10.50.20/24 10.50.90.1 UGSc utun10 10.50.30/24 10.50.90.1 UGSc utun10 10.50.40/24 10.50.90.1 UGSc utun10 10.50.90/24 10.50.90.10 UGSc utun10 10.50.90.10 10.50.90.10 UH utun10 10.50.95/27 10.50.90.1 UGSc utun10 10.50.99/24 10.50.90.1 UGSc utun10TCP dump pfSense-side while pinging tunnel IP and an internal server (10.50.1.201) from the client (10.50.90.10): no response routed back to the client
[23.05-RELEASE][admin@fw1.zzzzzzz.lan]/root: tcpdump -ni ovpns1 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on ovpns1, link-type NULL (BSD loopback), capture size 262144 bytes 17:42:23.756585 IP 10.50.90.10 > 10.50.90.1: ICMP echo request, id 24673, seq 0, length 64 17:42:24.764805 IP 10.50.90.10 > 10.50.90.1: ICMP echo request, id 24673, seq 1, length 64 17:42:25.764808 IP 10.50.90.10 > 10.50.90.1: ICMP echo request, id 24673, seq 2, length 64 17:42:26.764576 IP 10.50.90.10 > 10.50.90.1: ICMP echo request, id 24673, seq 3, length 64 17:42:31.884341 IP 10.50.90.10 > 10.50.1.201: ICMP echo request, id 37473, seq 0, length 64 17:42:32.892415 IP 10.50.90.10 > 10.50.1.201: ICMP echo request, id 37473, seq 1, length 64States while pinging an internal server (10.50.1.201) from the client (10.50.90.10)
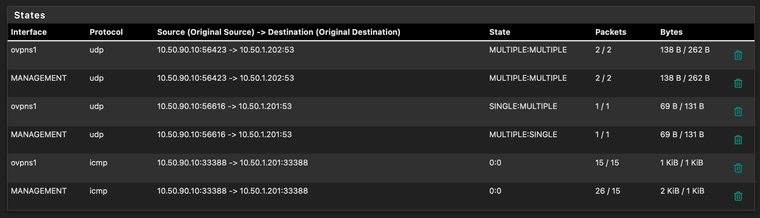
I really can't figure out what the problem could be.
Thanks in advance.
Bye,
Edoardo -
Sorry, solved... 🥺
By mistake I've entered the same subnet of the tunnel to a new interface (vlan) while copying/pasting from my config sheet...