Restrict access to specific ip to users remotely connected openvpn
-
You can set this up easy with CSO and Firewall Rules.
VPN > Open VPN > Client Specific Overrides:
Pick your Server, in Common Name put the Cert name of your Client. In IPv4 Tunnel Network put in the fixed IP you want to give to this user.
For example, if you have a 10.11.12.0/24 Tunnel network and want this User to have 10.11.12.13 you put in 10.11.12.13/24
Leave all the other stuff blank and hit Save.In Firewall > Rules navigate to the OpenVPN Group tab. Add a new Rule
IPv4 Any Source Single host or alias 10.11.12.13 Destination Single host or alias 192.168.1.200
Save and that's it. Maybe you need to Reset your States before testing.-Rico
-
Hi Rico, thanks for the reply.
I set a static ip / 24 for the tunnel of external account 1, everything ok, it takes it correctly, but I made the firewall rule as described by you, but I can still see the whole LAN by connecting with this account. I also created a blocking rule for the entire LAN, but anyway I can see everything anyway
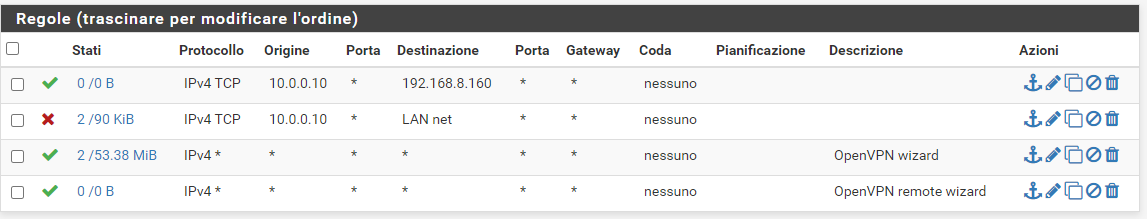
where am i wrong?
-
@Rico said in Restrict access to specific ip to users remotely connected openvpn:
Maybe you need to Reset your States before testing.
-Rico
-
Sorry, I was convinced that you intended to disconnect and connect with the user with the restrictions.
How do I restore my states? perhaps translating, I can't understand what you mean, sorry -
Diagnostics > States > Reset States
-Rico
-
Ah and change TCP to any, atm you only allow TCP to the server in the first Rule and block only TCP to LAN in the second. As result you allow any other protocols like ICMP ping, UDP and so on (because of the third any-any Rule).
-Rico
-
@Rico perfect, remember well that the rules apply from top to bottom? if so, did I do well to put up the rule that grants access to only that ip and block everything else with the rule below? While to limit the vpn connection only to a public IP address, how could I do it?
-
Yes, top to bottom, first trigger wins. See https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-basics.html
So if you have a Rule with some specific source IP and only allow traffic to one destination IP you don't need any other block rules because the traffic for this source IP stops there anyway.
If you have all your OpenVPN Clients connecting from a static IP you could create a Alias containing all the IPs and use this Alias as source for your OpenVPN Firewall Rule on WAN. Any other IPs are not allowed to connect to your OpenVPN server then.-Rico
-
perfect Rico, thank you very much, I learned a lot

-
This post is deleted!