openvpn site to site cannot access remote pfsense router
-
@rampuse said in openvpn site to site cannot access remote pfsense router:
"This site can’t be reached
192.168.7.7 took too long to respond."So the browser doesn't get a response like the access was blocked by the server.
That's weird, as you can access smb shares on the server site. So I assume that you have allowed at least TCP from 192.168.2.0/24 to 192.168.7.0/24 on the VPN interface.Anyway, something in the firewall log?
Maybe enable the logging in all related rules.
Do you have floating block rules, which match this traffic by any chance? -
@viragomann
Now i have configured NEW tunnel/VPN with ssl/tls method. this tunnel simply cannot ping the remote server. the setup is same. this time also the both sides have got/assigned a tunnel ip of 172.55.55.1 and all. but i cannot ping the other side!!!!! no smb either this time. cannot ping the other lans pcs!!!!! this time i have also created a openvpn 'interface' on client side. still no luck............
i just followed the netgate documentation to create the vpn.server side routes:
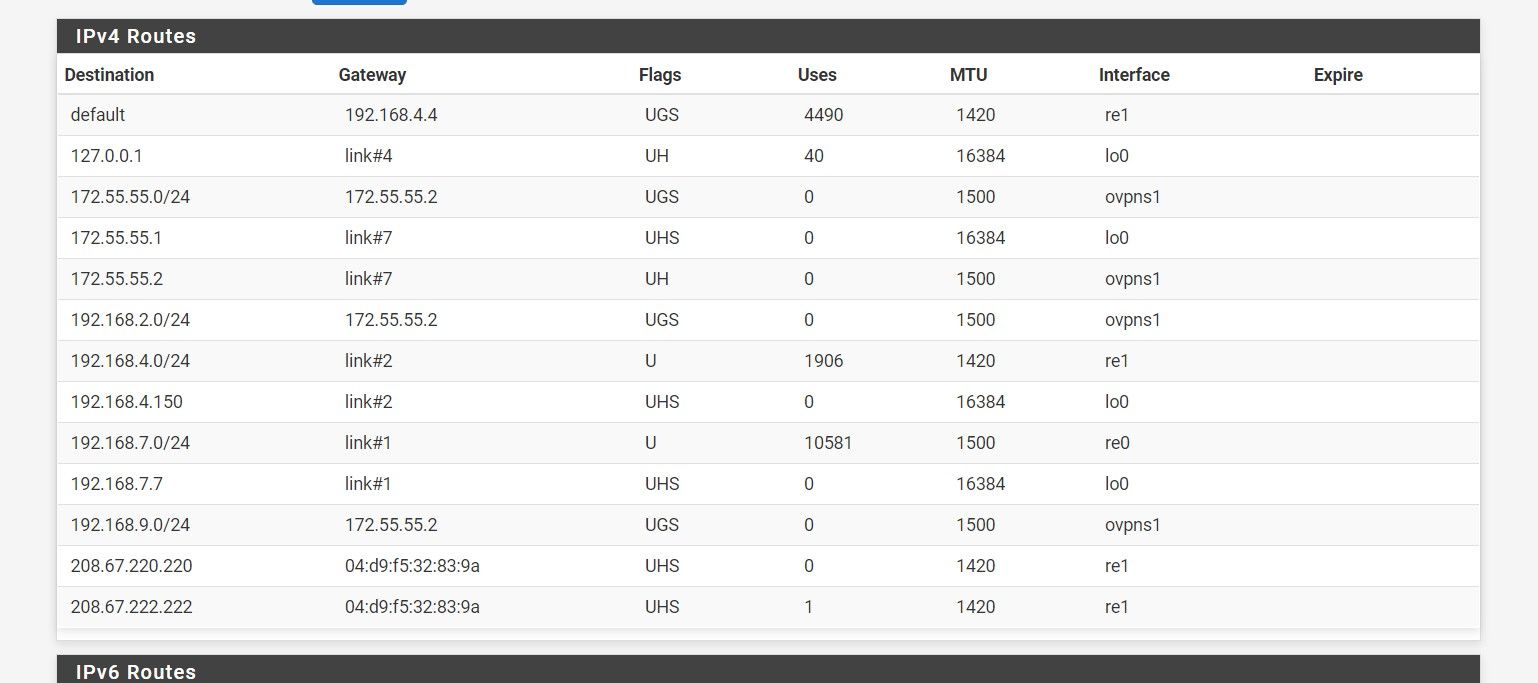
server side dashbaord:
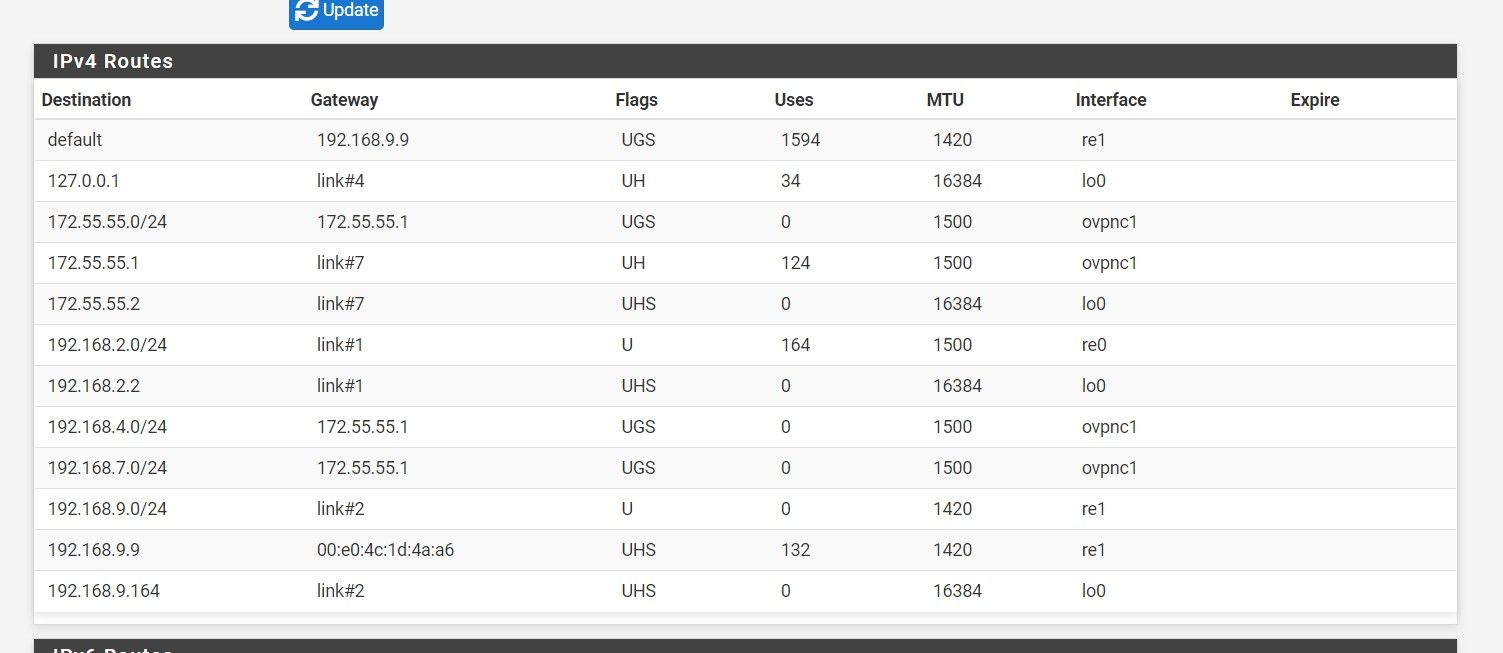
client side routes:
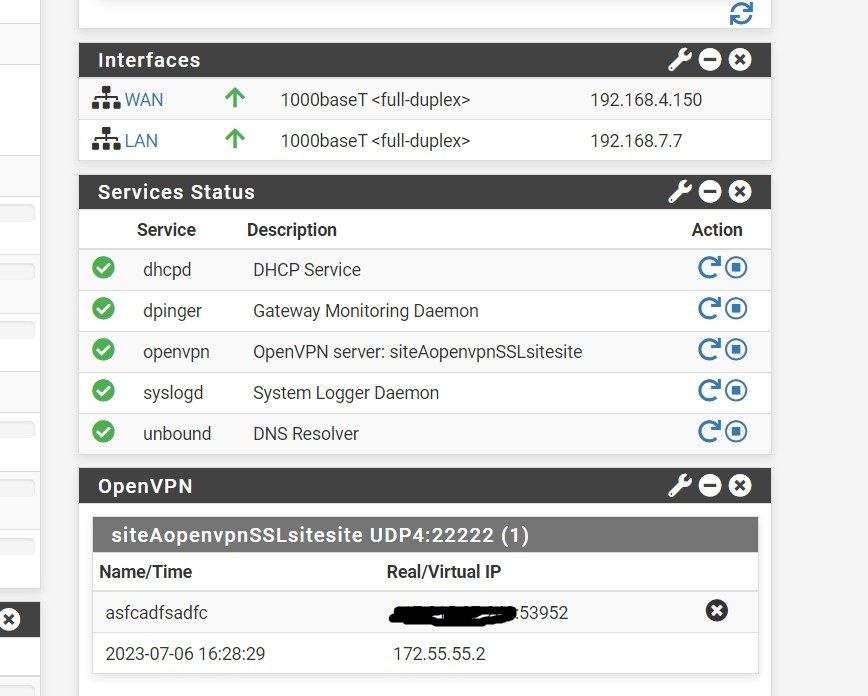
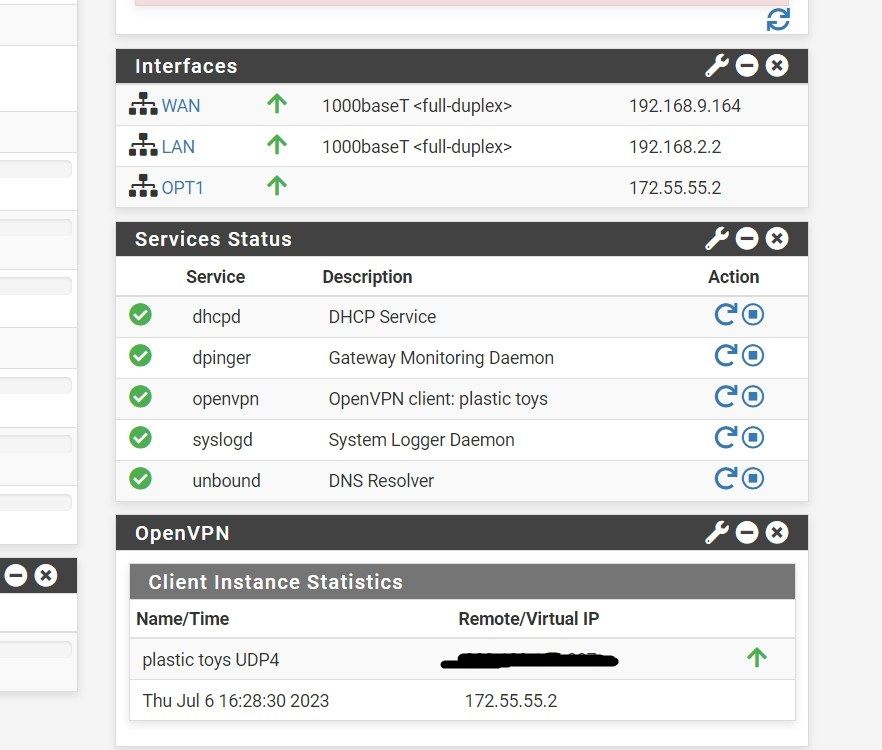
client side dashboard:
should i do anything in firewall > rules > floating ???????? it is currently just at default.
-
@rampuse
Set the tunnel network mask to /30 on the server.There is no need to assign interfaces to the OpenVPN instances as long as you don't need to policy route traffic to the other site or forward public traffic to the remote site.
Firewall rules are needed on all incoming interfaces. Either on the interfaces which you've assigned especially or on the OpenVPN tab.
And also on the LAN.
E.g. to access from site A LAN to B LAN you need a proper rule at A on LAN and at B on the VPN interface.Consider the OpenVPN rule tab is an interface group for all OpenVPN instances. Rules you add there are applied to all incoming vpn traffic in case it matches.
-
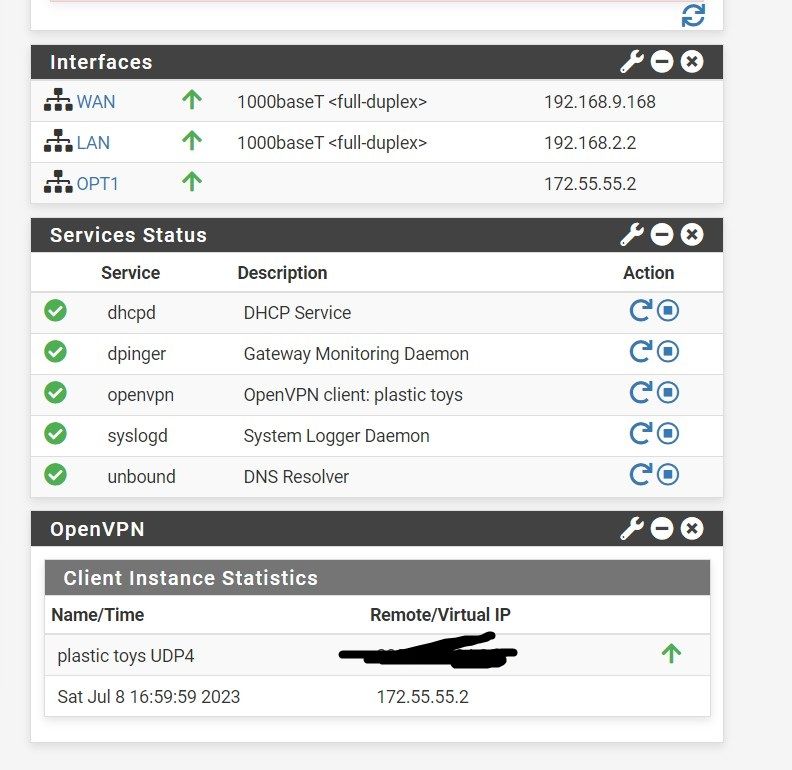
@viragomann
the server side dashboard shows under 'client instance statistics' the remote/virtual ip as '172.55.55.1' and the same on client side shows '172.55.55.2'
is this correct/ok?
client dashboard:
-
@rampuse
Yes, that's ok. The server takes the first IP in the tunnel subnet, the first client gets the next one. -
@viragomann
it seems i found the problem. i just changed the following settings and now everything works!!! :
changed tunnel address from /30 to /31
added 'concurrent connections' as '1'
now ssl works.
also did wireguard site2site. it also wasnt working TILL i did tunnel address as /31now everything works!!
thus, for site 2 site, the tunnel address HAS to be a /31 !!! -
@rampuse thanks for everyone who tried to help
-
Using public IP space in private networks is a bad idea ("172.55.55.0 - 172.55.55.255 is an IP address range owned by T-Mobile USA, Inc. and located in United States").
-Rico
-
@Rico
WTF !! I thought 10. AND 172. AND 192. are ALL private ranges. need to search the net for some clarification/info. -
10.0.0.0/8 (255.0.0.0) [10.0.0.0 – 10.255.255.255]
172.16.0.0/12 (255.240.0.0) [172.16.0.0 – 172.31.255.255]
192.168.0.0/16 (255.255.0.0) [192.168.0.0 – 192.168.255.255]https://en.wikipedia.org/wiki/Private_network
-Rico