Remote Access LAN from client behind OpenVPN Site-to-Site Tunnel
-
Hello Communtiy,
following situation:
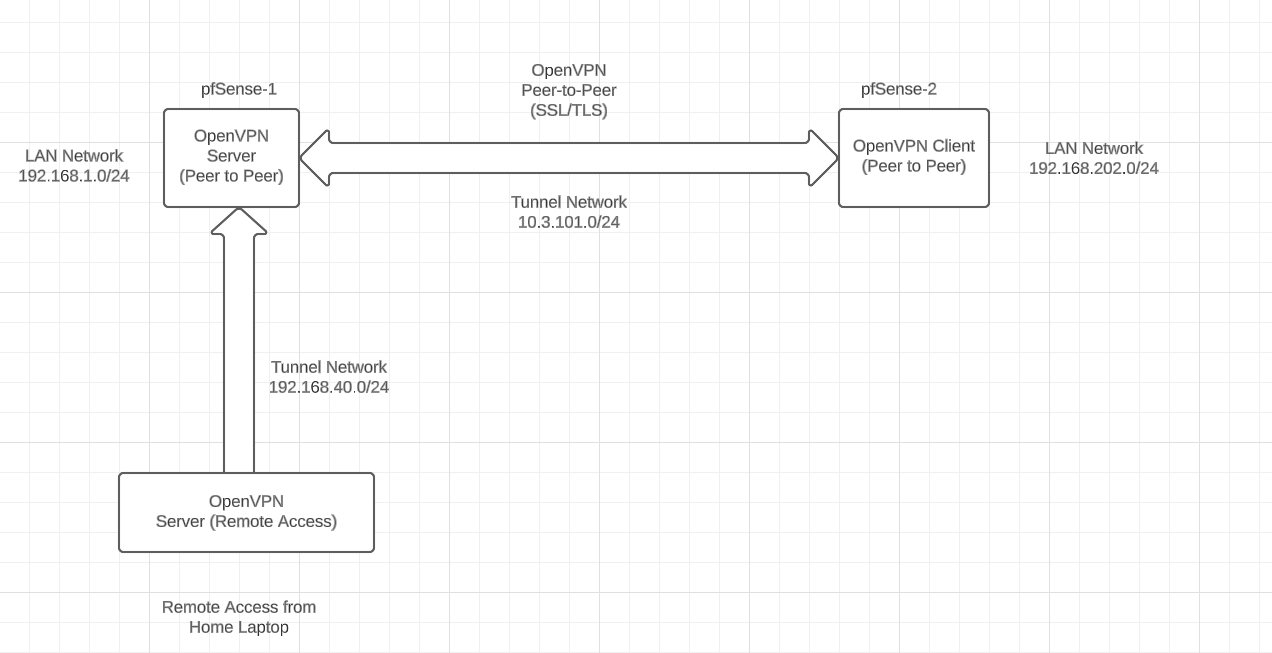
- I have 2 pfSense firewalls, these two firewalls are connected to each other with OpenVPN site-to-site (SSL/TLS). This works without any problems.
- One firewall is server and the other is client. pfSense Server reaches Lan from pfSense Client(192.168.202.0/24) and pfSense Client reaches pfSense Server LAN(192.168.1.0/24).
For this I used this guide: https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html
Now I have an additional requirement where I can't get any further: In the future, the customer users should be able to connect to the central office with "OPENVPN Connect" from home with a laptop (pfSense server) this also works without problems, LAN 192.168.1.0/24 is reachable. Furthermore, the (pfSense client) Lan network should also be accessible from the laptop, and this is exactly where I can't get any further. Does anyone have a similar situation and can help me?
For your information, I have already tried commands like push route " " and the like.
Attached are pictures for a better understanding + my configuration.!
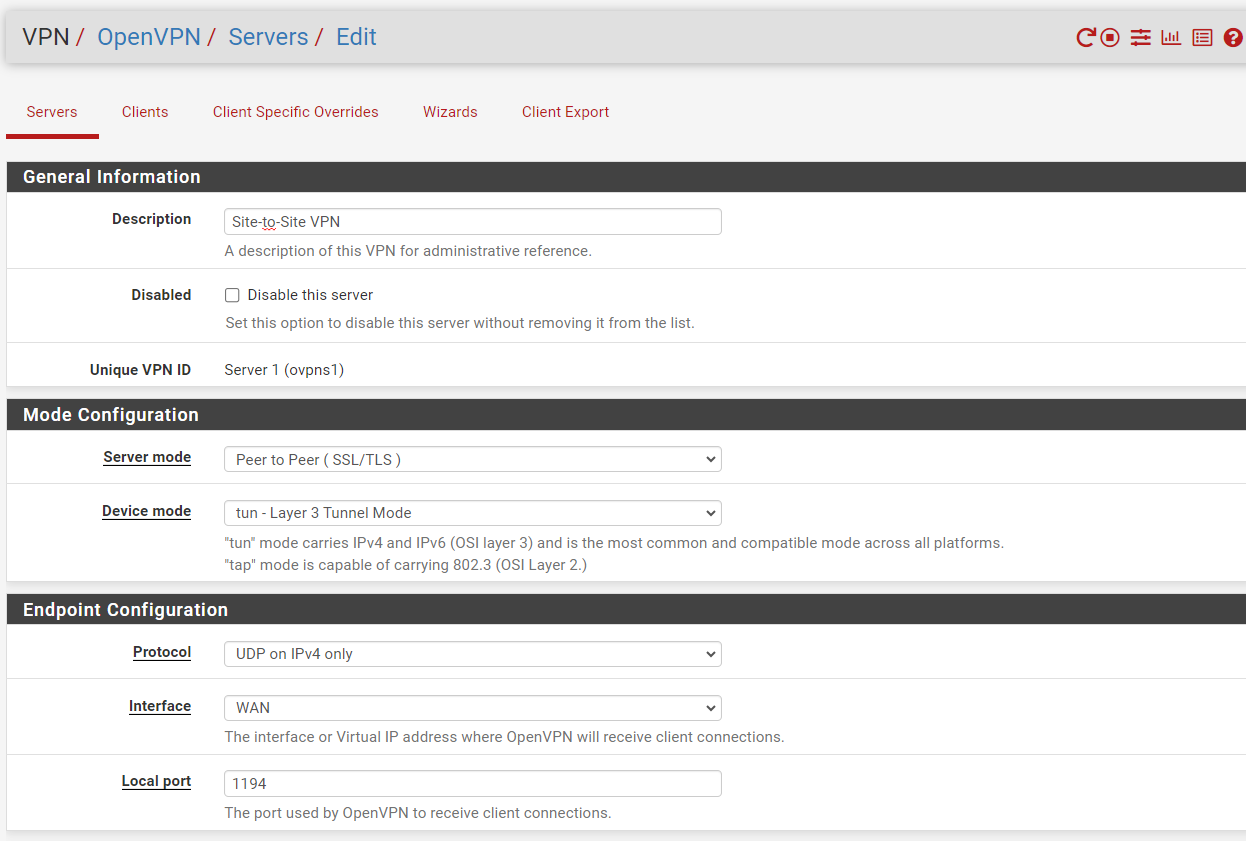
pfSense Server (Peer-to-Peer):
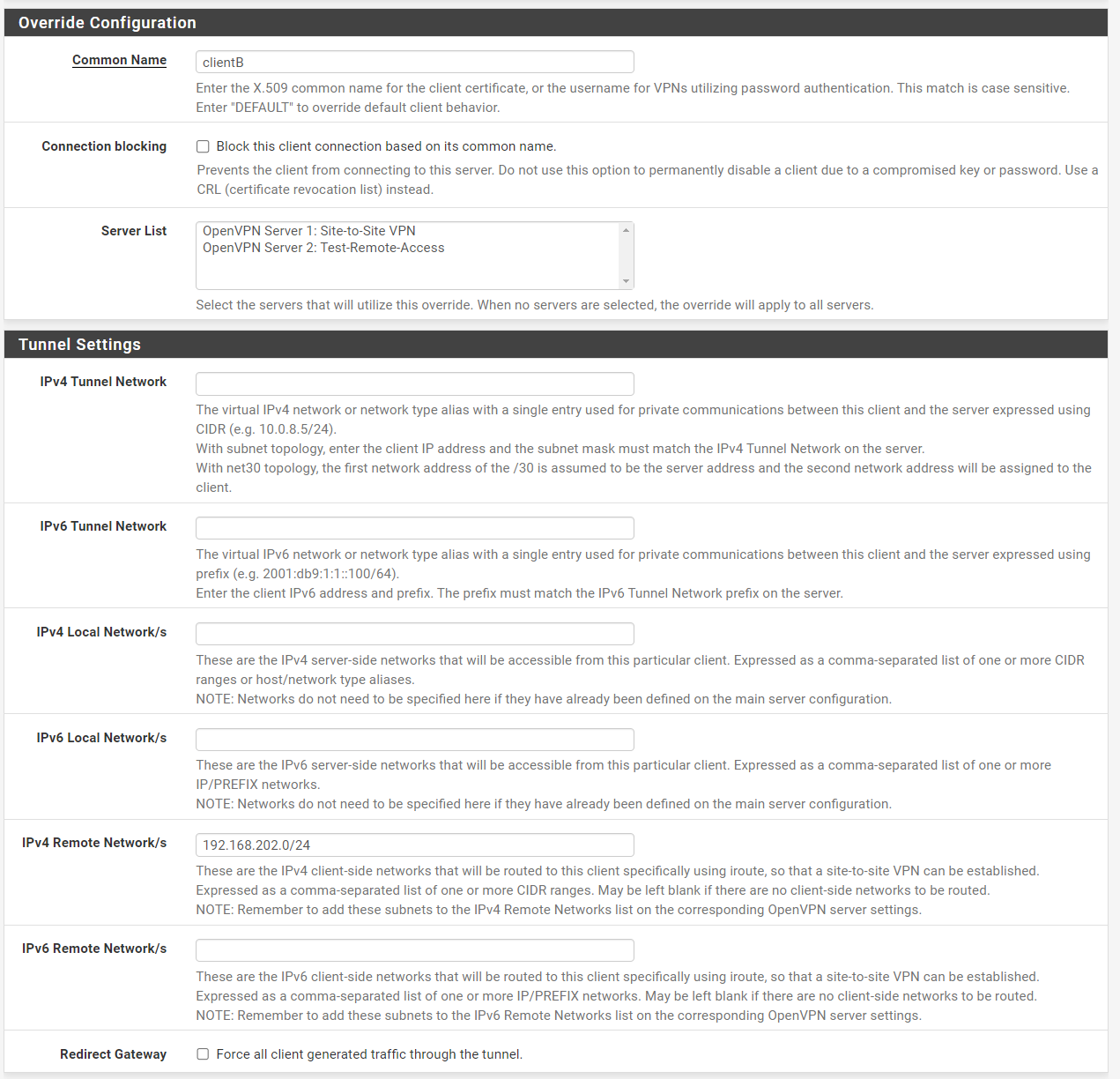
pfSense Server Client Specific Overrides:
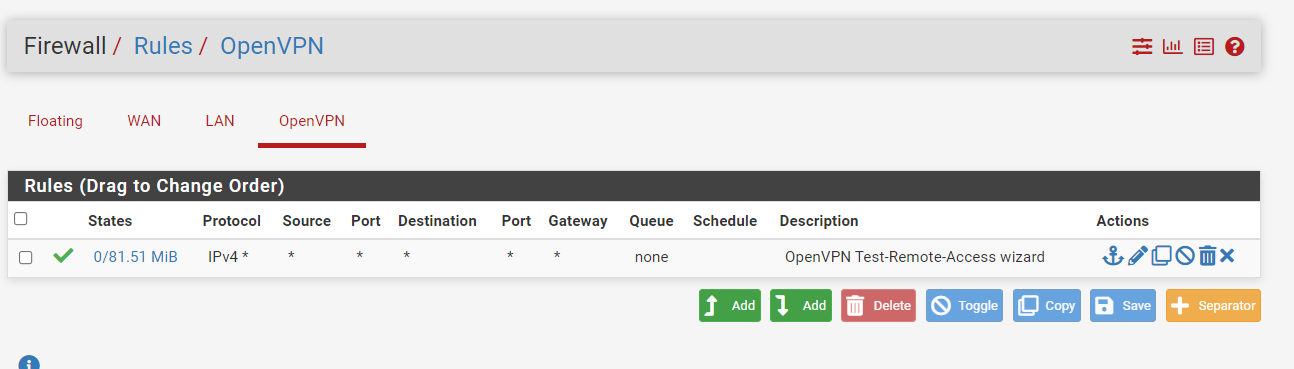
Firewall Rule pfSense Server:
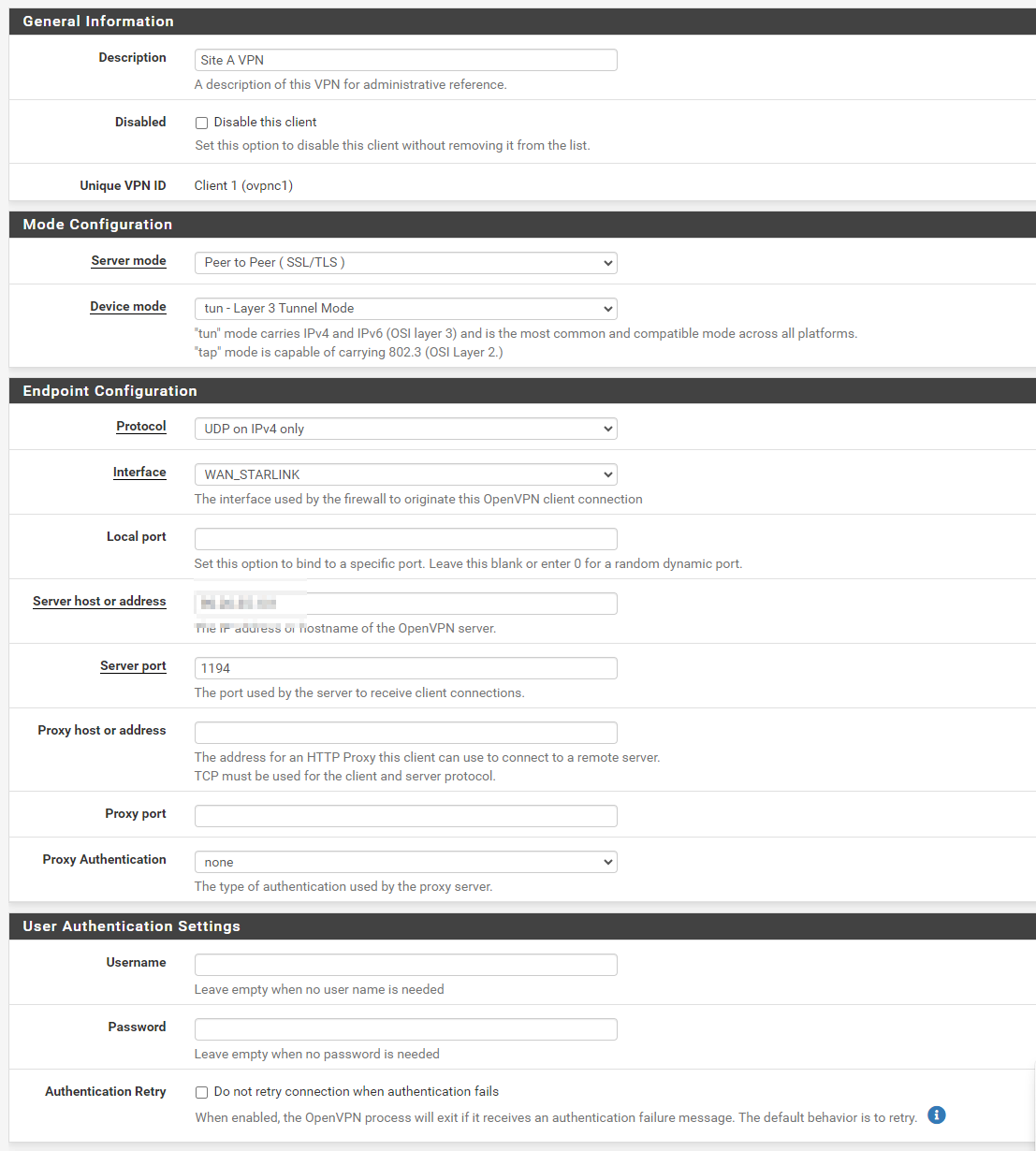
pfSense Client (Peer-to-Peer):
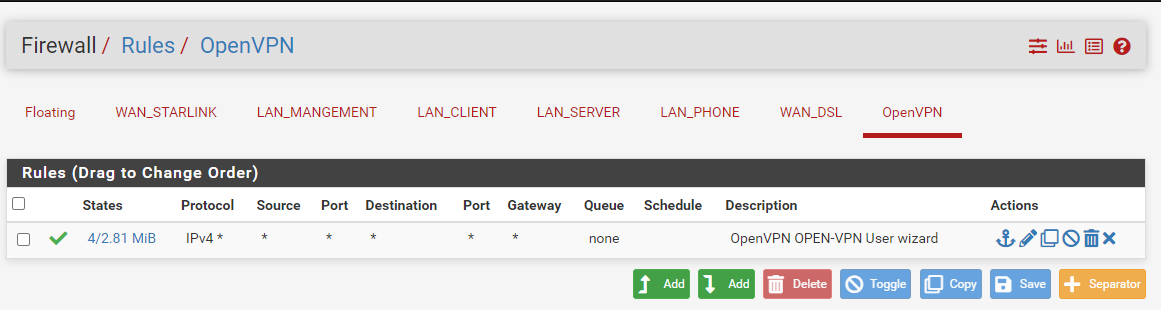
Firewall-Rule pfSense Client:
OpenVPN Server Remote Access (SSL/TLS+User Auth)
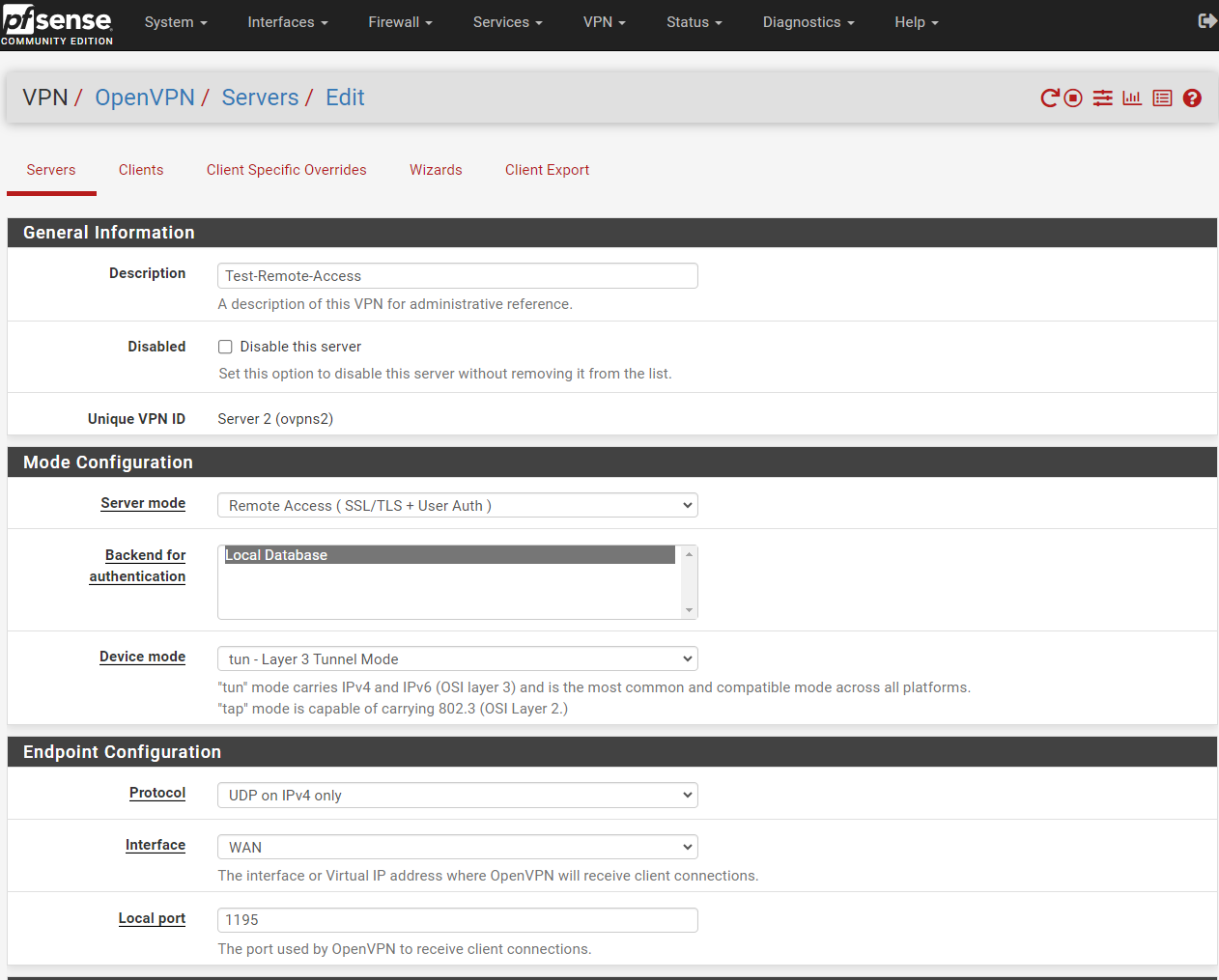
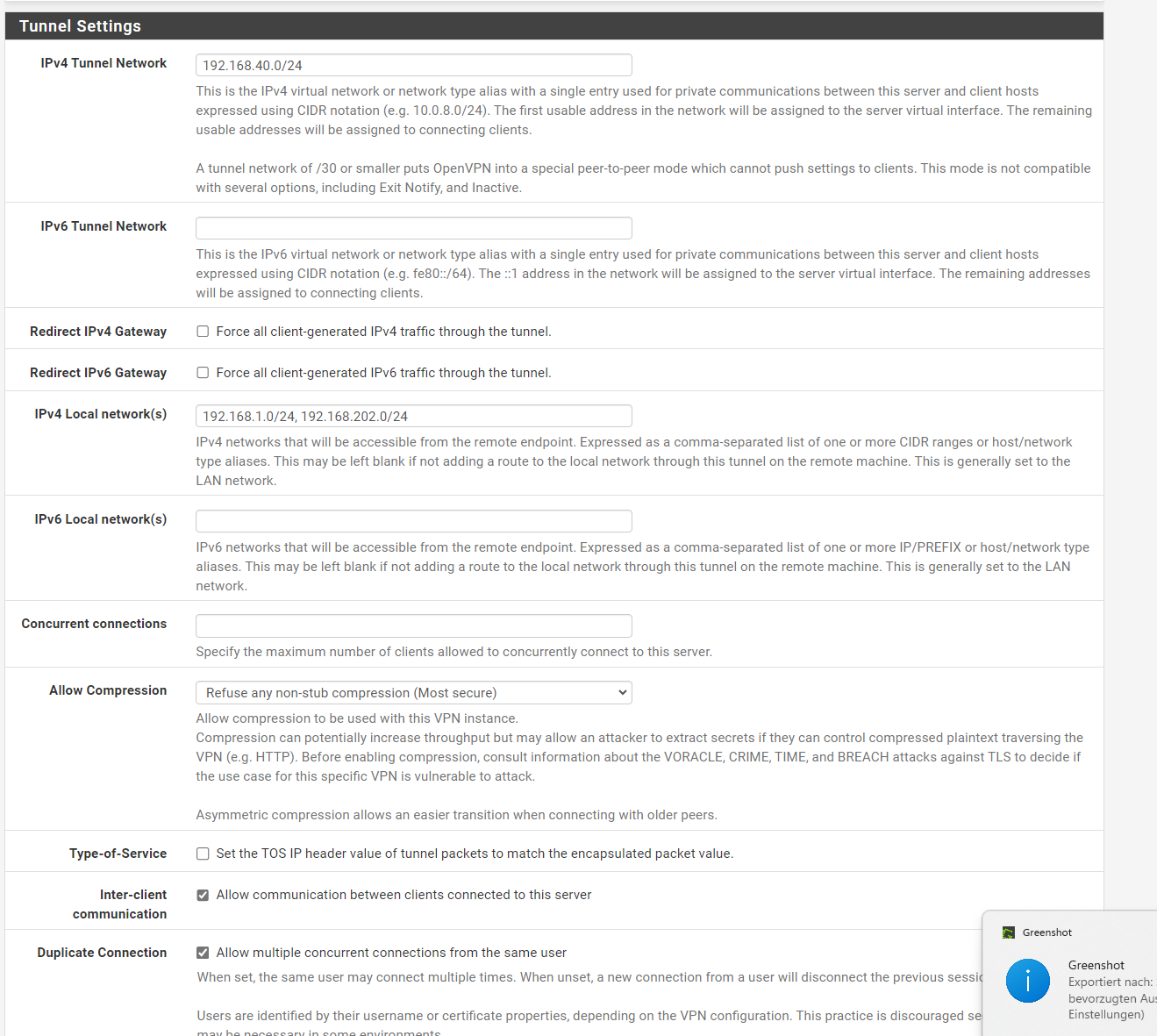
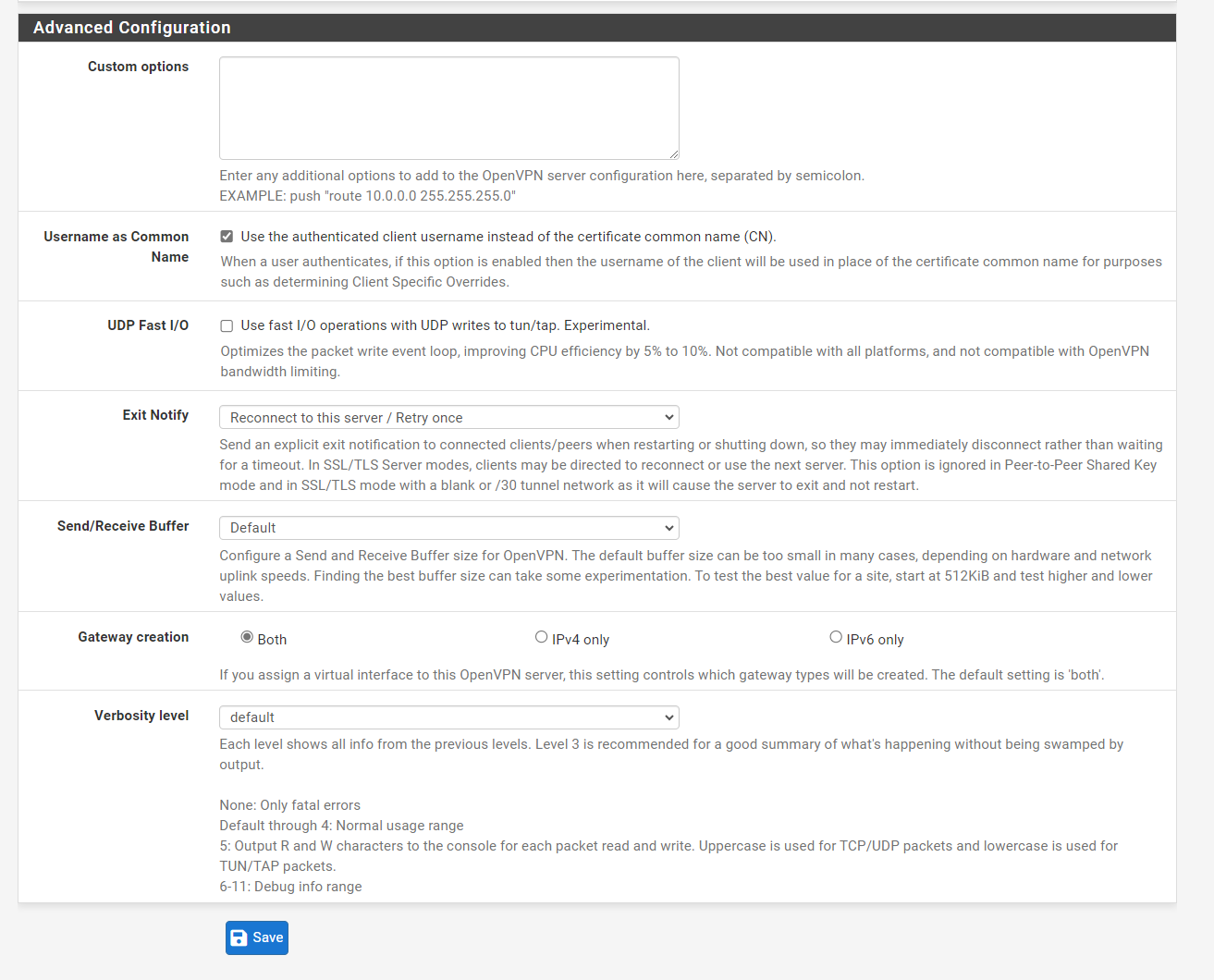
WAN-Rules for OPEN-VPN Ports:
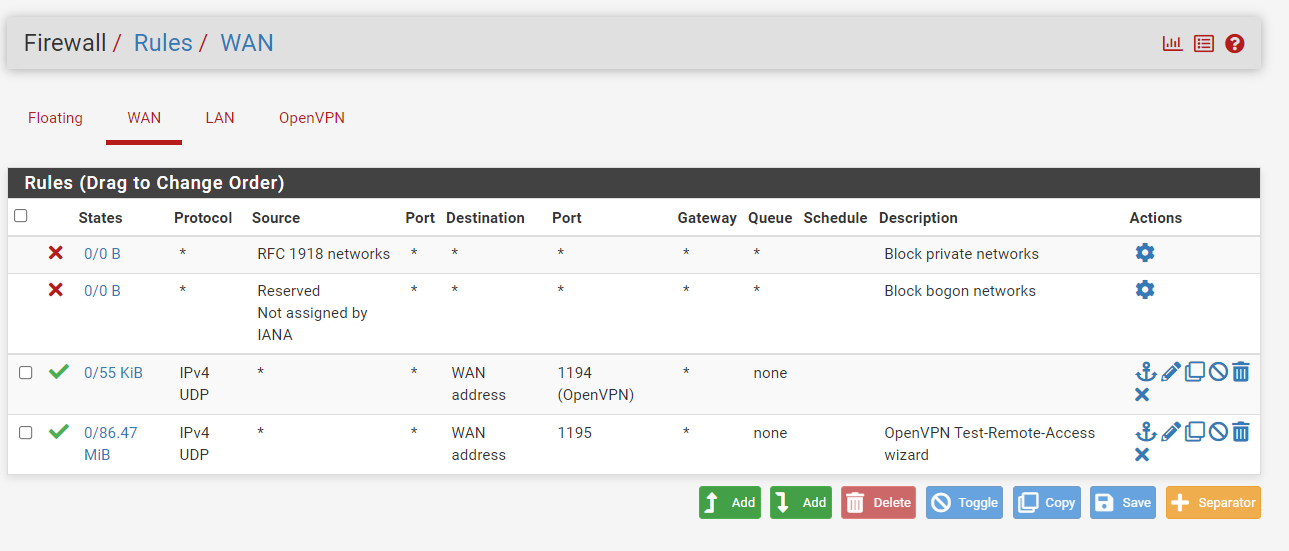
Thanks for help!
-
@Florian-Wögerbauer
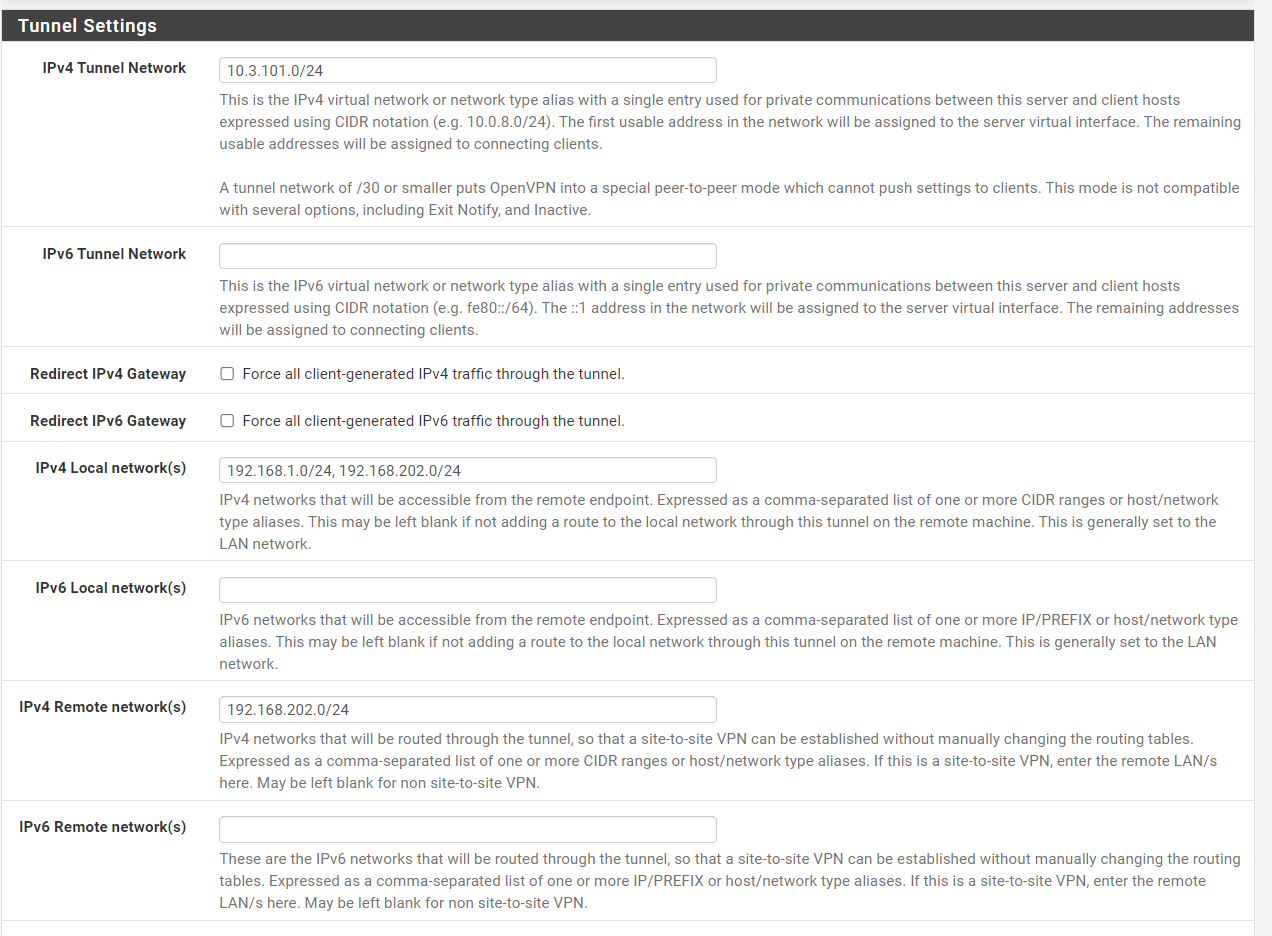
Empty the "Local Networks" box in the site2site server settings. This is meant for pushing routes to the clients, but that's not needed, since you can state the networks in the clients settings.
Also the clients LAN makes no sense here at all anyway.Instead in the client settings enter the server site LAN plus the remote access servers tunnel network into the "Remote Networks" box.
BTW: 192.168.1.0/24 is not really a good choice for a LAN subnet on an VPN access server.
This range is widely used as default on consumer routers. A client who is in such subnet would not be able to access the server site LAN, when connected to the VPN. -
@viragomann Thanks for answer what i tried:
If i empty "Local Networks" box in the site2site server settings. The tunnel is not working anymore i can't ping the client.
OpenVPN site2site Server looks like this now:
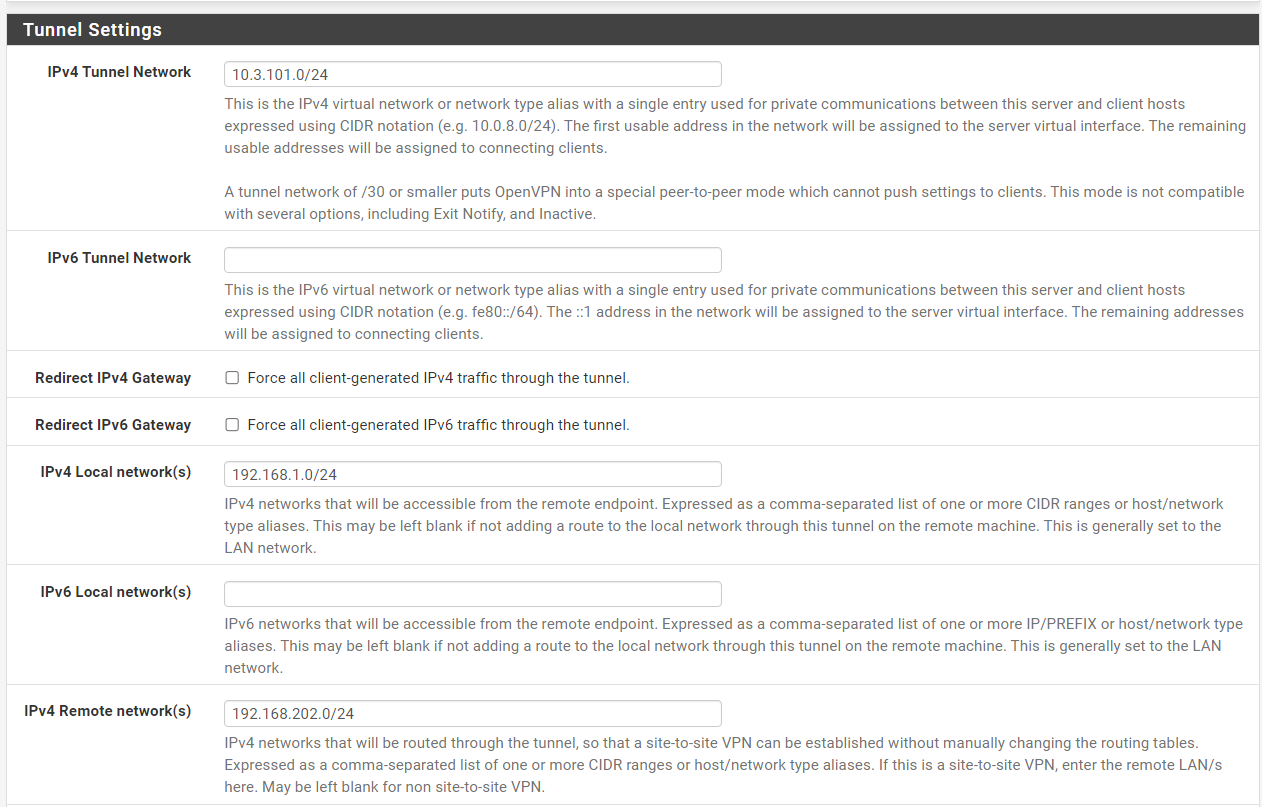
I added the clients LAN because in negate guide it says so.
Client Override Settings looks like this (I also tried without "192.168.202.0/24):
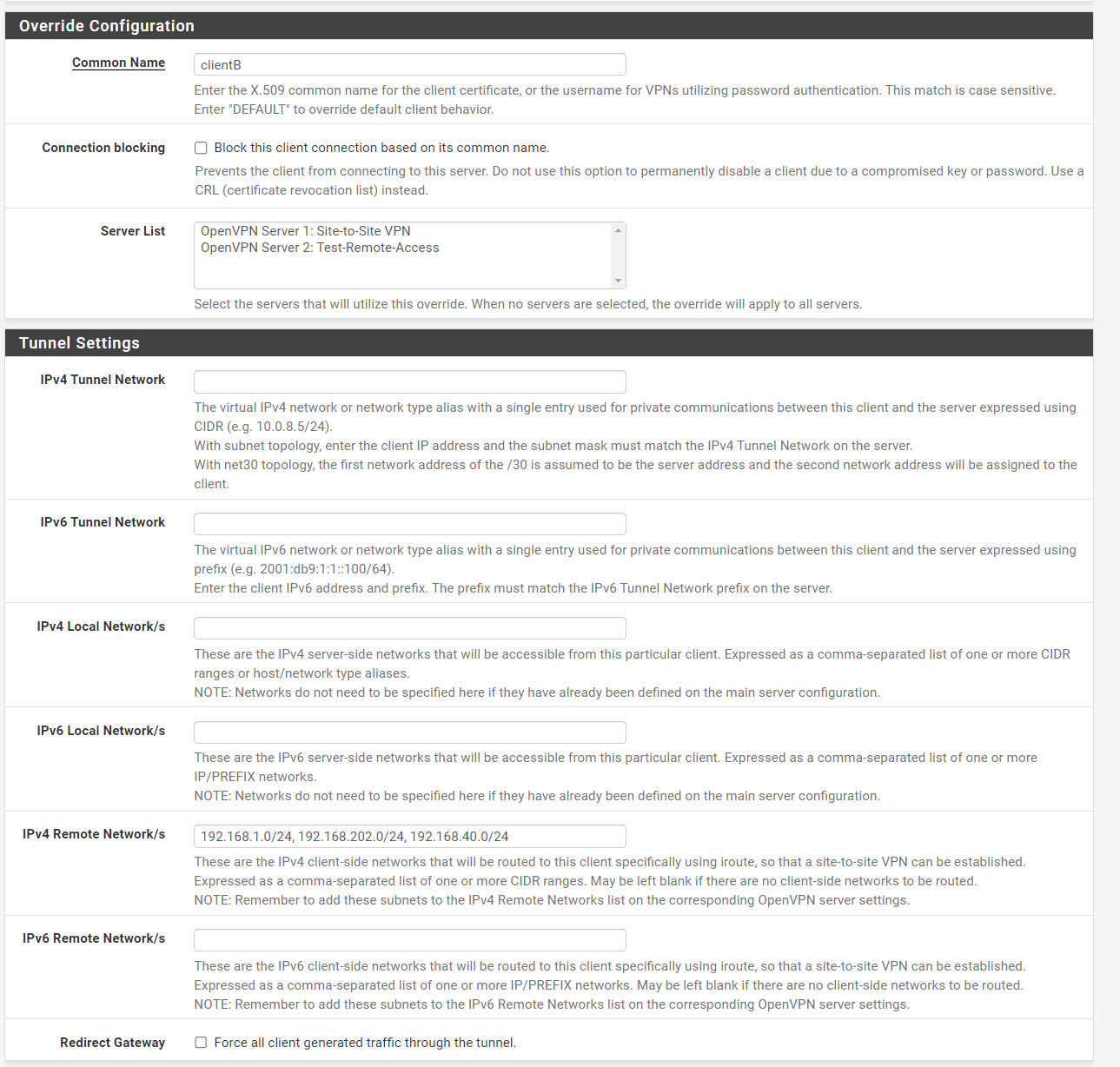
Is this correct? Is the common Name correct?
For your information i connect to VPN access Server with username "wdadmin", also tried client overrides for this common name - not working.
Tracert on laptop client looks like this:
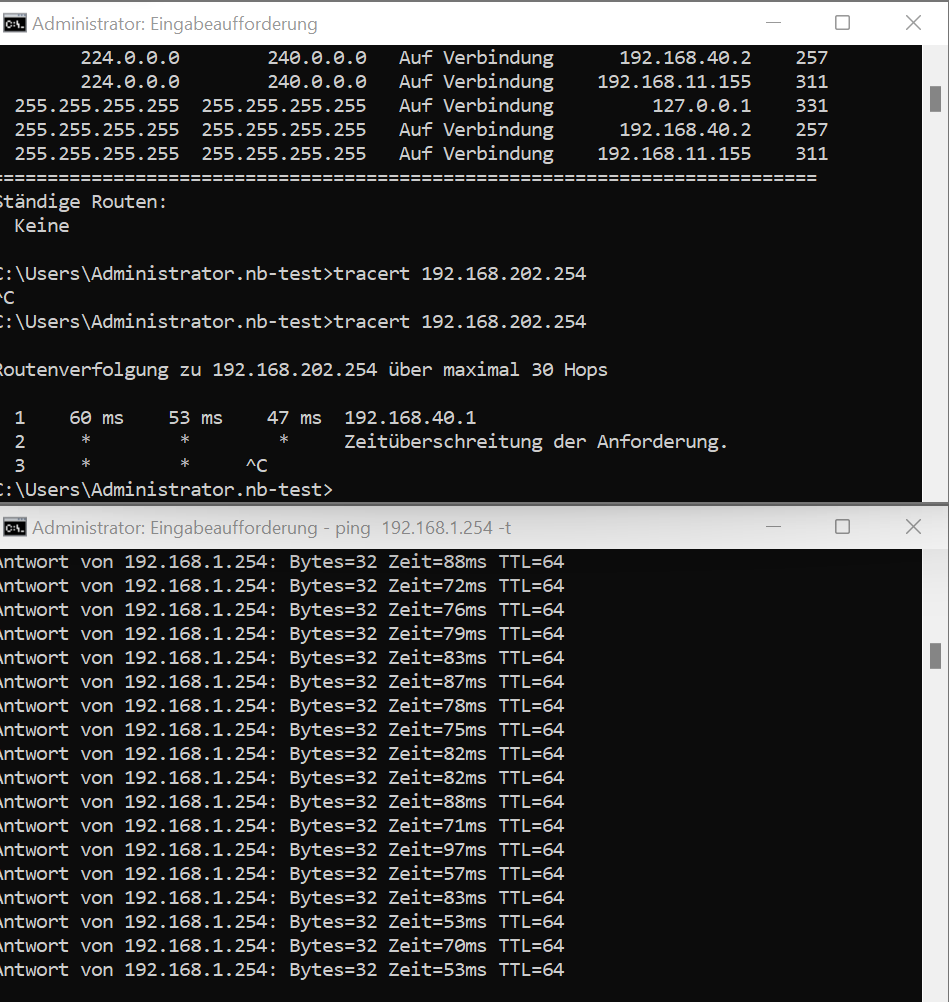
-
@Florian-Wögerbauer said in Remote Access LAN from client behind OpenVPN Site-to-Site Tunnel:
I added the clients LAN because in negate guide it says so.
Yes, this is correct.
Client Override Settings looks like this (I also tried without "192.168.202.0/24):
Is this correct? Is the common Name correct?
No. Again, at "Remote Networks" only enter the s2s clients LAN, nothing else.
For your information i connect to VPN access Server with username "wdadmin", also tried client overrides for this common name - not working.
Normally the common name from the clients certificate is used to determine the client for CSO.
After connecting check the OpenVPN log on the server to find out if the CSO is applied properly.And again as well: State the remote networks in the clients settings (not CSO). VPN > OpenVPN > Clients > Edit
At "IPv4 Remote network(s)" enter192.168.1.0/24,192.168.40.0/24 -
@viragomann
Okay on COS in Remote Networks i enter only clients LAN:
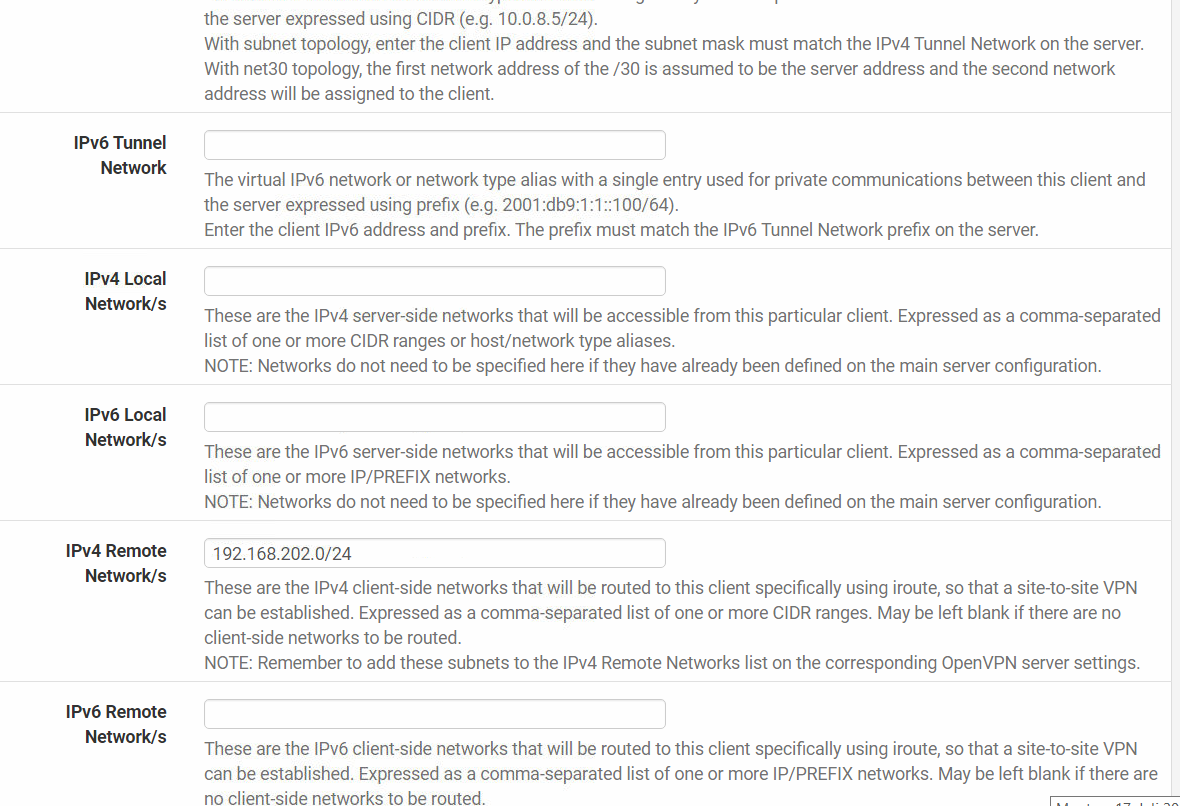
On Client Site i enter Remote Network, not surprised (192.168.40.0/24, 10.3.0.0/24 is the same i changed it):
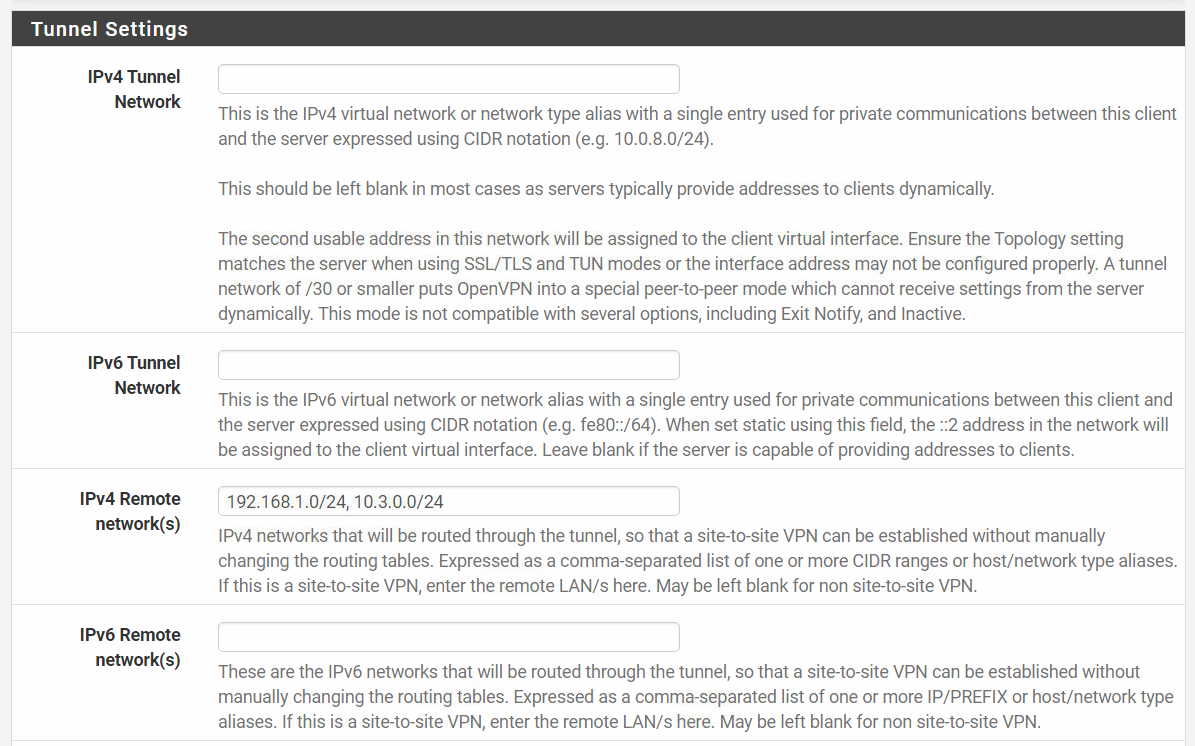
For my User i connect to Remote Access Server "xneadmin" i also create CSO:
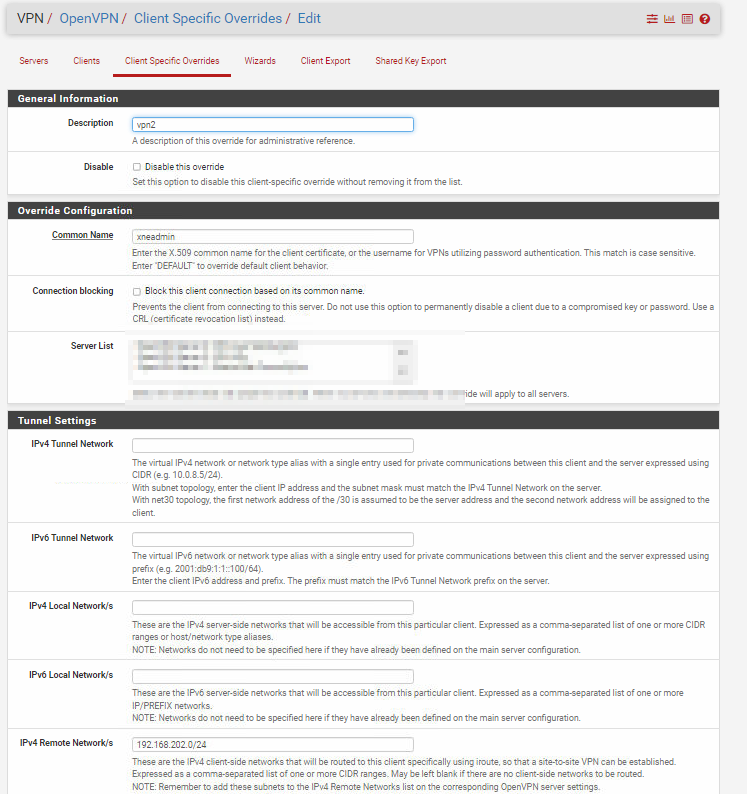
CSO also working i check it in Connectionstate:
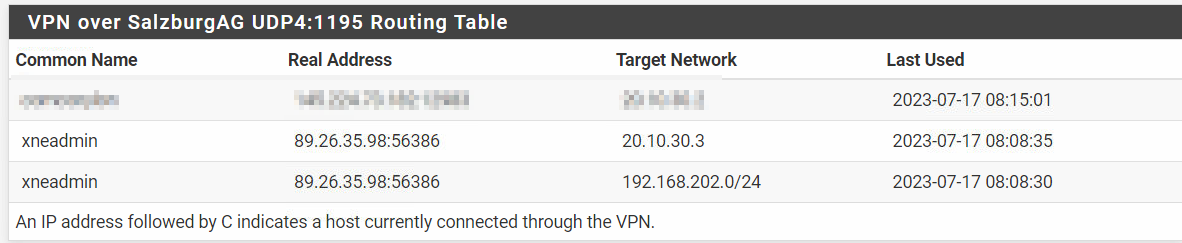
But still not working.
-
@Florian-Wögerbauer said in Remote Access LAN from client behind OpenVPN Site-to-Site Tunnel:
For my User i connect to Remote Access Server "xneadmin" i also create CSO:
In the "Remote Networks" setting in the CSO you have to state the local network of the respective client. This is used by OpenVPN to route access to accordingly.
But you must not state the same remote network on two different CSO.
And furthermore a CSO is only needed for accessing the client sides local network. I guess, this is not necessary for this client.
Please check if the site2site CSO is applied. I'm not sure if it is, if the server is in peer-2-peer mode. Maybe you have to move to access server mode.
Or you can change the tunnel mask to /30 in the peer-2-peer server, but these setting is deprecated and will not be supported in future versions. -
@viragomann
thanks for help. I tried so many things and nothing works.
I solved it differently now. I connect direct to the client pfSense.
I solved it differently now.