pcap on alert
-
Is there a way to capture a pcap whenever an alert is triggered for further analysis of the alert?
I currently have this set in my interface config
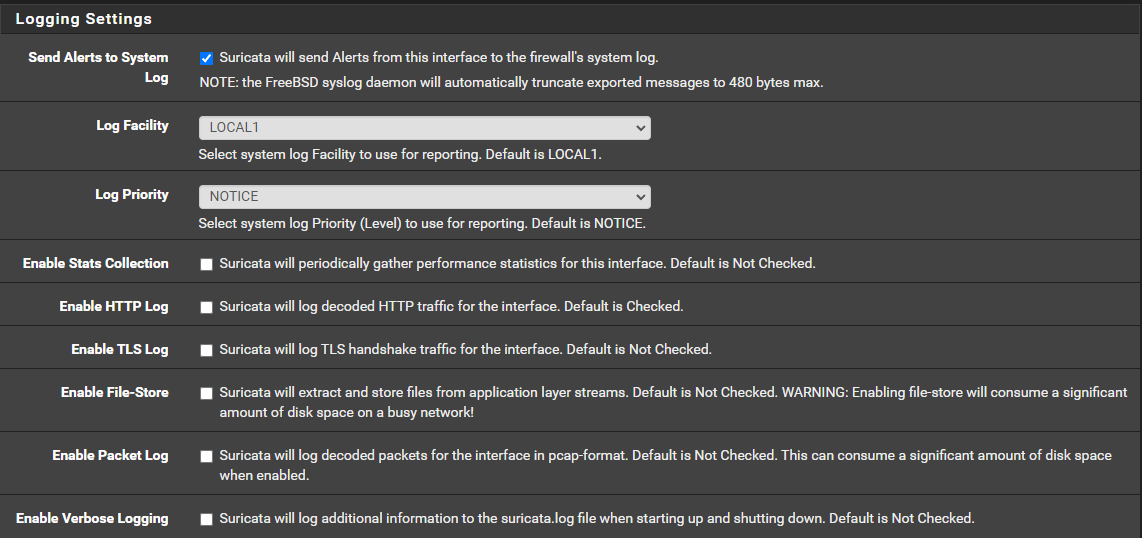
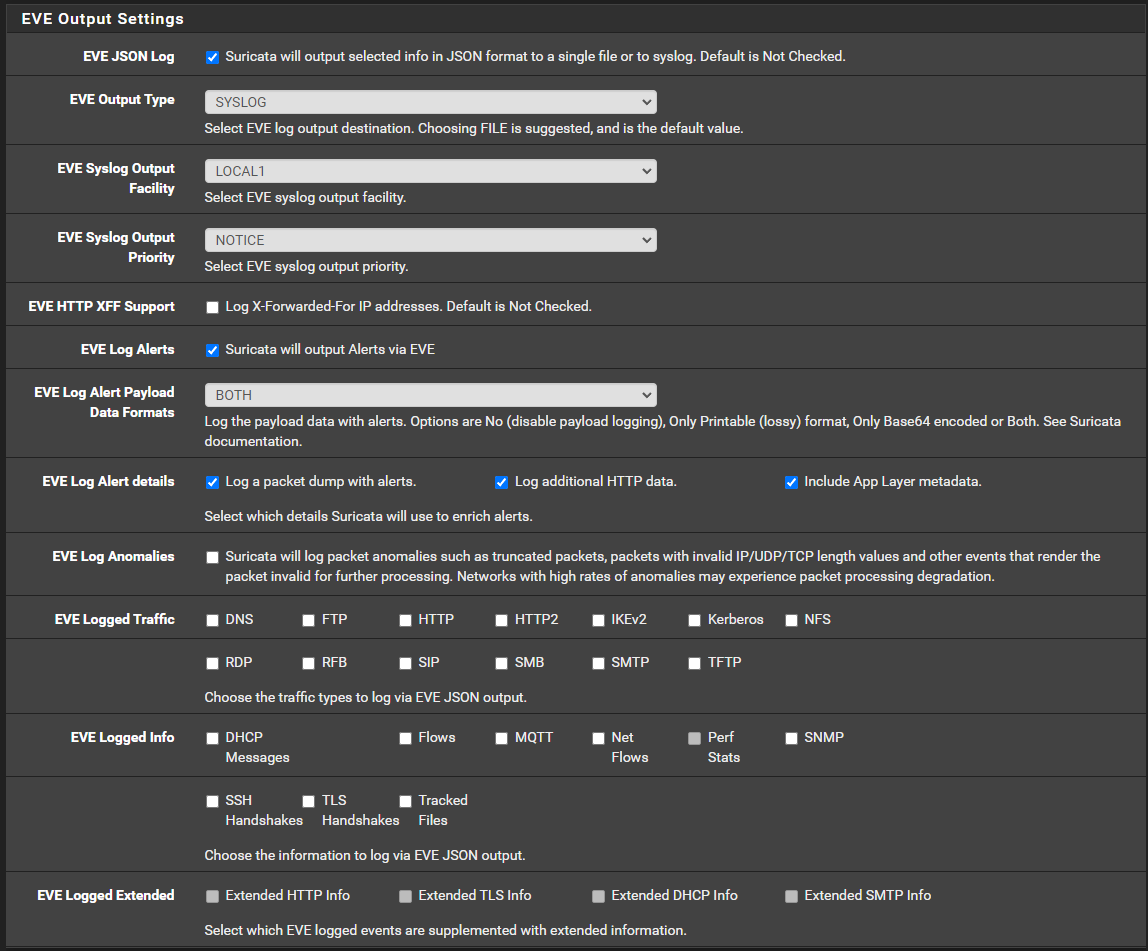
To me this suggests that I am using eve output to export the payload and a packet dump whenever there is a suricata alert detection, but I can't find where this information is stored, and I don't seeing it coming across the syslog over to graylog.
Any help would be greatly appreciated.
-
The setting you have enabled for EVE logging will write the data into the current EVE JSON log in
/var/log/suricata/suricata_xxxxxx/(wherexxxxxxwill be a GUID and the interface name). That log is NOT sent to syslog and thus won't be grabbed by your Graylog interface.However, you can check the box under Logging Settings called Enable Packet Log and that will log the packet info to syslog. From there, Graylog will be able to grab it. But there is a big caveat with that. The syslog daemon in FreeBSD (and thus in pfSense as well) will truncate syslog messages at 480 bytes (if I recall correctly). Thus your packet log via syslog will be severely limited.
A better approach, but one that will require a lot of manual effort to set up on your part, is to configure something like an ELK stack to export the EVE JSON logging info. Unfortunately, there is no existing package on pfSense for doing that, so you would need to Google some "how-to tutorials" and manually install what's needed.
-
@bmeeks appreciate the response.
I will just check that directory manually on the next alert and see what is generated. Don't really need it sent to a second location as I don't expect too many of these popping up.
-
@bigjohns97 said in pcap on alert:
@bmeeks appreciate the response.
I will just check that directory manually on the next alert and see what is generated. Don't really need it sent to a second location as I don't expect too many of these popping up.
There will be a lot of information in that EVE JSON log and all of it in JSON formatting which is a bit confusing at first. Because so much can get logged to that log file, it may frequently rotate as well. You can see the previous rotated logs in the same directory. They will have a timestamp appended to the filename.
-
@bmeeks Ended up going with the following config
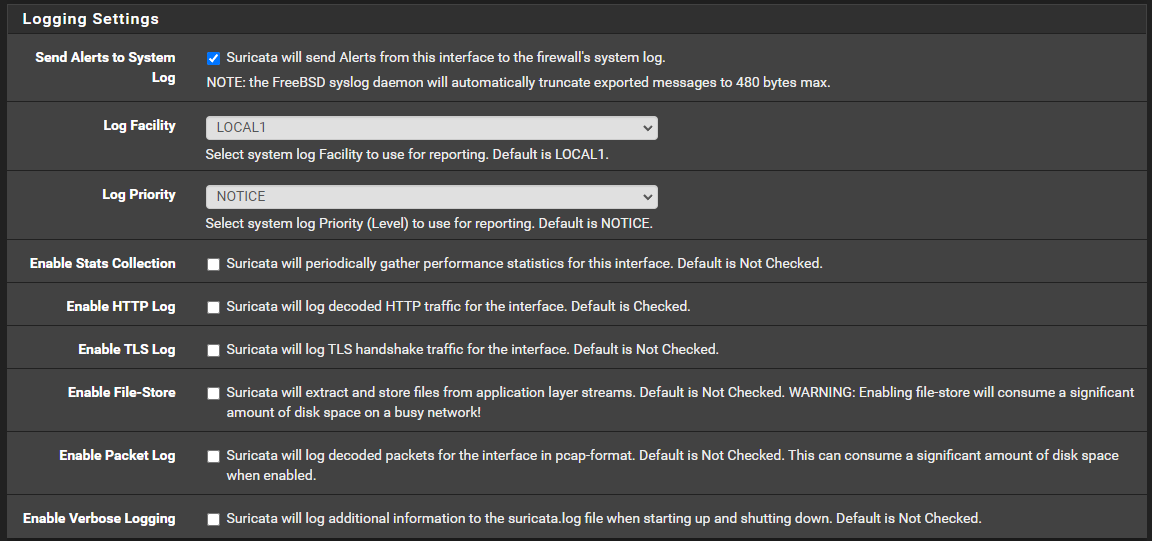
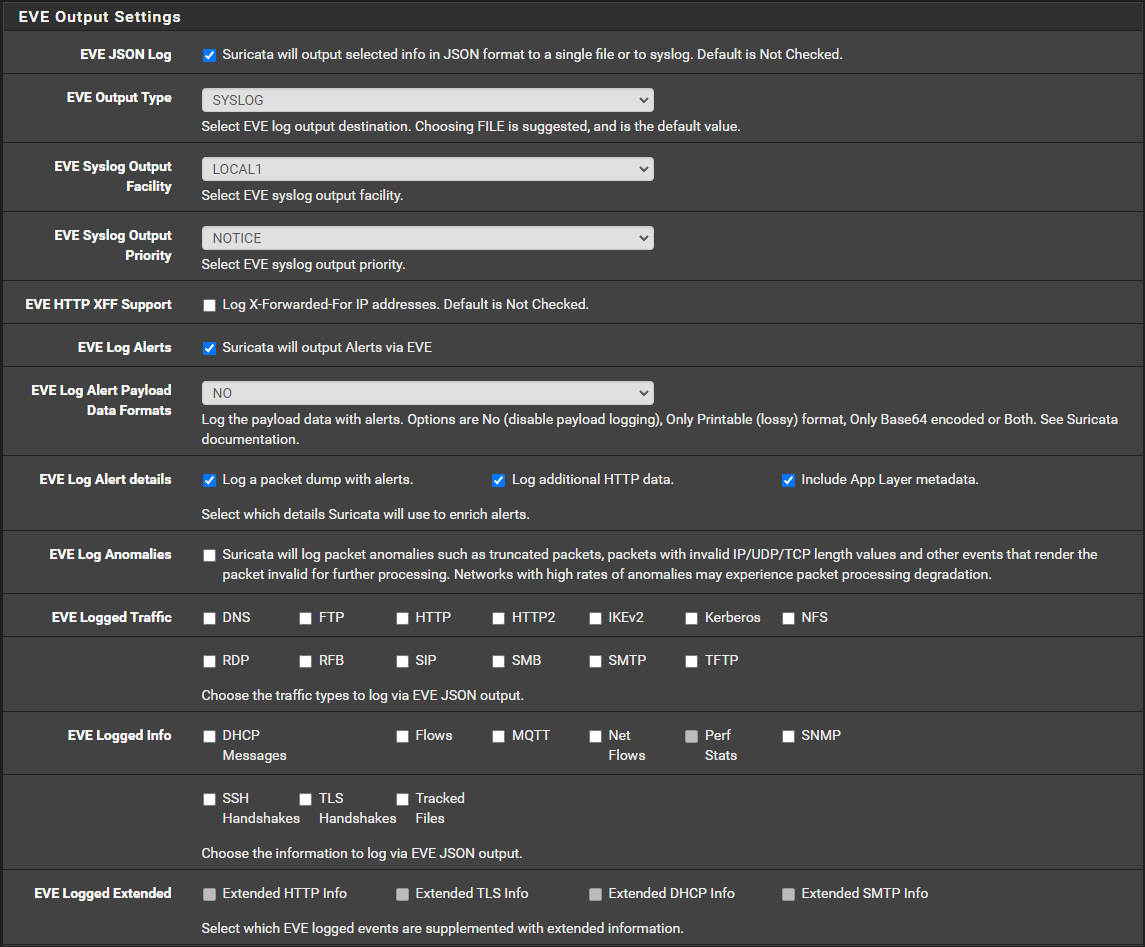
Trying to not hammer the NVMe drive that pfsense boots from into oblivion and it seems the payload as well as the packet dump in the eve log alerts section are the same thing, so I disabled the payload option because the packet dump will catch what information does get captures before the truncation.
All of the ELK solutions out there would require me writing to this drive first and then sending over to external logger so I would still need to get a second drive before feeling comfortable doing that.
It's a shame that suricata doesn't just support dumping alerts into a pcap as a simple option, it's already utilizing pcap in legacy mode to detect the alert so it's already in memory, just dumping that to a pcap on the local drive would limit the drive wear as well as providing a full picture into what happened during the alert for later analysis.
-
@bigjohns97 said in pcap on alert:
It's a shame that suricata doesn't just support dumping alerts into a pcap as a simple option,
The upstream developers decided quite some time ago to hitch their wagon to EVE JSON logging. Since that move, they have been slowly deprecating the older conventional syslog logging mechanisms.
And I concur that Suricata and Snort (and a few other heavy logging packages on pfSense) really need spinning conventional disks due to the sheer volume of data they can log on a busy network.
-
@bmeeks It looks like they might have put this into v7.
https://forum.suricata.io/t/how-to-log-alert-into-a-pcap/2127/4