Slow upload to server
-
@Marci Are you testing on WiFi or cellular? Either one your speeds will vary.
What are the speeds when not on vpn? -
@michmoor On the client side I am testing on cellular, server is connected via cable to ISP.
The connection on the server side has a 200 Mbit download and 60 Mbit upload line. The client side which I used for the test has 130 Mbit download and 85 MBit upload speed, without VPN. -
@Marci are you using tcp or udp? have you tried increasing sndbuf rcvbuf?
-
@hr1sha I am using UDP and I have really good download speed. Therefore I guess the protocol works.
I have tried setting
sndbuf 512000;
rcvbuf 512000;
push "sndbuf 512000";
push "rcvbuf 512000";
on the server side but it did not have any effect (I am not sure about the commands/values, I googled these). -
This post is deleted! -
@Marci please show your server and client configuration
-
@hr1sha
Client:dev tun persist-tun persist-key data-ciphers AES-256-GCM:AES-256-CBC data-ciphers-fallback AES-256-GCM auth SHA512 tls-client client resolv-retry infinite remote *deleted IP* *deleted port* udp4 lport 0 verify-x509-name "VPN server Cert" name auth-user-pass remote-cert-tls server explicit-exit-notifyServer:
reneg-sec 36000; sndbuf 393216; rcvbuf 393216; push "sndbuf 393216"; push "rcvbuf 393216";Thanks for looking into this

-
@Marci said in Slow upload to server:
reneg-sec 36000;
sndbuf 393216;
rcvbuf 393216;
push "sndbuf 393216";
push "rcvbuf 393216";Noop.
These are the option you added manually.edit : and you don't need to add
sndbuf 1048576 rcvbuf 1048576and these get added as soon as you select :
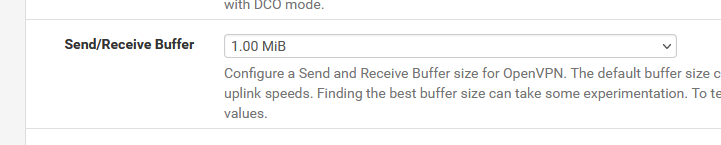
reneg-sec 36000;is more a security thing. Maybe not ok to set this to 10 hours. The default '3600' won't bite you (one hour !)
The actual OpenVPN server config looks like a OpenVPN client config.
Go console, or better : SSH,, option 8 :
It's here : /var/etc/openvpn/serverX/config.ovpn
Where X is your server ID, normally it's '1'Here it is :
dev ovpns1 disable-dco verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh learn-address "/usr/local/sbin/openvpn.learn-address.sh bhf.net" local 192.168.10.4 engine rdrand tls-server server 192.168.3.0 255.255.255.0 client-config-dir /var/etc/openvpn/server1/csc tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'bhf.net' 1" lport 1194 management /var/etc/openvpn/server1/sock unix max-clients 10 push "dhcp-option DOMAIN bhf.net" push "dhcp-option DNS 192.168.3.1" push "block-outside-dns" push "register-dns" push "redirect-gateway def1" client-to-client remote-cert-tls client capath /var/etc/openvpn/server1/ca cert /var/etc/openvpn/server1/cert key /var/etc/openvpn/server1/key dh /etc/dh-parameters.2048 tls-crypt /var/etc/openvpn/server1/tls-crypt data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 data-ciphers-fallback AES-256-GCM allow-compression asym persist-remote-ip float topology subnet status /var/log/openvpn.status status-version 1Note : my custom config :
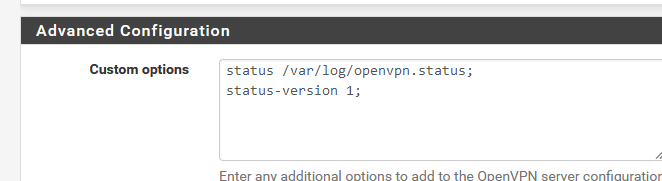
so these are just added to the rest.
-
@Marci try changing the encryption algorithm to 128 and test. A large buffer size is not always a good thing.
-
Could the iPhone be the bottleneck pushing encrypted traffic?
Maybe you can test with another more beefy client device first.-Rico
-
@Gertjan Thanks for the help, so here is the server config (I deleted some IPs)
dev ovpns2 verb 1 dev-type tun dev-node /dev/tun2 writepid /var/run/openvpn_server2.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA512 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local *IP deleted* engine rdrand tls-server server *IP deleted* 255.255.255.0 client-config-dir /var/etc/openvpn/server2/csc username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server2 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'VPN+server+Cert' 1" lport *port deleted* management /var/etc/openvpn/server2/sock unix max-clients 4 push "dhcp-option DOMAIN localdomain" push "dhcp-option DNS *IP deleted"" push "redirect-gateway def1" push "redirect-gateway ipv6" capath /var/etc/openvpn/server2/ca cert /var/etc/openvpn/server2/cert key /var/etc/openvpn/server2/key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server2/tls-auth 0 data-ciphers AES-256-GCM:AES-256-CBC data-ciphers-fallback AES-256-GCM allow-compression no persist-remote-ip float topology subnet sndbuf 524288 rcvbuf 524288 push "sndbuf 524288" push "rcvbuf 524288"I have also removed the manual entry for regen-sec and send/receive buffer (I used the pfSense GUI to set the send/receive buffer)
-
This post is deleted! -
@Rico That is a bit difficult for me as I am lacking the infrastructure for this test. I would need a PC/laptop in a different WLAN which I do not have.
-
@hr1sha Great
 that solved the issue, I am now getting the expected upload speed.
that solved the issue, I am now getting the expected upload speed.
I guess that means I have been limited by the iPhone hardware (like also @Rico suspected).I chose 256 encryption because I thought it is safer that 128, but after some quick research I guess 128 should be sufficiently safe (I guess).
-
This post is deleted!