Firewall rule to allow WAN outgoing
-
@silviub If you don't want to block every other VLAN then you have to create an RFC1918-alias for all private IPs and make a blockrule with that. This will at least work for IPv4.
-
@Bob-Dig that's not what I want.
I want to allow SEC1 traffic to leave the WAN interface (NATed) but I don't want SEC1 to be able to reach LAN/SEC2. -
@silviub said in Firewall rule to allow WAN outgoing:
that's not what I want.
Read the docs, you seem to have no clue at all how this works...
-
@Bob-Dig You are right, I have no clue how this works and I have read the docs, but they don't seem to answer my question.
I've got a simple question: how can I allow one VLAN to access the internet while limiting its access to any other VLANs. I feel like this is really difficult to accomplish using PFSense or I'm missing something (which is probably the case), that's why I opened this thread, to get some help so:
How would you achieve this, since it looks like you know your way around PFSense? In any other system (even FreeBSD) you can say "Pass from <interface> to <interface>...? -
@silviub said in Firewall rule to allow WAN outgoing:
@Bob-Dig that's not what I want.
I want to allow SEC1 traffic to leave the WAN interface (NATed) but I don't want SEC1 to be able to reach LAN/SEC2.On SEC1:
- reject from Sec1 Net to LAN
- reject from SEC1 Net to pfSense port 443/22 (if desired)
- allow from SEC1 Net to any
Rules are applied on the interface as packets arrive. “Any” being all IPs which includes the Internet.
-
@silviub said in Firewall rule to allow WAN outgoing:
another saying "Pass to !LAN_net" but if I'll ever get into having 5 - 10 - 20 networks.....)
The easiest solution to this - ie you adding more networks and not having to adjust your rules is create the mentioned rfc1918 alias.. Assuming all of your future vlans would be rfc1918 space.
Here is an example locked down vlan, it really can only go to the internet - other than the couple of things allowed. ping to check connectivity to its gateway (pfsense) and dns and ntp.
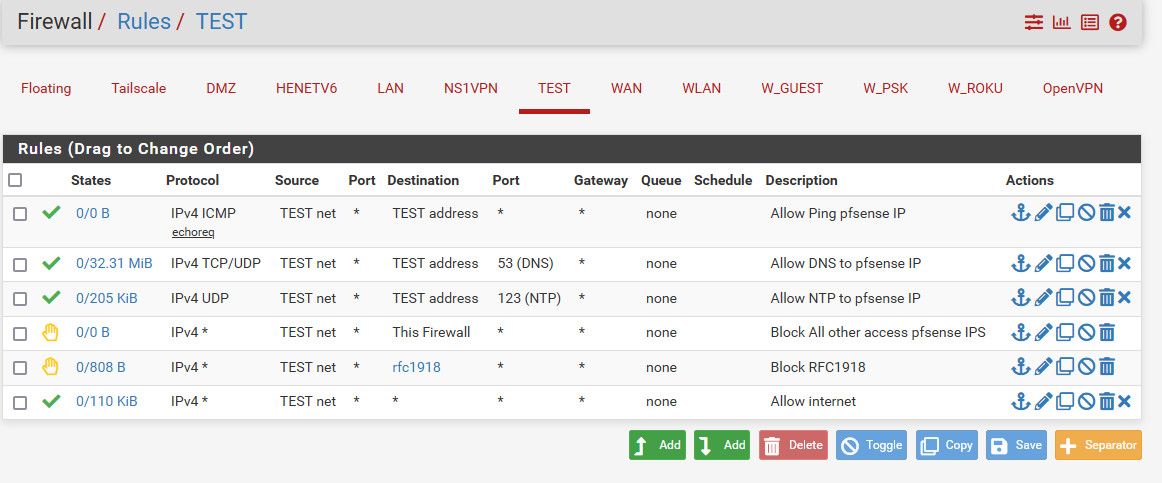
The rfc1918 alias contains all the rfc1918 space, with just 3 entries.
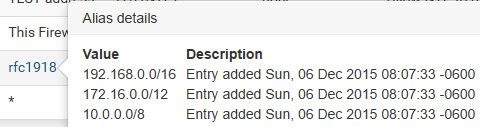
So if I added a new vlan, say 172.16.31.0/24 this network would not be able to go to it, now if I created some vlan that was not using rfc1918 space it would be allowed because of the last rule that allows any (internet)..
The reject to "this firewall" prevents this network from talking to say the pfsense wan IP (which is public IP).. So sure that this network can not get to pfsense web gui or ssh, etc.
-
-
@silviub not really a fan of bang rules. Its better to be very explicit in what is allowed or rejected. For one its easier to read as human - this is allowed, this not - vs oh there is a little ! symbol - the opposite is actually allowed, etc.
And if you use vips there has been some issues, etc..
I would just add the 2 rules, so its very clear to what is allowed and what is not. There is no performance issue if you have 10 rules or 1000..
-
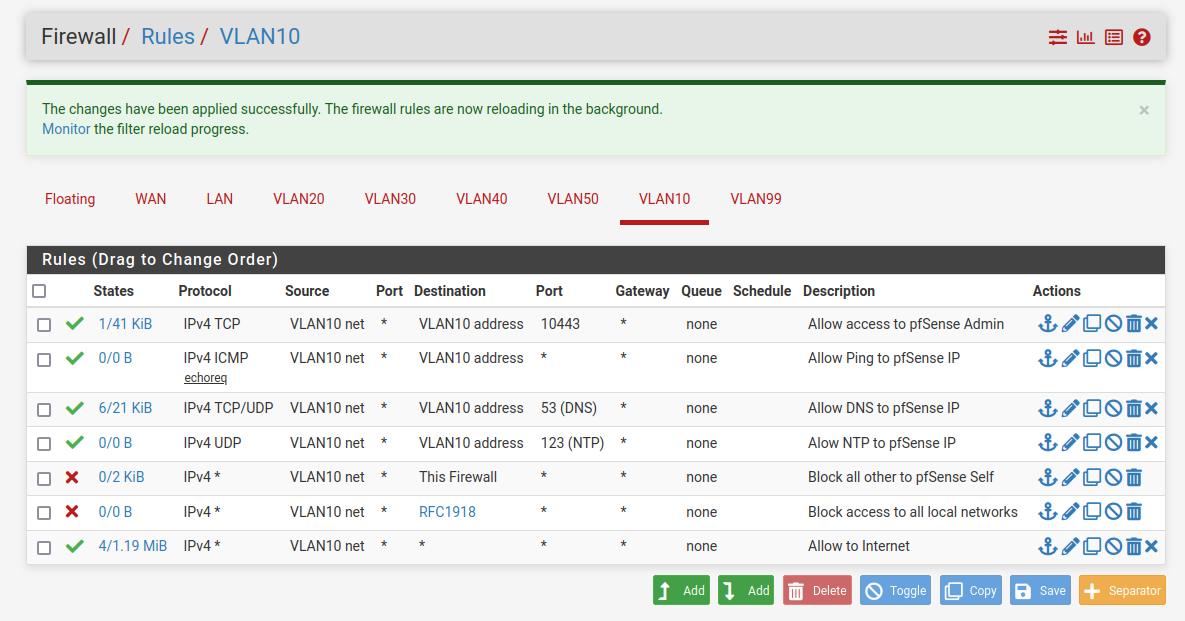
I had a similar questions and found my answers here. Thank you to all that replied. Following johnpov's example, I also wanted to add acess to the Admin page which I moved from port 80 to port 10443. I added the first line in my firewall rules for this. Is this a good secure way to allow access to the Admin page? I will not add that line to the other VLANS, so only VLAN10 can access the Admin page. Thank you.
-
@pV5 yep that will work
-
@pV5 normally if I was locking down a vlan, I wouldn't allow access to the pfsense gui. But what you allow or block is up to you.