wireguard and one interface multiple peers with network 0.0.0.0/0
-
@Bob-Dig When I add 0.0.0.0/0 in both, each of the gates is no longer reachable. It says here that the address must be unique. So it follows that I have to add each network manually? What if there are the same networks on both sides? Need to use NAT 1:1?
Allowed IP entries here will be transformed into proper subnet start boundaries prior to validating and saving. These entries must be unique between multiple peers on the same tunnel. Otherwise, traffic to the conflicting networks will only be routed to the last peer in the list.
-
@adam23450 said in wireguard and one interface multiple peers with network 0.0.0.0/0:
each of the gates is no longer reachable. It says here that the address must be unique.
Where does is say that?
-
@Bob-Dig Here
Peer >Address Configuration > Hint > Allowed IP entries here will be transformed into proper subnet start boundaries prior to validating and saving. These entries must be unique between multiple peers on the same tunnel. Otherwise, traffic to the conflicting networks will only be routed to the last peer in the list. -
@adam23450 said in wireguard and one interface multiple peers with network 0.0.0.0/0:
Peer >Address Configuration > Hint >
So I guess you have to make two tunnels then.
-
@adam23450 " I want to create site-to-site tunnels to several places ... I want traffic to be available for all networks on one WG interface"
Yes, that is how WG works...
"So I guess you have to make two tunnels then."
No, you make one tunnel and allow multiple peers.
The tunnel is just the connection from your pfSense box to the internet. That's why each device has a tunnel.
If you insist on the Mikrotiks WG tunnel being on a different subnet, then yes, you have to have two tunnels.
It would be so much easier to put them all on 172.17.1.X. It doesn't matter if the M's LAN is 10.X.X.X, the VPN doesn't care. Your static routes take care of that.
-
PfSenseGW
TUNNEL IPv4 Address:172.17.2.1/24
PEER Allow IP:172.17.2.2/32 Allow IP:(whatever Server 1 LAN subnet is)
PEER Allow IP:172.17.2.3/32 Allow IP:(whatever Server 2 LAN subnet is)
PEER Allow IP:172.17.2.4/32 Allow IP:(whatever Server 3 LAN subnet is)
PEER Allow IP:172.17.2.5/32 Allow IP:10.91.1.0/24 Allow IP:10.80.92.0/24
PEER Allow IP:172.17.2.6/32 Allow IP:192.168.0.0/24 Allow IP:192.168.1.0/24 Allow IP:192.168.3.0/24 Allow IP:10.80.0.0/24Server 1
TUNNEL IPv4 Address:172.17.2.2/24
PEER Allow IP:172.17.2.1/32 Allow IP:10.91.1.0/24Server 2
TUNNEL IPv4 Address:172.17.2.3/24
PEER Allow IP:172.17.2.1/32 Allow IP:10.91.1.0/24Server 3
TUNNEL IPv4 Address:172.17.2.4/24
PEER Allow IP:172.17.2.1/32 Allow IP:10.91.1.0/24Mikrotik 1
TUNNEL IPv4 Address:172.17.2.5/24
PEER Allow IP:172.17.2.1/32 Allow IP:10.91.1.0/24Mikrotik 2
TUNNEL IPv4 Address:172.17.2.6/24
PEER Allow IP:172.17.2.1/32 Allow IP:10.91.1.0/24At this point, you should be able to ping the VPN endpoint IPs.
All the above does is connect the VPN together, it doesn't tell any machine how to route to the LANs. After you get the tunnels/peers set up, you have to configure the static routes so they route correctly.
To setup the static routes, you define the GATEWAYS and then assign the STATIC ROUTES (under the SYSTEM >> ROUTES tab). -
@JustAnotherUser said in wireguard and one interface multiple peers with network 0.0.0.0/0:
"So I guess you have to make two tunnels then."
No, you make one tunnel and allow multiple peers.
Sure but he wants to have 0.0.0.0/0 at more than one peer, for whatever reason.
-
@Bob-Dig
@Bob-Dig said in wireguard and one interface multiple peers with network 0.0.0.0/0:
Sure but he wants to have 0.0.0.0/0 at more than one peer, for whatever reason.
That's just routing... Just set the pfSense gateway as the default gateway at whatever peer.
-
@JustAnotherUser this configuration doesn't work for me. does it work on its own?
-
@adam23450
It's how I have my network configured... Different IPs for me but the setup is how I'm running.I've got 4 sites and they all connect to each other through WG in a star pattern (you're running a spoke pattern). The IPs are different but the CIDRs are currently working for me.
-
@JustAnotherUser Well, you have different unique ip addresses and subnets and it works and it doesn't work with 0.0.0.0/0
-
@adam23450 You keep saying 0.0.0.0 which means all traffic (a default gateway).
If you want your pfSense GW to be the default GW, you just have to tell each site to set the WG interface as the default GW and send all traffic through the WG connection.
SYSTEM >> ROUTING >> GATEWAY >> DEFAULT GATEWAY IPV4 <---this is the setting if you're using pfSense at the sites.
If your sites have different routers, you have to figure out how to configure your WG interface as the Default GW on each of those site routers.
By default, if your pfSense GW gets a request for an address not on one of your subnets (an internet address), it will send it out the WAN connection because the WAN should be set as the pfSense's Default GW. This means there shouldn't be any changes necessary on your pfSense GW.
Now, the individual sites have a Default GW set and that setting needs to be to the WG interface, otherwise, they just route out their WAN.
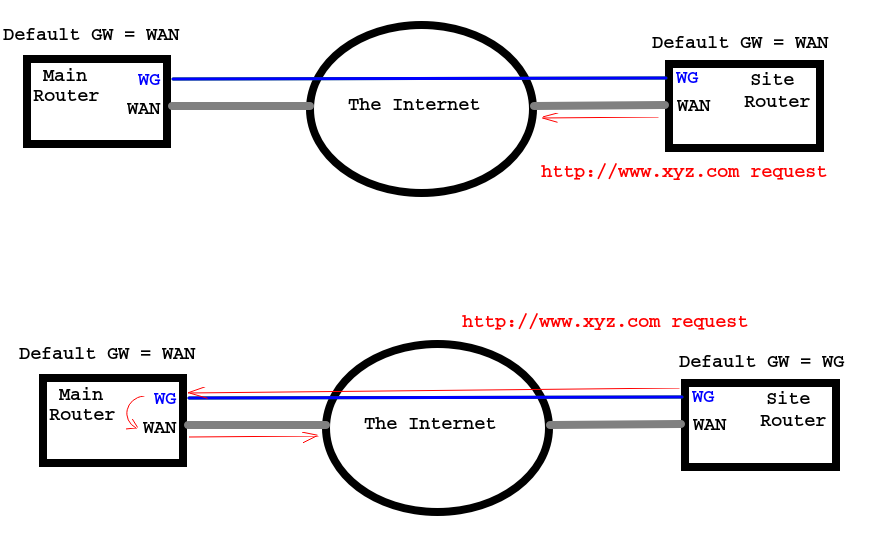
-
@JustAnotherUser yes it means default gateway, if i have several peers and i add them subnets 10.0.0.0/8 172.16.0.0/12 192.168.0.0/16 it also works last one i added.
-
@adam23450 said in wireguard and one interface multiple peers with network 0.0.0.0/0:
@Bob-Dig When I add 0.0.0.0/0 in both, each of the gates is no longer reachable. It says here that the address must be unique. So it follows that I have to add each network manually? ...
Allowed IP entries here will be transformed into proper subnet start boundaries prior to validating and saving. These entries must be unique between multiple peers on the same tunnel. Otherwise, traffic to the conflicting networks will only be routed to the last peer in the list.
@cmcdonald Now I became curious too, the limitation that only one peer can hold 0.0.0.0/0, is this an inherent limitation of WG or could/should it be changed for the implementation in pfSense?
I will connect mine to two other pfSense(s) and I want to use each as an "exit node" for mine. I will opt for two tunnels for now.