[Solved] Snort GPLv2 Community Rules - Unable to download checksum file
-
Hello,
Just wondering if anyone else has this problem again?
"pfSense CE 2.5.0" "Snort Package Version 4.1.3_2"
https://www.snort.org/downloads/community/snort-community-rules.tar.gz.md5 returns 404 (File not found)
https://www.snort.org/downloads/community/snort3-community-rules.tar.gz.md5 returns 200 and is a thing.I'm sorry to post in a resolved topic, but I believe we have the problem again.
Thanks.
-
@crsesilva
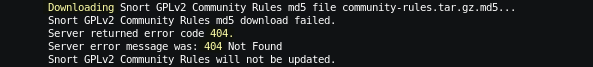
yes same here:Starting rules update... Time: 2021-03-27 11:07:31 [...] Downloading Snort GPLv2 Community Rules md5 file community-rules.tar.gz.md5... Snort GPLv2 Community Rules md5 download failed. Server returned error code 404. Server error message was: 404 Not Found Snort GPLv2 Community Rules will not be updated. -
Today, in a new download attempt, I was successful.
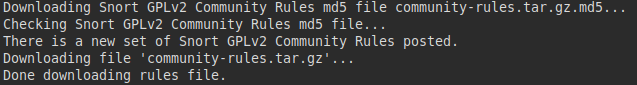
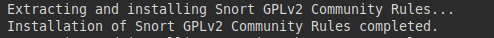
Looking at the download options page for snort.org in the community, Snort v2.9 appeared again. Yesterday, only Snort v3.0 available.

I want to believe that it is a one-off mistake and not forcing us to go immediately to Snort 3.0.
Thanks.
Cheers. -
This seems to be back:
Downloading Snort GPLv2 Community Rules md5 file community-rules.tar.gz.md5... Snort GPLv2 Community Rules md5 download failed. Server returned error code 404. Server error message was: 404 Not FoundIt looks like the Snort v2.9 community rules have been removed again?
-
Once again the Snort v2.9 community rules have been removed:

Excerpt from update log:
Downloading Snort GPLv2 Community Rules md5 file community-rules.tar.gz.md5... Snort GPLv2 Community Rules md5 download failed. Server returned error code 404. Server error message was: 404 Not Found Snort GPLv2 Community Rules will not be updated. -
Yes, I noticed this as well during some Suricata testing in a VM. This is a problem the Snort team will have to resolve.
Do NOT attempt to use the Snort3 rules with the 2.9.x binary! If you use any Snort3 rules with either Snort or Suricata, you will break your installation to the point the only recovery method is to remove the package and reinstall it.
-
This issue has once again been solved by the Snort Rules Team. The GPLv2 Community Rules for Snort 2.9.x are available.
-
@bmeeks Thank you.
I did send an email enquiry linking to this thread and describing the problem. I received a very brief reply effectively denying the problem.
I suspect the process that creates the
community-rules.tar.gzfile possibly breaks on occasion? -
@monotypetattoo said in [Solved] Snort GPLv2 Community Rules - Unable to download checksum file:
@bmeeks Thank you.
I did send an email enquiry linking to this thread and describing the problem. I received a very brief reply effectively denying the problem.
I suspect the process that creates the
community-rules.tar.gzfile possibly breaks on occasion?From the little bit I understand via previous email conversations with some of the Snort team members, this is an automated process. It sometimes hiccups, and I guess now that Snort3 is their main focus, they don't always notice if the 2.9.x rules packages fail to build and post correctly.
-
 F fireodo referenced this topic on
F fireodo referenced this topic on
-
Hi all, I'm new to pfSense.
I just installed it over the weekend and have this very issue from the start. My gateway has never seen the GPLv2 Community Rules for Snort 2.0.x. I find that it has happened a few times in years past. Seems to be back.
Do we need to keep reminding someone to fix this automated process?
Thanks! -
@xperttech said in [Solved] Snort GPLv2 Community Rules - Unable to download checksum file:
Hi all, I'm new to pfSense.
I just installed it over the weekend and have this very issue from the start. My gateway has never seen the GPLv2 Community Rules for Snort 2.0.x. I find that it has happened a few times in years past. Seems to be back.
Do we need to keep reminding someone to fix this automated process?
Thanks!This would be something you should take up with the Snort team. Perhaps by joining their mailing list here: https://seclists.org/snort/.
You should also be aware that if you have a Snort VRT subscription
(or are registered for their free 30-day aged rules), then you do not need to download the GPL v2 Community Rules separately as they are included within the subscriberand registeredpackages.Edited: found out only paid subscribers have the GPLv2 Community Rules included within that archive. Registered users (non-paying) get an archive that does not include the GPLv2 Rules.
-
@bmeeks said in [Solved] Snort GPLv2 Community Rules - Unable to download checksum file:
@xperttech said in [Solved] Snort GPLv2 Community Rules - Unable to download checksum file:
Hi all, I'm new to pfSense.
I just installed it over the weekend and have this very issue from the start. My gateway has never seen the GPLv2 Community Rules for Snort 2.0.x. I find that it has happened a few times in years past. Seems to be back.
Do we need to keep reminding someone to fix this automated process?
Thanks!This would be something you should take up with the Snort team. Perhaps by joining their mailing list here: https://seclists.org/snort/.
You should also be aware that if you have a Snort VRT subscription (or are registered for their free 30-day aged rules), then you do not need to download the GPL v2 Community Rules separately as they are included within the subscriber and registered packages.
I’m having the same exact issue although I’m a paid subscriber, so I just disabled the community rules. Something definitely happened in the last few days.
Update: It looks like Snort removed the community ruleset for v2.9.. #Shocker
-
@DefenderLLC said in [Solved] Snort GPLv2 Community Rules - Unable to download checksum file:
Something definitely happened in the last few days.
I guess asking Talos would bring clarity ... ;-)
-
@bmeeks
any change to bring SNORT 3.x to pfSense?
I guess this is much work, otherwise you would have done it a long time ago? -
@slu said in [Solved] Snort GPLv2 Community Rules - Unable to download checksum file:
@bmeeks
any change to bring SNORT 3.x to pfSense?
I guess this is much work, otherwise you would have done it a long time ago?No, I am not working on anything for Snort3 and have no future plans to do so. I tried it twice and gave up. The benefit was not worth the effort and hassle compared to just using the existing Suricata package.
At some point Snort 2.9.x is going to go EOL (end-of-life) upstream. At that point Suricata will be the IDS/IPS package on pfSense unless someone else steps up to provide a Snort3 package.
-
@bmeeks I'm guessing you probably have that reply saved in your notes somewhere for replies to this never-ending question. :)
-
@bmeeks said in [Solved] Snort GPLv2 Community Rules - Unable to download checksum file:
At that point Suricata will be the IDS/IPS package on pfSense unless someone else steps up to provide a Snort3 package.
Is there a good strategy to go from snort to suricata? (I mean with as less as possible hassle)
-
@fireodo I know you didn't ask me, but most of your rulesets will work. Some Snort rules might throw up an error. The good news is that your suppression lists should also work too since they seem to use the same format. For me, that's the hardest about tuning IDS/IPS on a new network. Just make sure to copy them before removing the Snort package. You also just disable any Snort interfaces while you're configuring Suricata. When you're done, then you can remove Snort and it's underlying data.
-
@DefenderLLC said in [Solved] Snort GPLv2 Community Rules - Unable to download checksum file:
@fireodo I know you didn't ask me, but most of your rulesets will work. Some Snort rules might throw up an error. The good news is that your suppression lists should also work too since they seem to use the same format. For me, that's the hardest about tuning IDS/IPS on a new network. Just make sure to copy them before removing the Snort package. You also just disable any Snort interfaces while you're configuring Suricata. When you're done, then you can remove Snort and it's underlying data.
Thanks! Ofcourse I will try to save as much of the settings (and most important the supression list) in a note-file.
-
@fireodo said in [Solved] Snort GPLv2 Community Rules - Unable to download checksum file:
Is there a good strategy to go from snort to suricata? (I mean with as less as possible hassle)
It's pretty much starting over with a green field install with regards to IDS/IPS. First thing to do is review the official Suricata docs from upstream here: https://docs.suricata.io/en/suricata-6.0.13/.
Here is what I would do next --
- Document your current Snort interface names (assuming you will want to run Suricata on those same interfaces).
- Take note of the rule families you are using. You can continue to use the majority of the Snort Subscriber Rules with Suricata. Just be aware that not all of them are compatible. Suricata will let you know which ones it does not like in the
suricata.logfile. Make sure you still have access to your Snort Oinkcode so you can enter it into Suricata if you plan to continue with the Snort Subscriber Rules. - Remove the Snort package first! You never want both of them installed and active at the same time. Make sure your Snort interfaces are all set to DISABLED before installing Suricata if you plan on leaving Snort there for a bit to copy over things like Suppress Lists. And if it were me, I would uncheck the option on the GLOBAL SETTINGS tab to save the old Snort configuration when removing Snort. I would not want it cluttering up my
config.xmlfile. But this is not a requirement. It won't hurt anything by remaining other than make the file slightly larger. - Install the Suricata package. With no existing configuration, it will install quickly.
- Go to the GLOBAL SETTINGS tab and enter your rules download configuration just like you did when you set up Snort.
- Now go to the UPDATES tab and download the rules you selected previously.
- When the rules download is completed, go to the INTERFACES tab and configure your interfaces. For each interface click on the Edit icon to access its configuration parameters. Note that Suricata relies heavily on its EVE JSON logging system whereas Snort primarily used syslog. Suricata can also use syslog, but with some limitations. There is a multitude of EVE JSON logging options available in Suricata. Details about each can be found in the Suricata docs link provided up above.
- For each configured interface, remember to visit the CATEGORIES tab and select the rules groups you desire. Or you can use the SID MGMT feature if preferred. This all works exactly like it does in Snort.
- Start up all your interfaces and monitor things for a while.
Some Observations:
- The GUI look and feel is almost identical between Snort and Suricata. Suricata's PHP code was in large part a simple copy and paste from existing Snort code in many areas. So, there should be no big surprises in terms of the GUI between Snort and Suricata.
- Suricata does not have OpenAppID nor any similar feature. Anything you had around OpenAppID in Snort will not be available in Suricata.
- Suricata does NOT use preprocessors. There are no preprocessor configuration options. That simplifies setup a bit in my opinion.