Whitelisting specific inbound IP addresses
-
Good morning,
I’m currently trying to allow specific IP addresses to ping one of my servers, I used pfblockerng for geo ip blocking. I attempted to move the ip white list rule up above all of the blocking rules and it works but the order changes back to default when it reloads. When I change the order of how pfblockerng should be blocking and I change it to allow it works but then it stops geo ip blocking. Does anyone know how to only allow specific ips inbound while geo ip blocking?
-
@sfigueroa You can change the sort order
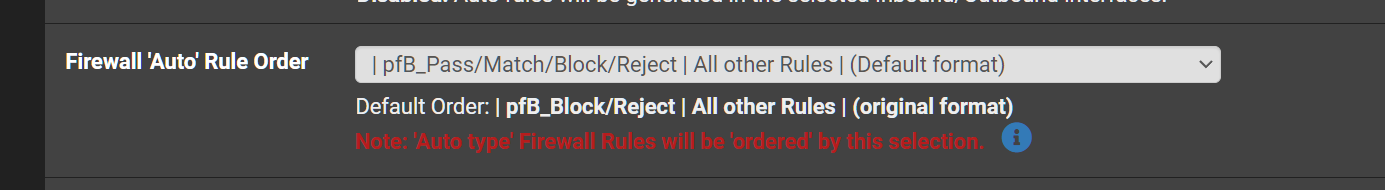
So you probably want your rule (not created by pfblocker) at the top. Therefore change it to the following
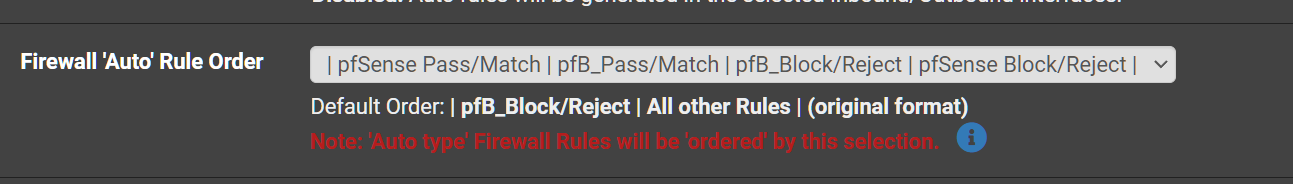
-
@michmoor I did that reordered my rules and when I reload the go back down to the bottom of the list
-
@michmoor When I duplicate it it moves it too, do I need to fully recreate it manually?
-
@michmoor sorry I hope I’m being clear haha. What I’m trying to achieve is to have the certain ips that are white listed at the top and and some ips under the pfblocking rules so they would technically sit in the middle of the rule order
-
@sfigueroa I think i understand what you are asking for. Similar to what ive done.
I created an Alias having certain IPs [192.168.5.1 - 192.168.5.5] That option i showed you in the picture allows you to put your custom rules at the top. Then pfblocker. Then you can put custom rules at the bottom.
All this assumes you are using Floating Rules so pfblocker creates it there which is what i would recommend anyway. -
@michmoor yea I’m trying would to be able to show me a screenshot of where you’re adding your rule? And how it shows in your firewall? My pfsense firewall rules where created in the wan firewall area I have some in the floating but the “geo ip” blocks got created in the regular fire wall area. I did add an alias with the ip and attempted to add. I’ll keep trying, no worries if you’re unable to show me an example.
-
@michmoor I think I got it!
-
@sfigueroa I take it back I don’t have it
-
@sfigueroa You have to update-reload to see the changes.
-
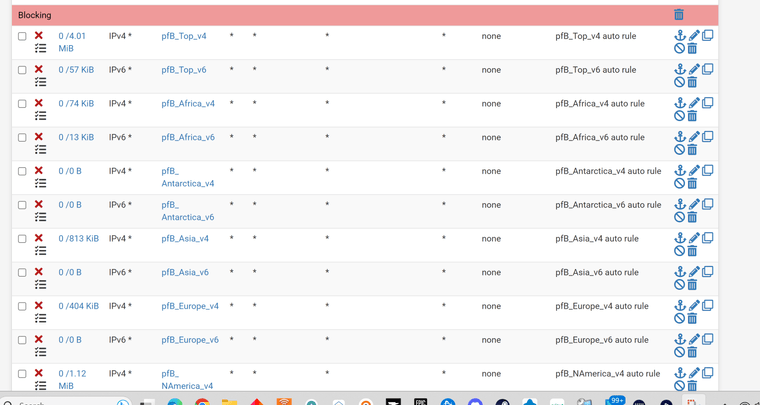
@Bob-Dig Am I manually adding the below in the floating tab? or should they already be there? because I only see them in the rules section not floating. Im trying to understand how it knows th order.
-
@sfigueroa My advice. That screenshot i would assume is for your WAN facing.
By default, pfsense blocks all inbound attempts. So you blocking the world may not make sense if you are not hosting services behind your firewall.
If you are hosting services behind your firewall, then you are better off only whitelisting / passing just the countries you need instead of blacklisting the ones you dont.