in Site-to-Site OpenVPN can not access to the client LAN from Server
-
Hello,
I'm using pfSense 2.7 on the server side and pfSense 2.6 on the client side.
Server-side: 192.168.10.0/23
Client-side: 192.168.20.0/24
Tunnel Network: 192.168.250.0/24I have full access from 192.168.20.0/24 (client) to 192.168.10.0/23 (server), but on the server side, I just have access from 192.168.10.1 (server-side pfSense) to 192.168.20.0/24 (client) and I can't reach to the client LAN from server LAN.
Can anyone guide me to fix this problem?
Many Thanks,Server:
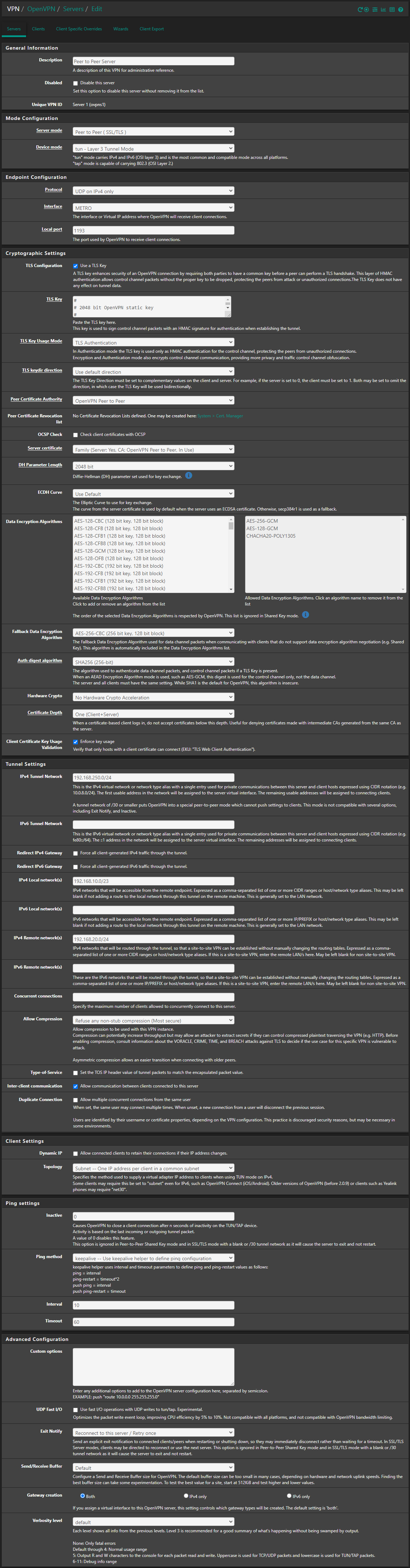
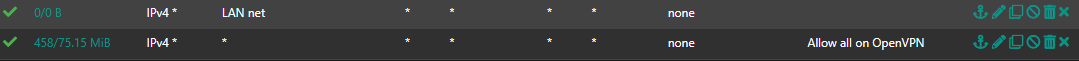
Server WAN Firewall Rules:

Server OpenVPN Firewall Rules:
Client:
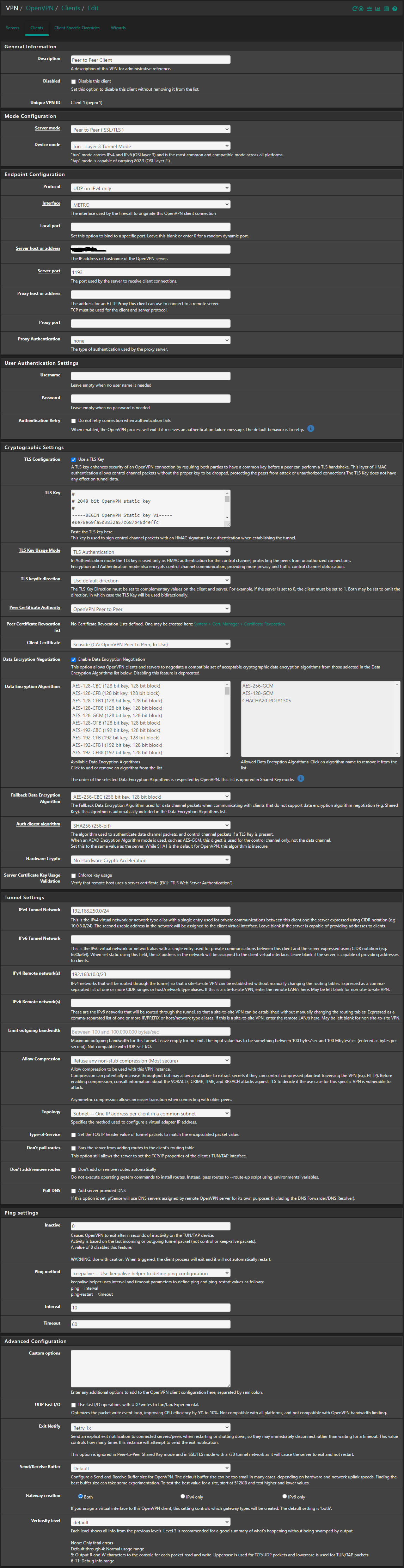
Client WAN Firewall Rules:
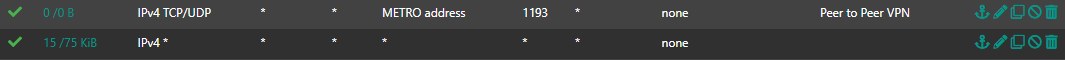
Client OpenVPN Firewall Rules:
-
@vahidmoghadam
Is the client the default gateway in its local network?Post the routing table of both, client and server, pleas. Diagnostic > Routes
In the server settings enhance the verbosity level to 4 and reconnect the client. Then check in the logs if the CSO is applied properly.
BTW: In the OpenVPN rules a pass rule for the source "LAN net" is useless. This is just the local LAN and will never be seen as source on this interface.
Also a pass any to any rule on WAN is pretty dangerous. And you don't need even a pass rule on the clients WAN to connect to the server. -
@viragomann
Thanks for your advice about the rules,Is the client the default gateway in its local network?Actually, I can't fully understand your question, But the locations of the server and the client are completely separate and far apart, and each of them uses the Internet (WAN) independently.
Server Routes:
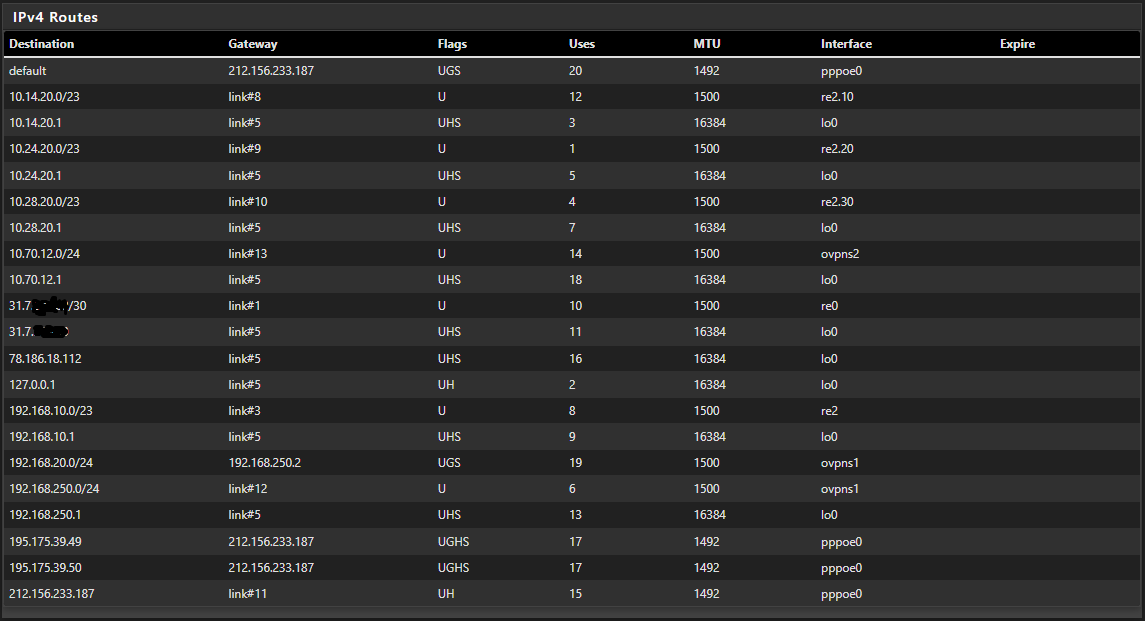
Client Route:
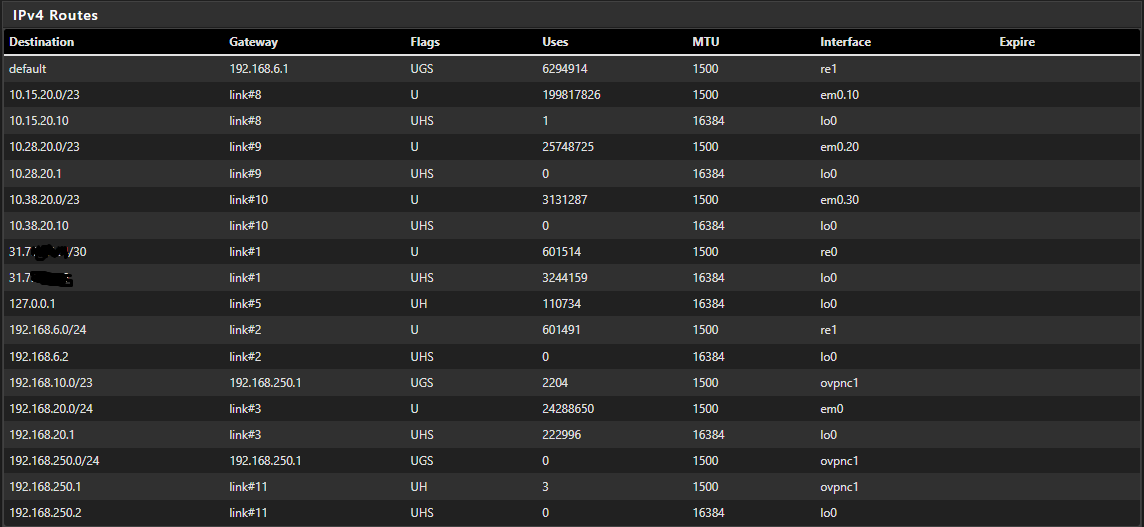
-
@vahidmoghadam
The question is if the devices in the clients pfSense LAN use it as default gateway or is there is another router for the internet connection.The routes look well.
Please post the servers log after enhancing the verbosity level as asked before.
Can you even ping the clients virtual IP 192.168.250.2 and the clients LAN IP 192.168.20.1 from the server side?
-
@viragomann
No, It's not the default gateway. In the previous configuration when I was using pfSense 2.6 and shared key in both, I didn't have any problem with the same configs on both sides.The client LAN can ping all of the IPs in the server LAN, But on the server side Just firewall can ping all of the IPs in the client LAN.
For example, the 192.168.20.101 machine can ping 192.168.10.4, but the 192.168.10.4 machine can not ping 192.168.20.101 or 192.168.20.1.
but just my server firewall 192.168.10.1 can ping all of 192.168.20.0/24And I test the ping of 192.168.250.2 from the server LAN, It's failed.
@viragomann , I sent logs to you in private chat, Thanks
-
@vahidmoghadam said in in Site-to-Site OpenVPN can not access to the client LAN from Server:
And I test the ping of 192.168.250.2 from the server LAN, It's failed.
At least this should work with your settings. The only one requirement for this is that the server pfSense is the default gateway on the server side devices.
-
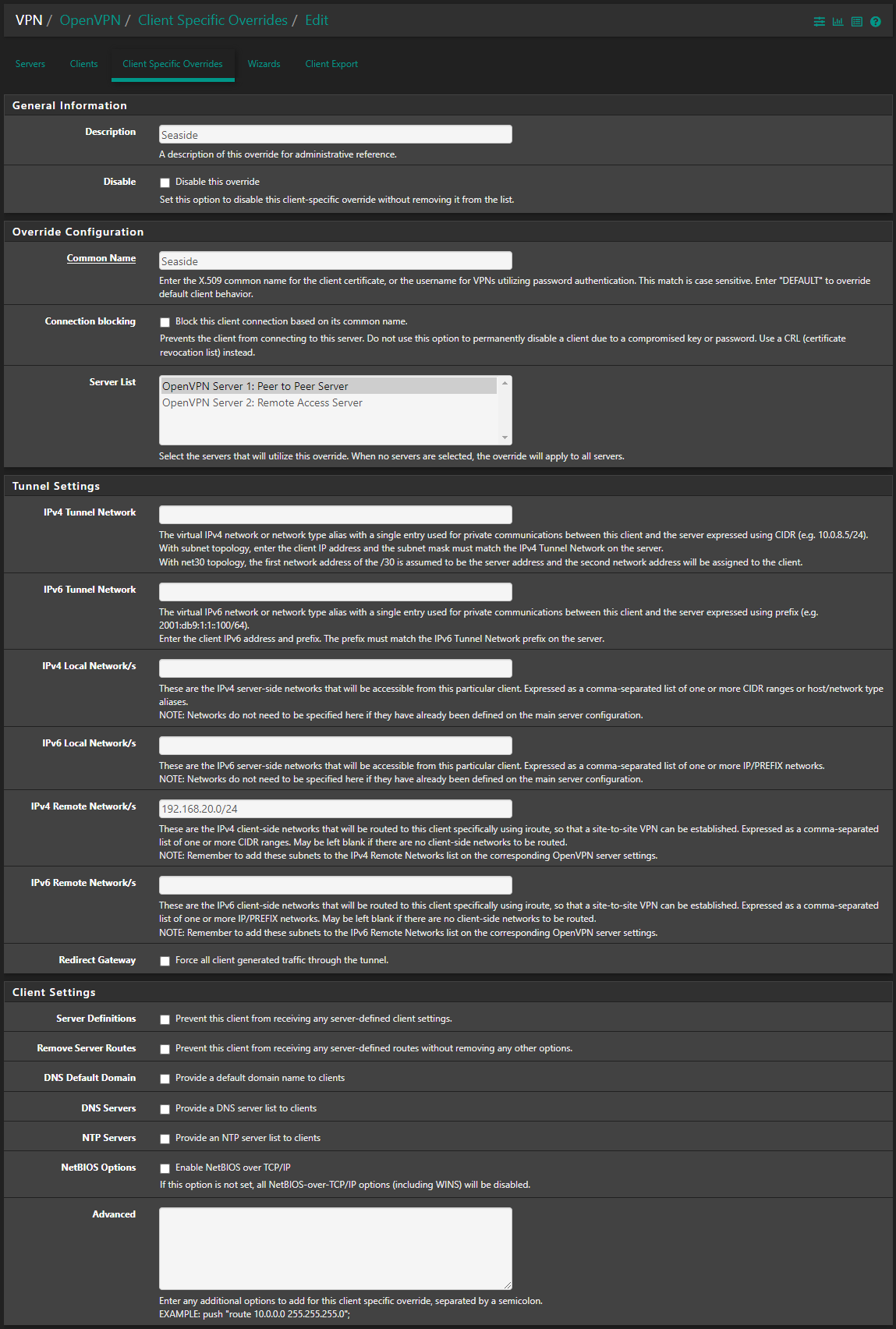
@vahidmoghadam On the client specific override, try explicitly assigning an IP, eg. 192.168.250.2/24
-
@vahidmoghadam we've struggled with something similar, so I will add this in case it helps - our iRoutes were specified in the client specific overrides advanced field rather than the tunnel settings. This was one issue for us in the 2.6 to 2.7 migration. The other was some change to the keys, so we reissued and reinstalled them.
Now we're getting a full swap space intermittently. This is prevented by stopping the S2S/P2P OpenVPN service (not our remote access OpenVPN service) before the shell and web configurator lock up. We'll be reinstalling from scratch over the weekend since our S2S isn't mission critical.
-
@spittlbm
My server's pfSense is fresh install of 2.7 but client's pfSense remain on 2.6.
I decided to install a fresh 2.7 on the my test device as client and retry to test site to site. I will share the results. -
@vahidmoghadam Hi, any news about this router problem ? I had the same problem since we upgrade the both pfsense to 2.7 a few months ago. To downgrade is complicate. My workaround was create an openvpn remote access and install OpenVPN Windows client at a workstations(server network) that need access the workstations at client network.
Regards
-
Unfortunately, I have not found any way to solve this problem. Even on a new machine, I installed the latest version of pfSense from scratch, but I still didn't succeed.
Even in an example, I connected two pfSense machines to the server as clients, both clients had full access to each other and the clients had full access to the server, but still the server did not have access to any of the clients.
It is a complex and strange problem that unfortunately. -
@vahidmoghadam Same here. I test some tracert
-
workstation at client network to workstation at server network = work fine
1 1 ms 1 ms <1 ms 192.168.148.5 -> pfsense client
2 26 ms 27 ms 27 ms 10.3.101.1 - tunnel
3 29 ms 28 ms 25 ms 192.168.140.20 - (workstation on server network) -
workstation at server network to workstation at server network = timeout
1 * * * Timeout
2 * * * Timeout
3 * * * Timeout -
pfsense server to workstation at client network = work fine
1 10.3.101.0 27.440 ms 28.003 ms 27.996 ms
2 192.168.148.20 23.889 ms 28.069 ms 27.972 ms (workstation on client network)
The problem is when pfsense server receive a request to client network ip, the pfsense don´t redirect to tunnel. But the request is at pfsense server, it know redirect to tunnel.
-
-
S ShaneDeak referenced this topic on
-
I have the same problem. In addition, I have a dual WAN setting. The pfSense sends the packets, which are actually intended for the client network, over WAN2 to the Internet.
The pfSense can reach all clients in the client network with the OpenVPN server.Has anyone already found a solution for this? If even a new installation doesn't help, I guess I have to go back to 2.6.
-
Did anyone try my suggestion? That was what fixed it for me when I had this issue before. All my other settings aligned with the guide here: https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html
-
After trying everything suggested I found a solution: there was a dual Wan setup that was only operating as a single. I didn't need it so fully removing the dual wan setup returned full function of the site to site connection.
-
-
@PauloPedrozo So did I, but I still had the same issue until I explicitly defined the IP in the tunnel network field on the client specific override (eg. 192.168.250.2/24 in the OP example)
-
@TTBruce said in in Site-to-Site OpenVPN can not access to the client LAN from Server:
Did anyone try my suggestion? That was what fixed it for me when I had this issue before. All my other settings aligned with the guide here: https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html
I tried, but unfortunately it did not work. I even swapped client and server. Now it is the client side (the one with dual WAN) that does not reach the server side.
-
Its the same problem in my case. Single WAN workts perfect but activating a dual wan setup breaks it. Its possible to ping all IP destinations from OpenVPN Client pfsense (the one with dual wan), but it its not possible in case of clients which are part of the remote network ip range.
-
@Rossi said in in Site-to-Site OpenVPN can not access to the client LAN from Server:
Its the same problem in my case. Single WAN workts perfect but activating a dual wan setup breaks it. Its possible to ping all IP destinations from OpenVPN Client pfsense (the one with dual wan), but it its not possible in case of clients which are part of the remote network ip range.
It actually works for me now. After swapping the client and server side, I made the following entry on the client side (the side with dual WAN):
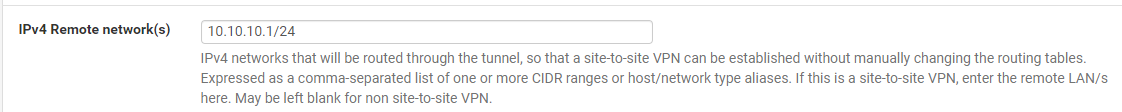
This is the network of the server side. But the instructions did not say that you have to enter this on the client side as well.
However, in the meantime, I also deleted the WAN gateway group and failover. So I don't know if the combination of both led to success.