newbie question - snort rule not applying ?
-
Hello all,
I am quite new with pfSense and Snort and I encounter some issues to understand how the things are working.
I have a bunch of traffic blocked and I can't figure out what is happening on snort side.
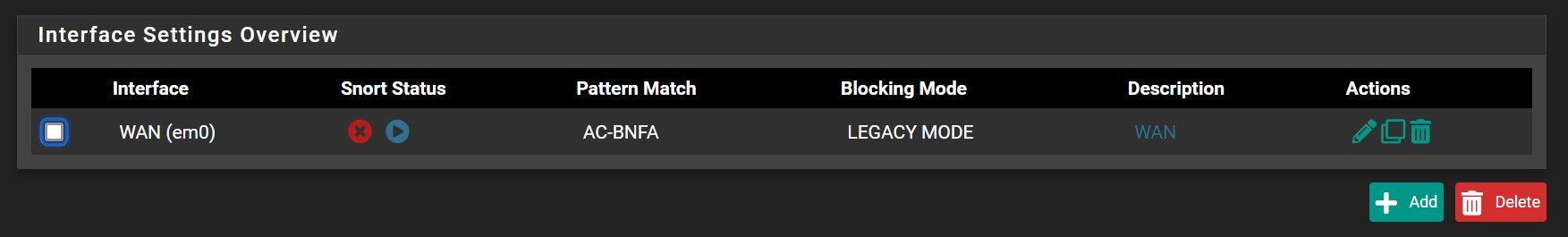
I have installed snort in Block Offenders and applied the "IPS Policy Selection - Balanced" on my WAN interface only.
Under WAN rules, I see that some rules enabled.
Right away, the Alerts list and Blocked list got populated. The strange thing is that my snort is not yet running/checking my WAN interface:
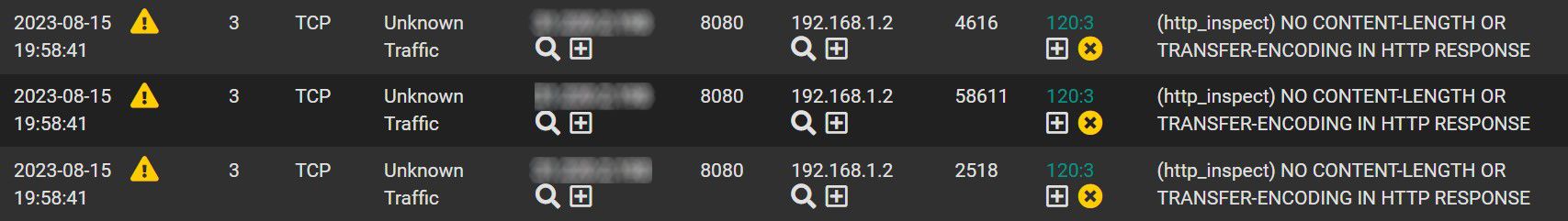
How is this possible?I also checked the Blocked list and I see a bunch of "(http_inspect) NO CONTENT-LENGTH OR TRANSFER-ENCODING IN HTTP RESPONSE". So to test I go in the Alerts list, click on the X under the list number to ignore this rule blocking.
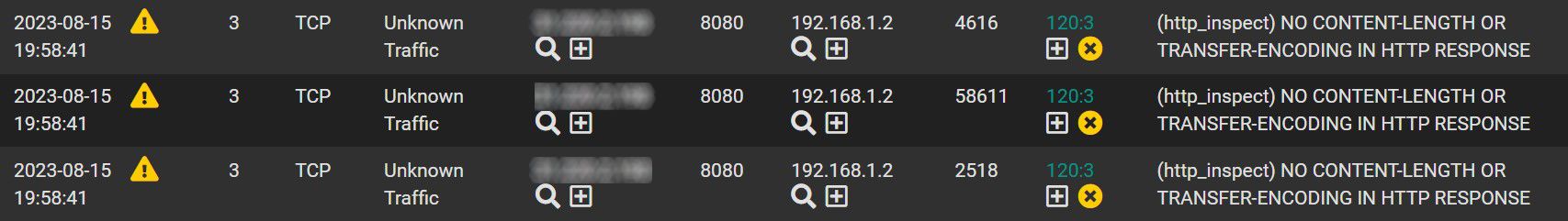
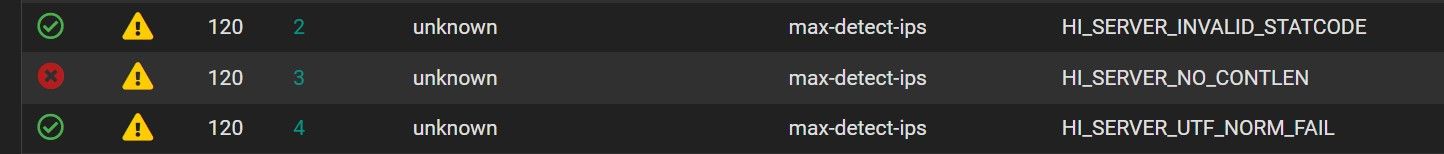
In the WAN rule under the interface, I clearly see that this list is correctly disabled:
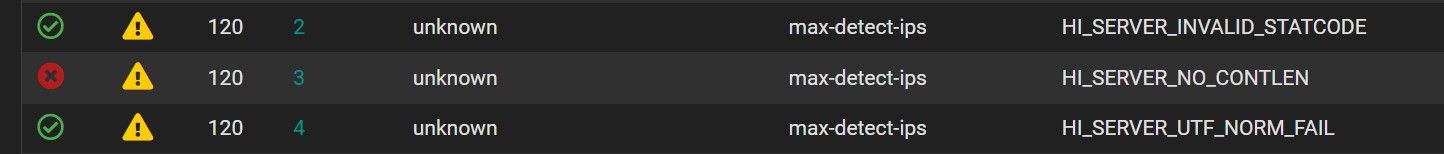
BUT in the blocked list I still see lines appearing even if it is disabled and cleared.
Is it the good way to "unlock" a rule or I totaly miss something essential?
Does a device restart is necessary to apply policy changes ?
Thanks
-
@bibou635 It's not impossible there is a zombie process running that is creating the blocks. It comes up from time to time here, but is unexpected. Unless 192.168.1.2 is your pfSense WAN, that would an address detected by an instance running on LAN.
If you run on WAN Snort runs outside the firewall so will scan all inbound packets even those that will be immediately dropped. If you run on LAN it will show the Dst IP as the LAN device IP.
Normally changes take effect upon a "live reload" (applying changes) or restarting the Snort interface.
-
Run this command from a shell prompt on the firewall. Get to this prompt either directly on the firewall console (if possible), or via a remote SSH session. From the console menu, choose "8" to drop to a shell session.
ps -ax | grep snortYou should not see any running Snort processes if Snort is actually stopped in the GUI. If you see a running process, note its Process ID (PID) and then run this command for each identified PID:
kill -9 <pid>Once any "zombie" processes are killed, you can return to the GUI and start Snort manually on the INTERFACES tab. Before restarting Snort, I suggest you visit the BLOCKS tab and click the Clear Blocked Hosts button to remove all the spurious blocks added by the errant process.
-
Thank you guys! There was I guess a zombie process. I have restarted and now all run as it should.
By the way, is the way to "ignore/not apply" a snort list the proper way to do ?
-
@bibou635 said in newbie question - snort rule not applying ?:
By the way, is the way to "ignore/not apply" a snort list the proper way to do ?
I'm not sure what you mean with your question. What specific list are you talking about?
-
Hi @bmeeks,
I mean what is the good way to remove a blocking list that is apply?
Is clicking on the X on the alert under the rule number (in this case 120:3) the correct way? or should I do something else to avoid this kind of traffic to be blocked?
-
@bibou635 said in newbie question - snort rule not applying ?:
Hi @bmeeks,
I mean what is the good way to remove a blocking list that is apply?
Is clicking on the X on the alert under the rule number (in this case 120:3) the correct way? or should I do something else to avoid this kind of traffic to be blocked?
The translation of your question into English is coming across a bit strange. The words used are not entirely correct, but I think I understand the goal of your question.
On the ALERTS tab Snort will show all of the triggered alerts. For each alert it will show some basic information such as the time the alert triggered, the Source and Destination IP addresses and ports of the traffic that triggered the rule, the Group and Signature ID (GID:SID) of the triggering rule, and some other information about the triggering rule.
There will be a red
Xicon next to the GID:SID displayed for each alert line. Clicking that icon will disable that particular rule from your inspection rule set based on its GID:SID. That means Snort will no longer load that rule into memory for use in matching against traffic. You can disable rules in three different ways as outlined below:- Clicking the red
Xon the ALERTS tab. - Going to the RULES tab, selecting the category that contains the rule in question, and then finding the rule in the list shown and clicking the red
Xthere to disable the rule. - Use the SID MGMT tab features to selectively disable that GID:SID. There are many options available on the SID MGMT tab. Looking through the example SID Managment conf files there will help as they contain commented examples of usage.
Later Edit: note that simply disabling a rule will NOT remove any existing traffic blocks. You will need to clear that host's IP address from the Blocked Hosts list on the BLOCKS tab. There is also an icon that will appear by the blocked IP address (Source or Destination) on the ALERTS tab. You can click that icon to remove the block as well. Disabling a rule and clearing a blocked host are not the same thing. Disabling a rule removes that rule from Snort's signature match list and no further alerts will come from the rule. But that will not remove any previously blocked host IPs from the BLOCKS tab. You must manually do that.
- Clicking the red
-
Hi @bmeeks !!
Thank you for the comment, I have a better understanding on how snort works on pfSense.
I could review a bit my traffic and I have my stuff to work perfectly now :)
Thanks for all your reply