Can't get SNORT to ignore an alert
-
I can't get SNORT to ignore an alert. It is baffling actually because in the signature area I have it disabled but it keeps flagging the wasabi.com website! Why? I don't know! I tried
I tried to white list the IP in the pass list (failed)
I tried to disable the signature: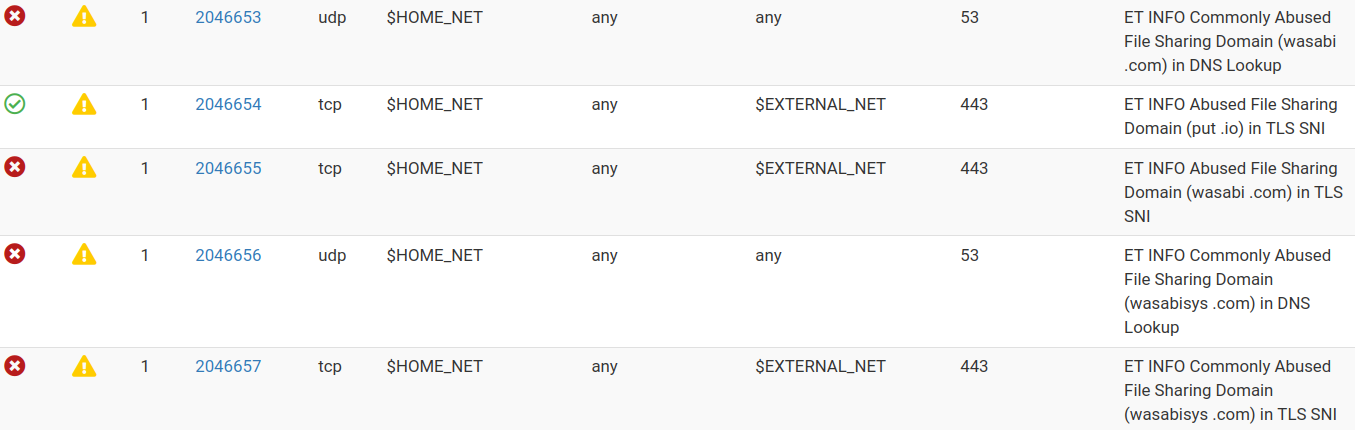
In the log, as seen below, it says it's forced to a disabled state but no dice.
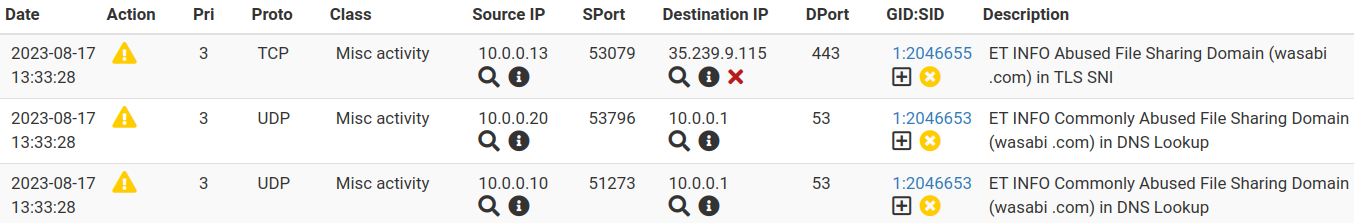
I've restarted the service. I haven't rebooted the firewall yet but maybe that's what I have to do next? I can't do it in the middle of my day.
Does anyone have any other ideas? I haven't tried to "reinstall" SNORT. It seems to be working just fine besides this little problem.
Thanks.
-
You most likely have multiple Snort instances running on the same interface. When that happens, only one of them will respond to GUI commands. The other becomes a sort of autonomous "zombie" process.
To see if that is the problem, run this command from a shell prompt on the firewall:
ps -ax | grep snortYou should see exactly one and only one Snort process per configured interface. If you see a duplicate, then you have a zombie process.
Return to the GUI and stop all running Snort processes using the icons on the INTERFACES tab in the Snort package.
Once those processes are stopped, return to the shell prompt and run the command above once more. If you still see running Snort processes, kill them using this command (where <pid> is the Process ID shown in the former shell command's output):
kill -9 <pid>Return to the GUI and start Snort on all interfaces normally.
Zombie processes are most often created by either using the Service Watchdog package with Snort (or Suricata), or an interface flapping on the firewall or some other external event causing pfSense to issue a rapid series of the "restart all packages" command.
If you have Service Watchdog installed and are using it to monitor Snort, then immediately remove Snort from the monitored processes. The IDS/IPS packages and Service Watchdog are NOT compatible with each other.
-
@wolfsden3
I'm having the same issue where the destination is a SIP PBX in the cloud. snort is running legacy mode / AC-BNFA on all interfaces. I have a firewall rule to allow all traffic from the PBX IP in question (both wan and lan interface), an entry in the snort configured pass list, and I've disabled the rules via the alerts that matched so far. Once I click the blocked tab - clear button, all is well but within a few seconds is caught up in the snort blocks again.The hypothesis from @bmeeks sounded relevant as I may be clearing too fast and causing zombies -- I haven't checked yet. Either way, I am concerned as well that snort doesn't seem to be honoring the pass list entry. I can verify that the firewall is allowing the traffic via the 'log traffic' option on the firewall rule, but I don't know of a way to verify or log that snort is letting traffic through via a pass list.
edit -- I'm running CE 2.7.2-RELEASE (amd64), snort version in package manager is 4.1.6_14, current snort ruleset
Snort Subscriber Ruleset a52c5cde8e58d3a47a68da206ef3deda Friday, 22-Dec-23 00:19:29 EST
Snort GPLv2 Community Rules 08d0e13ffededce6d45b948cf62edea3 Friday, 22-Dec-23 00:19:29 EST
Emerging Threats Open Rules 5a1efe26a0ff2cef8cfcac880c1d2f57 Friday, 22-Dec-23 00:19:30 EST
Snort OpenAppID Detectors c726cf937d84c651a20f2ac7c528384e Tuesday, 21-Nov-23 08:24:09 EST
Snort AppID Open Text Rules 2c26cb4f6a3bc03ab9c8e02befcf6fe1 Tuesday, 21-Nov-23 08:24:09 EST
Feodo Tracker Botnet C2 IP Rules a59559a8c2ed3641a288bf971631b919 Friday, 22-Dec-23 00:19:14 EST -
For giggles did you try to reinstall SNORT (making sure that the option one one of those screens says to keep your config on an uninstall).
I'm on 7.2 and after bumping to 7.2 I no longer have this problem.
Good luck!
-
@mkeys You probably have the same issue as us over on https://forum.netgate.com/topic/184858/suricata-blocking-ips-on-passlist-legacy-mode-blocking-both/27
Passlist is randomly not working and suricata blocks internal ip's and carp vip's on passlist.
-
@wolfsden3 have you inspected your surpass list and make sure you don’t have extra space or a mistake in that list. I had an issue with one doing this for AppID the surpass list had a half deleted rule i removed and it was causing issues for me until I deleted it and corrected the spaces. I kept having it block a app until I fixed it.