Taming Snort with Portscan detection on
-
I have Snort enabled on both my WAN interfaces.
Current settings are:
Protocol: All
Scan Type: All
Sensitivity: lowHowever when I browse the internet such as using Office 365 or play games the IPs of the sites are alerted to GID:SID 122:1 (portscan) TCP portscan and become blocked.
I have been filtering the alerts and suppressing legitimate traffic, however it currently seems like an endless stream of legitimate IPs become blocked.
Any suggestions?
Thanks.
-
Yes, turn off the Snort port scan preprocessor. It is not very useful in today's world in my view. As you have discovered, it will false positive frequently, and when you have Legacy Blocking enabled it will cause a ton of needless blocks.
You should also put Snort on your internal interfaces and not your WAN. There are three reasons for this.
- The way network traffic flows in FreeBSD and pfSense, Snort is seeing inbound traffic before any firewall rules have been applied. That means it is wasting CPU cycles and RAM scanning packets the default rules on the WAN firewall interface are going to drop anyway. So, having Snort block something that is already most likely going to blocked by the firewall is wasteful.
- Snort running on the WAN sees all local host outbound traffic after NAT rules have been applied, and traffic inbound destined for local hosts before NAT has been unwound. Therefore all your local hosts show up masked by the NAT public IP of the WAN unless you are not using NAT at all.
- You don't run Snort to protect the firewall. You run Snort to protect internal hosts. You can do that just fine and with the same level of security by running Snort on the LAN interface of the firewall. No traffic can come from nor go to internal hosts without passing through the Snort instance on the LAN.
I've shared these diagrams a lot on the forum. They show how network traffic flows when using either Snort or Suricata in the two available modes: Legacy Mode Blocking and Inline IPS Mode blocking.
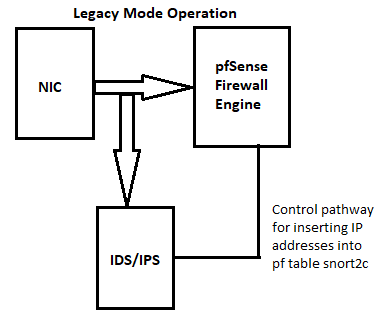
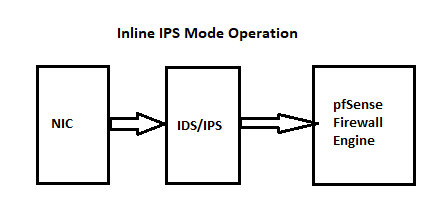
-
@AirGapped if you want to leave scanning on, set in preprocessors what block of IPs to ignore. Example being, I have one IP block set to ignore, it's the Roblox scans that occur when the game establishes connections. I would set that area if you wanted to run it. I run it have been for a number of years. Any scan that occurs gets blocked.
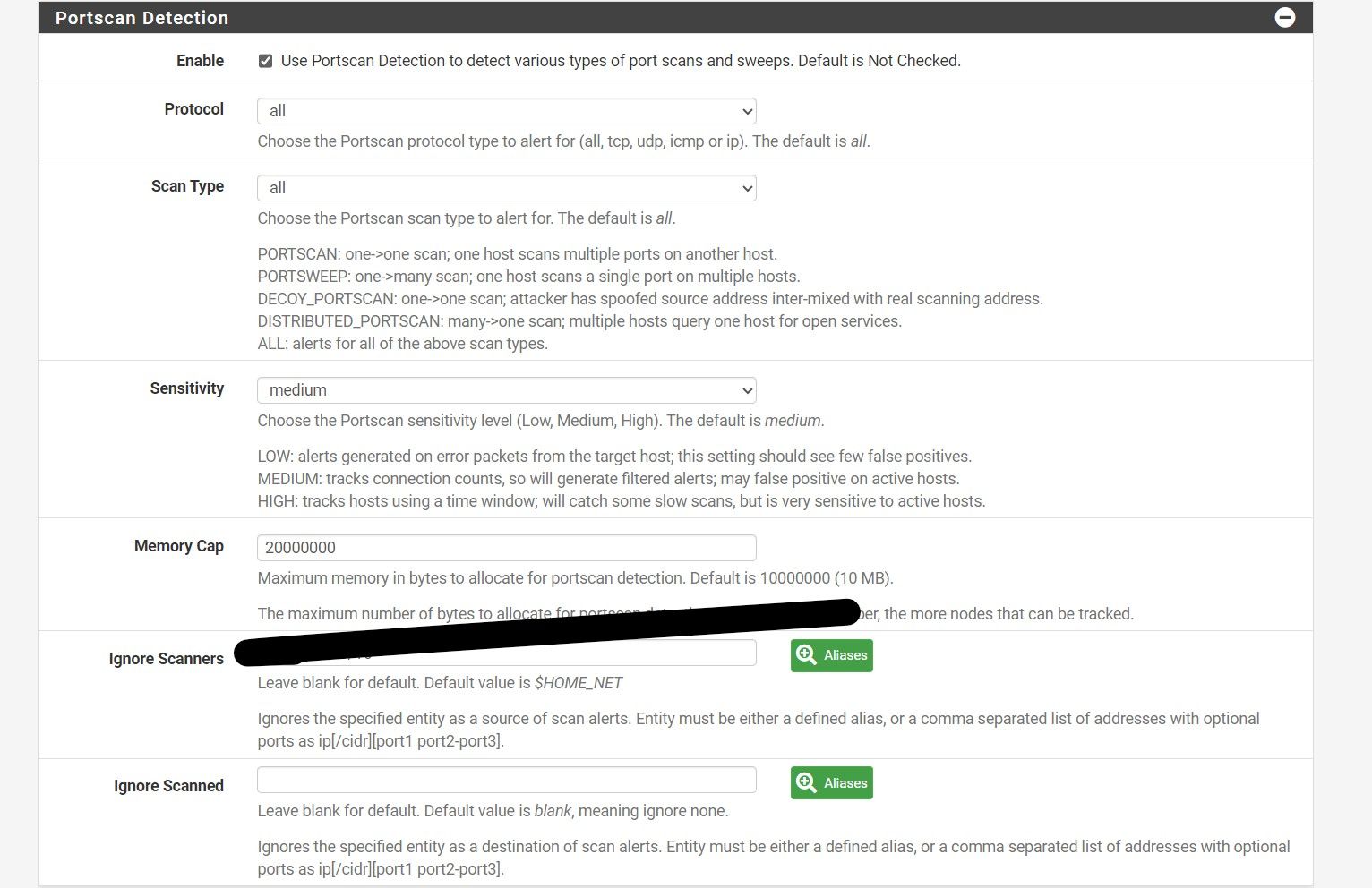
-
@bmeeks If I run Snort with the oink Code on my LAN will this cover my vlans as the Lan is set as the parent Interface?
-
@AirGapped said in Taming Snort with Portscan detection on:
@bmeeks If I run Snort with the oink Code on my LAN will this cover my vlans as the Lan is set as the parent Interface?
Yes, because the interace is placed in Promiscuous Mode when using Legacy Mode Blocking, running on the parent will also check all VLANs defined on that parent.