Blocking wanted inbound traffic - no rule
-
@cdsJerry said in Blocking wanted inbound traffic - no rule:
showing 0/0 in the firewall.
This would indicate the rule has never triggered. Might be helpful if you showed your wan rules, any floating rules?
And what exactly is being blocked - from the firewall log.
You sure your not just looking at old log entries, after you had deleted the rule that blocked it - that might explain why your not seeing anything in the popup.
-
@johnpoz Yes the 0/0 means the rule isn't being triggered. That was my point. The pass rule isn't being triggered but the IP IS failing, and pfsense isn't telling me what rule is failing it so how do I identify where the failure is coming from?
The log is failing IP 198.241.xxx.xxx that's being routed to my mail server's IP. It's actually failing several IPs from 198.241.xxx.xxx where the last two sets of xxx are different (but all legit and should pass).
I'm looking at the time stamp on the log file and it's after I set the pfblocker rule to disabled and reset the tables. It's reporting the blocks with newer timestamps. -
It just passed traffic from two IPs in the range. It still says the rule that triggered this action is: and then blank.. nothing. BUT it passed the traffic and I haven't made any changes since it was blocking that same traffic 20 minutes earlier. I'm confused. Why wasn't the alias allowing traffic to pass even with pfblocker was set to reject it (since the pass was the highest rule, but showing 0/0) and why did it continue to block traffic when pfblocker was disabled and the states tables reset? Any why is it now allowing that traffic 20 min. later when no other changes were made?
My alias that allows the traffic to pass now shows 1/326 and four emails have now come in from that sender.
-
@cdsJerry said in Blocking wanted inbound traffic - no rule:
and placed it at the top of the rules list, above floating rules
How do you do that.
-
@Bob-Dig
Just go to Firewall/Rules then click the floating tab in the top left corner. Click Add and create a rule based on the alias. Drag it to the top of the list then save and apply. Then restart states from the Diagnostics tab. -
@cdsJerry Do you know that pfBlocker will by default put its rules above any other rule every time it updates.
-
@Bob-Dig
Yes. I've had to move my alias back to the top several times as a result but since my alias was already at the top that's not the situation this time, besides, I had disabled the Asia rule that had been showing as the reason for the fail originally even though the manually created pass rule was above it. -
@cdsJerry said in Blocking wanted inbound traffic - no rule:
the manually created pass rule was above it.
I wouldn't count on that. Let pfBlocker place its rules on the WAN, not on Floating.
Or change the default rule order in pfBlocker. -
@Bob-Dig
I had to disable pfblocker in order to get the emails we need. It was only after I disabled it that we started getting emails. Disabling just the Asia rule didn't get the job done. It was still saying the IP was blocked by the Asia rule that we'd disabled. Only when we unchecked the enable box for pfBlocker did we start to get the email we need. Unfortunately we're now getting a pile of spam too.In the pfblocker settings I have the Floating Rules Enable box UNchecked. So that means these rules should be on the WAN interface rule set... but again, I had to turn off pfblocker to get the traffic to pass at all.
I turned pfblocker back on just now to see where they show up in the rules and they are on the WAN as expected. Asia isn't listed (remember it's disabled). pfblocker did move my manual pass down below it's rules again so I'll have to manually move my pass rules to the top again.Not sure how I can re-test to see if we're still getting the emails from Asia until later when someone sends us an email.
-
@cdsJerry said in Blocking wanted inbound traffic - no rule:
In the pfblocker settings I have the Floating Rules Enable box UNchecked. So that means these rules should be on the WAN interface rule set... but again, I had to turn off pfblocker to get the traffic to pass at all.
You have to "update" pfBlocker to apply any changes. The only thing that is applied immediately is the checkbox to disable pfBlocker.
-
@Bob-Dig
I always do the Save then Apply buttons. And if that doesn't work I also reboot it. And if that still doesn't work I post here for help. Sometimes we figure it out and sometimes we never figure it out.Since we got all those emails this morning after turning pfblocker off, we don't really expect to get more until tomorrow morning so I won't know our status until then. Currently the logs show no entries from that entire IP range.
-
@cdsJerry said in Blocking wanted inbound traffic - no rule:
I always do the Save then Apply buttons.
pfBlocker is not working like that!
-
After you save your changes you need to update pf blocker. Click the update tab at the top of pf blocker then hit run. This will update pf blocker with the changes you made immediately. If you dont Pf will make the update at its next cron schedule.
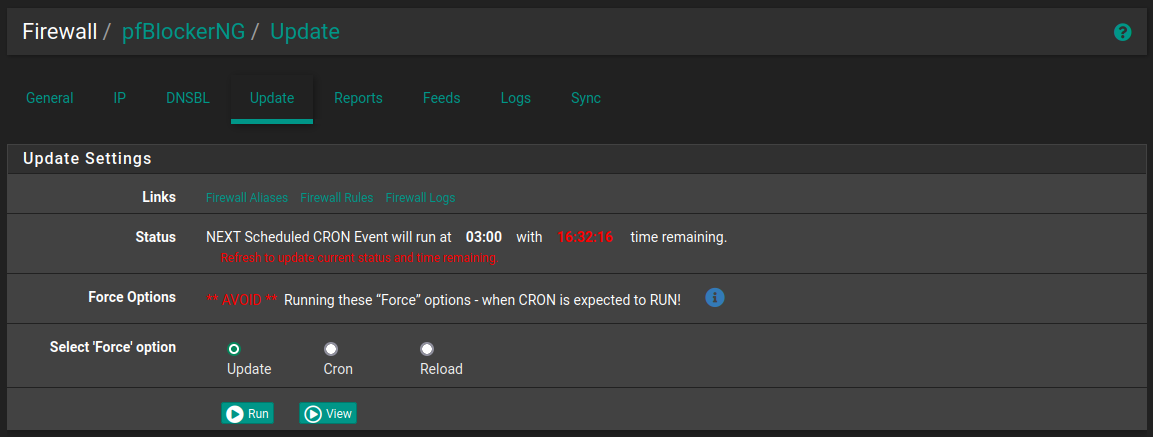
-
@Uglybrian
AH! You know, I'd never noticed that Update button there before. I most certainly was NOT clicking that so that would explain why it was still blocking Asia after I'd cleared the tab. It seems so inconsistent with the rest of the way pfsense operates. I certainly missed it. -
@cdsJerry It is, a bit, but under the hood pfBlocker downloads its feeds, and creates the alias tables, then generates the rules. If the feed isn't downloaded then there would be nothing to do.
If you want a little more control you can use pfBlocker aliases in your own rules. To do that without having pfBlocker generate rules, there is an Alias Native action choice that only creates an alias without any rules. (note that still doesn't download feeds or create the aliases, the pfB update does that)
-
@SteveITS
I think I'll leave it as it is. I don't want to make my firewall too customized because I'm not an expert at it and then it gets harder for someone to help me when I have problems. For example you know how long I was making changes to the rules and was super frustrated because they never worked? It was probably years before I learned that I have to reset the States tables before any blocks would take place if I was being attacked at the time I added the block. To me it seems like when you save a change it should change everything it needs to change for it to take effect, that the software should do it automatically. But.. .that's not how it works.PfSense is a super strong firewall if you want to spend all the time to learn it and then remember what you learned. But for a small business guy like me I have a lot of other things I need to be doing instead of learning complex details about a firewall. Especially since I won't change anything again for long periods of time and by then I'll have forgotten some of what I used to know.