OpenVPN Site to Site VPN broken TCP Sync issue.
-
@Bohodir
I'm using a VPN Server & Port , per site for my S2S setup.
It's setup with a /30 "connect net" ... "Makes magic happen" , as pfSense then knows it can't be a multisite , ie you can specify local & remote nets on the server (same for the remote client)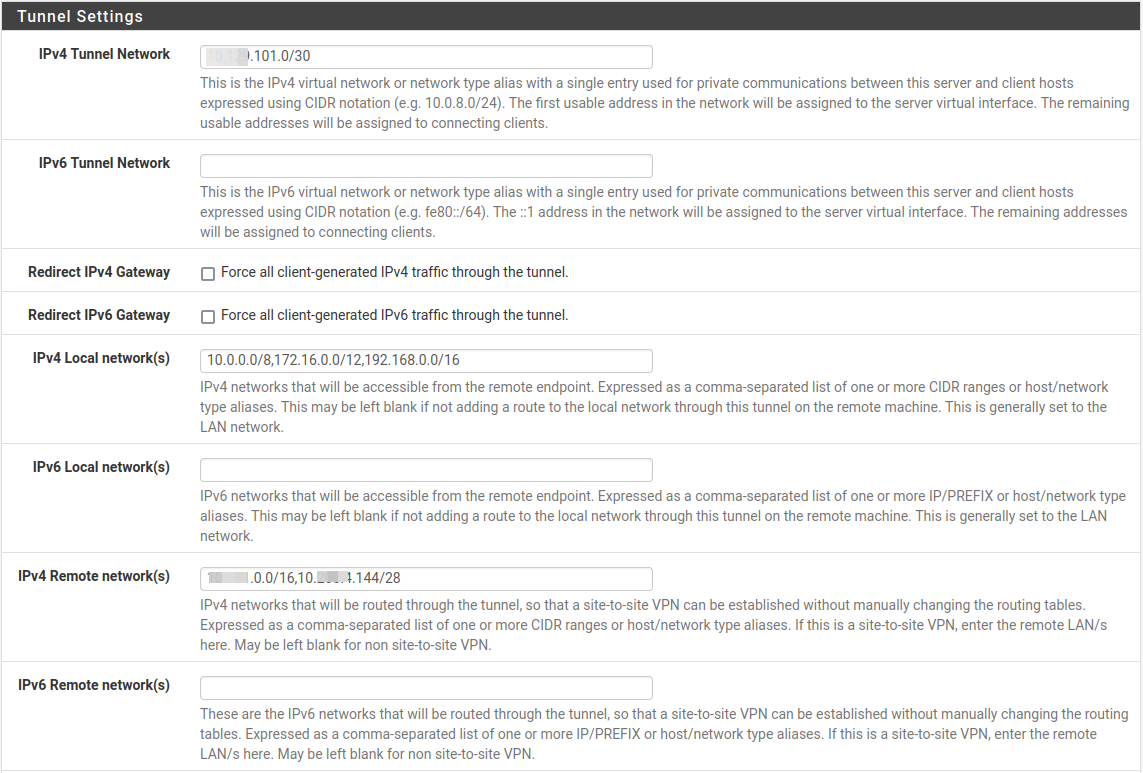
Initially the multi VPN Server was chosen for better performance. As i was hoping that the servers, then would be able to utilize more CPU's (as in multi tasks).
But i got the "/30 magic for free" too.My Roadwarrior (dialin) VPN is a single Server w. a /24 , same topology
Do NOT use the "NET /30 Topology" in the dropdown box, it will be obsolete soon
I have "Adjusted VPN MTU" to 1450 on S2S connections , and to 1400 on my (Dialin Server) , as i was bitten by the Citrix ICA Client not working wo. that.
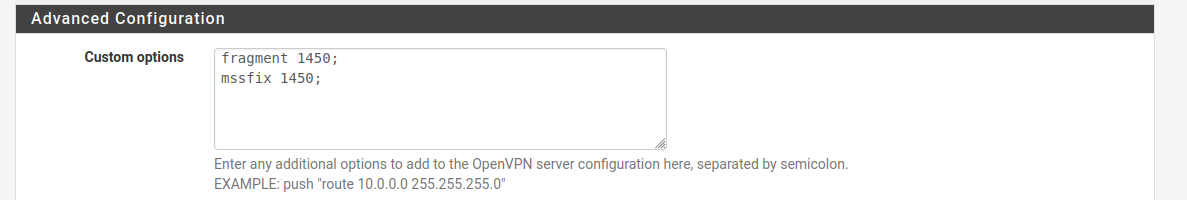
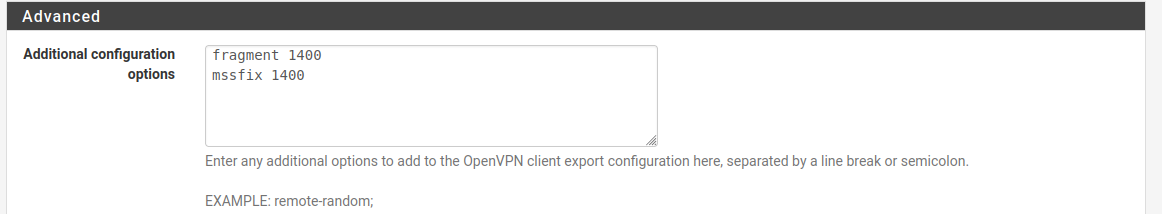
The MTU adjust settings has to be equal in both ends, ALSO on the roadwarrior (dialin clients) ... That was no fun to change all the settings for the "dialin cliens".
You can put the matching roadwarrior (dialin clients) settings in the client export settings here.
NB:
If changing/adjusting on a S2S Ovpn tunnel, that is also used to manage the remote Box.
Change the settings on the remote box first (you'll lose VPN), and then change them on the local (HQ) box after that (VPN will connect again).******** FW OVPN Rules**
My "OpenVPN" Firewall Rule tab is empty (the one shown is disabled)
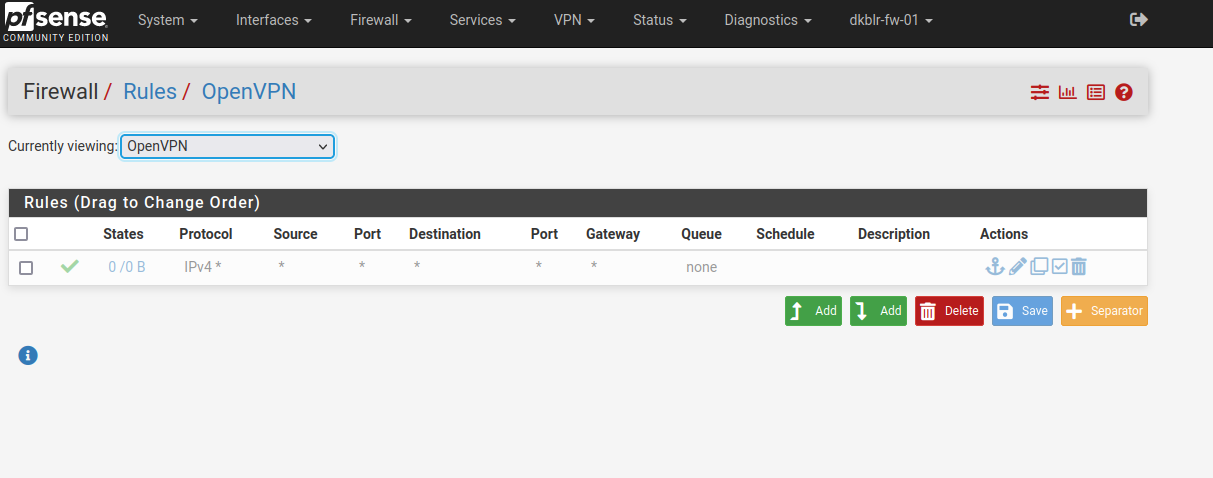
I have added my "Servers" on the interface assignent tab , and they're now treated as normal interfaces , where i can apply the rules.
/Bingo
-
@bingo600 Hey appreciate your provided settings information insights. I'm really having hard time after upgrades to 2.7. I'll test your way to setup I liked your approach.
Are you assigning OpenVPN interface on only Client side or you assigned OpenVPN server side also ?
Original OpenVPN interface rules has to be empty right ?Thanks man
-
@Bohodir
Yes - OVPN Rule must be empty , else that overrides the interface settings.I'm assigning ovpn interfaces on both client & server side.
IMHO Makes rules much easier to understand, as they are per instance. Instead of one big "mess" ...Edit:
Btw. I'm still running 2.6 on most sites , but did upgrade my "Test Fwall - Client " to 2.7 , and saw no issues with the S2S VPN.
The central (HQ) server is still running 2.6Edit2:
I'm using SSL/TLS Certs + TLS-Key for all my VPN's.
I generate all certs on the "HQ" box.
I have chosen one (the same) CA for all S2S , but separate (per site) Server/Client CertsFor Roadwarriors (dialin) , i have 3 Servers (different accesses , as in adm , trusted , untrusted" , each with own CA + own Srv + Client certs.
My dialin's have def-gw through the pfSense vpn tunnel , the S2S don't (they do local Inet exit)I use CSO on some of the dialin's to assign a specific IP , that ip can then be allowed/denyed in the fw interface rules.
Ie i can allow RDP, to selected users or other stuff./Bingo
-
@bingo600 Yea be cautious upgrading 2.7 on both Server and Client, because my settings working without any issues since I started using Pfsense 5 years ago.
I'll need your update if you decided to upgrade to 2.7 on your all nodes. Hope it will not break things.
Let me know how well it went, when you upgrade your all nodes.Thanks,
-
@bingo600 Hey you the man, I have resolved issue regarding your settings on MTU and MSS, appears to be these default values changed some how on newer version of OpenVPN, after exactly specifying MTU/MSS values as you defined it is working like a charm. My old setup working only changing these values.
As a appreciation for your help, I wanna send you starbucks gift card for coffee, send me your email man.
-
@Bohodir
I'm glad it worked for you
What "mss/fragment values" dud you have to use ???Thank you for the Starbucks offer, but we don't have many of these here in DK.
You could give my usefull posts a "Thumbs up" instead/Bingo
-
@bingo600 Hey sorry I was little busy over weekend. So your settings on custom options section fixed the issue:
fragment 1450;
mssfix 1450;After putting this it started working normal.
-
@Bohodir Hi,
It seems that I've a similar problem with my openvpn server.
I've a Client to Server OpenVPN active to allow my user connect on it and go outside through the VPN.But, since update in 2.7, it's not work.
I'm able to ping any services in internal networks through VPN but no TCP trafic is OK, just the ACK.
I can make searches on Google but unable to enter on any site.I try to fix fragment and mss to 1400 or 1450 but not work.
You only need to fix it in the server configuration or in the customer export configuration too ?Thanks a lot!
-
I have to put this settings on both ends. On my situation I have been using TLS/SSL method of server client.
You have to put these on custom field on both sides:
fragment 1450;
mssfix 1450;Thank you.
-
@Bohodir Hi,
Ok, I will try it on another Pfsense.
Now, I downgrade to 2.6 to avoid any problems with this update..., waiting netgate make actions to correct it...I use User Auth + TLS/SSL on my configuration
Thanks