New user Compromised pc - APT & keylogger
-
@johnpoz said in New user Compromised pc - APT & keylogger:
@smoses so mac address of what your router, that is a netgear mac address. 192.168.0.1 - most likely your netgear router.
also login.cgi is not a pfSense page.
-
@rcoleman-netgate said in New user Compromised pc - APT & keylogger:
also login.cgi is not a pfSense page.
Yeah brought that up in one of the other 3 posts with the same nonsense posted about this..
-
At this point I want you to do something for me: Take a photo of your router and post it here.
In your packet capture I see a number of things that could be in the middle and at aplay.
Zyxel
ASUSYour base IP range is 192.168.0.0
But your computer gets 192.168.1.0You have Netgear (not Netgate) hardware appearing and addresses related to that manufacturer in your posts.
Also a drawing of what is plugged in and how -- it doesn't have to perfect lines but it would need to be legible.
It seems to me as though you have many different pieces cobbled together and it is possible one of those is your root issue.
-
@rcoleman-netgate The double mac address is a mitm of another machine, that I made a windows reimage download usb drive on a "supposedly" clean machine which turned out to be the most infected. The other machine - as soon as I connected it to a different wifi, I received the Norton alert and I did the arp -a, showing duplicate mac addresses. I was not using anything to access my webcam. I used Norton VPN. I tried another VPN, same thing. It didn't make a difference. My cursor was moving also. They ARE MITMS. Back in the original network, there's a ton of CA network traffic and I'm causing data breaches. I'm not stupid. I wouldn't be posting anything on here if it weren't for the stupid derogatory comments which is typical in the IT field. I normally avoid it. I wouldn't post if I "had the language set wrong". They are my SSN hackers using my healthcare. I'm THE data breaches and gov has verified I am supplying tv shows and movies. I went to the FBI and spoke to two cybercrime agents in person, who also told me specific information and it's been correct.
My phones have been on our network over and over again. The pictures I'm forced to take of stalking, turned my USB drives into "rubber duckies" and my GOV accounts have been hacked with the librarian telling me and she took a picture.
Some credit rather than being talked down like I'm stupid, would be appreciated. Gov verified my searches are included and illegal surveillance of our house. Stores where my prescriptions are filled have told me, doctors have told me, yet - you're telling me it's "nonsense". I make perfect sense. My birth records are included with my entire family and I'm a business ID. My specific hackers and my PII IS a business ID. I CAN post the specific pictures. It'd be great to be asked that before the OH YEAH - SHOW US DUMMY. PROVE IT. YOU seem STUPID. I've also been told to not use this company as they are likely related to my hackers. The Marvel ARM 1U. That's me. Aries & Gemini lake, etc.
My healthcare pointed out "demotses" and that specific network traffic.
I appreciate the help. The actual help. It IS an AMD that IS the problem. I've used 5-7-8 different brands / manufacturers. The AMD IS the most problematic / infected. My Pentium hasn't been as infected as the AMD. Dell, HP, Asus, etc. I can also post the impostors of me and all the different locations of them also. and companies. I saved my conversations with Microsoft also. The AMD started conversations with Microsoft on it's own. As in the instant message Hub conversations - started on it's own. I sat and watched it. My parents, grandparents are Marvel characters, aunts, uncles, etc. I'd rather not give out my family tree without a lawyer. Other companies knew one, aunt MAY. The Embers MJ's - when it was open - is 15 minutes from me. -
@SteveITS - Thank you Steve. It's one of the names in our network traffic also. Perhaps not coincidentally.
-
@johnpoz The 192.168.0.1 was not a netgear router. I was at a coffee shop using wifi. As I said - a pc with a iso windows image that was done on the infected machine - that at that time was supposedly "safe".
-
@rcoleman-netgate no, it's not a pfsense page. Its on the infected machine on the infected network. Non-genuine or malware files on the the BIOS infected AMD machine. Part of the APT. Healthcare has told me our keystrokes are visible with my purchases. As in the encoded form that is in our network traffic, or somewhere else. That mac address was not pfsense, I was using a different and public wifi.
-
@rcoleman-netgate - I'm unable to find the upload image or attach image / file since my last posts. Was the icon disabled or moved or am I blind? Specific names are in our network traffic also.
-
@johnpoz LinkedIn CISSP professionals college professors teach duplicate mac's are MITM's. Go argue with them. I've verified it with them and other CISSP professionals including a RAT. Maybe the better question is what is proof to you johnpoz? Are you saying the CISSP's are wrong?
-
@johnpoz There should be a thumbs down button and after enough of them, that person is flagged as unhelpful, sarcastic, demeaning or similar.
-
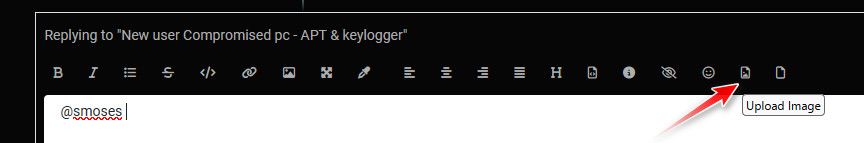
Yup maybe the Russian's are hiding in your machine - I mean that has to be the only logical answer.. <rolleyes>
BTW - omg, the Russians must be hacking me as well.. There is a duplicate mac on my network with a 169.254 address..
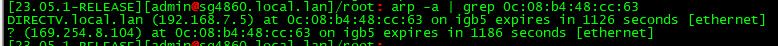
Oh shit - there is another duplicate
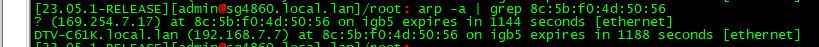
Oh my god, must be the china hackers and the germans, maybe candada is in on it too..
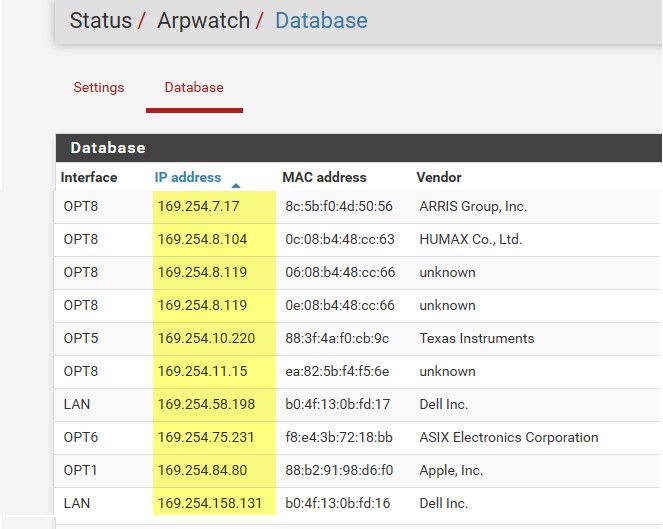
Maybe I should contact some CISSP college professors to explain it too me...
Or just maybe - its not RU hackers, and its how networking works when you have a device that likes to use APIPA (the link local 169.254 address space) as well as its normal IP.. No couldn't be that must be hackers doing MITM on my camera..
-
@smoses said in New user Compromised pc - APT & keylogger:
LinkedIn CISSP professionals college professors teach duplicate mac's are MITM's. Go argue with them. I've verified it with them and other CISSP professionals including a RAT. Maybe the better question is what is proof to you johnpoz? Are you saying the CISSP's are wrong?
????
That "MITM" must be on your LAN, if you see any MAC other than the nearest router. MAC addresses are valid on the local LAN only and discarded when a packet passes through a router and a new MAC from the next interface is used.
-
@johnpoz they have an Arp watch package now?? This could tie into the experimental layer 2 Ethernet filtering rules. Cool!!
-
@JonathanLee they have had arpwatch for quite sometime - not all that happy with it, it can cause a lot of noise with notifications.. have not been able to figure out a way to not have it put into the db 0.0.0.0..
But I will run it now and then for testing/play..
-
@johnpoz I wonder if that database can be used to help populate the experimental Ethernet filtering rules some way. That is a pain to enter by hand.
-
@smoses have you attempted to replace your AP your using? It might have an invasive container running on top of it. That is a big security issue right now. Unknown containers that can data marshal your NIC. Have you ever attempted to fingerprint the operating systems running with p0f?
But if you have someone using all your information that sounds like identity theft.
https://forum.netgate.com/topic/180467/23-05-source-os-p0f-fp-database-signatures-outdated/
Again the signatures are outdated but you can add approved ones manually and comparmentalize them with the fingerprints. It's really cool.
I really wish they would update the fingerprint database upstream for openBSD and even add AP's OS fingerprints that contain internal NAS systems. Flat out fix container issues once and for all. For example, Apple Airport Extreme APs have a Linux OS on them that helps run the NAS (time machine). This Time Machine product was an older Apple product with huge TB sized drives inside an AP. Again, an older version of SMB server message block was what was used to helped make this massive home all in one NAS (network attached storage) function. You could even access the NAS filesystem remotely off LAN with this type of AP. This was eventually recommended to be disabled because of a security concern within SMB ( disable the remote access). The issues were similar to the Eternalblue smb exploit, as the AP contained the same SMB issues. So yeah, I am thinking if your really having all of these issues and feel this unsafe, try to replace your AP. Give that a shot.
I had a bug once everyones recommendations at Microsoft support were just reinstall. Again, if I did that the meat/heart of the problem would never have been resolved ever. They eventually patched it for everyone.
Proof is needed. I recommend Wireshark, Wireshark, Wireshark logs. Hard evidence is what is needed. You can also run Airsnort and check traffic on the wifi side too. Do you have the Norton alert screen shot?
I hope your ok. If you are overwhelmed you can always ask for help. I hope this community makes you feel safer. It's ok, we will get the bad guys. You're in good hands.
-
Side Note:
Yes stuff can get super complicated and complex inside something the size of a nickel.
"Straddling bipartite monoalphabetic substitution superenciphered by modified double transposition."
https://shilongcrypto.blogspot.com/2016/11/the-soviet-spy-hand-cipher-that.html?m=1
-
Throw out the hard drive and start over.
-
@provels but hey it's got a cool puzzle inside it to fix still. If it's thrown out it will just pop up somewhere else and have a new victim.
https://www.rosevilletoday.com/news/foreign-hackers-target-home-and-office-routers/
A home office router bug has occured in the past in some locations. Leading to the default solution when say the government does start to discover the main threat or issue, is that everything is always timed just right with a math equation so that all the sudden it's "upgrade time" and bingo now it's time to a new system. Like say a fiber optic network. Or, to use that and say we disconnected that old equipment force the upgrades. Leading to that issue occurs again inside all new equipment that again is made in another country with different data sovernity and laws again. After, that has been resolved with what I have coined as "the consumer replacement upgrade mitigation platform" it becomes a throw the bug under the bus replacement plan again with statements like, "that issue was the old equipment, so its time to update!!" This results in tons of e-waste and tons of excuses for who's to blame. A couple months later it's back to the hacked devices as usual and the government it's back to catch up and new training as usual. Or the other solution now is they just silo the guys that find the bugs with a shiney new all in one equipment plan and tell them they can't use their own routers. That way it's harder to catch those invasive actors. Hey, we are all to blame we want that latest greatest product. What this needs programing professionals that can stomp out issues with compliance servers firewalls and code we can trust built with communities. Open source is a good solution, it's starting to get closer to were we are one step ahead of the invasive actors.