Solved - Firewall WAN - Blocking packets destined for a "working OpenVPN"
-
I just had a weird one ....
I have a fully working OpenVPN L2L tunnel between our home & the summerhouse.
I have been xferring tonzz of data wo issues on that tunnel.This weekend i set up an Outside Camera in the summerhouse , and it was working fine in the summerhouse , using VLC and rtsp://xxxxxxx
When i came home i wanted to see the stream, but VLC showed "black screen" (No errors).
I was checking the firewall for any blocks, there were none.
Then i noticed my home WAN-IF.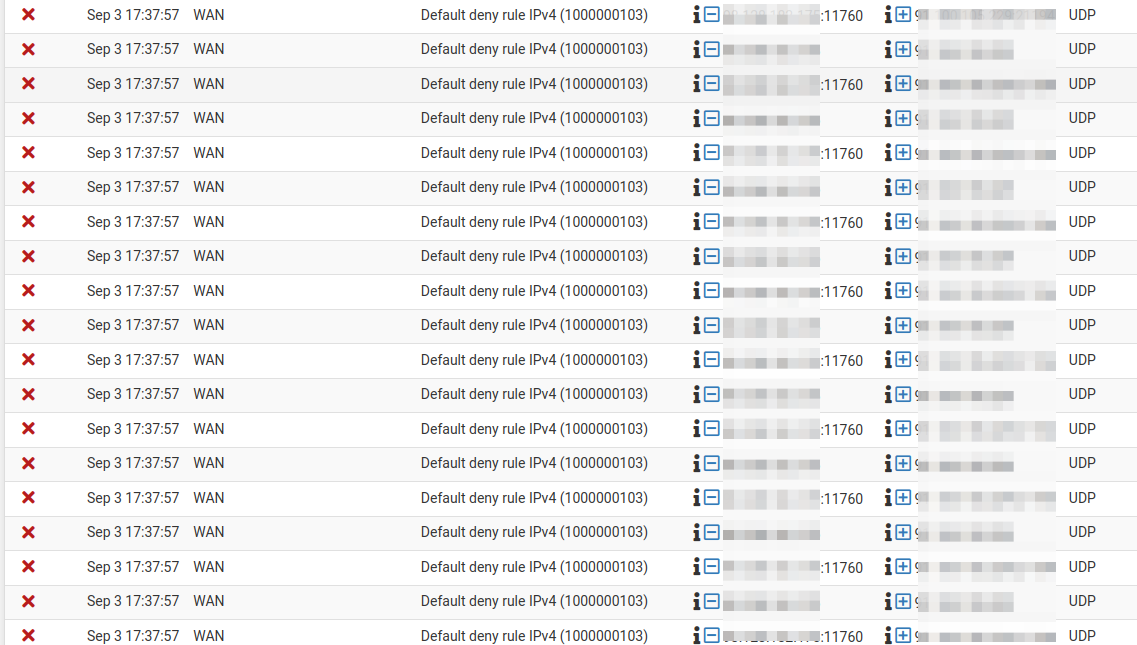
I had tonzz of deny's on my home wan interface , source = summerhouse ip , dest = home ip , some just showing udp , others showing summerhouse ip (source) + source port + udp & dest = home ip + (ovenvpn port) + udp ????.
When i stopped the VLC stream , the WAN deny's stopped too.
Despite the "kazillion" WAN Deny's , My OpenVPN tunnel was still working fine for ie. managing the pfSense or ssh to a linux in the summerhouse.
I had a "suspicion" : It might be MTU
I have previously discovered that my home link doesn't like full 1500 byte packets.So i did a packet trace on "home wan" , and some of the packets were reported as "too big" , which (for me) actually was kind of expected...
I added this to both ends of my openvpn L2L ... You'd better do it on the remote end first , as they have to match.
fragment 1400 mssfix 1400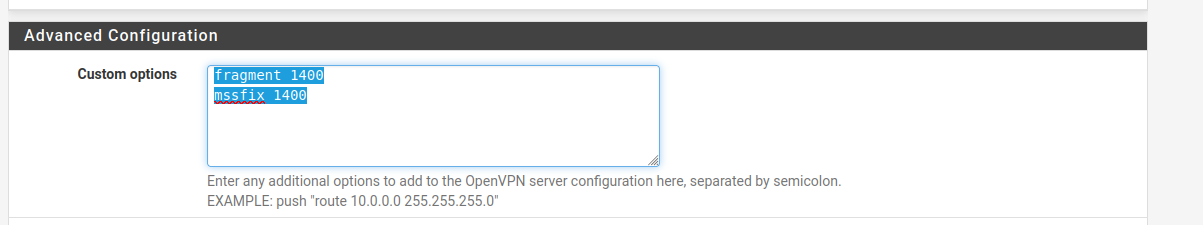
Now the WAN deny's were gone , and i could see the video stream.
Only two things makes my "head scratch" ...
1:
Why were the large packets shown as deny on the WAN ?2:
Why could my packet trace show that the packet was too big (if it is my ISP) that doesn't like 1500 byte packets. ... aka why weren't they dropped further out.Unfortunately i lost the packet trace due to an issue w. my PC.
Lesson Learned here : If you see deny's on WAN even if there is a 100% clear rule allowing the data ... It could be MTU related.
Edit: I just noted this on my home Wan IF
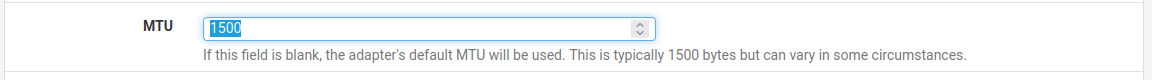
It's not on my summerhouse IF ....
I might have had a "brainfart" at some time ..... and put it there, but it shouldn't really matter (default) , and i doubt my ISP's switch runs jumbo.Will
consider toremove the newly added stuff on the openVPN server/client
I had to test .... Same WAN Deny's , and no video stream if i remove the 1500byte MUT on WAN , and the 1400byte "openVPN" mtu stuf.
I have now reapplied the openVPN fix ... Aaannnd i have picture.Edit: The 1400 MSS size for openVPN, was selected "emperically" ... Could prob be higher ....
/Bingo
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on