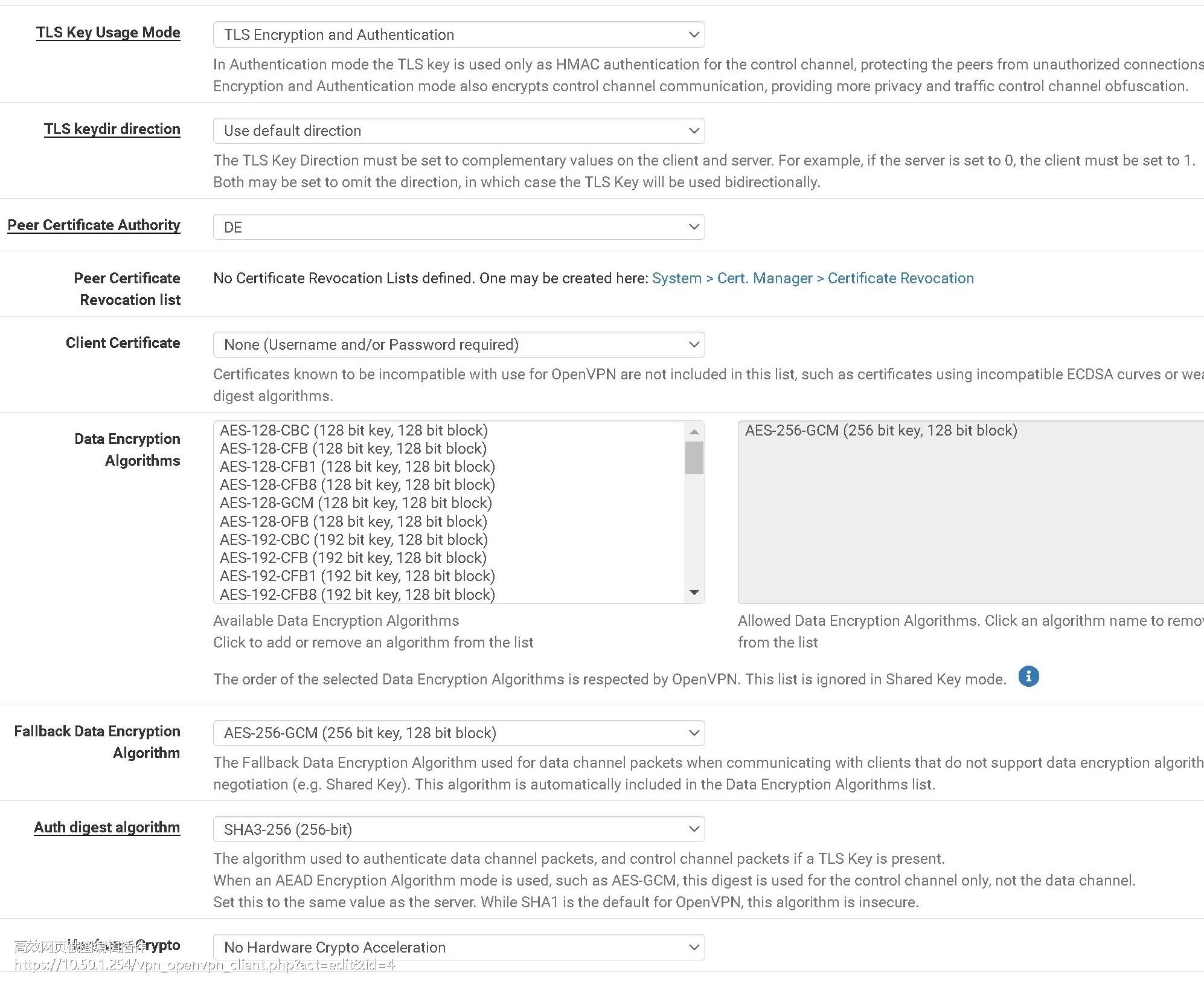
openvpn ED cert
-
-
That set of curves is treated differently in OpenSSL than others so it's not surprising that it isn't working.
It isn't in
openssl ecparam -list_curvesand it isn't returned by the PHP functionopenssl_get_curve_names(). Nor does it show in the list of non-EC digest or cipher algorithms in OpenSSL. If it's not listed as a supported in OpenSSL, or if it's one we have flagged as weak, then certificates using that method of signing are hidden.The drop-down list has to validate certificate hashes and curves now because OpenSSL 3.0 will fail if you choose the wrong one (e.g. one signed by SHA1)
So while it may have functioned in the past by sheer luck, we have to be more careful now.
I'm not sure what all work needs to be done to officially add support for
X25519andX448in certificate handling, but we can certainly look into that. We may be limited by what is possible in the PHP OpenSSL module there, though.EDIT: I added a feature request for this: https://redmine.pfsense.org/issues/14762
-
The previous Pfsense 23.05 version was working, and after I upgraded from the previous version, openvpn is using the ED22519 certificate, but the pfsense 23.09 version now does not display the ED certificate in the openvpn list.
-
I get that, and I explained why in my reply.
We cannot pass on certificates we can't specifically identify as being good to use with OpenVPN, otherwise we risk users causing OpenVPN to fail in various ways.
Before this was not filtered or validated so you could do whatever you wanted there.
So it worked but only be accident. It was never supposed to be supported, you were lucky it worked at all.
You could manually edit and disable some of that validation, but you are better off using a supported certificate.
-
ED22519 and ED448 supported by openvpn and php. Because I have tested and used it. And Openvpn recommends using ed certificate. so openvpn EasyRSA tool support ED cert. Including SSH have been converted to use ED certificate. So it is widely accepted certificate
-
I didn't say it wasn't supported there.
I'm saying it's not supported on pfSense software or in the OpenSSL module for PHP.
We won't be disabling the validation that protects users from using invalid certificates, but without support for those algorithms in the PHP OpenSSL module, we can't tell they are valid for use.
So your choices are to either use a certificate that is supported fully, or to manually edit the PHP and disable the validation.
-
@jimp said in openvpn ED cert:
OpenVPN
https://forums.openvpn.net/viewtopic.php?t=29734
https://github.com/OpenVPN/openvpn/commit/a177388735566c3d7c3120860ceea71b81db5c34
https://www.eduvpn.org/openvpn-and-modern-crypto-part-ii/
https://github.com/OpenVPN/easy-rsa/issues/488
https://github.com/OpenVPN/easy-rsa/releases
EasyRSA 3.0.8
3.0.8 (2020-09-09)Provide --version option (#372)
Version information now within generated certificates like on *nix
Fixed issue where gen-dh overwrote existing files without warning (#373)
Fixed issue with ED/EC certificates were still signed by RSA (#374)
Added support for export-p8 (#339)
Clarified error message (#384)
2->3 upgrade now errors and prints message when vars isn't found (#377)
Update OpenSSL Windows binaries to 1.1.1g
Reverted OpenSSL back to 1.1.0jED certificates have been widely supported and validated for many years now.
-
-
@yon-0 I do realize this topic is a bit old, but I wanted to contribute a solution for overriding the local check for compatible certificate curves. I was led to this forum post, as I was doing my own research while working with another individual on importing a client certificate that uses the ED25519 curve.
 ️ PLEASE NOTE
️ PLEASE NOTE  ️ that I am not a developer, but am comfortable reading, writing, and modifying scripts. There are likely much better ways of doing this, but this was being done on a pfSense firewall in a lab environment. YOU are responsible for any issues that arise from making these changes.
️ that I am not a developer, but am comfortable reading, writing, and modifying scripts. There are likely much better ways of doing this, but this was being done on a pfSense firewall in a lab environment. YOU are responsible for any issues that arise from making these changes.I did try adding
ed25519to theOpenVPNarray of compatible curves:'OpenVPN' => array('prime256v1', 'secp384r1', 'secp521r1'),But realized that this wouldn't work, because that curve is not in the
openssl_get_curve_names()orcert_get_pkey_curve()output, so any comparisons against this array will will fail.
Below is the solution that I came up with in the limited time I had:SSH into your firewall and choose
8) Shellat the menunano /etc/inc/certs.incBefore
2568 return (($curve === false) || 2569 !array_key_exists($consumer, $cert_curve_compatible) || 2570 in_array($curve, $cert_curve_compatible[$consumer])); 2571 }After
2568 return true; 2569 /* return (($curve === false) || 2570 !array_key_exists($consumer, $cert_curve_compatible) || 2571 in_array($curve, $cert_curve_compatible[$consumer])); */ 2572 }Exit the shell and choose
16) Restart PHP-FPMand you should be able to select your certificate(s). -
@0xBEN said in openvpn ED cert:
@yon-0 I do realize this topic is a bit old, but I wanted to contribute a solution for overriding the local check for compatible certificate curves. I was led to this forum post, as I was doing my own research while working with another individual on importing a client certificate that uses the ED25519 curve.
 ️ PLEASE NOTE
️ PLEASE NOTE  ️ that I am not a developer, but am comfortable reading, writing, and modifying scripts. There are likely much better ways of doing this, but this was being done on a pfSense firewall in a lab environment. YOU are responsible for any issues that arise from making these changes.
️ that I am not a developer, but am comfortable reading, writing, and modifying scripts. There are likely much better ways of doing this, but this was being done on a pfSense firewall in a lab environment. YOU are responsible for any issues that arise from making these changes.I did try adding
ed25519to theOpenVPNarray of compatible curves:'OpenVPN' => array('prime256v1', 'secp384r1', 'secp521r1'),But realized that this wouldn't work, because that curve is not in the
openssl_get_curve_names()orcert_get_pkey_curve()output, so any comparisons against this array will will fail.
Below is the solution that I came up with in the limited time I had:SSH into your firewall and choose
8) Shellat the menunano /etc/inc/certs.incBefore
2568 return (($curve === false) || 2569 !array_key_exists($consumer, $cert_curve_compatible) || 2570 in_array($curve, $cert_curve_compatible[$consumer])); 2571 }After
2568 return true; 2569 /* return (($curve === false) || 2570 !array_key_exists($consumer, $cert_curve_compatible) || 2571 in_array($curve, $cert_curve_compatible[$consumer])); */ 2572 }Exit the shell and choose
16) Restart PHP-FPMand you should be able to select your certificate(s).Yes, I also deleted these codes and used them on OPENVPN. But now I still need to manage it in system_certmanager.php. https://redmine.pfsense.org/issues/15787
I think PF needs to keep up with new technologies and needs in some aspects, but they are regressing and putting too many restrictions.
Maybe it has something to do with culture, we like innovation and meeting needs. -
Hello,
i ran into this issue quite a while ago. Last time i tried to use ec25519 certs i went to the official doku pages.
They are referencing to a list of compatible / accepted algorithm but unfortunately forget to put a link to this list into the dokumentation.
Certificate Properties -> curve name.Does somebody know were to find this reference?
Thank you very much.