Firewall Rules / VLANs / Synology NAS
-
@Bob-Dig said in Firewall Rules / VLANs / Synology NAS:
@stevencavanagh And you want to access something from a device behind your dd-wrt router?
I would like to be able to access the NAS when connected wirelessly to the FLASHROUTER ideally, rather than having to change LAN networks in order to access it, assuming it is relatively easy to do!
-
@stevencavanagh said in Firewall Rules / VLANs / Synology NAS:
I assume it is natting traffic behind it but I didn't set it up
Yeah that is a valid assumption, since pretty much every wifi router on the planet defaults to doing nat. So either setup port forwarding, on the dd-wrt device for traffic that hits is wan IP 192.168.30.x -- or turn it into just a router, ie disable nat.. And then allow the traffic you want on it. But then you would need to setup routing on pfsense for it know how to get to the 192.168.11 network.
The simpler solution is to just use it as a AP vs a router or nat router.
Any wifi router can be used as just an AP.. Turn off its dhcp server, and connect it to your network via one of its lan ports vs its wan interface. And of course set its LAN ip to be on this network 192.168.30 so you can access it to manage its wifi settings, etc.
dd-wrt allows for setup of a gateway on the lan IP, so you wouldn't have to do source natting to get to the dd-wrt web gui to admin from a different network If you don't setup a gateway on it, you wouldn't be able to access its web gui from another network unless you tell pfsense to source nat the traffic so say coming from your lan network to its 192.168.30.x address it looks like its coming from pfsense 192.168.30.1 address. This would be a outbound nat you setup on the flashrouter interface in pfsense.
-
@johnpoz said in Firewall Rules / VLANs / Synology NAS:
@stevencavanagh said in Firewall Rules / VLANs / Synology NAS:
I assume it is natting traffic behind it but I didn't set it up
Yeah that is a valid assumption, since pretty much every wifi router on the planet defaults to doing nat. So either setup port forwarding, on the dd-wrt device for traffic that hits is wan IP 192.168.30.x -- or turn it into just a router, ie disable nat.. And then allow the traffic you want on it. But then you would need to setup routing on pfsense for it know how to get to the 192.168.11 network.
The simpler solution is to just use it as a AP vs a router or nat router.
Any wifi router can be used as just an AP.. Turn off its dhcp server, and connect it to your network via one of its lan ports vs its wan interface. And of course set its LAN ip to be on this network 192.168.30 so you can access it to manage its wifi settings, etc.
dd-wrt allows for setup of a gateway on the lan IP, so you wouldn't have to do source natting to get to the dd-wrt web gui to admin from a different network If you don't setup a gateway on it, you wouldn't be able to access its web gui from another network unless you tell pfsense to source nat the traffic so say coming from your lan network to its 192.168.30.x address it looks like its coming from pfsense 192.168.30.1 address. This would be a outbound nat you setup on the flashrouter interface in pfsense.
Didn't want to mess with the FLashrouter configuration as it under a support contract currently so if it has to be modified then I'll have to live with it for now!
However, as a more general question, if I required access to the Synology NAS from a VLAN (ignore flashrouter, just a straightforward VLAN, say HIVE) I assume I would create a rule on the HIVE interface to allow any traffic to SERVERS and exclude all other VLANS??
Such as...
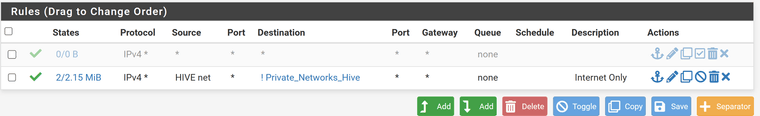

Would I need a rule coming the other way, I believe normally you wouldn't
-
@stevencavanagh said in Firewall Rules / VLANs / Synology NAS:
Would I need a rule coming the other way, I believe normally you wouldn't
No return would be allowed by the state the firewall creates.
Traffic is evaluated as it hits pfsense interface, from the interface the device is connected too. If you have A and B interfaces and you want a device on A to talk to B or not to talk to B those rules would be on the A interface.
What rules you have on B would not matter, you could have zero rules on B, and A could talk to B, the return traffic from the device on B would be allowed by the state pfsense creates when it allowed the traffic.
-
@johnpoz said in Firewall Rules / VLANs / Synology NAS:
@stevencavanagh said in Firewall Rules / VLANs / Synology NAS:
Would I need a rule coming the other way, I believe normally you wouldn't
No return would be allowed by the state the firewall creates.
Traffic is evaluated as it hits pfsense interface, from the interface the device is connected too. If you have A and B interfaces and you want a device on A to talk to B or not to talk to B those rules would be on the A interface.
What rules you have on B would not matter, you could have zero rules on B, and A could talk to B, the return traffic from the device on B would be allowed by the state pfsense creates when it allowed the traffic.
So, if I understand correctly, the rule shown above would allow a device on the HIVE VLAN to talk to any device on the SERVERS VLAN (including the NAS) and therefore I would be able to log on to the NAS but I would not be able to communicate with any devices connected to the 4 VLANs under "Private_Networks_Hive"
-
@stevencavanagh yeah if that rule is on your hive interface.. Personally not a fan of ! rules... I would write very easy to read explicit rules that are easy to understand with a simple glance at them.
But yeah such rules can work, I just wouldn't do it that way personally.
-
@johnpoz said in Firewall Rules / VLANs / Synology NAS:
@stevencavanagh yeah if that rule is on your hive interface.. Personally not a fan of ! rules... I would write very easy to read explicit rules that are easy to understand with a simple glance at them.
But yeah such rules can work, I just wouldn't do it that way personally.
Must admit I would do it the same way as you but I was following a guide on it and they did it that way for some reason. So, I would simply be better having a Pass rule with source HIVE and destination SERVERS, as simple as that!
-
@stevencavanagh said in Firewall Rules / VLANs / Synology NAS:
a Pass rule with source HIVE and destination SERVERS, as simple as that!
Pretty much.. But you could get way more restrictive.. Good security practice is least privilege, if what you need it access 192.168.1.42 on port 445 that is what should be allowed nothing more. Allowing all access to 192.168.1.42 is not least privilege, allowing all 192.168.1.0/24 is for sure not least privilege.
If your running some webserver on server X, then you should allow 443 to server X IP.. nothing more.. etc.. or 80/443 if both http and https, etc.
-
@johnpoz Yep, will restrict it once it is up and working. The NAS is on a static IP so will restrict to that but not sure at the moment which ports it uses to communicate.
-
@johnpoz I tried to tighten up the rules for the IP Cameras. Would these rules seem reasonable, I know I still have the ! bit and will sort that later but the rest?
There are cameras attached to a NVR and a standalone camera, both require 587 to send emails and I opened 123 for NTP.
Have I missed anything else?