Rule to block internet access for alias devices still goes through for ipv6
-
It seems my ISP had enabled ipv6 and now the following rule I had set up to prevent certain devices from accessing the internet is no longer blocking all internet access. Websites which are using ipv4 are still blocked as usual but ipv6 websites such as www.yahoo.com is allow through.
Under Firewall/Aliases: New IP Alias "Cameras" For each camera, enter IP and a description. Under Firewall/Rules - / Lan: Action: Reject Interface: LAN Address Family: IPv4+IPv6 Protocol: TCP/UDP Source: Single host or alias / Cameras apply the pfsense rules, then reboot the cameras, or flush the states in PFSenseOn my Windows 11 computer I could go into the network adapter settings and uncheck 'Internet Protocol Version 6 (TCP/IPv6)' and this would solve the issue. But how do I do this from pfSense so that devices such as camera are also blocked from accessing the internet? I believe disabling ipv6 in pfsense may create the desired effect but is there a better way?
-
Cameras are devices to which you as a human, with an app, like a browser, connect to.
If you've bought a camera that starts to "all by itself" to send it's available info, like video's to "somewhere" without your consent, you have not "IP" problem : you just made a huge failure by actually buying and using the camera : unscrew it, and throw it away - sorry : recycle it.Camera, optimally, should be on their own "LAN" network, like an OPT1 interface. Keep only your really trusted devices on the LAN.
Now : your question has a one click solution :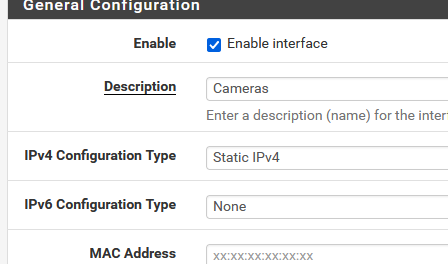
Disable IPv6 on that "camera" interface.
Btw :
To make Ipv6 work on your LAN(s), there is more needed as just the ISP "to activate it".
You're - afaik - the first one on this forum that says that IPv6 "auto enabled".
Disabling it isn't a real option, as, in the future, it will be IPv4 that simply stops .... as it is a protocol from in the past, eventually being abandoned (we still have some time ;) )And true, devices that use IPv6 can have more then one IPv6 so blocking isn't as easy as an IPv6 device. MAC based blocking could be an option.
See what :
can do for you.
-
@Gertjan
Thanks for your response. I do not have any proof that the cameras "phone" home but it is better to be on the cautious side and block their internet access. I am looking into creating an IOT interface where all potentially vulnerable devices connect to. Currently I only have the LAN interface and use a rule to block devices based on their ipv4 addresses from accessing the internet.As for the ipv6 "auto enabled" I mentioned earlier it is just a theory I have. There is a Windows 11 computer I included in the blocked list for accessing the internet that I discovered was able to Windows Update last Friday. This PC was cut off from the internet and had not updated in over a year before this event.
Initially I thought pfSense 2.7 had a bug that allowed the rule to not take effect. But as I navigated to various websites I discovered some sites were blocked but others went through. So I used the Windows Command prompt and used ping on those websites. The websites that did not connect had an ipv4 address while the sites that went through had ipv6. I assumed the Windows Update used an ipv6 address so that was how it was able to bypass the rule. When I disabled the ipv6 checkbox in the Windows 11 network adapter all internet access cease to work including Windows Update.
-
@aceventura said in Rule to block internet access for alias devices still goes through for ipv6:
I do not have any proof that the cameras "phone" home
Why not ?
You can get the your proof !Place the camera on its own dedicated interface.
Add these two rules :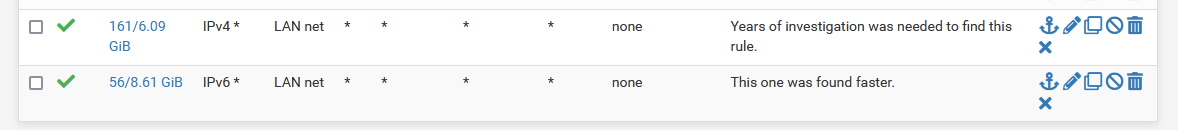
(my example shows the "LAN net", yours would be "OPT1 Net")
As soon as the one and only device on that network start to communicate, even the slightest NTP, or DNS, or whatever, these counters :
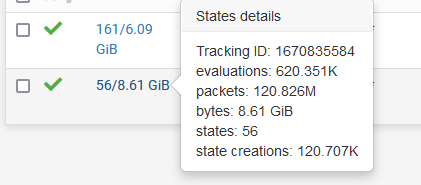
start to raise.
That's pretty rock solid a proof.@aceventura said in Rule to block internet access for alias devices still goes through for ipv6:
As for the ipv6 "auto enabled" I mentioned earlier it is just a theory I have. There is a Windows 11 computer I included in the blocked list for accessing the internet that I discovered was able to Windows Update last Friday. This PC was cut off from the internet and had not updated in over a year before this event.
When you put a bucnh of Windows Pc's on a switch, even with pfSense not offering any IPv6 support, the "Windows Network neighborhood" will be using IPv6 to talk to its neighbors.
Every known OS, for the last decade or so, prefers to communicate over IPv6 - and if it is not available, will fall back (this costs time !) to IPv4.
For those who use their ISP router and no pfSense at all, IPv6 might already works for years without them even nothing it. As that is what Ipv6 is meant to be : as Ipv4 : transparent. Humans don't need to know what IP-whatever is to use the 'Internet'.
Of course, you've chosen to use pfSense. Being 'ignorant' isn't an option anymore
-
@Gertjan
Appreciate the help and all the examples with screenshots you've given so far, really learned a lot from you.