OpenVPN client network FW rules
-
Hello!
I have a pfSense server with Site-to-Site setup. Everything is working as expected. Now I want to create some firewall rules witch clients can access witch resources. But it seems that pfSense sees only the incoming tunnel IP not the actual LAN address on the client? That means, that I cant configure the rules per client, but for the whole tunnel network. I'm sure, I'm missing something? Could somebody point me in the right direction?
-
@zaitz
This is by design of a VPN. The client connects to the server and gets an IP out of the tunnel pool. On base of this virtual IP you can set filter rules.That means you need to assign specific IPs to certain clients to restrict their access differently.
This can be done with VPN > OpenVPN > Client Specific Overrides (CSO). Add a CSO for each client you want to limit with specific rule. Use the common name from the clients certificate and state a certain IP out of the tunnel pool. -
@zaitz
If you have a S2S tunnel , then you don't have "any clients" at the remote end, well technically the remote site is a client.
But all data will flow through the S2S tunnel, with just source/dest ip's as designators.If you need to do rules, based on remote client data coming through the S2S tunnel, you have to give the remote site users a fixed ip.
And create rules based on that./Bingo
-
It sounds like you might not have S2S setup correctly, if it's properly S2S then the "clients" on the LAN aren't actually clients and should not have a IP related to the VPN itself. Normally the way this would work is you'd make sure the devices on one LAN have static IPs and then add rules to allow traffic from that LAN to the other site's network(s), so everything should be based on the local LAN IPs.
-
@viragomann
My tunnel network is 10.10.1.0/24 so the lan on the remote site is 10.10.66.0/24 and the traffic flows. I also setup a CSO where I have set the remote network, i'll attach a screen. Where do I set the static IP address for the tunnel?
Now when i create a FW rule on the OpenVPN tab to block incoming 10.10.66.0/24 traffic, nothing happens, now if I edit my rule to block traffic from 10.10.1.0/24 the traffic from 10.10.66.0/24 stops.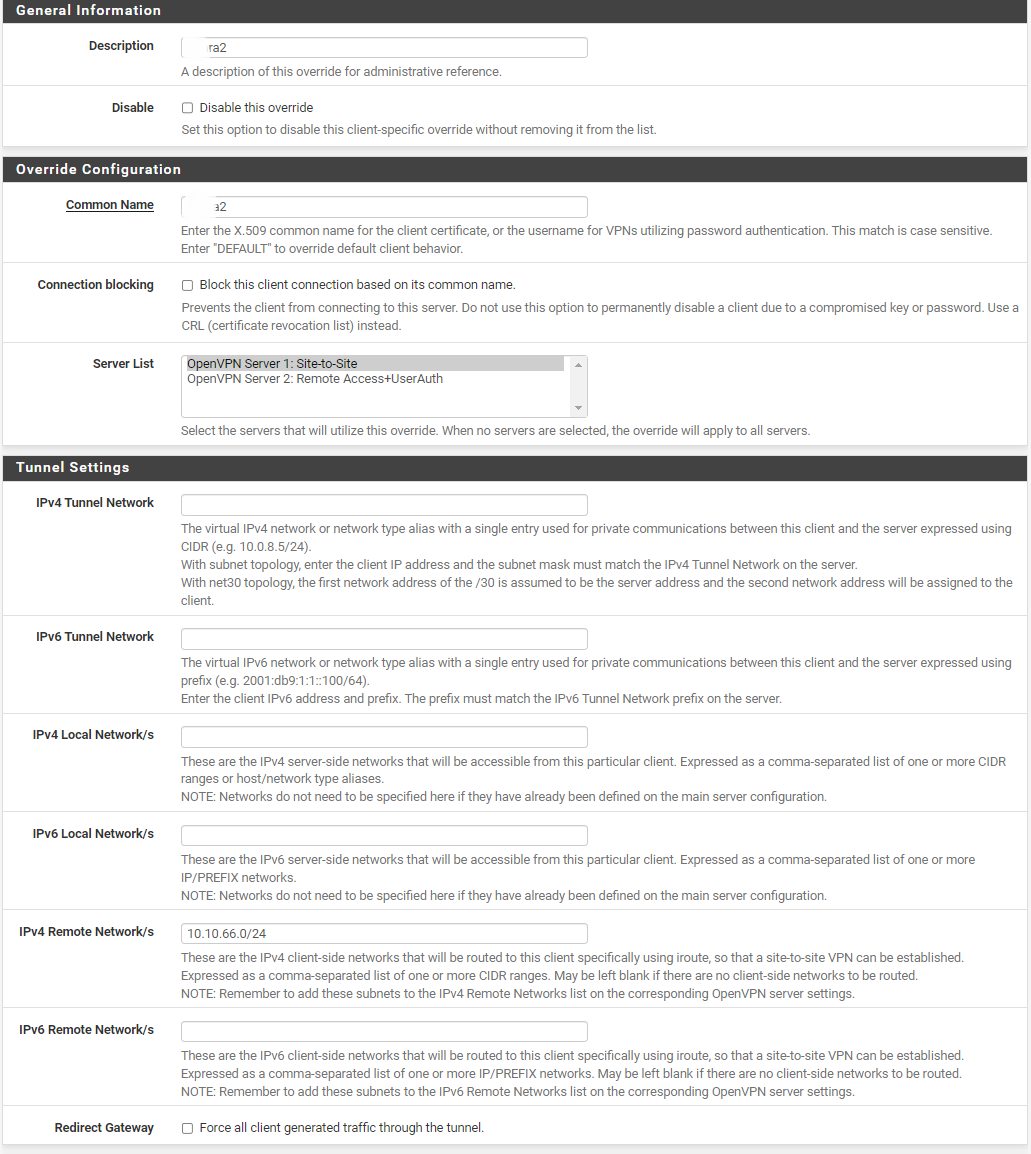
-
I got it. If i add "ifconfig-push 10.10.1.66 255.255.255.0" to the CSO then the client will get a static IP which I can now filter!
-
@zaitz said in OpenVPN client network FW rules:
I got it. If i add "ifconfig-push 10.10.1.66 255.255.255.0" to the CSO then the client will get a static IP which I can now filter!
The tunnel network field is meant for this setting.