Blocking IoT and other devices on my network
-
I am guessing your wifi clients are accessing the alternate networks directly via the netgear AP's own routing and therefore before the traffic reaches pfsense.
When I changed my existing wifi router over to AP mode (after moving to pfsense), I needed to use a third party firmware (supporting VLANs) in order to achieve proper SSID/network isolation. -
@mikehalsey When eero finally added guest to bridge mode they did make it isolate guests, I was pleased to find. Unless the guest devices get a different IP range (carrying through to the router) then I don't think there is a way to isolate them yourself, since LAN packets do not go through the router. As noted VLAN is a way to do this. Otherwise possibly a separate AP since on the 2100 ports can be isolated.
-
@mikehalsey said in Blocking IoT and other devices on my network:
Netgear Mesh Wi-Fi system
None of those soho mesh systems are going to be able to give you the isolation you want I am afraid.
You need wifi that can do vlans - and I am not aware of really any soho or mesh wifi systems that supports it. Now if you could be say dd-wrt or openwrt on your equipment - more than likely you could do actual vlans.
Is it too late to return that system and or sell it and get say something like some unifi AP.. They can do wireless uplink between the AP if you don't have the ability to run wires. They fully support vlans, with vlans its piece of cake to isolate devices onto their own networks and firewall between them with pfsense.
-
One other thing, if you do decide to isolate your various wifi networks using VLANs, you will need a managed switch OR connect the access point directly to the netgate box.
I used my old Asus RT-N66U, which I'd been using as combined gateway router and access point, and installed freshtomato on it. This then allowed multiple wifi SSIDs each tied to a separate bridges and VLAN. These are then all trunked via one network port on the Asus RT-N66U with the remaining ports acting as regular access ports on one specific VLAN. That was IIRC a limitation of the SOC & hardware switch built in to the ASUS. It has been working well in this role since I moved to pfsense.
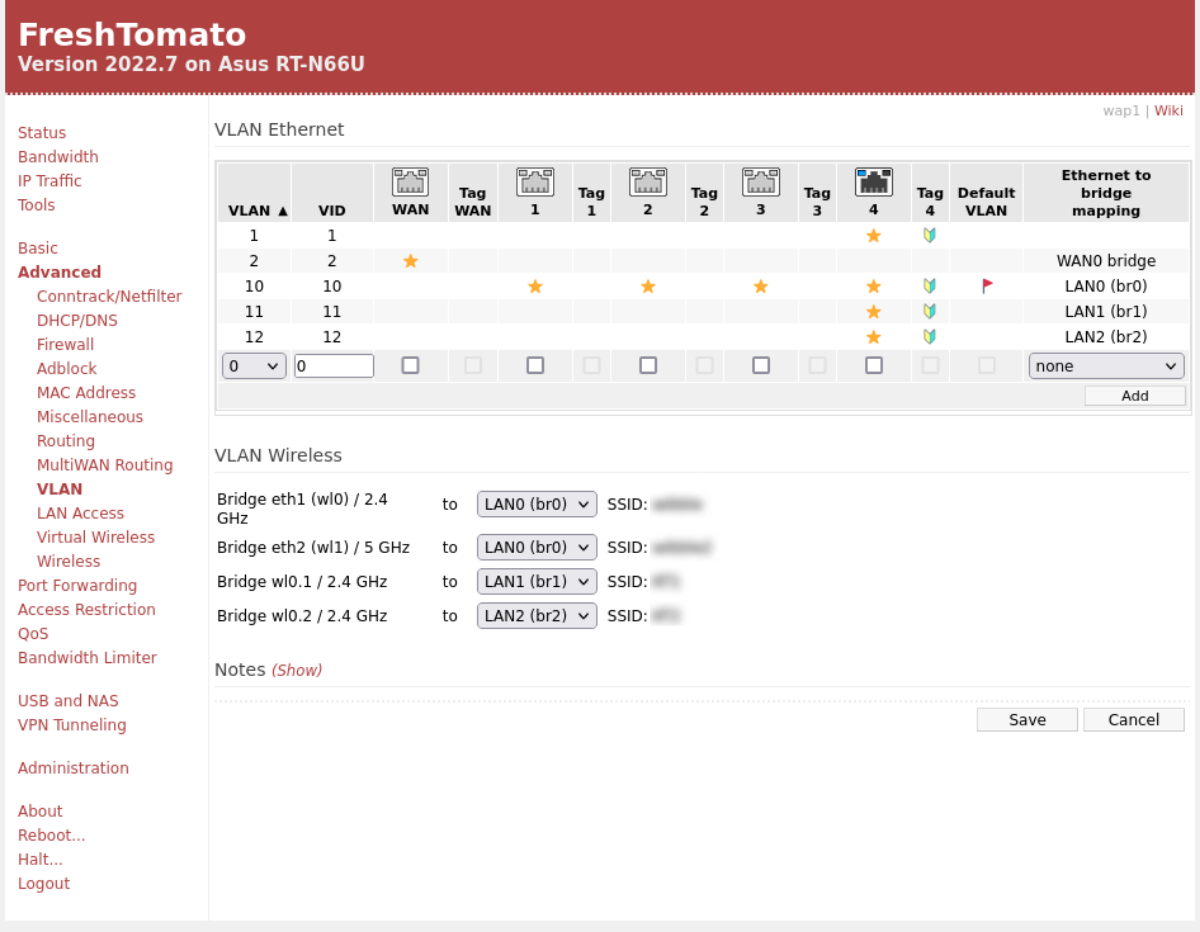
-
This post is deleted! -
I have run pfSense on my home network for several years now. Great software! I also have a Netgear ORBI mesh wifi system - RBK853. I put my IoT devices on the ORBI guest network and it very effectively separates them from the rest of my system. Devices on the guest network are put on a separate LAN (eg, 192.168.2.x as opposed to my regular network of 192.168.1.x). The ORBI handles the isolation and I confirm that those devices are not in contact with my NAS, PCs, etc. For example if I connect to my guest wifi with a laptop then I cannot access any of my NAS drives or any other devices on the regular network. I can’t even ping them.
-
@slimypizza I am not familiar with the ORBI or how it does virtual wireless. My ideal AP setup is what Openwrt refer to as dumb access point. That's If openwrt is perfomant on the hardware at hand, which it is not on RT-N66U due to the Broadcom SoC. So I went with FreshTomato. VLANs seem to be the preferred way to achieve isolation and push all the firewalling/routing control back to pfsense.
-
@slimypizza said in Blocking IoT and other devices on my network:
very effectively separates them from the rest of my system
Where exactly does it do that? Other devices connected to ORBI? How exactly does orbi keep devices on its wifi network from talking to devices on orbi wan? Which normally would be your pfsense network(s)..
-
Hey there, @MikeHalsey and check it!
It's great to see you diving into the intricacies of your setup with the Netgate 2100, Starlink, and Netgear Mesh Wi-Fi. Kudos for the proactive approach in setting up a guest network to isolate your IoT devices from your main network.
Now, onto your snafu with the Mesh box in AP mode. It's quite the pickle, I must say. While Netgear may not be rushing to your aid with a firmware fix, you've hit the right note with the Netgate 2100. Here's a way forward:
-
Access Control Lists (ACLs): Dive into the Netgate's firewall settings. You can create specific ACL rules to allow certain devices to only access the Internet, effectively blocking them from your local network. This is your first line of defense.
-
Device-Specific Rules: For your second requirement, you'll want to configure device-specific rules. You can do this in the firewall settings as well. Assign devices to different zones or VLANs and set up rules to control their access to local resources. This allows you to fine-tune your network security.
Now, for a sprinkle of personal experience: When I had a similar issue, I found that third-party firmware with VLAN support was a game-changer. It allowed me to achieve the desired isolation and control. So, if your situation persists, consider exploring that avenue.
And who knows, pfBlockerNG might just be your knight in shining armor...
-
-
@MikeHalsey Hey Mike...
I've had this problem... isolating subnets etc...
This is a common issue with firewalls and you can find out how to do this in the documentation...
Just substitute OPT with WLAN or IOT. Should be all the same.
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/opt-lan.htmlIf you want to isolate individual clients, it has to be done at the switch level.
You'll have to find a managed switch that suppoers this feature.;-)