OpenVPN Site to Site not working after upgrade to pfSense 2.7
-
Hello,
I have several pfSense boxes at various locations which tie into a pfSense+ AWS instance via OpenVPN so that that they can communicate with one another via VPN tunnel. Each "site" has multiple WAN connections, so doing it this way was simpler in my mind than using one of them as a "home base"
I recently upgraded the pfSense software on what I'll call "router 2" and it no longer connects to the OpenVPN tunnel. I am using TLS, not a shared key. Clients on v2.6.0-RELEASE still work fine. AWS instance is on pfSense+ v23.01-RELEASE. The only thing out of the ordinary that I found in the logs on "router 2" is an entry stating "WARNING: 'ifconfig' is present in remote config but missing in local config, remote='ifconfig 10.255.255.14 10.255.255.13'"
I should note that I am using /30 subnets for all the site to site (or, in my case, site to datacenter) connections. Changing the server side and "router 2" side to a /29 did bring the connection back "up," but I could not communicate with anything behind "router 2" via the connection. I checked routes, firewall rules, etc., tried rebooting the AWS instance and "router 2." No dice. So I flipped back to my original /30 config on both sides and broke the connection again.
I could "try" upgrading the AWS instance to see if that fixes it (maybe differing versions of OVPN?), but I may break everything if I do. I'm inclined to revert "router 2" back to v2.6.0-RELEASE, but I'd really like to make this work again so I can upgrade all the others.
Anyone's help would be greatly appreciated!!
-Mike
-
I'm still using 2.6.0 on my Central node , but have upgraded several remotes to 2.7.0 wo. any issues.
I have that warning on all my S2S tunnels too , not causing any issues.
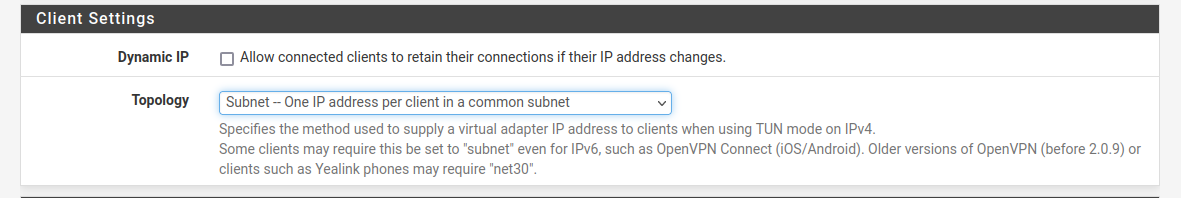
I'm using /30 as linknet too , and subnet topology (NET30 is deprecated)
/Bingo
-
@bingo600 I wonder what would be causing this then. Literally the only change that occurred was changing from 2.6 to 2.7 on one router. Do you happen to know if the version of OpenVPN changed in the upgrade?
-
@IntrusionDetector
I "think" the openVPN version changed , but am not 100% sure.What i find strange is that you say it doesn't connect with a /30 , but does connect with a /29 as linknet (no data through though).
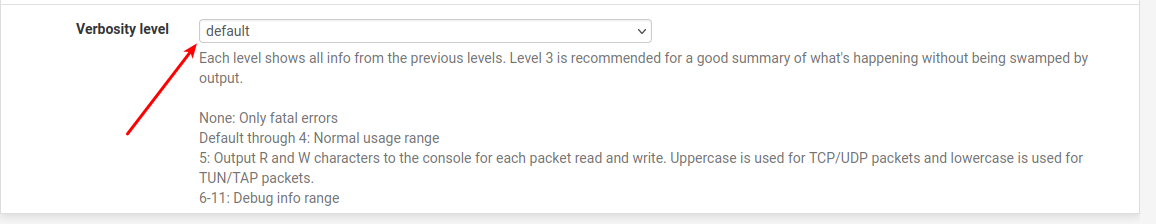
I have not seen openVPN not being able to connect wo. "barfing" in the logs.Did you try to increase the "verbosity level" ?
/Bingo
-
@bingo600 BINGO!
Now I know why that's your handle lol
I turned the verbosity level to "3 (recommended)" instead of default and came up with this:
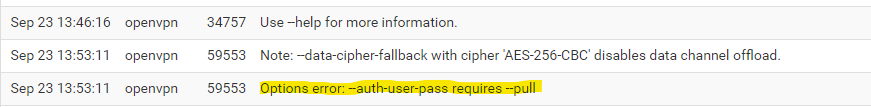
I had an old username and password in the client side config, removed them, saved, and the tunnel came right back up using only my certificates. I wonder why it worked with the old creds in there for so long...In any case, it's fixed now. Thank you for nudging me in the right direction. I should've thought to turn up the logging. I guess I hadn't had an issue with the thing in so long that the thought never crossed my mind.
A huge THANK YOU for helping me solve this!!
-
@IntrusionDetector
Nice you got it working/Bingo