Stopping Ads - Best Way
-
@JonathanLee said in Stopping Ads - Best Way:
This was the only way it would work for me I also attempted the loopback only version
hmm, I wonder if your Unbound is listening in the loopback ?
For this to work, Unbound needs to be listening in the loopback too. -
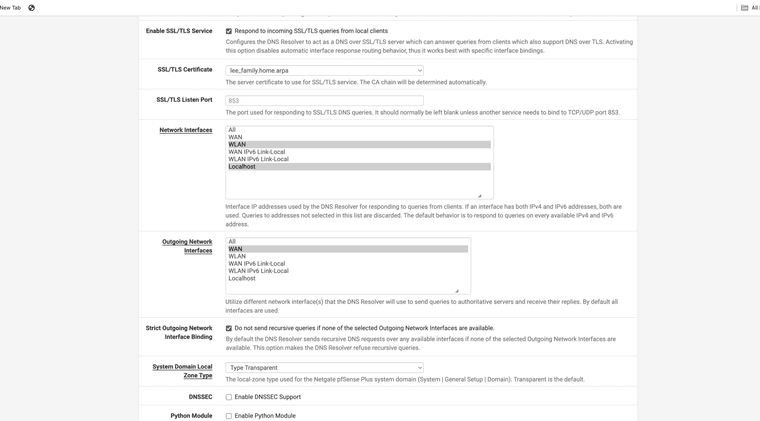
Loopback used DNS over TLS SSL
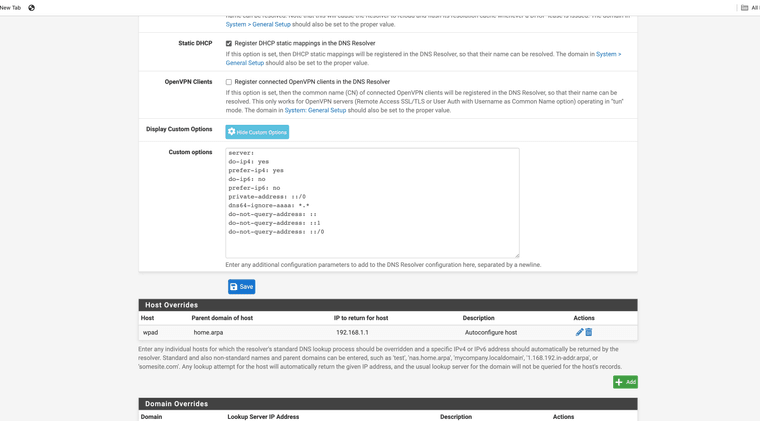
Custom options because of ipv4 only isp restrictionsWPAD in use for proxy with DHCP options 252 and 42 enabled
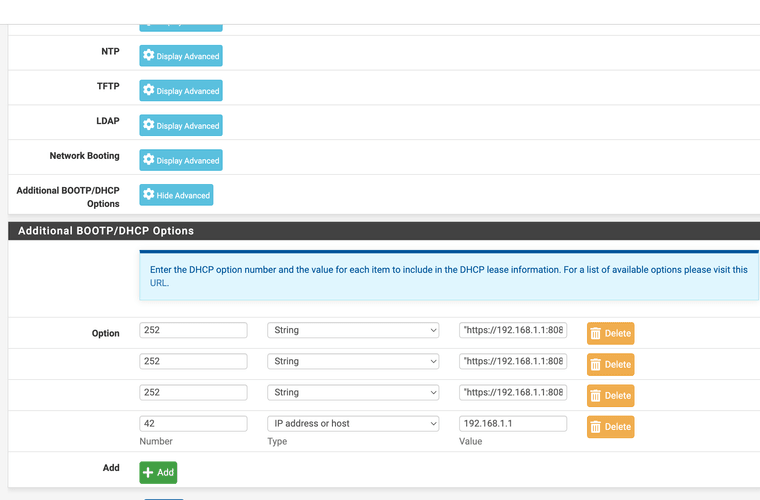
Interesting I could only get this to work with use of both loopback and firewalls address
-
@mcury If I use this setting wont it ignore the adguard dns servers as I would think these would be considered remote dns?
-
@JonathanLee said in Stopping Ads - Best Way:
Interesting I could only get this to work with use of both loopback and firewalls address
hm, indeed, I can't see at this moment a reason why it wouldn't work..
The idea behind that NAT is simple, force everything that refuses to use pfsense's DNS server to use it.
Unbound forward mode is disabled, which means, use pfsense's DNS server for everything and if not in cache or in domain/host override, query root servers directly.
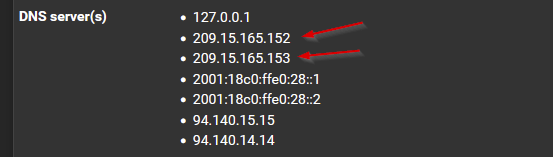
Also, ignore ISP's DNS servers provided by DHCP on WAN.Resuming, everything will be filtered by pfblockerNG DNSBL.
I can see that its working..
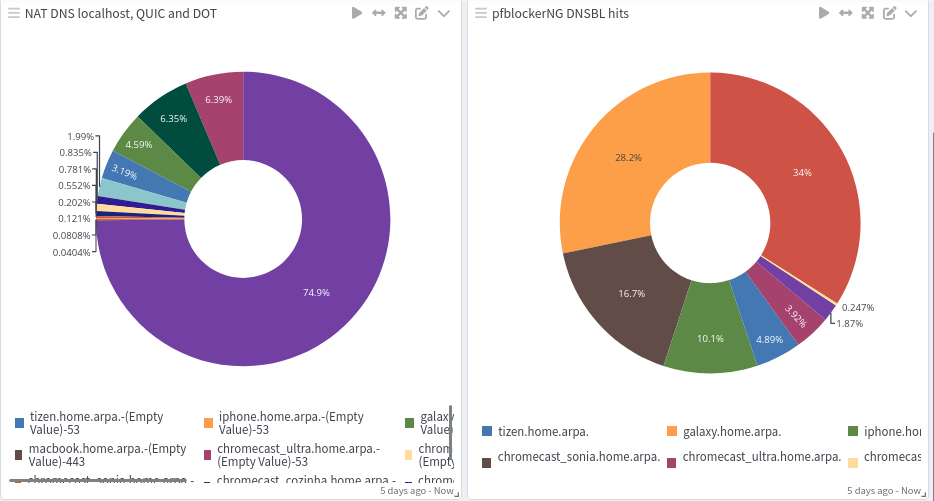
In the picture above, left side, all hosts that shows up with a destination port 53, I know that were trying to use another DNS server, QUIC will show up using UDP 80/443 and DOT (TCP-853).
The right side, I'm just filtering for connections to 10.10.10.1
-
@oznet my firewall's address is the 192.168.1.1 so if you set it to allow the firewall itself it should still work as when the address hits the firewall it would still convert to the loopback for the resolve anyway.
I use the 853 tls dns sites, sometimes I get hit with scans that use decoy addresses of my dns servers that causes issues once and a while snort blocks it.
-
@mcury I notice you allow QUIC. Palo Alto just created software to decode it recently. I am wondering how you are using that?
-
@keyser What is this setting called, I dont see that?
-
@oznet I see it in your graph, it's HTTPS 3 or HTTPS over UDP
-
@JonathanLee said in Stopping Ads - Best Way:
@mcury I notice you allow QUIC. Palo Alto just created software to decode it recently. I am wondering how you are using that?
I'm blocking QUIC entirely with a reject rule, this means that the browser will receive a 'no-go' as soon as it tries to use QUIC, thus reverting the connection to normal TCP.
If you use drop, it will slow down everything.
You want the browser to know that QUIC won't work as soon as possible so it can use the TCP protocol without any delays.
-
@mcury They have some youtube videos out there with how to decode QUIC it is amazing stuff.
-
@JonathanLee said in Stopping Ads - Best Way:
@mcury They have some youtube videos out there with how to decode QUIC it is amazing stuff.
I'll take a look at it, definitely will..
I have been treating QUIC as an insect, a bug that needs to be smashed..
Just like DOH or DOT.These techniques (DOH and DOT), in my opinion, were developed not for privacy, but to avoid ADs blocking. To increase their revenue, but this is just my opinion.
QUIC is another thing, it is faster.. But how can you control it?
-
@mcury I agree one can say they were created to avoid CCPA and GDPR laws. They do not follow official protocol compliance.
-
@oznet DNS Query Forwarding: Enable Forwarding mode