Squid Feature Request "host verify strict" GUI option
-
Hello fellow Netgate community members,
I just learned about this amazing Squid feature on the Netgate forum.
This option could be built into the GUI to bring more visibility to host verification options.
This could be the solution to the package/ GUI interaction.
Tell me what you think.
A radio button for the following in Squid package config options. . .
host_verify_strict on
host_verify_strict offRef:
https://redmine.pfsense.org/issues/14786http://www.squid-cache.org/Doc/config/host_verify_strict/
-
@JonathanLee My only question is this.
How come when you add it to the Advanced Sections in squid , it seems to have no effect.
Im all for having a GUI option but it doesnt seem that the package even takes this feature into account. -
@michmoor I was able to have it accept it when placed in before auth in custom, now it is visible inside of the Squid configuration file. No errors came up with Squid.
We could research it more with "Apple music "and "mzstatic" by way of leaving Apple music set to splice and not splicing mzstatic just to see if Squid allows the UPP connection to continue on with other piggy backed spliced connections on a bumped certificated device.
-
@JonathanLee Same.
But /409 Conflict errors should stop. They dont.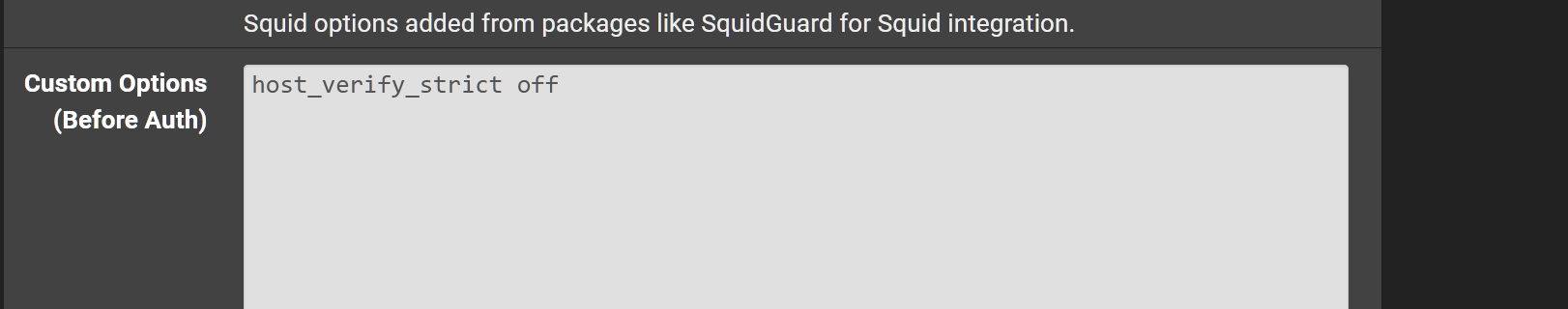
-
https://redmine.pfsense.org/issues/14390
Check this out I just learned about this open Redmine.
-
@JonathanLee Ive seen this one.
The solution to this is to turn it off but as i mentioned, the package is not respecting the "host_verify_strict off" command.
In my opinion thats the overall problem. Having an option in the GUI is nice but that still wont do anything to fix the issue.Overall, yes. CDNs are an example where the TTL is so short that what pfsense knows about domain name/IPs and what the client may know or cached is so different it breakts applications.
Also, the other problem is that from the looks of things there doesnt seem to be any maintainer for Squid at Netgate. So a problem like this will most likely go unresolved. They still havent fixed the " Youtube Restrictions set to None" problem. You still need to make a change manually in the conf file for that...
edit: Bug #14390 is still set to HIGH with no Assignee..
edit: According to the conf file the setting is in its default state.
# as from where it was loaded at the IP level. The Host: header may # be different from the connected IP and approved origin. # #Default: # host_verify_strict off -
@michmoor what about using storeID?
https://wiki.squid-cache.org/Features/StoreID
-
@JonathanLee
Bug #14390 pretty much summarizes perfectly the issue and one that i discovered as well.
Today in 2023, you have applications that hold on to cache DNS entries for a long time. Longer than what the TTL is set for. Thats just how the modern internet works today.The solution is to either
- Fix this by disabling host verify strict. Give the proper warning in the GUI as to why this should be disabled. Additionally figure out why the setting to turn off doesnt work in the package.
- Do nothing (Netgates position) and continue to have these /409 errors break connectivity for users ONLY if Transparent proxy settings are used. Explicit proxy has no issue with this.
-
@jimp
You think a resource can be assigned to review the redmine? This will be a quality of life improvement with the use of the application.
https://redmine.pfsense.org/issues/14390