Is remote access possible with virtualisation?
-
Hello,
is remote access possible with virtualisation of pfSense?
I would like to remotely access my home desktop Ubuntu 22.04 LTS desktop, which is running VMM 4.0.0 and pfSense 2.7.0-RELEASE (amd64) as a KVM on VMM.
The KVM router pfSense, the host Ubuntu desktop and other KVMs can access the Internet.
pfSense's WAN interface seems to be different to the ISP's public WAN IP, so I'm unsure what address or configuration is needed for remote access? -
@eiger3970-0 said in Is remote access possible with virtualisation?:
pfSense's WAN interface seems to be different to the ISP's public WAN IP, so I'm unsure what address or configuration is needed for remote access?
VM, KVM or VMM or bare bone hardware : it's all the same.
What do you mean with "seems different" ? Can't you see it ? is it RFC1918, or not ?
If the pfSense WAN NIC has the ISP's public IP, then nothing is needed. The one and only WAN firewall rule to allow VPN traffic enter is enough.
If pfSense uses a RFC1918, then, bewteen the pfSense WAN and your ISP there is another router.
This router has to be NATted (PATted).
Like "traffic coming in, using protocol UDP, with destination port 1194, send it to the pfSense WAN IP, same port". -
@Gertjan
My understanding is:
KVM: Kernel Virtual Machine running from the host OS or VMM's kernel, much faster than a VM.
VM: Virtual Machine running on top of an OS (doubling up a lot of resources).
VMM: Virtual Machine Manager/Hypervisor, needed to host virtual machines.My poorly worded "seems different"; the KVM pfSense router's WAN interface 100.76.25.214 is different to the ISP's public WAN IP.
This is where I think I'm having the network issue. My physical ISP modem is bridged, so my understanding is all packets should be routed to my machine's NIC0 WAN physical interface.
I understand that my machine's Ubuntu OS has bridged NIC0 to the KVM pfSense router's WAN interface, so somewhere in between the ISP public WAN IP is changed to the KVM pfSense router's WAN IP/interface.My understanding is that for remote access to work, a public WAN IP address must be entered.
1: I can either enter my public WAN IP address and then perhaps port forward SSH port 22 or VNC port 5900?
or
2: I can setup pfSense's OpenVPN remote access software, but this needs the pfSense WAN interface to have a public WAN IP, as the remote user access certificate generates a log in access from the pfSense WAN interface?Here's my home network:

-
@eiger3970-0 said in Is remote access possible with virtualisation?:
the KVM pfSense router's WAN interface 100.76.25.214 is different to the ISP's public WAN IP.
Where does this 100.76.25.214 come from ?
It's a public IP .... and I presume your not owning this IP, and your not an ISP.edit : wait : no .... it's an rfc6598 IP : https://www.rfc-editor.org/rfc/rfc6598.html whatever that might be.
100.64.0.0/xx is part of this range.Anyway ... nice ... a local "complicated" setup using also a complicated ISP setup.
I've been running a VM setup of pfSense @home, where the WAN was connected to my ISP router.
My pfSense WAN used a classic RFC1918 (like 10.0.0.1/24). Using the build in Hyper-V VM.
After a year or two I had enough of it, gave it its own 'box'.Is remote access possible with virtualisation?
Yeah, of course. Your setup is unrelated to that capability.
In a few words : Just NAT/PAT the routers you use.And better be sure that your ISP actually routes traffic TO you.
Without reading this rfc6598 .... I suspect there might be an issue there.Fire up packet capturing on the WAN, using the right port (1194 ?) and protocol (UDP ?).
Now, run to your neighbour **, connect, with his device (PC) to your WAN IP usina OpenVPN client, using the 1194 port and UDP protocol. If the packet sniffer now shows packets, your good.** : or use your phone, wifi disabled.
-
@Gertjan
My nat doesn't seem to be allowing remote access?
My ISP uses a carrier grade NAT, so maybe that's an issue?
-
@eiger3970-0 said in Is remote access possible with virtualisation?:
a carrier grade NAT
from what I know about CGNAT : that type of connection doesn't allow traffic initiated form the Internet being routed to you.
Maybe you have an "ISP GUI" where you can instruct them to NAT ports to your WAN IP ? -
@Gertjan
The ISP says:
Yes. We support VPNs that use TCP or UDP. SSL based VPNs typically work best to traverse CGNAT. NAT traversal support is required by the VPN.We are unable to provide support for troubleshooting services for VPN connectivity issues. The App also may not work correctly when using VPN. Please contact your VPN provider for further support.
-
@eiger3970-0 said in Is remote access possible with virtualisation?:
The ISP says:
Yes. We support VPNs that use TCP or UDP. SSL based VPNs typically work best to traverse CGNAT. NAT traversal support is required by the VPN.That would be correct, if they were implying outgoing VPN client connections to the outside world

Incoming VPN = the traffic should be present on the pfSense WAN interface, like this :
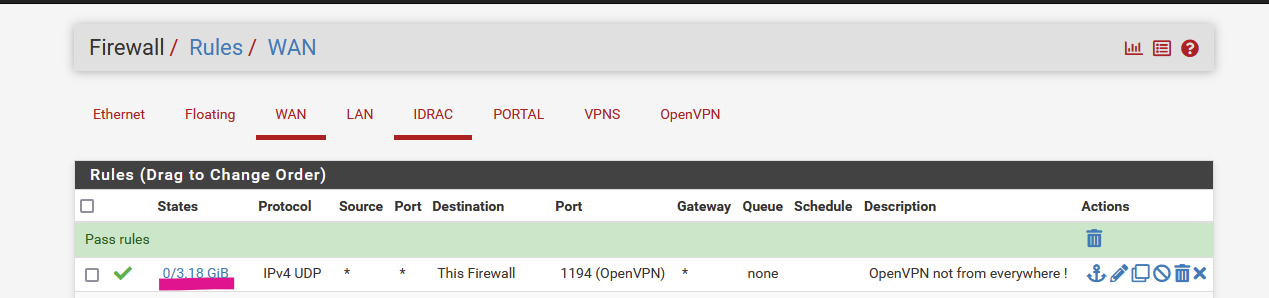
which proves traffic is reaching my pfSense WAN interface.
If nothing reaches pfSense, examine the device to which is is connected. Example :
Because I'm using an ISP router, I also had to "PAT/NAT" my ISP router, like :
Incoming UDP traffic using port 1194 => send it to the WAN IP of pfSense, same 1194.
And that's all there is to do.The fact your using a VM doesn't change much.
That is : it adds a ton of complexity, of course. -
@Gertjan
Thx.
I have the virtual router and network trafficking the Internet via the ISP's brigded modem.
So that's not too complex.
The challenge isn't solve though by a NAT. Something to do with the ISP's CGNAT? -
@eiger3970-0 said in Is remote access possible with virtualisation?:
Something to do with the ISP's CGNAT?
Look up that word in this forum.
It's known this makes NAT-not-possible.