in Site-to-Site OpenVPN can not access to the client LAN from Server
-
I have the same problem. In addition, I have a dual WAN setting. The pfSense sends the packets, which are actually intended for the client network, over WAN2 to the Internet.
The pfSense can reach all clients in the client network with the OpenVPN server.Has anyone already found a solution for this? If even a new installation doesn't help, I guess I have to go back to 2.6.
-
Did anyone try my suggestion? That was what fixed it for me when I had this issue before. All my other settings aligned with the guide here: https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html
-
After trying everything suggested I found a solution: there was a dual Wan setup that was only operating as a single. I didn't need it so fully removing the dual wan setup returned full function of the site to site connection.
-
-
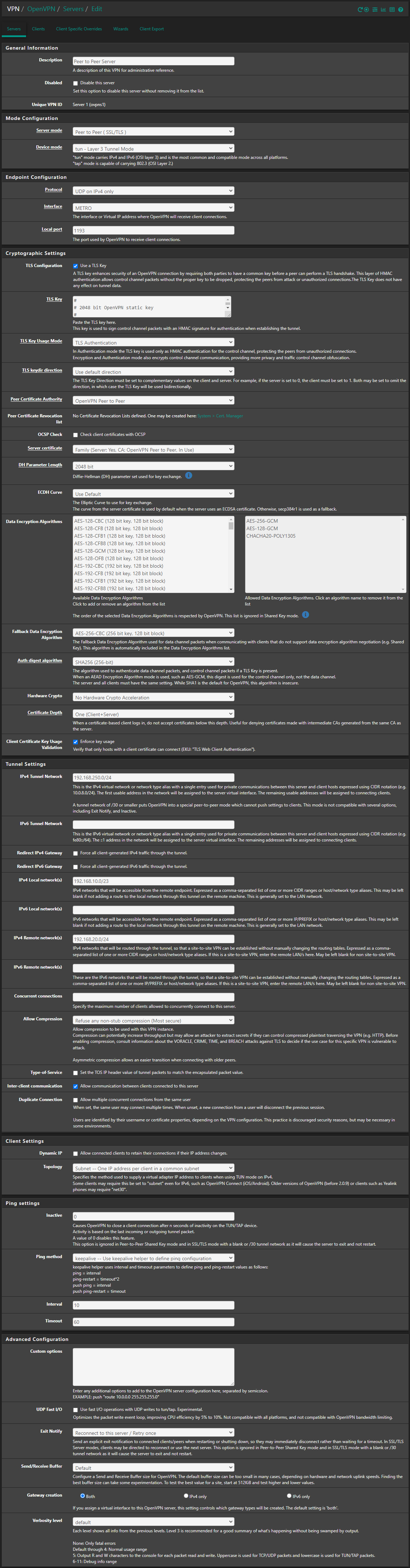
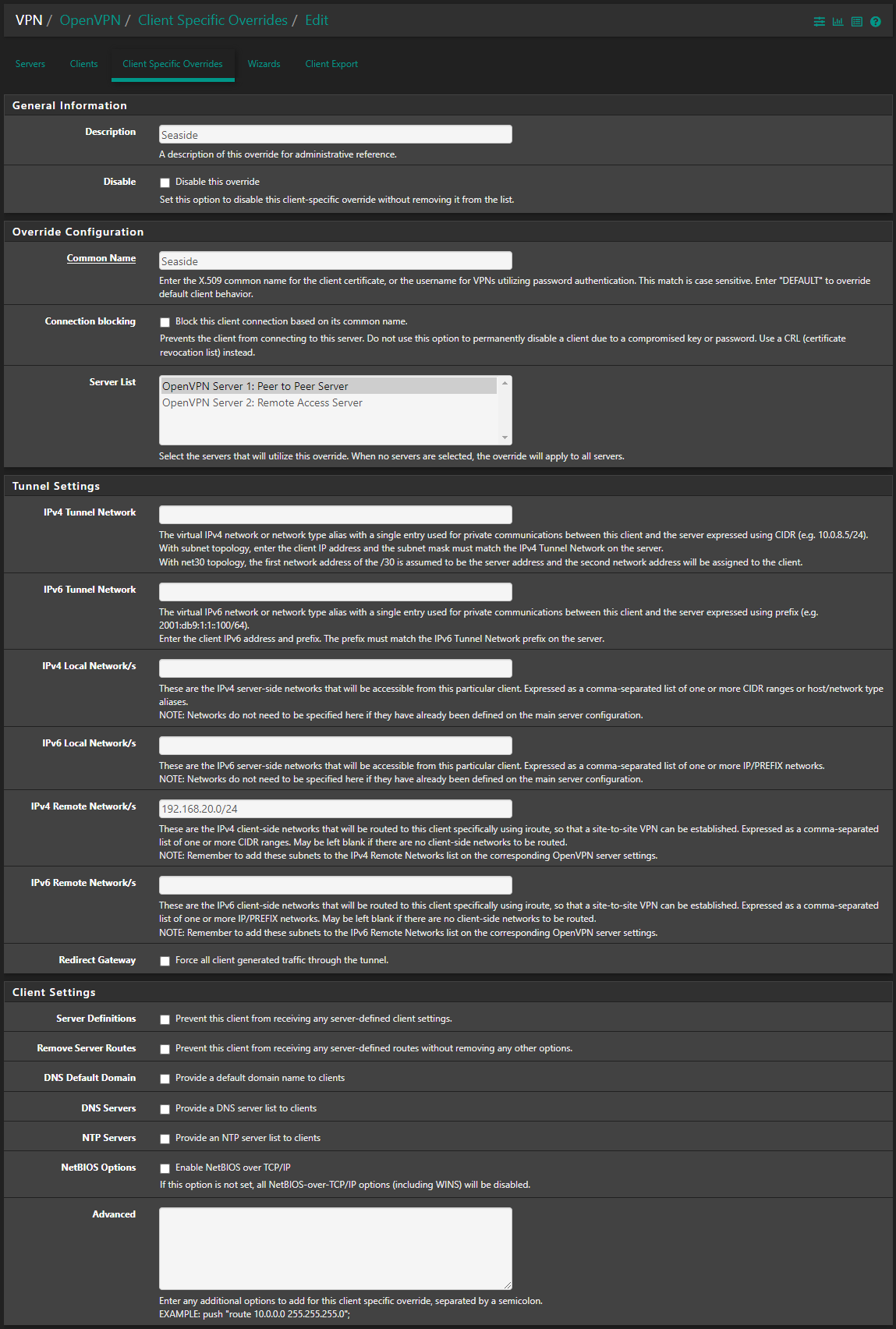
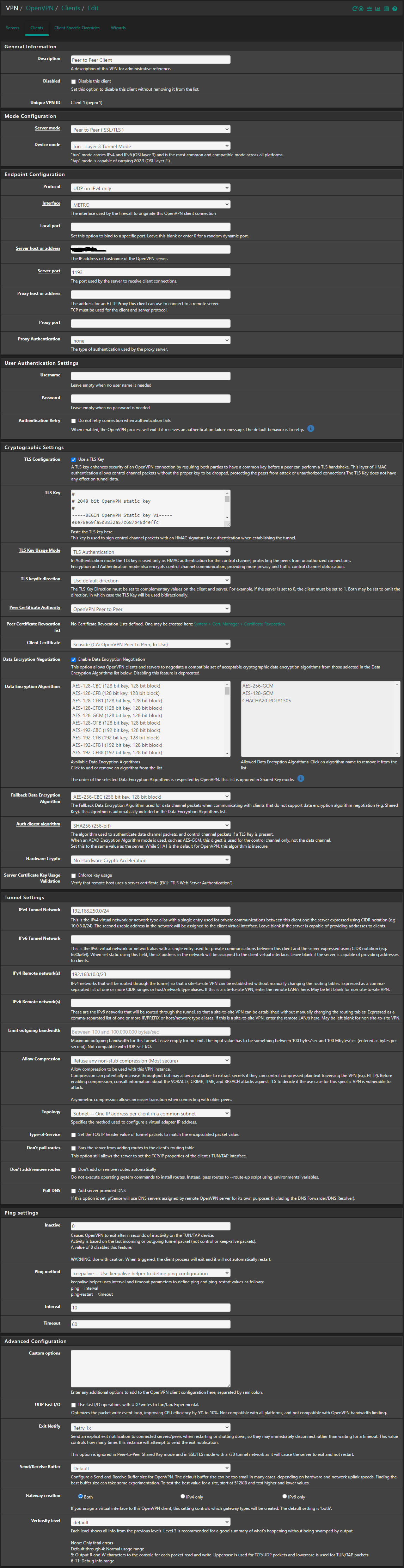
@PauloPedrozo So did I, but I still had the same issue until I explicitly defined the IP in the tunnel network field on the client specific override (eg. 192.168.250.2/24 in the OP example)
-
@TTBruce said in in Site-to-Site OpenVPN can not access to the client LAN from Server:
Did anyone try my suggestion? That was what fixed it for me when I had this issue before. All my other settings aligned with the guide here: https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html
I tried, but unfortunately it did not work. I even swapped client and server. Now it is the client side (the one with dual WAN) that does not reach the server side.
-
Its the same problem in my case. Single WAN workts perfect but activating a dual wan setup breaks it. Its possible to ping all IP destinations from OpenVPN Client pfsense (the one with dual wan), but it its not possible in case of clients which are part of the remote network ip range.
-
@Rossi said in in Site-to-Site OpenVPN can not access to the client LAN from Server:
Its the same problem in my case. Single WAN workts perfect but activating a dual wan setup breaks it. Its possible to ping all IP destinations from OpenVPN Client pfsense (the one with dual wan), but it its not possible in case of clients which are part of the remote network ip range.
It actually works for me now. After swapping the client and server side, I made the following entry on the client side (the side with dual WAN):
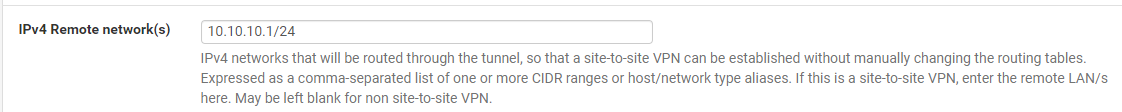
This is the network of the server side. But the instructions did not say that you have to enter this on the client side as well.
However, in the meantime, I also deleted the WAN gateway group and failover. So I don't know if the combination of both led to success.
-
Just a reminder : this 10.10.10.1/24 network is also a default network created by pfBlockerng.
If you have pfBlocjerng installed, and have this :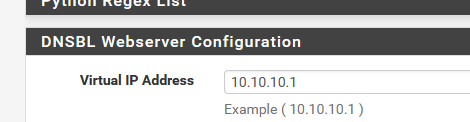
then a 'nothing is working' situation is created.
-
I don't have this installed. But thanks for the info, will keep that in mind!
-
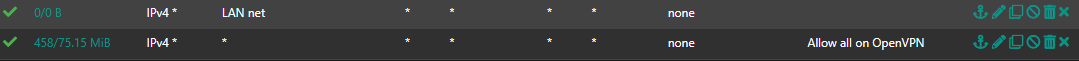
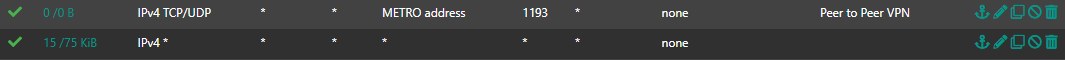
Makes no difference in my case. At the end i had to create a new LAN firewall rule at client site pfsense (the one with dual wan and failover).
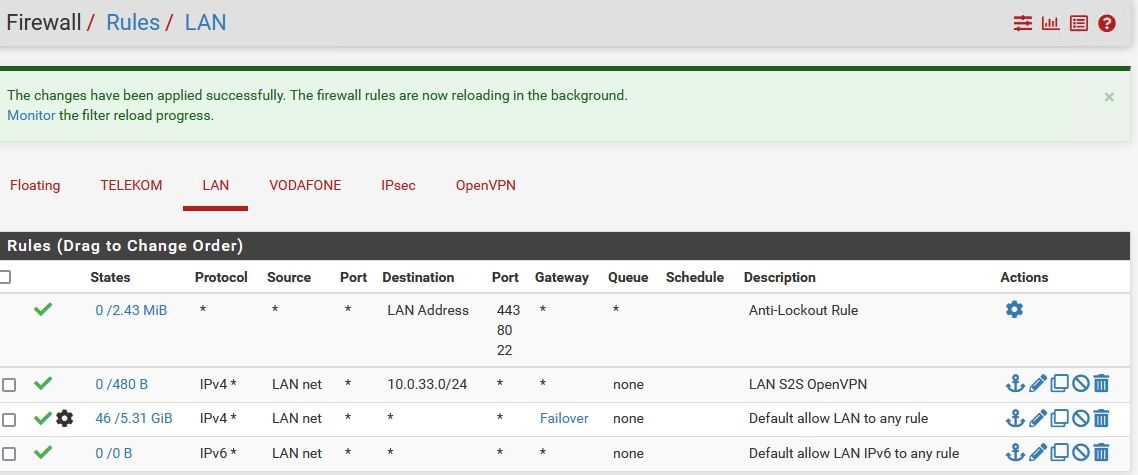
10.0.33.0/24 is the remote local net.
Now it works in both directions.