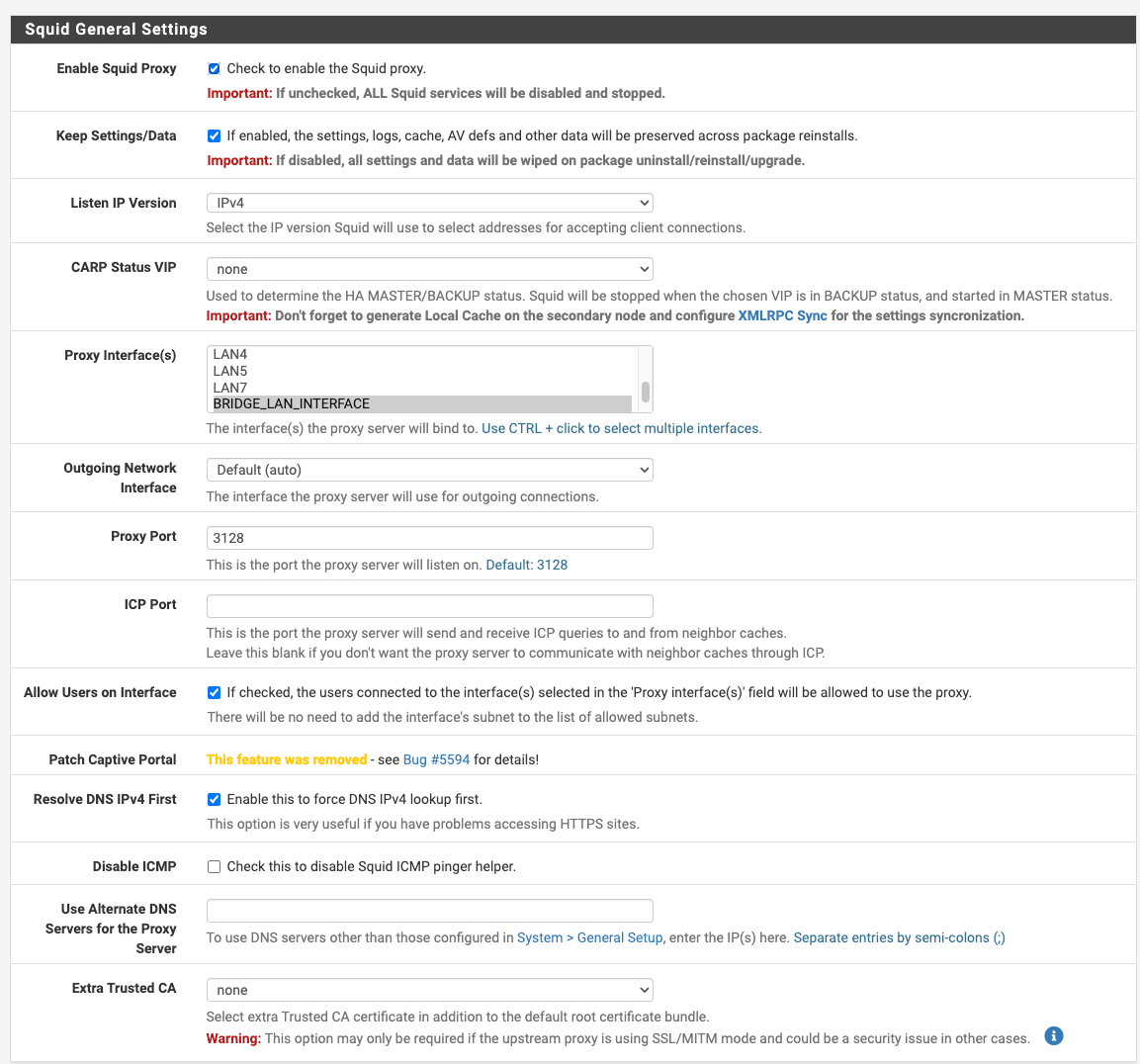
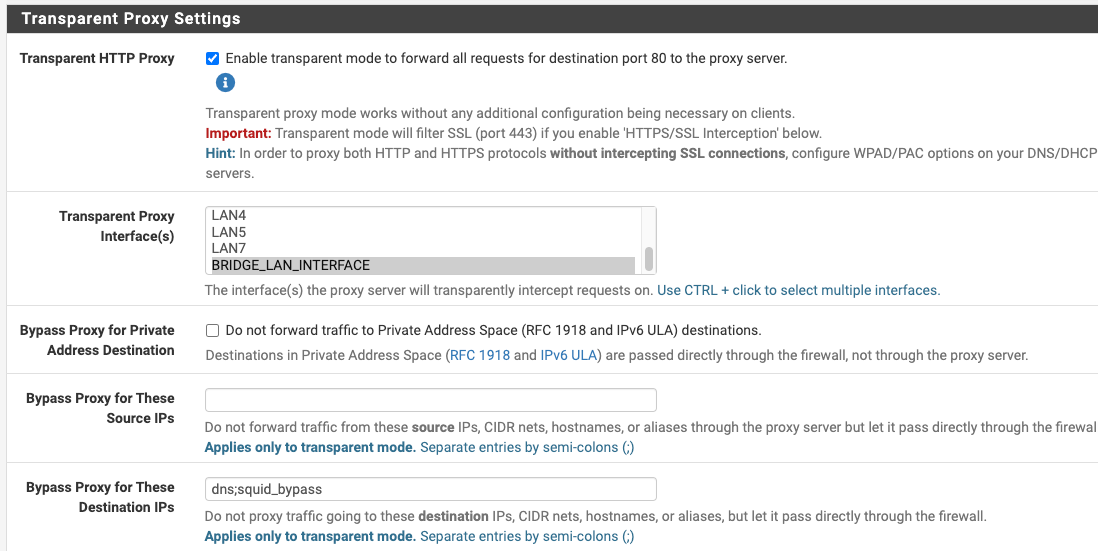
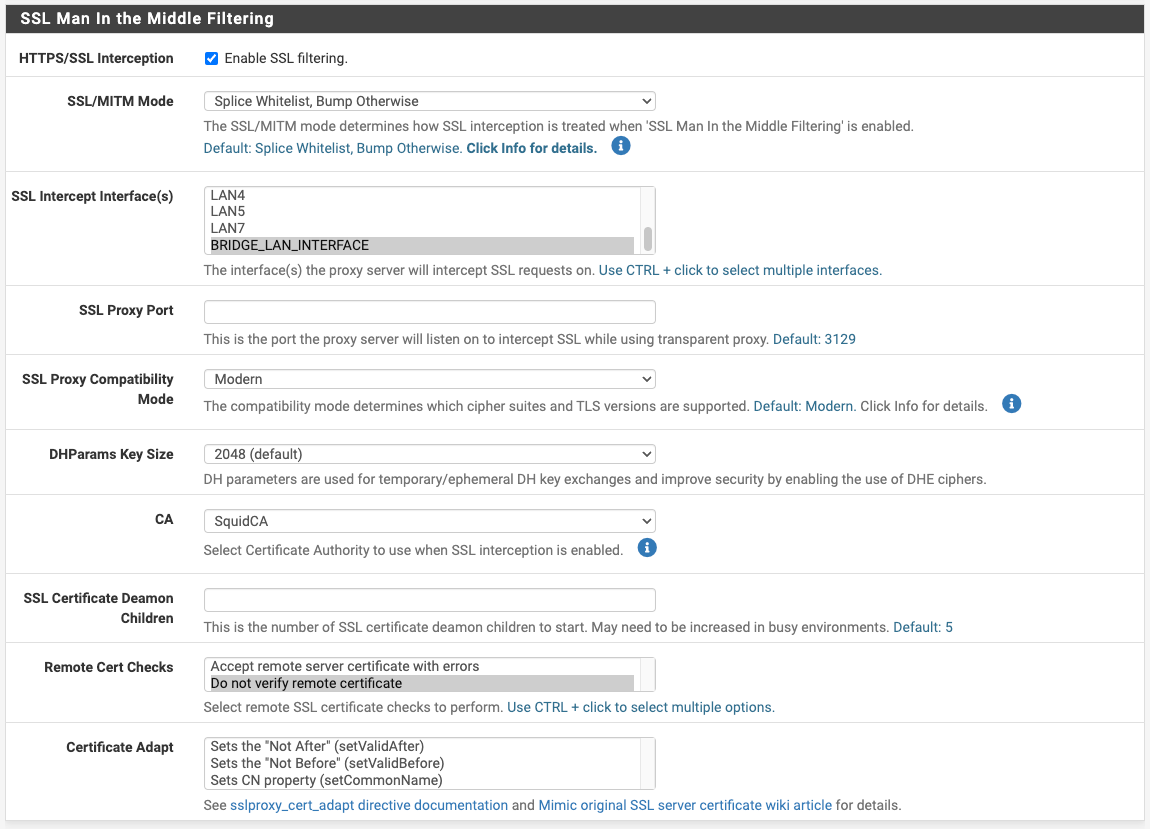
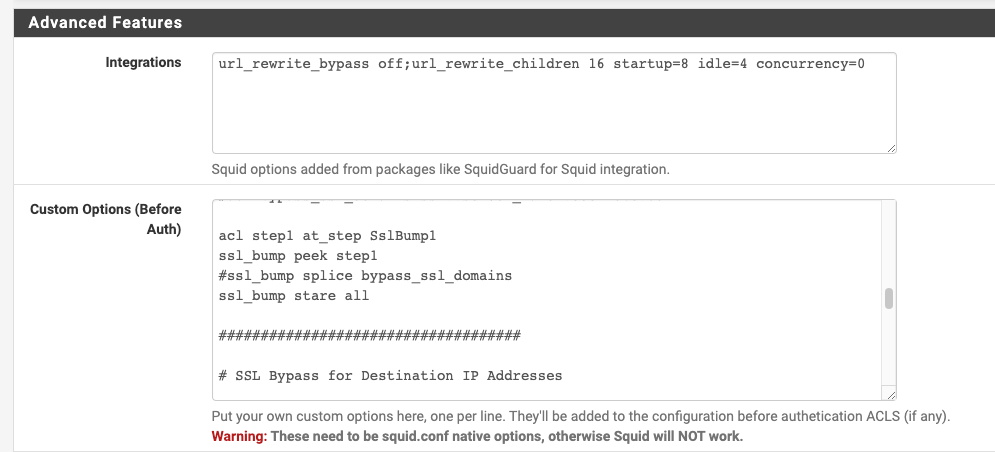
Squid Proxy "Bypass Proxy for These Destination IPs" Not Working?? Transparent HTTP Proxy Mode + HTTPS/SSL Interception
-
@dkzsys
Check this out for WPADhttps://docs.netgate.com/pfsense/en/latest/recipes/http-client-proxy-wpad.html
It's a really good how to overview of WPAD. I have mine set up this way with an addition of DHCP options to automatically send the proxy and DNS information when IP addresses are distributed.
DHCP option 252 and 42
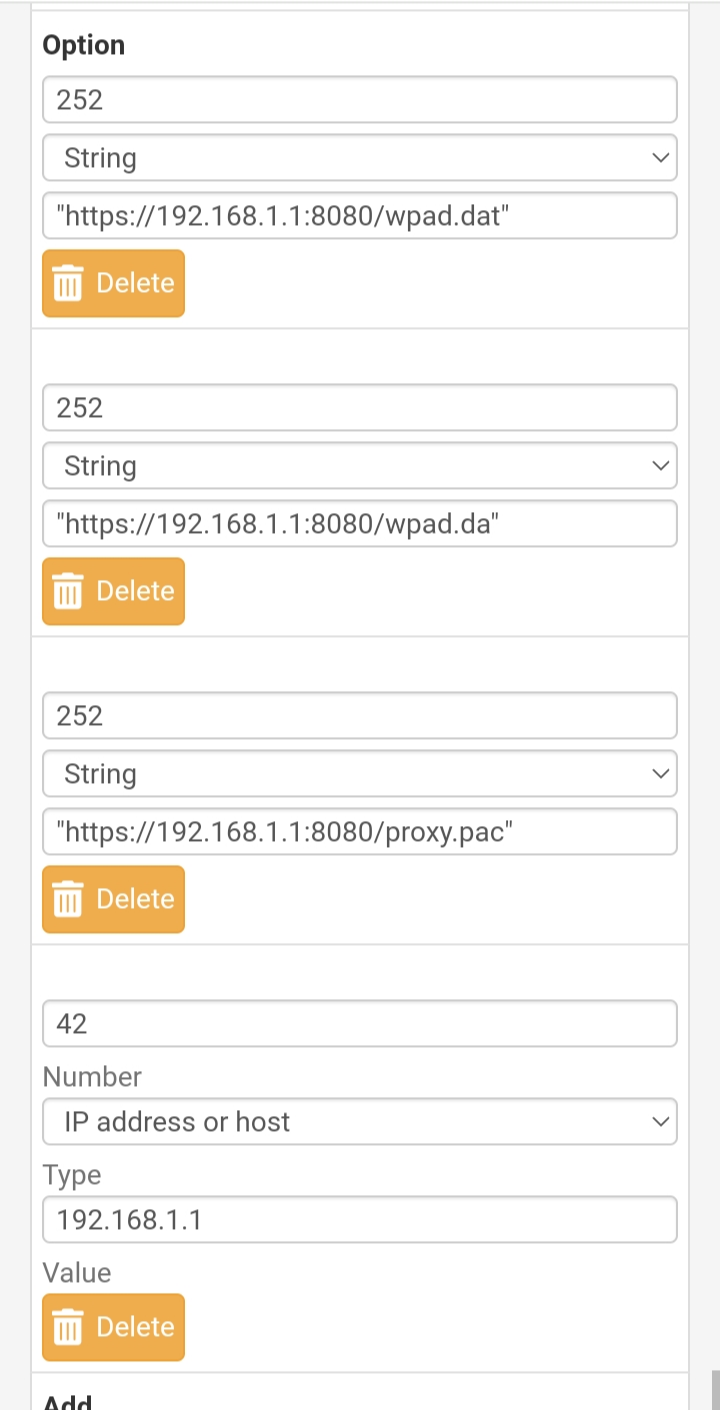
"A WPAD host may be supplied via DHCP numbered option 252 (string value containing the entire URL to the WPAD file) or DNS, which is easy to do with the built-in DNS forwarder" (Netgate docs).
Normally you would use standard ports again my GUI uses port 8080 and it works good for the XBOX One
-
@JonathanLee said in Squid Proxy "Bypass Proxy for These Destination IPs" Not Working?? Transparent HTTP Proxy Mode + HTTPS/SSL Interception:
@dkzsys
Check this out for WPADhttps://docs.netgate.com/pfsense/en/latest/recipes/http-client-proxy-wpad.html
It's a really good how to overview of WPAD. I have mine set up this way with an addition of DHCP options to automatically send the proxy and DNS information when IP addresses are distributed.
Thanks for the illustration as always @JonathanLee ! Yes - I went through the same page as well:)
For me, the next is to evaluate switching back to AdGuard Home for DNS on RaspberryPi, or use SquidGuard with pfSense DNS. Since I've blocked DNS (53, DoH, DoT) to WAN, and NATing locally, AdGuard would have a similar effect of SquidGuard in terms of service/domain blocking. (and neither approach will prevent kids bypassing with VPN). And at this stage, I don't need time-of-day control. So my criteria would be relatively simple:
- #1: no impact to Squid transparent proxy implementation (re earlier discussion in this thread)
- Ease of adding/removing domains
- Ease and effectiveness of rule toggles.
-
@michmoor WPAD auto configures devices to use the proxy. It's for laptops that move from the office and back to home. It's so you an admin never need to set the poxy settings. When a known device jumps on your network the device already knows to use the proxy, versus having to configure it on the device each and every time you change from a lan at the office to your lan at home. It's explicitly for proxy use. It just does it automagically.
-
After a few days of testing with Transparent proxy + SSL Interception (Splice All), a couple of observations:
-
For the whitelisted source IP by FQDN (e.g. microsoft, Apple icloud etc), the result is intermittent - sometimes 200 and others 409... I have updated the "Aliases Hostnames Resolve Interval" to 60 sec. but still not resolved. Some input for resolution will be appreciated.
-
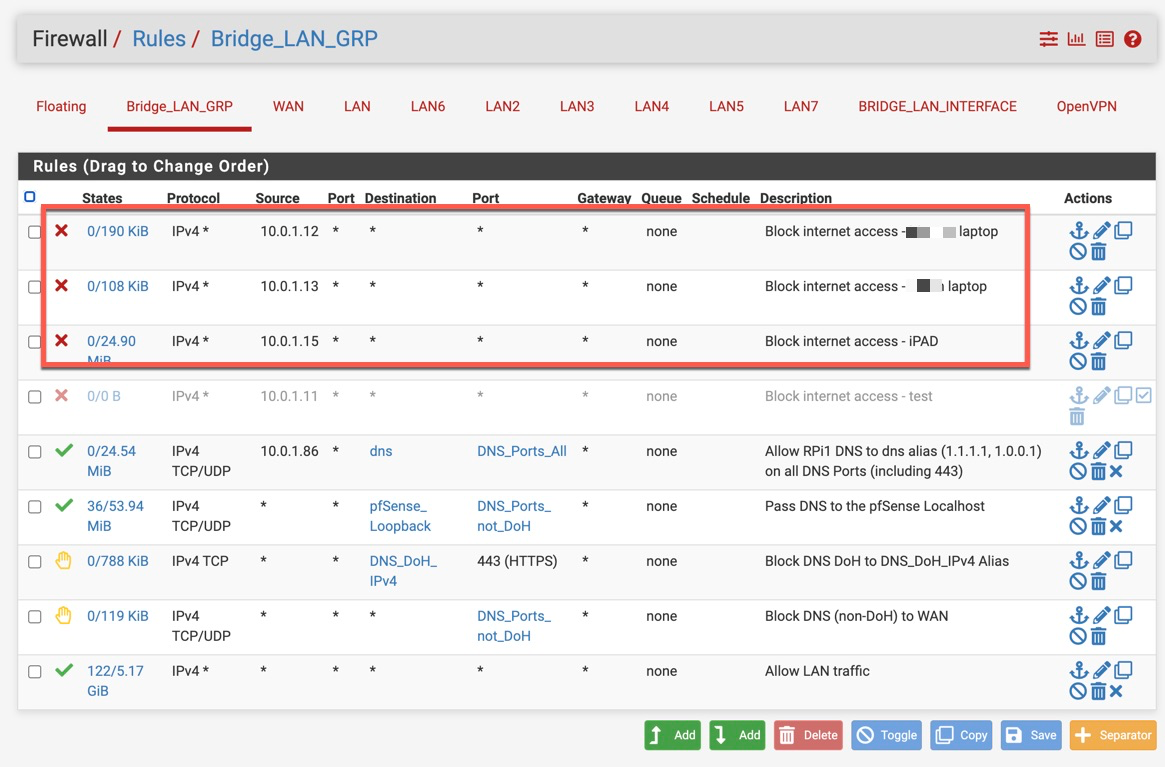
FW Blocking to WAN is no longer 100% effective, to the FQDNs on and off the source bypass list. For example, blocked clients can still search on google.com, play chess on chess.com, etc. See screenshot for the fw block rule below. I will have to reset fw states to block all outgoing traffic to WAN from those clients. @periko - can I get your input on this pls - any other options to effectively block client to WAN without fw state reset?
-
-
@dkzsys if you use Squid or Squidguard you can utilize regular expressions.
Some examples from my always splice file:
^((alt[0-9]-mtalk.)|(mtalk.)|(mtalk-(staging|dev).))google.com
^(((clients)[0-9])|accounts).google.(com|us)
^.*(outlook.)(office365|office).com
^(disney.(content|connections)).edge.bamgrid.com
Test and create them with a regular expressions tester online if needed.
-
@JonathanLee my understanding is that for the regex domain to work, squid will need to be set to explicit mode, or transparent mode with peek and splice config; and it doesn't work for transparent mode with Splice All. Happy to be corrected.
-
@dkzsys it should work if the domains are using .something else in it. Yes that is mostly used with SSL intercept
-
@dkzsys said in Squid Proxy "Bypass Proxy for These Destination IPs" Not Working?? Transparent HTTP Proxy Mode + HTTPS/SSL Interception:
- FW Blocking to WAN is no longer 100% effective, to the FQDNs on and off the source bypass list. For example, blocked clients can still search on google.com, play chess on chess.com, etc. See screenshot for the fw block rule below. I will have to reset fw states to block all outgoing traffic to WAN from those clients. @periko - can I get your input on this pls - any other options to effectively block client to WAN without fw state reset?
I just found out that I can use "pfctl -k" to reset fw sessions for specific client IPs via terminal. Since I am using CLI to toggle the blocking rules, it actually worked out well for me as a workaround - simply adding the extra command in the block rule CLI snippet.
-
@dkzsys said in Squid Proxy "Bypass Proxy for These Destination IPs" Not Working?? Transparent HTTP Proxy Mode + HTTPS/SSL Interception:
I just found out that I can use "pfctl -k" to reset fw sessions for specific client IPs via terminal. Since I am using CLI to toggle the blocking rules, it actually worked out well for me as a workaround - simply adding the extra command in the block rule CLI snippet.
Unfortunately killing the state for the client still doesn't block their traffic to WAN with the block rule enabled... Looking for an alternative workaround.
-
@dkzsys try this
client_persistent_connections on
client_persistent_connections off"Squid uses persistent connections (when allowed). You can use
this option to disable persistent connections with clients."http://www.squid-cache.org/Doc/config/client_persistent_connections/