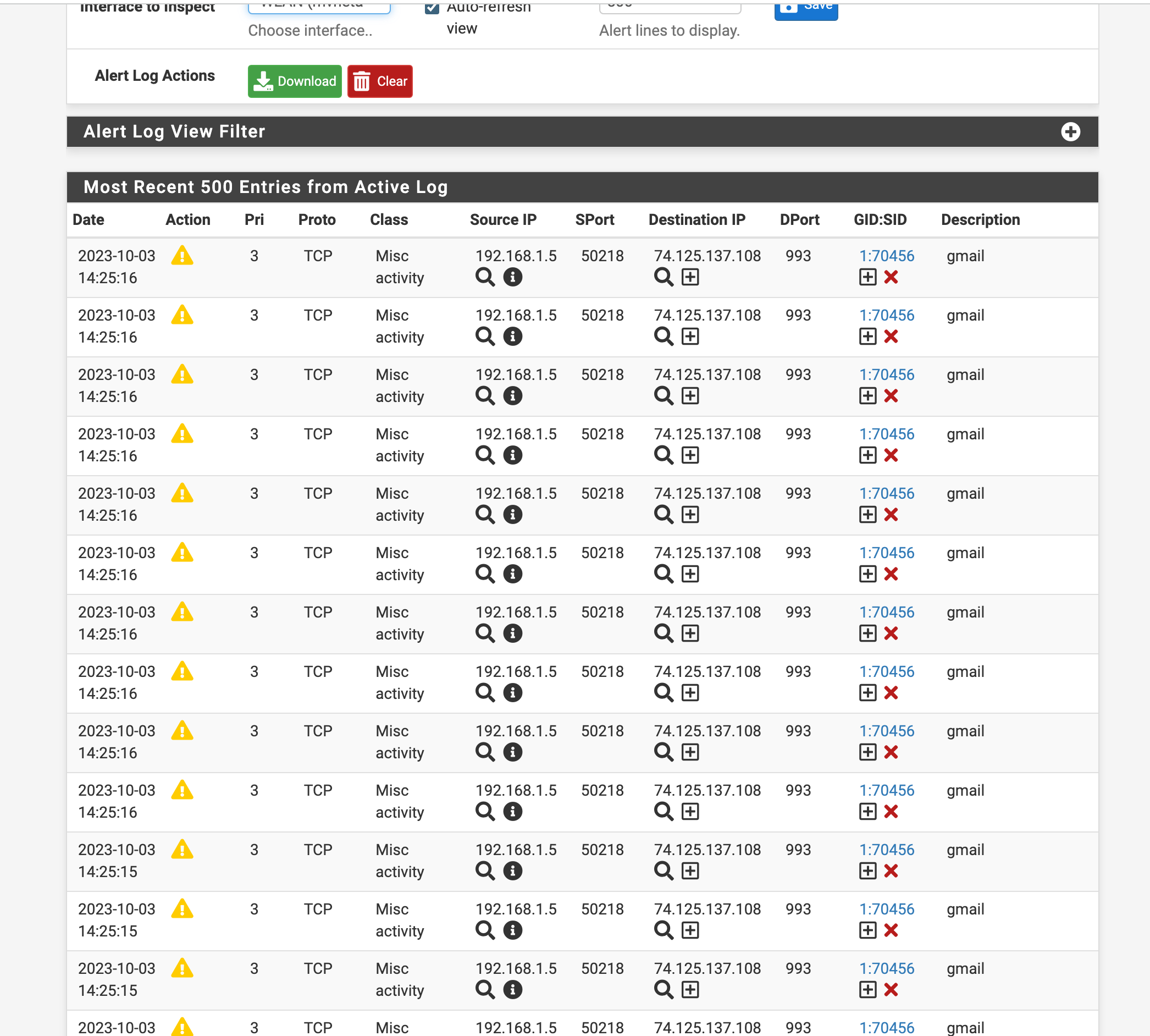
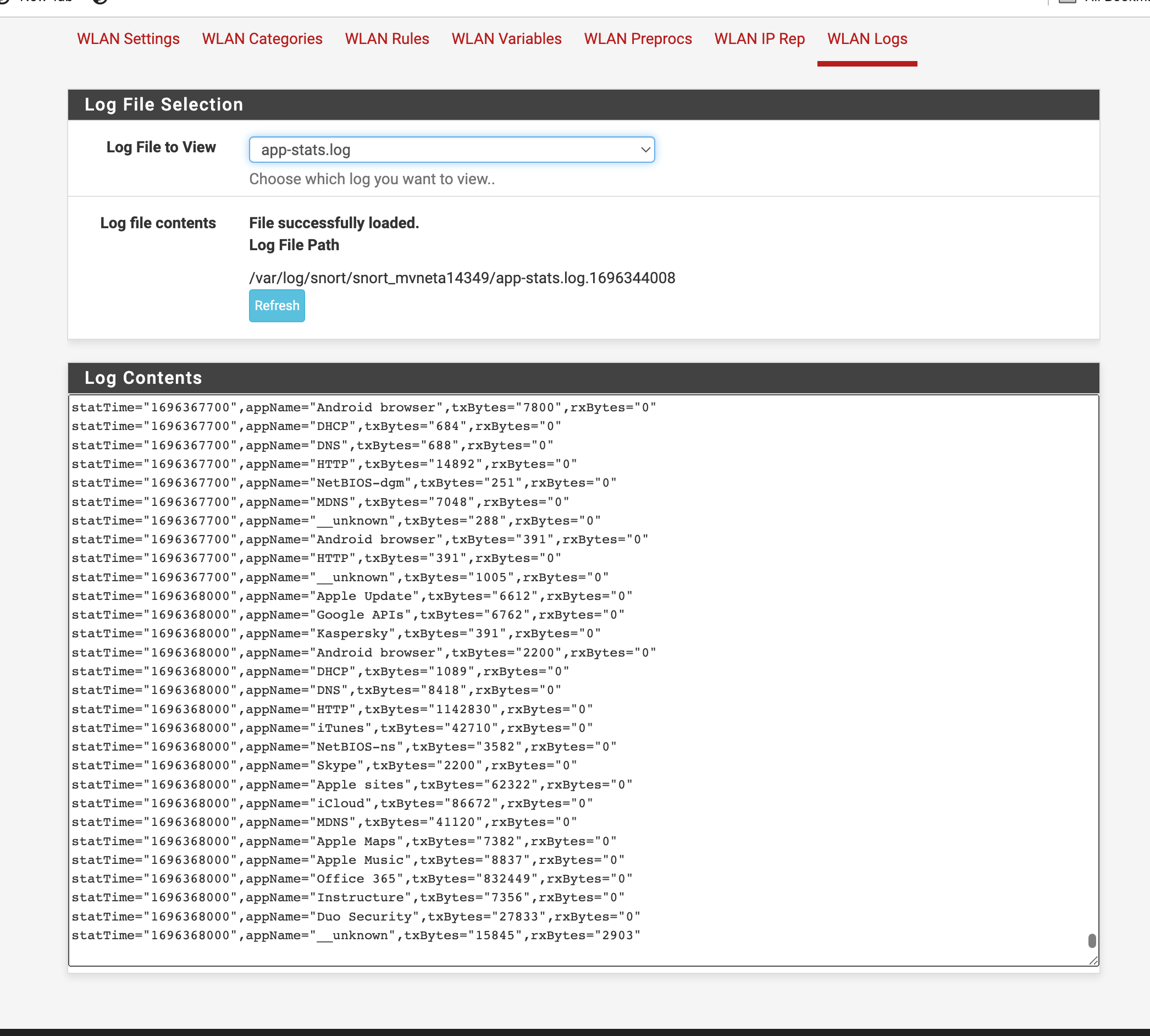
AppID alerts question
-
statTime="1696368600",appName="MSN",txBytes="3000",rxBytes="0" statTime="1696368600",appName="Chrome",txBytes="3000",rxBytes="0" statTime="1696368600",appName="DNS",txBytes="185",rxBytes="0" statTime="1696368600",appName="HTTP",txBytes="123401",rxBytes="0" statTime="1696368600",appName="iTunes",txBytes="19696",rxBytes="0" statTime="1696368600",appName="MDNS",txBytes="8394",rxBytes="0" statTime="1696368600",appName="Instructure",txBytes="10975",rxBytes="0" statTime="1696368600",appName="__unknown",txBytes="8703",rxBytes="0" statTime="1696368600",appName="Bing",txBytes="37181",rxBytes="0" statTime="1696368600",appName="Google",txBytes="4783",rxBytes="0" statTime="1696368600",appName="MSN",txBytes="29991",rxBytes="0" statTime="1696368600",appName="Android browser",txBytes="5748",rxBytes="0" statTime="1696368600",appName="Chrome",txBytes="110019",rxBytes="0" statTime="1696368600",appName="DHCP",txBytes="363",rxBytes="0" statTime="1696368600",appName="DNS",txBytes="773",rxBytes="0" statTime="1696368600",appName="HTTP",txBytes="135861",rxBytes="0" statTime="1696368600",appName="iTunes",txBytes="4999",rxBytes="0" statTime="1696368600",appName="LinkedIn",txBytes="2788",rxBytes="0" statTime="1696368600",appName="MDNS",txBytes="15112",rxBytes="0" statTime="1696368600",appName="Apple Music",txBytes="8026",rxBytes="0" statTime="1696368600",appName="Instructure",txBytes="4403",rxBytes="0" statTime="1696368600",appName="Google Inbox",txBytes="5748",rxBytes="0" statTime="1696368600",appName="__unknown",txBytes="60644",rxBytes="92" statTime="1696368900",appName="Android browser",txBytes="13181",rxBytes="0" statTime="1696368900",appName="Chrome",txBytes="2944",rxBytes="0" statTime="1696368900",appName="DNS",txBytes="969",rxBytes="0" statTime="1696368900",appName="Gmail",txBytes="13181",rxBytes="0" statTime="1696368900",appName="HTTP",txBytes="255810",rxBytes="0" statTime="1696368900",appName="iTunes",txBytes="12446",rxBytes="0" statTime="1696368900",appName="MDNS",txBytes="42590",rxBytes="0" statTime="1696368900",appName="Office 365",txBytes="214391",rxBytes="0" statTime="1696368900",appName="Instructure",txBytes="10750",rxBytes="0" statTime="1696368900",appName="__unknown",txBytes="10572",rxBytes="4824" statTime="1696368900",appName="McAfee",txBytes="433",rxBytes="0" statTime="1696368900",appName="HTTP",txBytes="13055",rxBytes="0" statTime="1696368900",appName="iTunes",txBytes="6078",rxBytes="0" statTime="1696368900",appName="NetBIOS-ns",txBytes="606",rxBytes="0" statTime="1696368900",appName="Apple sites",txBytes="3577",rxBytes="0" statTime="1696368900",appName="Apple Maps",txBytes="2967",rxBytes="0" statTime="1696368900",appName="__unknown",txBytes="70360",rxBytes="6556" statTime="1696369200",appName="DNS",txBytes="1341",rxBytes="0" statTime="1696369200",appName="HTTP",txBytes="285047",rxBytes="0" statTime="1696369200",appName="NetBIOS-dgm",txBytes="251",rxBytes="0" statTime="1696369200",appName="NetBIOS-ns",txBytes="790",rxBytes="0" statTime="1696369200",appName="iCloud",txBytes="56378",rxBytes="0" statTime="1696369200",appName="MDNS",txBytes="33974",rxBytes="0" statTime="1696369200",appName="Office 365",txBytes="213385",rxBytes="0" statTime="1696369200",appName="Instructure",txBytes="15284",rxBytes="0" statTime="1696369200",appName="__unknown",txBytes="15537",rxBytes="7167" statTime="1696368600",appName="Chrome",txBytes="137190",rxBytes="0" statTime="1696368600",appName="DNS",txBytes="403",rxBytes="0" statTime="1696368600",appName="HTTP",txBytes="137190",rxBytes="0" statTime="1696368900",appName="DNS",txBytes="1235",rxBytes="0" statTime="1696369200",appName="Google APIs",txBytes="7481",rxBytes="0" statTime="1696369200",appName="Google",txBytes="14107",rxBytes="0" statTime="1696369200",appName="Windows Live",txBytes="58841",rxBytes="0" statTime="1696369200",appName="Android browser",txBytes="117655",rxBytes="0" statTime="1696369200",appName="Chrome",txBytes="97811",rxBytes="0" statTime="1696369200",appName="DHCP",txBytes="363",rxBytes="0" statTime="1696369200",appName="DNS",txBytes="1137",rxBytes="0" statTime="1696369200",appName="HTTP",txBytes="270874",rxBytes="0" statTime="1696369200",appName="LinkedIn",txBytes="2854",rxBytes="0" statTime="1696369200",appName="Microsoft",txBytes="27781",rxBytes="0" statTime="1696369200",appName="MDNS",txBytes="34553",rxBytes="0" statTime="1696369200",appName="Microsoft Azure",txBytes="11598",rxBytes="0" statTime="1696369200",appName="Office 365",txBytes="48571",rxBytes="0" statTime="1696369200",appName="Instructure",txBytes="4318",rxBytes="0" statTime="1696369200",appName="__unknown",txBytes="2481",rxBytes="3741" statTime="1696369500",appName="Google",txBytes="2907",rxBytes="0" statTime="1696369500",appName="McAfee",txBytes="433",rxBytes="0" statTime="1696369500",appName="Chrome",txBytes="2907",rxBytes="0" statTime="1696369500",appName="DNS",txBytes="615",rxBytes="0" statTime="1696369500",appName="HTTP",txBytes="237491",rxBytes="0" statTime="1696369500",appName="MDNS",txBytes="20038",rxBytes="0" statTime="1696369500",appName="Office 365",txBytes="223135",rxBytes="0" statTime="1696369500",appName="Instructure",txBytes="11016",rxBytes="0" statTime="1696369500",appName="__unknown",txBytes="13402",rxBytes="0" statTime="1696368600",appName="Chrome",txBytes="696365",rxBytes="0" statTime="1696368600",appName="HTTP",txBytes="696365",rxBytes="0" statTime="1696369200",appName="__unknown",txBytes="4387",rxBytes="0" statTime="1696369500",appName="Google APIs",txBytes="61123",rxBytes="0" statTime="1696369500",appName="Chrome",txBytes="61123",rxBytes="0" statTime="1696369500",appName="DNS",txBytes="185",rxBytes="0" statTime="1696369500",appName="HTTP",txBytes="61123",rxBytes="0" statTime="1696369500",appName="MDNS",txBytes="24630",rxBytes="0" statTime="1696369500",appName="__unknown",txBytes="723516",rxBytes="610" statTime="1696369800",appName="DNS",txBytes="622",rxBytes="0" statTime="1696369800",appName="HTTP",txBytes="238658",rxBytes="0" statTime="1696369800",appName="NetBIOS-dgm",txBytes="491",rxBytes="0" statTime="1696369800",appName="NetBIOS-ns",txBytes="1158",rxBytes="0" statTime="1696369800",appName="MDNS",txBytes="1200",rxBytes="0" statTime="1696369800",appName="Office 365",txBytes="230067",rxBytes="0" statTime="1696369800",appName="Instructure",txBytes="8591",rxBytes="0" statTime="1696369800",appName="__unknown",txBytes="25620",rxBytes="0" statTime="1696369200",appName="HTTP",txBytes="35964",rxBytes="0" statTime="1696369200",appName="Office 365",txBytes="35964",rxBytes="0" statTime="1696369200",appName="__unknown",txBytes="6784",rxBytes="0" statTime="1696369800",appName="Google APIs",txBytes="9047",rxBytes="0" statTime="1696369800",appName="Google",txBytes="3525",rxBytes="0" statTime="1696369800",appName="Chrome",txBytes="188230",rxBytes="0" statTime="1696369800",appName="DNS",txBytes="498",rxBytes="0" statTime="1696369800",appName="HTTP",txBytes="197054",rxBytes="0" statTime="1696369800",appName="MDNS",txBytes="8210",rxBytes="0" statTime="1696369800",appName="Instructure",txBytes="6492",rxBytes="0" statTime="1696369800",appName="__unknown",txBytes="141551",rxBytes="10071" statTime="1696370100",appName="Bing",txBytes="4421",rxBytes="0" statTime="1696370100",appName="Google APIs",txBytes="2434",rxBytes="0" statTime="1696370100",appName="Chrome",txBytes="19961",rxBytes="0" statTime="1696370100",appName="DNS",txBytes="440",rxBytes="0" statTime="1696370100",appName="HTTP",txBytes="261238",rxBytes="0" statTime="1696370100",appName="MDNS",txBytes="8210",rxBytes="0" statTime="1696370100",appName="Office 365",txBytes="232555",rxBytes="0" statTime="1696370100",appName="Instructure",txBytes="8722",rxBytes="0" statTime="1696370100",appName="__unknown",txBytes="89160",rxBytes="0" statTime="1696370100",appName="Bing",txBytes="205111",rxBytes="0" statTime="1696370100",appName="Google APIs",txBytes="5739",rxBytes="0" statTime="1696370100",appName="Chrome",txBytes="161160",rxBytes="0" statTime="1696370100",appName="HTTP",txBytes="243976",rxBytes="0" statTime="1696370100",appName="Apple Maps",txBytes="3970",rxBytes="0" statTime="1696370100",appName="Instructure",txBytes="4332",rxBytes="0" statTime="1696370100",appName="__unknown",txBytes="121479",rxBytes="376" statTime="1696370400",appName="Google APIs",txBytes="2816",rxBytes="0" statTime="1696370400",appName="Chrome",txBytes="141702",rxBytes="0" statTime="1696370400",appName="DNS",txBytes="237",rxBytes="0" statTime="1696370400",appName="HTTP",txBytes="425023",rxBytes="0" statTime="1696370400",appName="NetBIOS-ns",txBytes="368",rxBytes="0" statTime="1696370400",appName="GitHub",txBytes="136818",rxBytes="0" statTime="1696370400",appName="MDNS",txBytes="1134",rxBytes="0" statTime="1696370400",appName="Office 365",txBytes="272441",rxBytes="0" statTime="1696370400",appName="Instructure",txBytes="10880",rxBytes="0" statTime="1696370400",appName="__unknown",txBytes="17218",rxBytes="4448" statTime="1696370100",appName="__unknown",txBytes="1285",rxBytes="2989" statTime="1696370400",appName="Chrome",txBytes="34223",rxBytes="0" statTime="1696370400",appName="HTTP",txBytes="34223",rxBytes="0" statTime="1696370400",appName="GitHub",txBytes="34223",rxBytes="0" statTime="1696370400",appName="__unknown",txBytes="20489",rxBytes="5236" statTime="1696370700",appName="DNS",txBytes="707",rxBytes="0" statTime="1696370700",appName="HTTP",txBytes="238089",rxBytes="0" statTime="1696370700",appName="NetBIOS-dgm",txBytes="251",rxBytes="0" statTime="1696370700",appName="MDNS",txBytes="16911",rxBytes="0" statTime="1696370700",appName="Office 365",txBytes="222825",rxBytes="0" statTime="1696370700",appName="Instructure",txBytes="15264",rxBytes="0" statTime="1696370700",appName="__unknown",txBytes="13978",rxBytes="765" statTime="1696370100",appName="HTTP",txBytes="19607",rxBytes="0" statTime="1696370100",appName="Office 365",txBytes="19607",rxBytes="0" statTime="1696370100",appName="__unknown",txBytes="6784",rxBytes="0" statTime="1696370700",appName="DNS",txBytes="263",rxBytes="0" statTime="1696370700",appName="HTTP",txBytes="9224",rxBytes="0" statTime="1696370700",appName="iCloud",txBytes="2720",rxBytes="0" statTime="1696370700",appName="MDNS",txBytes="8210",rxBytes="0" statTime="1696370700",appName="Instructure",txBytes="6504",rxBytes="0" statTime="1696370700",appName="__unknown",txBytes="29432",rxBytes="410" statTime="1696371000",appName="DNS",txBytes="168",rxBytes="0" statTime="1696371000",appName="HTTP",txBytes="230336",rxBytes="0" statTime="1696371000",appName="NetBIOS-ns",txBytes="368",rxBytes="0" statTime="1696371000",appName="Office 365",txBytes="215099",rxBytes="0" statTime="1696371000",appName="Instructure",txBytes="15237",rxBytes="0" statTime="1696371000",appName="__unknown",txBytes="5665",rxBytes="161" statTime="1696371000",appName="Google APIs",txBytes="3830",rxBytes="0" statTime="1696371000",appName="Chrome",txBytes="166046",rxBytes="0" statTime="1696371000",appName="HTTP",txBytes="166046",rxBytes="0" statTime="1696371000",appName="__unknown",txBytes="3208",rxBytes="1554" statTime="1696371300",appName="Google",txBytes="3952",rxBytes="0" statTime="1696371300",appName="Chrome",txBytes="8154",rxBytes="0" statTime="1696371300",appName="DNS",txBytes="507",rxBytes="0" statTime="1696371300",appName="HTTP",txBytes="256637",rxBytes="0" statTime="1696371300",appName="NetBIOS-dgm",txBytes="251",rxBytes="0" statTime="1696371300",appName="NetBIOS-ns",txBytes="460",rxBytes="0" statTime="1696371300",appName="Office 365",txBytes="228959",rxBytes="0" statTime="1696371300",appName="Instructure",txBytes="19524",rxBytes="0" statTime="1696371300",appName="__unknown",txBytes="6608",rxBytes="0" statTime="1696371000",appName="__unknown",txBytes="106644",rxBytes="0" statTime="1696371300",appName="Google APIs",txBytes="2666",rxBytes="0" statTime="1696371300",appName="Chrome",txBytes="49101",rxBytes="0" statTime="1696371300",appName="DNS",txBytes="341",rxBytes="0" statTime="1696371300",appName="HTTP",txBytes="49101",rxBytes="0" statTime="1696371300",appName="Yahoo! Mail",txBytes="1055",rxBytes="3812" statTime="1696371300",appName="IMAPS",txBytes="1055",rxBytes="3812" statTime="1696371300",appName="SSL client",txBytes="1055",rxBytes="3812" statTime="1696371300",appName="MDNS",txBytes="7048",rxBytes="0" statTime="1696371300",appName="__unknown",txBytes="106522",rxBytes="4726" statTime="1696371600",appName="Google",txBytes="6971",rxBytes="0" statTime="1696371600",appName="Chrome",txBytes="12068",rxBytes="0" statTime="1696371600",appName="DNS",txBytes="510",rxBytes="0" statTime="1696371600",appName="Google Analytics",txBytes="7412",rxBytes="0" statTime="1696371600",appName="HTTP",txBytes="1200057",rxBytes="0" statTime="1696371600",appName="CloudFront",txBytes="671459",rxBytes="0" statTime="1696371600",appName="Office 365",txBytes="218577",rxBytes="0" statTime="1696371600",appName="Instructure",txBytes="163934",rxBytes="0" statTime="1696371600",appName="__unknown",txBytes="7189",rxBytes="0" statTime="1696370700",appName="__unknown",txBytes="538",rxBytes="3077" statTime="1696371000",appName="HTTP",txBytes="26947",rxBytes="0" statTime="1696371000",appName="Office 365",txBytes="26947",rxBytes="0" statTime="1696371000",appName="__unknown",txBytes="6718",rxBytes="0" statTime="1696371600",appName="Chrome",txBytes="27829",rxBytes="0" statTime="1696371600",appName="DNS",txBytes="91",rxBytes="0" statTime="1696371600",appName="HTTP",txBytes="27829",rxBytes="0" statTime="1696371600",appName="MDNS",txBytes="8210",rxBytes="0" statTime="1696371600",appName="__unknown",txBytes="101399",rxBytes="1117" statTime="1696371900",appName="Google APIs",txBytes="78815",rxBytes="0" statTime="1696371900",appName="Chrome",txBytes="80883",rxBytes="0" statTime="1696371900",appName="DNS",txBytes="789",rxBytes="0" statTime="1696371900",appName="HTTP",txBytes="337188",rxBytes="0" statTime="1696371900",appName="NetBIOS-ns",txBytes="368",rxBytes="0" statTime="1696371900",appName="Office 365",txBytes="216253",rxBytes="0" statTime="1696371900",appName="Instructure",txBytes="40052",rxBytes="0" statTime="1696371900",appName="__unknown",txBytes="8595",rxBytes="161" statTime="1696371600",appName="__unknown",txBytes="817",rxBytes="0" statTime="1696371900",appName="Bing",txBytes="204428",rxBytes="0" statTime="1696371900",appName="Google APIs",txBytes="2185",rxBytes="0" statTime="1696371900",appName="MSN",txBytes="54676",rxBytes="0" statTime="1696371900",appName="Chrome",txBytes="288603",rxBytes="0" statTime="1696371900",appName="HTTP",txBytes="400339",rxBytes="0" statTime="1696371900",appName="NetBIOS-dgm",txBytes="251",rxBytes="0" statTime="1696371900",appName="NetBIOS-ns",txBytes="460",rxBytes="0" statTime="1696371900",appName="Apple Maps",txBytes="3780",rxBytes="0" statTime="1696371900",appName="Instructure",txBytes="4429",rxBytes="0" statTime="1696371900",appName="__unknown",txBytes="84710",rxBytes="9714" statTime="1696372200",appName="Google",txBytes="7069",rxBytes="0" statTime="1696372200",appName="MSN",txBytes="2934",rxBytes="0" statTime="1696372200",appName="Chrome",txBytes="39216",rxBytes="0" statTime="1696372200",appName="DNS",txBytes="435",rxBytes="0" statTime="1696372200",appName="HTTP",txBytes="276242",rxBytes="0" statTime="1696372200",appName="Office 365",txBytes="219901",rxBytes="0" statTime="1696372200",appName="Instructure",txBytes="15882",rxBytes="0" statTime="1696372200",appName="__unknown",txBytes="40047",rxBytes="0" statTime="1696372200",appName="Bing",txBytes="113251",rxBytes="0" statTime="1696372200",appName="Google APIs",txBytes="2665",rxBytes="0" statTime="1696372200",appName="Google",txBytes="3056",rxBytes="0" statTime="1696372200",appName="Chrome",txBytes="67078",rxBytes="0" statTime="1696372200",appName="DNS",txBytes="86",rxBytes="0" statTime="1696372200",appName="Google Analytics",txBytes="4182",rxBytes="0" statTime="1696372200",appName="HTTP",txBytes="138902",rxBytes="0" statTime="1696372200",appName="Google Adsense",txBytes="10648",rxBytes="0" statTime="1696372200",appName="MDNS",txBytes="6855",rxBytes="0" statTime="1696372200",appName="Google ads",txBytes="2156",rxBytes="0" statTime="1696372200",appName="__unknown",txBytes="24753",rxBytes="4195" statTime="1696372500",appName="Amazon",txBytes="6328",rxBytes="0" statTime="1696372500",appName="Google APIs",txBytes="9427",rxBytes="0" statTime="1696372500",appName="Android browser",txBytes="20910",rxBytes="0" statTime="1696372500",appName="DNS",txBytes="1103",rxBytes="0" statTime="1696372500",appName="HTTP",txBytes="252573",rxBytes="0" statTime="1696372500",appName="MDNS",txBytes="2694",rxBytes="0" statTime="1696372500",appName="Office 365",txBytes="222675",rxBytes="0" statTime="1696372500",appName="Instructure",txBytes="8988",rxBytes="0" statTime="1696372500",appName="Google Inbox",txBytes="5155",rxBytes="0" statTime="1696372500",appName="__unknown",txBytes="26304",rxBytes="0"I did notice "unknown" tends to show lots of rxBytes. Yahoo and SSL lines show RX maybe it only matches the rxBytes as an alert?
statTime="1696371300",appName="Yahoo! Mail",txBytes="1055",rxBytes="3812" statTime="1696371300",appName="IMAPS",txBytes="1055",rxBytes="3812" statTime="1696371300",appName="SSL client",txBytes="1055",rxBytes="3812" -
I just noticed the update for alerts tab.
I just installed it thank you !!!
-
I forgot I have to add the custom rules for the text that is not mapped over yet right? Starting at 1000000. I also found one to detect and alert on ChatGPT :)
alert ip $HOME_NET any -> $EXTERNAL_NET any (msg:"iTunes";flow:from_client;appid:itunes; sid:1000000 ; classtype:misc-activity; rev:1;) alert ip $HOME_NET any -> $EXTERNAL_NET any (msg:"iCloud";flow:from_client;appid:icloud; sid:1000001 ; classtype:misc-activity; rev:1;) alert ip $HOME_NET any -> $EXTERNAL_NET any (msg:"LinkedIn";flow:from_client;appid:linkedin; sid:1000002 ; classtype:misc-activity; rev:1;) alert ip $HOME_NET any -> $EXTERNAL_NET any (msg:"ChatGPT";flow:from_client;appid:chatgpt; sid:1000003 ; classtype:misc-activity; rev:1;)With the help of . . . /usr/local/etc/snort/appid/odp/appMapping.data
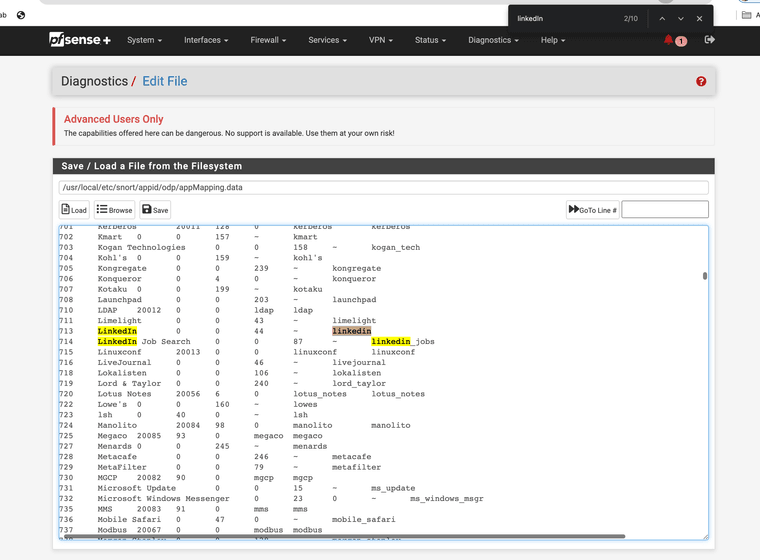
-
@JonathanLee said in AppID alerts question:
I forgot I have to add the custom rules for the text that is not mapped over yet right? Starting at 1000000. I also found one to detect and alert on ChatGPT :)
Yes, you will possibly need to create your own supplemental AppID text rules for some of the newer AppID stubs in the updates that come down from the Snort Vulnerability Research Team.
Remember that the AppID text rules package is a very old variant created by University volunteers several years ago. It has not been maintained, so that means it will lack the necessary rules for some of the newer apps. There were also a few typos in some app names in those rules (or else the Snort VRT changed the names slightly since the text rules were developed).
-
The one big shortcoming of OpenAppID is the dearth of available and maintained text rules that must be used with the stub detectors. Without matching text rules for each AppID stub detector, there will be no alerts.
Much like lists of IP addresses that must be created and maintained for known bad actor and poor reputation blocking, you must have someone creating and maintaining the associated text rules for OpenAppID to work corrrectly in Snort. It's these associated text rules that are not being maintained, and thus OpenAppID loses some of its usefulness because without the text rules you will not get alerts for some application traffic. But maintaining such a collection of rules is labor intensive and nobody wants to do it for free. As of yet, I have not located an available package of OpenAppID text rules that is current and maintained.
Users are certainly free to create their own custom OpenAppID text rules to match up with all the available detector stubs provided by the Snort VRT, but that takes a good bit of effort.
-
@bmeeks I did try Bill. I dont know if you remember but we had a talk about this maybe a year or two ago.
To keep the list current i compared what was in here https://appid.cisco.com/home and seeing if there was a corresponding text ruleI created maybe 200 and then stopped. Its an impossible task if it's one person. This is why this is a paid service from other vendors. There is no way to keep on top of writing text rules with new appids without some level of automation or a team for oversight.
-
@michmoor This could be fully automated with use of /usr/local/etc/snort/appid/odp/appMapping.data for iterations. Make a string in java and iterate for lower case strings add all the rules at once. It is really easy to code it with java. I will download the file and do a one time conversion to a new text file to add to custom but it will be huge. It may take some time but I have a good idea on how to do this with Java's scanner object now that I understand it. Only took me a couple years.
Here is a nice reference:
https://forum.netgate.com/topic/183210/guide-snort-s-appid-custom-rules-quick-guide-to-blocking-example-shows-openai-chatgpt-or-itunes
-
@michmoor said in AppID alerts question:
Its an impossible task if it's one person. This is why this is a paid service from other vendors. There is no way to keep on top of writing text rules with new appids without some level of automation or a team for oversight.
100% agree with this sentiment. But apparently vendors do not sense a wide level of interest/desire for this kind of product and thus no promise of a revenue stream large enough to fund the effort and produce some amount of profit.
This is one of the reasons I've become sort of soured on Snort. Not "soured" in a bad way, but rather because there is no active support and interest in its most distinguishing feature (when comparing Snort to Suricata): OpenAppID. Without OpenAppID, Snort really trails Suricata due to Suricata's multithreaded nature and its extensive logging options.
-
@bmeeks said in AppID alerts question:
This is one of the reasons I've become sort of soured on Snort. Not "soured" in a bad way, but rather because there is no active support and interest in its most distinguishing feature (when comparing Snort to Suricata): OpenAppID. Without OpenAppID, Snort really trails Suricata due to Suricata's multithreaded nature and its extensive logging options.
I get what you're saying completely. There's potential there but not a lot of commitment to bettering the product.
Until there is functional and automated way of writing these rules and importantly categorizing the apps and text rules correctly its difficult to recommend OpenAppID as is. -
@JonathanLee Your solution doesn't take into account categorizing the apps as well which is a huge undertaking and arguably the hardest part.
-
Here is, the fully converted appMapping.data to text file...
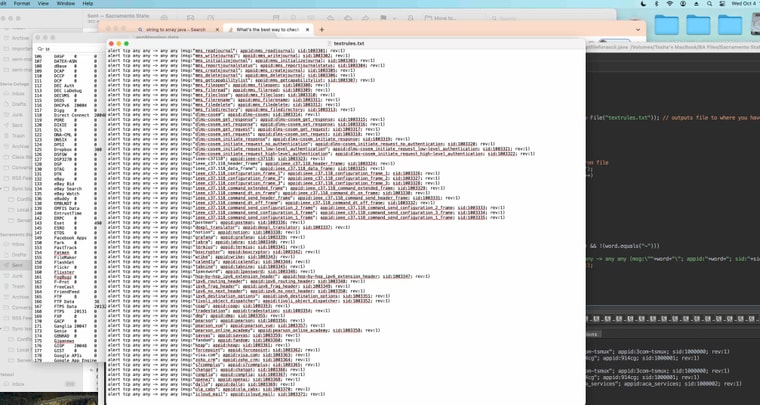
The pfSense Snort AppID de-cipher sorcerer's code file: --> textrules.txt
Sid range: 1000000 - 1003371
Total 3,371 AppID rules you can use with the custom option.
I converted it with a Java program I just made. The message is the same as the appid match it makes it easier.
Some of the ieee items are bigger but they seem to match.