Can't ping WAN2 from ouside when WAN1 is the default
-
I have 2 VPNs configured:
VPN1 Interface WAN1 (FIOS)
VPN2 Interface WAN2 (COMCAST)I can't ping WAN2 from outside when I capture the packet; I see that the ping going through the WAN1.
10:54:51.362239 IP WAN2 > 1.1.1.1: ICMP echo request, id 53438, seq 13147, length 9
10:54:51.373302 IP 1.1.1.1 > WAN2: ICMP echo reply, id 53438, seq 13147, length 9
10:54:51.863503 IP WAN2> 1.1.1.1: ICMP echo request, id 53438, seq 13148, length 9
10:54:51.873165 IP 1.1.1.1 > WAN2: ICMP echo reply, id 53438, seq 13148, length 9
10:54:52.348666 IP 68.183.62.218 > WAN2: ICMP echo request, id 4234, seq 1, length 64
10:54:52.359295 IP WAN1 > WAN2: ICMP host 68.183.62.218 unreachable - admin prohibited filter, length 36 -
@fgenao
Did you allow the ICMP access with a floating rule or with one on an interface group?
This won't work. You would have to remove such rules.You have to define pass rule on each WAN interface separately instead.
-
Thanks @viragomann
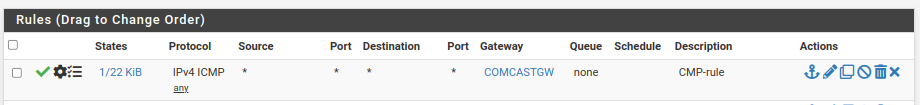
Here is what I got on the WAN2 Interface rule:
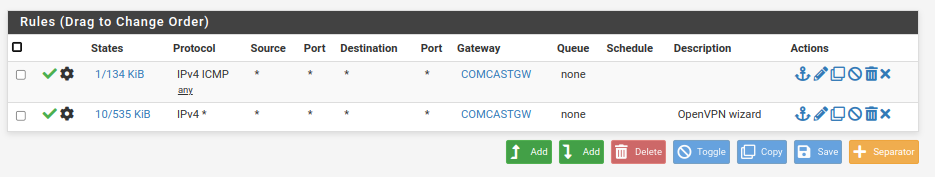
-
@fgenao
The rule on the interface is fine, but are you sure, that it is applied to the incoming ICMP request?Simple test: Edit the ICMP rule, state a unique description and enable the logging. Try a ping and check the log then.
-
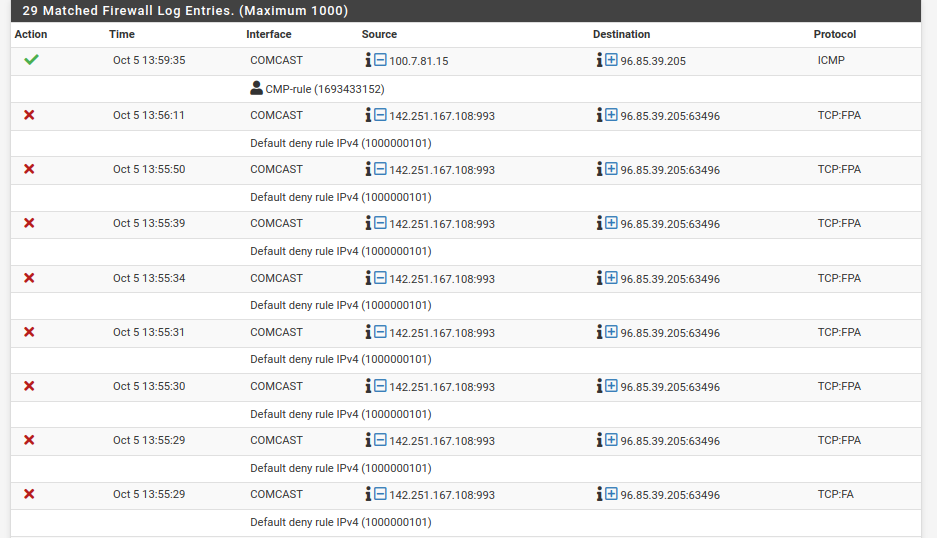
@viragomann here is what I get on the log:
-
@fgenao
Enable the displaying of the rule descriptions in the log settings to get the information. -
-
@fgenao
So the rule in question is obviously applied. But on which rule tab is it defined? The screenshots do not show this.
And what is the COMGASTGW gateway? I don't expect any gateway setting on a rule for passing incoming traffic. -
-
@fgenao
As mentioned, there should not be a gateway stated in inbound rules.
With this pfSense redirects the packets to this gateway. This might not be, what you intend. -
Thank you for your help, it is working now.