-
Hi,
I did check the health of my Let's Encrypt SSL certificate with ssllabs.com and the result shows some weak SSL cipher used:
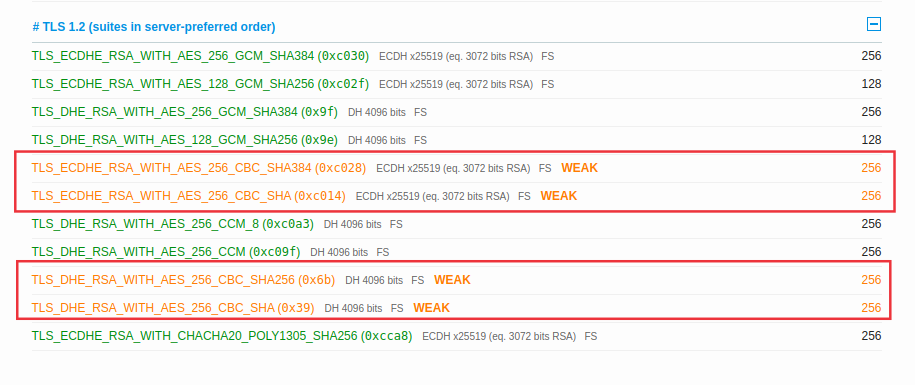
any idea how to disable the weak cipher on pfsense?
-
@moelharrak you have your pfsense web gui open to the public internet? That doesn't seem like a good idea..
What version are you running?
I don't show those being listed
[23.05.1-RELEASE][admin@sg4860.local.lan]/root: cat /etc/inc/system.inc | grep nginx_config system_generate_nginx_config("{$g['varetc_path']}/nginx-webConfigurator.conf", function system_generate_nginx_config($filename, echo "system_generate_nginx_config() being called $mt\n"; $nginx_config = <<<EOD $nginx_config .= "error_log /dev/null;\n"; $nginx_config .= "error_log syslog:server=unix:/var/run/log,facility=local5;\n"; $nginx_config .= <<<EOD $nginx_config .= "\tlimit_conn_zone \$binary_remote_addr zone=addr:10m;\n"; $nginx_config .= "\tkeepalive_timeout 0;\n"; $nginx_config .= "\tkeepalive_timeout 75;\n"; $nginx_config .= "\n"; $nginx_config .= "\tserver {\n"; $nginx_config .= "\t\tlisten {$nginx_port} ssl http2;\n"; $nginx_config .= "\t\tlisten [::]:{$nginx_port} ssl http2;\n"; $nginx_config .= "\n"; $nginx_config .= "\t\tssl_certificate {$g['varetc_path']}/{$cert_location};\n"; $nginx_config .= "\t\tssl_certificate_key {$g['varetc_path']}/{$key_location};\n"; $nginx_config .= "\t\tssl_session_timeout 10m;\n"; $nginx_config .= "\t\tkeepalive_timeout 70;\n"; $nginx_config .= "\t\tssl_session_cache shared:SSL:10m;\n"; $nginx_config .= "\t\tssl_protocols TLSv1.1 TLSv1.2 TLSv1.3;\n"; $nginx_config .= "\t\tssl_protocols TLSv1.2 TLSv1.3;\n"; $nginx_config .= "\t\tssl_ciphers \"EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305\";\n"; $nginx_config .= "\t\tssl_prefer_server_ciphers on;\n"; $nginx_config .= "\t\tadd_header Strict-Transport-Security \"max-age=31536000\";\n"; $nginx_config .= "\t\tadd_header X-Content-Type-Options nosniff;\n"; $nginx_config .= "\t\tssl_session_tickets off;\n"; $nginx_config .= "\t\tssl_dhparam /etc/dh-parameters.4096;\n"; $nginx_config .= "\t\tssl_stapling on;\n"; $nginx_config .= "\t\tssl_stapling_verify on;\n"; $nginx_config .= "\t\tresolver " . implode(" ", get_dns_nameservers(true)) . " valid=300s;\n"; $nginx_config .= "\t\tresolver_timeout 5s;\n"; $nginx_config .= "\n"; $nginx_config .= "\tserver {\n"; $nginx_config .= "\t\tlisten {$nginx_port};\n"; $nginx_config .= "\t\tlisten [::]:{$nginx_port};\n"; $nginx_config .= <<<EOD $nginx_config .= <<<EOD $nginx_config .= <<<EOD $nginx_config .= <<<EOD $nginx_config .= " # Plugin Servers ({$pkgname})\n"; $nginx_config .= "{$server}\n"; $nginx_config .= "}\n"; printf(gettext('Error: cannot open %1$s in system_generate_nginx_config().%2$s'), $filename, "\n"); fwrite($fd, $nginx_config); [23.05.1-RELEASE][admin@sg4860.local.lan]/root:$nginx_config .= "\t\tssl_ciphers "EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305";\n";
I just ran a sslscan and not seeing any cbc
Supported Server Cipher(s): Preferred TLSv1.3 256 bits TLS_AES_256_GCM_SHA384 Curve 25519 DHE 253 Accepted TLSv1.3 256 bits TLS_CHACHA20_POLY1305_SHA256 Curve 25519 DHE 253 Accepted TLSv1.3 128 bits TLS_AES_128_GCM_SHA256 Curve 25519 DHE 253 Preferred TLSv1.2 256 bits ECDHE-RSA-AES256-GCM-SHA384 Curve 25519 DHE 253 Accepted TLSv1.2 128 bits ECDHE-RSA-AES128-GCM-SHA256 Curve 25519 DHE 253 Accepted TLSv1.2 256 bits DHE-RSA-AES256-GCM-SHA384 DHE 4096 bits Accepted TLSv1.2 128 bits DHE-RSA-AES128-GCM-SHA256 DHE 4096 bits Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA384 Curve 25519 DHE 253 Accepted TLSv1.2 256 bits ECDHE-RSA-AES256-SHA Curve 25519 DHE 253 Accepted TLSv1.2 256 bits DHE-RSA-AES256-CCM8 DHE 4096 bits Accepted TLSv1.2 256 bits DHE-RSA-AES256-CCM DHE 4096 bits Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA256 DHE 4096 bits Accepted TLSv1.2 256 bits DHE-RSA-AES256-SHA DHE 4096 bits Accepted TLSv1.2 256 bits ECDHE-RSA-CHACHA20-POLY1305 Curve 25519 DHE 253 Server Key Exchange Group(s): TLSv1.3 128 bits secp256r1 (NIST P-256) TLSv1.3 192 bits secp384r1 (NIST P-384) TLSv1.3 260 bits secp521r1 (NIST P-521) TLSv1.3 128 bits x25519 TLSv1.3 224 bits x448 TLSv1.2 128 bits secp256r1 (NIST P-256) TLSv1.2 192 bits secp384r1 (NIST P-384) TLSv1.2 260 bits secp521r1 (NIST P-521) TLSv1.2 128 bits x25519 TLSv1.2 224 bits x448 SSL Certificate: Signature Algorithm: sha256WithRSAEncryption RSA Key Strength: 2048 Subject: sg4860.local.lan Altnames: DNS:sg4860.local.lan, DNS:pfsense.local.lan, IP Address:192.168.9.253 Issuer: home-ca Not valid before: Dec 12 10:39:23 2017 GMT Not valid after: Dec 10 10:39:23 2027 GMThttps://github.com/rbsec/sslscan
edit: so showing with iana names..
Supported Server Cipher(s): Preferred TLSv1.3 256 bits TLS_AES_256_GCM_SHA384 Curve 25519 DHE 253 Accepted TLSv1.3 256 bits TLS_CHACHA20_POLY1305_SHA256 Curve 25519 DHE 253 Accepted TLSv1.3 128 bits TLS_AES_128_GCM_SHA256 Curve 25519 DHE 253 Preferred TLSv1.2 256 bits TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 Curve 25519 DHE 253 Accepted TLSv1.2 128 bits TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 Curve 25519 DHE 253 Accepted TLSv1.2 256 bits TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 DHE 4096 bits Accepted TLSv1.2 128 bits TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 DHE 4096 bits Accepted TLSv1.2 256 bits TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 Curve 25519 DHE 253 Accepted TLSv1.2 256 bits TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA Curve 25519 DHE 253 Accepted TLSv1.2 256 bits TLS_DHE_RSA_WITH_AES_256_CCM_8 DHE 4096 bits Accepted TLSv1.2 256 bits TLS_DHE_RSA_WITH_AES_256_CCM DHE 4096 bits Accepted TLSv1.2 256 bits TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 DHE 4096 bits Accepted TLSv1.2 256 bits TLS_DHE_RSA_WITH_AES_256_CBC_SHA DHE 4096 bits Accepted TLSv1.2 256 bits TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 Curve 25519 DHE 253Those do seem to be listed..
you could edit the system.inc to only use the ciphers you want.. Just keep in mind that that would get overwritten on an update.
I think an edit with !SHA1:!SHA256:!SHA384 could prevent the cbc ciphers... Man its been long time since I played with this sort of stuff ;) I don't know if I would go around editing system.inc directly though. A good feature request might to easy edit ciphers in the gui.. To be honest prob best to just disable tls 1.2 completely.. That prob be a safer edit.
edit2: ok simple edit to not do tls 1.2 at all, and now those bad weak ciphers are gone ;)
$ sslscan.exe --iana-names 192.168.9.253:8443 Version: 2.1.1 Windows 64-bit (Mingw) OpenSSL 3.0.9 30 May 2023 Connected to 192.168.9.253 Testing SSL server 192.168.9.253 on port 8443 using SNI name 192.168.9.253 SSL/TLS Protocols: SSLv2 disabled SSLv3 disabled TLSv1.0 disabled TLSv1.1 disabled TLSv1.2 disabled TLSv1.3 enabled TLS Fallback SCSV: Server supports TLS Fallback SCSV TLS renegotiation: Session renegotiation not supported TLS Compression: Compression disabled Heartbleed: TLSv1.3 not vulnerable to heartbleed Supported Server Cipher(s): Preferred TLSv1.3 256 bits TLS_AES_256_GCM_SHA384 Curve 25519 DHE 253 Accepted TLSv1.3 256 bits TLS_CHACHA20_POLY1305_SHA256 Curve 25519 DHE 253 Accepted TLSv1.3 128 bits TLS_AES_128_GCM_SHA256 Curve 25519 DHE 253 Server Key Exchange Group(s): TLSv1.3 128 bits secp256r1 (NIST P-256) TLSv1.3 192 bits secp384r1 (NIST P-384) TLSv1.3 260 bits secp521r1 (NIST P-521) TLSv1.3 128 bits x25519 TLSv1.3 224 bits x448 SSL Certificate: Signature Algorithm: sha256WithRSAEncryption RSA Key Strength: 2048 Subject: sg4860.local.lan Altnames: DNS:sg4860.local.lan, DNS:pfsense.local.lan, IP Address:192.168.9.253 Issuer: home-ca Not valid before: Dec 12 10:39:23 2017 GMT Not valid after: Dec 10 10:39:23 2027 GMTJust edited the else
$nginx_config .= "\t\tssl_protocols TLSv1.2 TLSv1.3;\n";
Since not using captive portal anyway, to
$nginx_config .= "\t\tssl_protocols TLSv1.3;\n";I still wouldn't recommending exposing your gui to the public.. And if your going to edit system.inc, I would highly suggest make a copy just in case you typo something that breaks something..
BTW, moved this to the web gui section, this has really nothing to do with acme.
-
 J johnpoz moved this topic from ACME on
J johnpoz moved this topic from ACME on
-
@johnpoz thank you for your quick reply.
I agree that it's not safe to open web GUI to the public internet but I need that for now to accede my firewall from anywhere, Will stop that later after configuring VPN.
my version is 2.7.0.
Ok I will try to disable tls1.2 and keep only 2.3
Thank you -
@moelharrak if your gui is not exposed, ie once you get your vpn working - what does it matter really about old ciphers?
The only devices that should ever talk to your gui is your admin devices. I wouldn't be too concerned if old cipher is available.. If you were serving some web service open to the public, then ok, etc. But a web gui that only admins ever can even access..
-
But now firewall is still exposed that why I wanted to disable the weak ciphers. and I wasn't planing to configure VPN right away.
-
@moelharrak you never responded on which version you are running. John shows that those weak ciphers aren’t present on the latest OS
Edit. You’re on 2.7
I’m not sure there is a way to disable weak ciphers. A complex workaround would be to have your own domainnname and use Cloudflare l. That way CF being able he reverse proxy to your pfsense you can be certain that those ciphers wouldn’t be present and you can create an ACL for your WAN that only permits CF addresses…
Honestly it’s just a workaround that’s meaningless but I figured I’d bring it up.
Use Tailscale in the interim -
@moelharrak said in Disable weak SSL Cipher:
But now firewall is still exposed
To the public - or your specific IP only? Getting rid of those weak ciphers are not going to lower your exposure risk.. The issues with those weak ciphers has little to do with someone logging into your gui - doesn't matter what cipher is used, etc.
Its not like oh cipher X we can just login, and oh your using cipher Y can't log in.. The security implications of a weak cipher really has little to do with the overall exposure of your gui to the public.
You using only what is considered good secure ciphers is not going to make you more secure to someone being able to access your gui from the public internet.
-
@johnpoz 100%
Having strong ciphers does not prevent anyone from guessing your password. It protects data in transit but I can still hit your port….i can still brute force attempt… -
@michmoor said in Disable weak SSL Cipher:
John shows that those weak ciphers aren’t present on the latest OS
No they are.. I just didn't notice them as being cbc until I set my tool to report in iana names. But to be honest its really a minor concern if one at all. The only devices that should ever talk to the web gui are admin devices in the first place. Proper security would allow only an admin network or admin IP to talk to the gui..
I would never even think to expose my web gui to the public internet in the first place.. So scanning from an external tool like ssl labs should never even be viable to do.
Which is why I scanned using a local tool to report what ciphers are being offered. While I agree there is little point in even offering old ciphers.. I have now set mine to only use tls 1.3 currently. I would never need or want to access from my admin machine with old tls 1.2 etc.. But to be honest its pretty pointless, other than just good practice.
If you were setup securely - accessing the gui via just http shouldn't be a problem..
Once you exposed the gui to public or some other hostile local network - the use of some old cipher via old tls 1.2 should be the least of your concerns.
All that being said, I do agree that it would be a good feature add to allow for tweaking and setting what you want to offer specifically be it via the normal web gui, or some captive portal your running on pfsense. Normal users would prob never have need to adjust, but it would be nice feature.. Maybe let the user select modern ciphers, more compatible ciphers for older browsers, etc. Or full custom settings where user could pick exactly which ciphers are offered.
This sort of granular control should also be available for ssh as well. When I looked earlier redmine was down, when it comes back I might look to see if these features have been requested already, if not maybe I will put them in. Of very low priority request - but it would be nice to have.
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.