Firewall rules with Wireguard VPN active
-
None of my firewall rules work when the VPN tunnel is active. I am trying to create some policy-based routes on the LAN interface so that certain local devices go direct to the WAN instead of through the tunnel.
The firewall logs show that the rules are not being applied.
Is this a known bug?
-
@hspindel Can you show your firewall rules? Might be a config issue.
-
@paoloposo said in Firewall rules with Wireguard VPN active:
@hspindel Can you show your firewall rules? Might be a config issue.
There does not seem to be a way to attach an image in this forum.
An example of one of the LAN rules is:
https://www.dropbox.com/scl/fi/yy26d37acmoq9a0b6ejsn/Screenshot-2023-10-15-at-17-11-08-firewall.sci1.com-Firewall-Rules-Edit.png?rlkey=7qvz2sy4al9wfz4ca6780rtly&dl=0
This rule is supposed to route from source tivoPremiere (192.1.1.242) to the WAN even when the Wireguard tunnel is in use. Despite the presence of this rule, the source is still routed via the tunne.
-
FYI you can attach an image, just copy and paste it and it will work, or click the "upload image" icon which is near the end of the toolbar.
Anyway, as for this issue, I think we need a bit more info to understand exactly what is going on. Do you have a Wireguard VPN setup that is being used as WAN for most things or something? Or are you connecting via Wireguard as a remote client and then need to get out the WAN from there? Or is this a site to site setup?
Yeah I think more info will help us get to the bottom of this faster.
I can definitely say that there are know bugs I'm aware of around this though, I have plenty of WireGuard setups and haven't had any issues with firewall rules not working/being ignored.
-
Okay, thank you for the reply. To answer your questions...
I am using Wireguard as a client connecting to Windscribe's VPN service. The goal is to run a full-time VPN for all of my local devices. I had this working fine on a DD-WRT router, so the issue has to be in my configuration of pfSense.
I am running pfSense+ on a Netgate 8200.
With the VPN tunnel up, I am able to access nearly any website, so the VPN is working. whatsmyip.com reports the address of the VPN endpoint instead of my usual ISP's address, so I am confident the VPN is operating. Plus the pfSense Wireguard status shows the tunnel handshaking.
The issue is that for a couple websites, I need to bypass the VPN and go directly out the WAN. Note that both of the affected websites below work fine when the VPN is inactive.
- instacart.com blocks access if one tries to access it through a VPN (I hate websites that do this to yoo!). So I created LAN firewall rules to route any instacart IP destination direct to the WAN. I looked up all the available instacart IPs using nslookup. An example instacart firewall rule is:
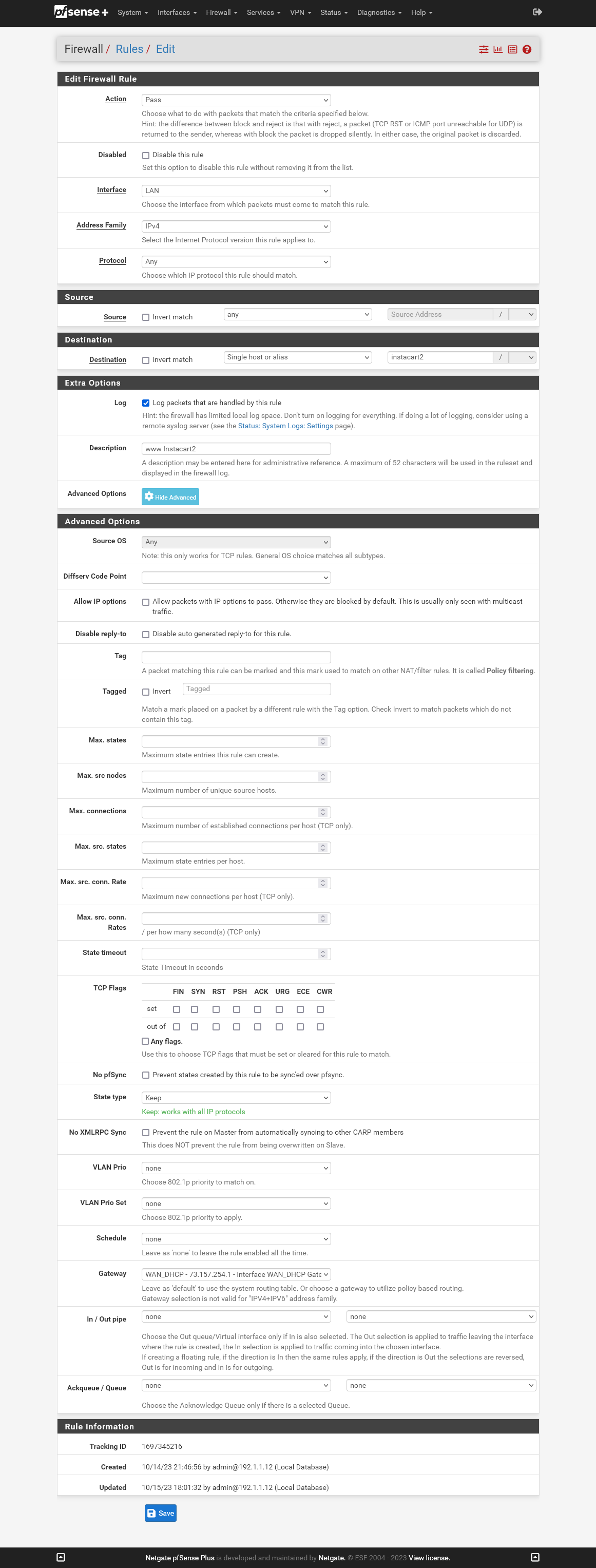
- My Tivos do not operate properly if the VPN is active. They say they cannot access their Tivo services, but unfortunately provide no clues about what or why they are trying to access. With the DD-WRT router, the Tivos worked if I established a rule that used to the Tivo as a source address, anything as a destination, and default route through the WAN.
An example Tivo firewall rule was linked in my previous post.
pfSense behaves very much like LAN firewall rules I've created are ignored when the VPN is active. As a test, I created a LAN rule which routed everything through the WAN. whatsmyip.com still told me that my IP was the VPN IP, so this test rule was ignored.
I have tried rebooting the router after applying firewall rules in hopes that that would reset something important, but it was of no help. Since I was able to get this working with a DD-WRTE router, I am reasonably confident that this is a routing issue with pfSense.
I appreciate any help you can provide.
-
@hspindel Thanks for the info here, do you mind screenshotting your LAN firewall rules as well? Things look correct for these rules, I'd also be curious to see the alias you have setup though, are you just using the domains in the alias here?
I've definitely done some policy routing very similar to this and it worked as expected, or at least mostly, the only thing is a lot of services use random domains that you might not expect, for example I was trying to route specific sites over a VPN and this only worked partially.
Either way though if your rule that is supposed to route everything out the main WAN gateway isn't working, then something seems off here.
-
There's a lot of rules. I'm only going to post the two most relevant rules. I've tried disabling all the others, so I know they don't interfere. The point of the posted rules is for my Tivos to bypass the VPN.
You are correct that it's possible I have not attempted route all the IPs that instacart uses. I routed the IPs I could find using nslookup. But, as I said, these are now disabled and shouldn't factor into our discussion.
With the below rules, it does not appear that the Tivos are routed through the WAN, but still go through the VPN (which doesn't work). Also as I mentioned I tried a rule to route everything through the WAN and it didn't work (last rule posted below). I made sure the allow everything rule was first in the list of rules so it had the highest precedence. It's like all LAN rules are ignored when the VPN is up. But my firewall logs show that the allow anything rule triggered and allowed passage of data.
With the allow anything rule active, whatsmyip.com still shows my VPN IP, not my usual ISP IP.
Aliases:
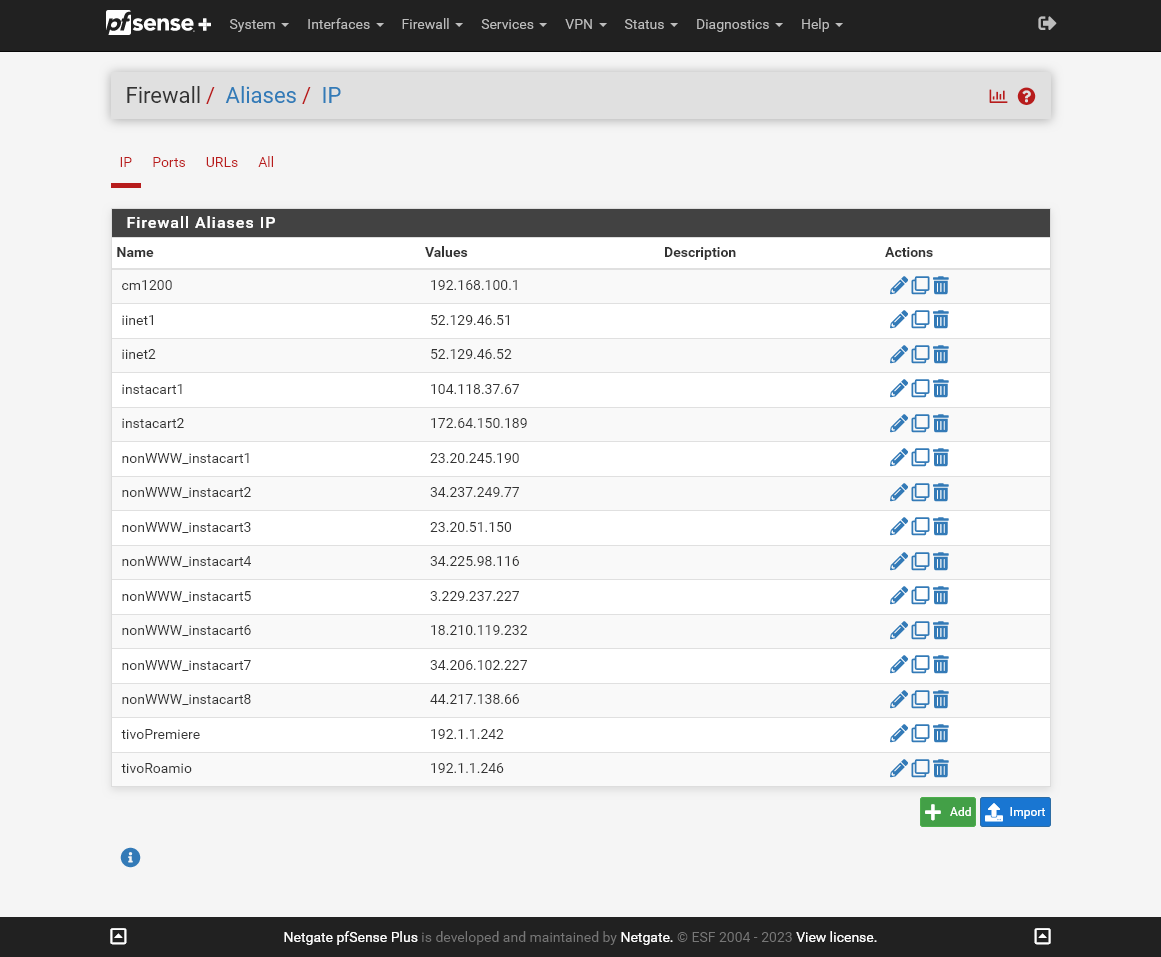
Tivo 1:
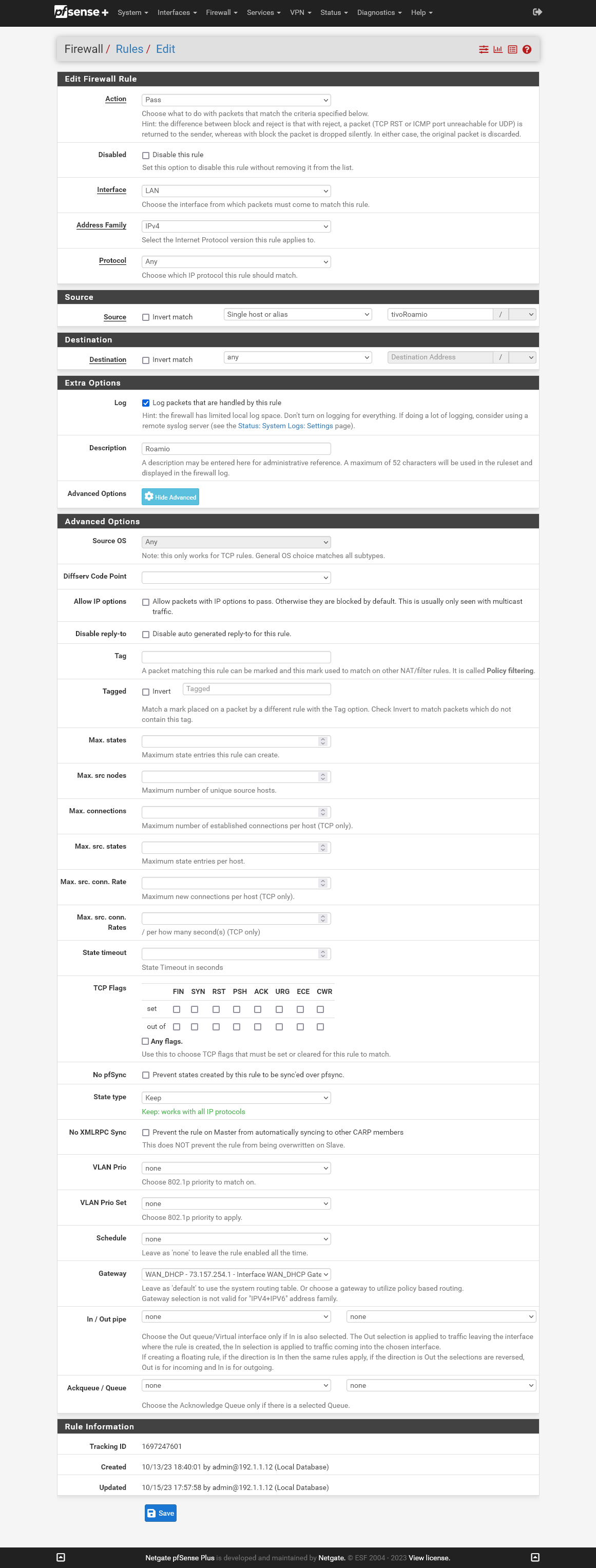
Tivo 2:
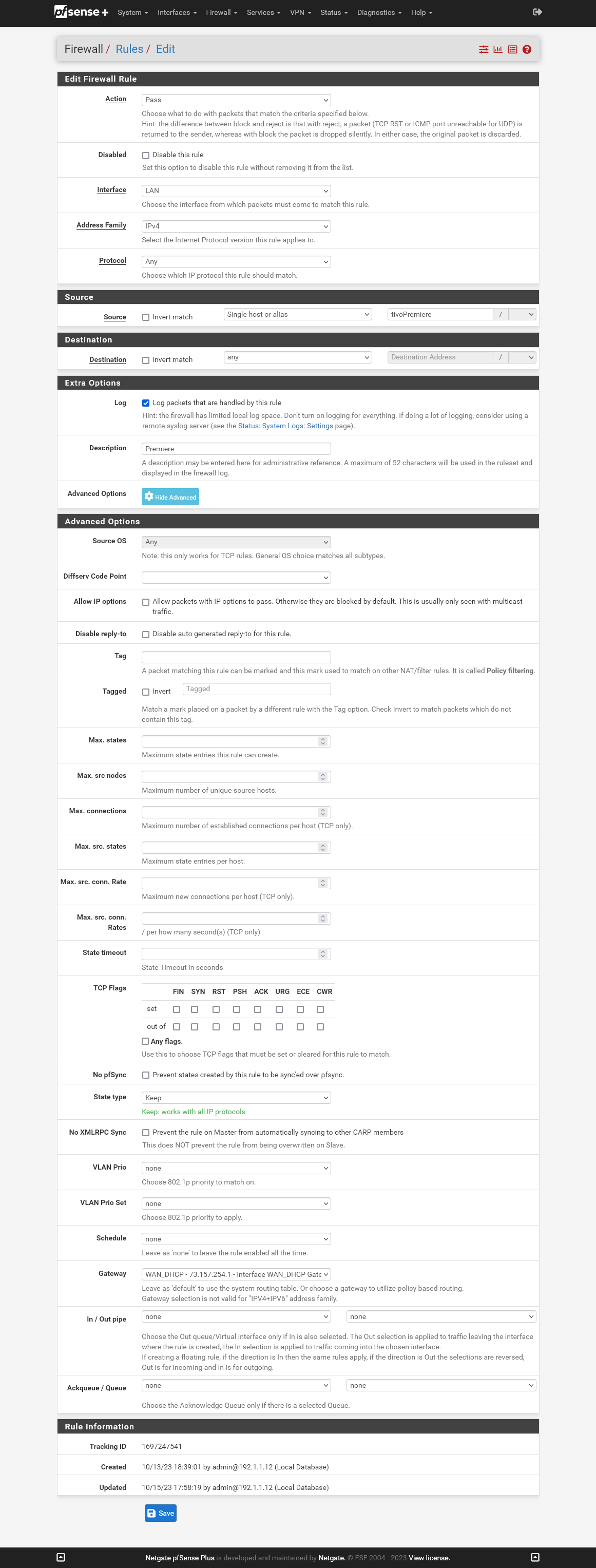
Allow everything:
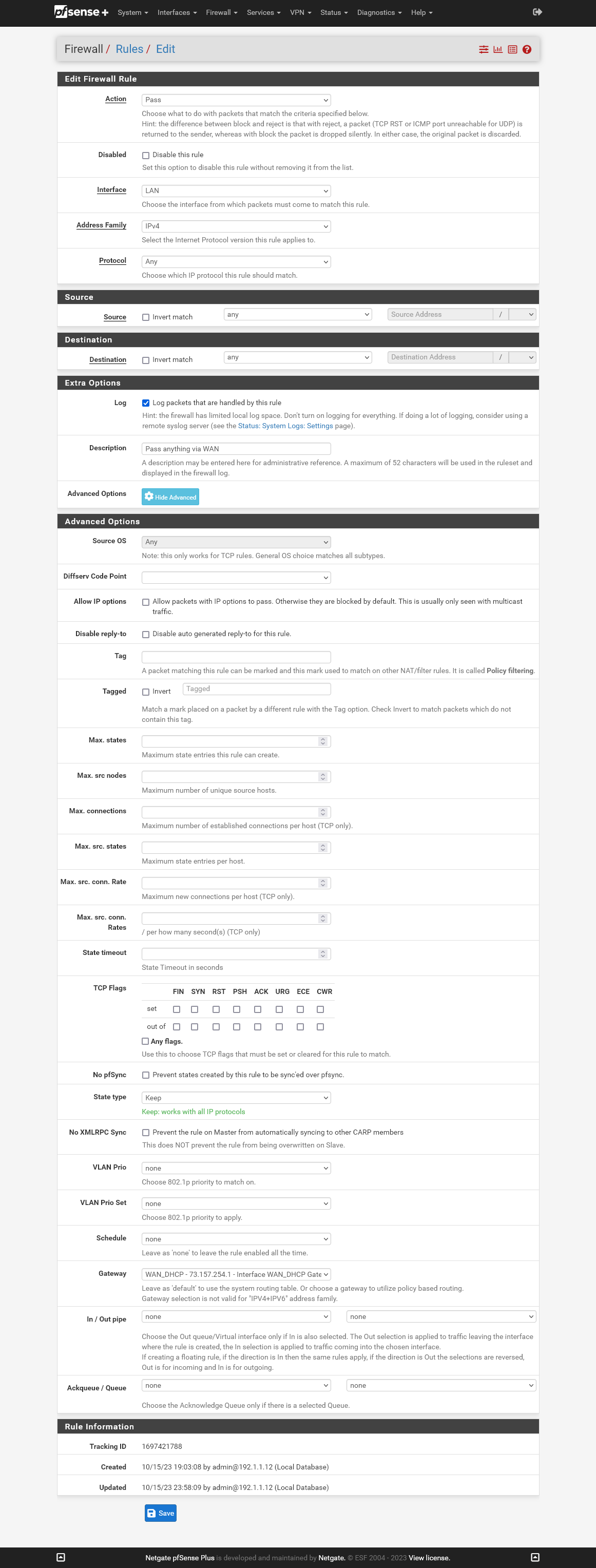
-
I left my router alone overnight and tried it again today.
Bizarrely, the firewall rules now work as expected. My only thought is that there was some stale state information that timed out overnight.
Think my best strategy now is to just leave the router configuration alone and check it periodically.
-
@hspindel said in Firewall rules with Wireguard VPN active:
Think my best strategy now is to just leave the router configuration alone and check it periodically.
Or clear the related states. You can dump the states table at any time from Diagnostics > States
-
I had tried clearing the states multiple times before, and it never fixed the problem.
I think there is some bug in pfSense that does not correctly respond immediately to changed firewall rules.
Regardless, I am at present just happy it is working.
-
@hspindel Glad you got it working, as for a bug though I don't think this is likely, I manage like 8 pfSense boxes in enterprise environments and rule reloads and state clearing always work as expected. Still not sure what caused this though, it does sound buggy but I've never had anything remotely similar happen.
If it happens again be sure to update this thread so we can dig deeper, if there is some bug I'd love to try and get to the bottom of it.
-
Thank you for your help so far.
I will update this thread if I see anything unusual in the future. Kind of unlikely, because once I get a router up and running the way I want it's usually "forget about it except for firmware updates."
On the pfSense boxes you manage, is a VPN active? If not, that could be an important distinction between your setups and mine.
-
@hspindel Yes, on all my boxes actually there are VPNs active, including in production mission critical environments, in fact some have like 30 VPNs setup, some WG, some IPsec, etc..... so I don't really think it was related to that. Either way though glad it's working as expected now!