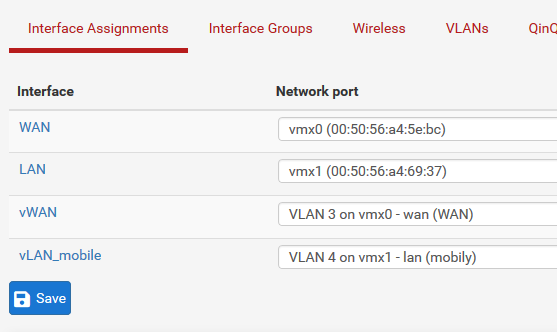
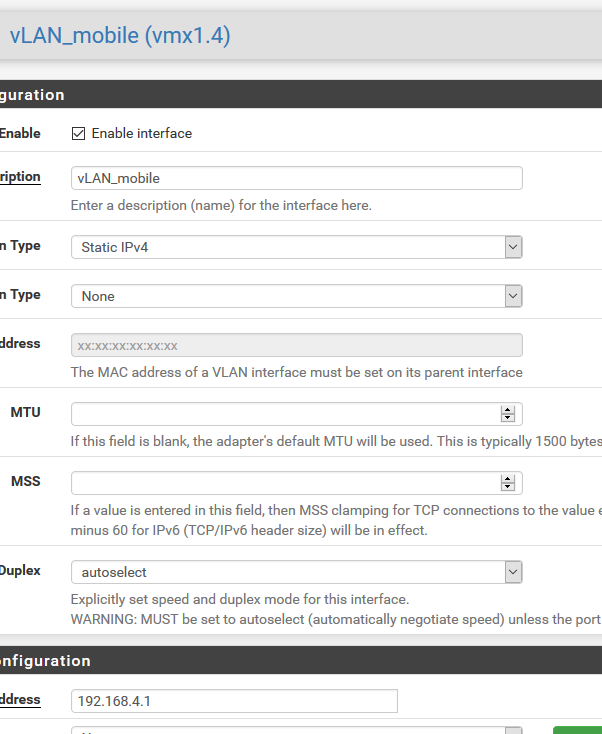
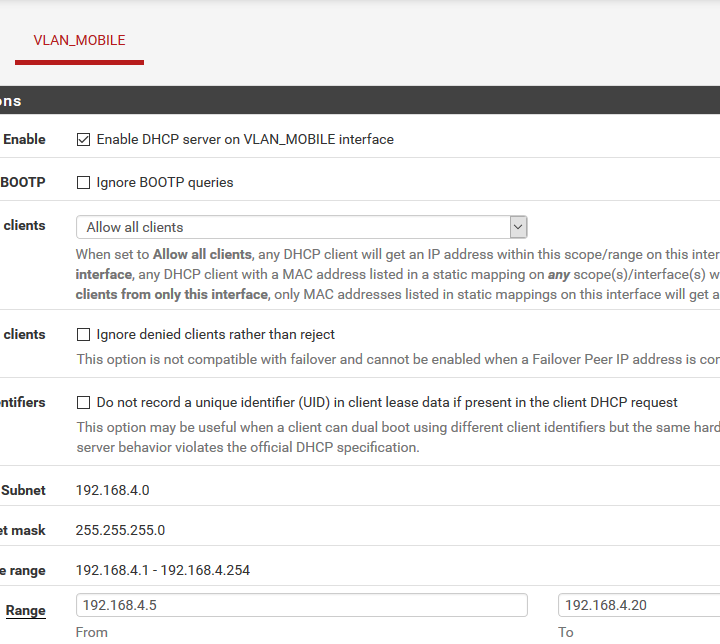
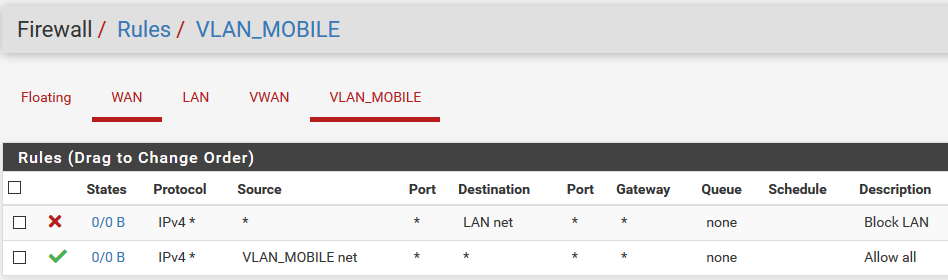
VLAN not getting internet access
-
I'll try to help here as best I can, I think a few questions will help at first though.
- So these are using wifi right? You'll need to be sure the wifi network is set to use the right VLAN; setting that up will vary a lot depending on what wifi router you are using.
- Second, why do you have a VLAN setup for the WAN interface? Is this something your ISP requires? Normally you'd have a single WAN interface and normally a VLAN on that interface is not required. You do NOT need a WAN VLAN for every "LAN" VLAN you create, each network/subnet/VLAN can use the same WAN externally.
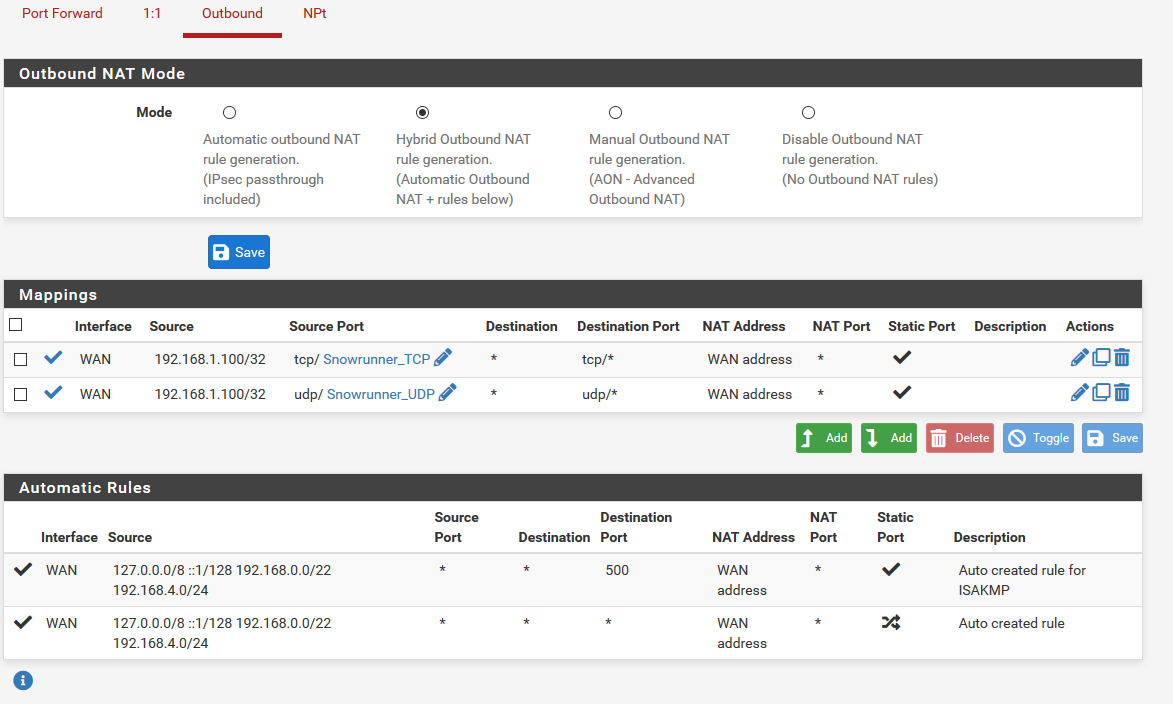
- What are your NAT settings looking like on the outbound NAT tab?
- Can you validate that mobile devices get IPs in the DHCP range you have setup?
Your DHCP setup looks good and your rules should still work if all else is configured right and outbound NAT is setup right.
-
- Yes. The switch is set up like this:
VLAN 2 - local network
VLAN 3 - WAN. One port for the cable from the roof, the other is going into the server. I actually have no idea why it doesn't go directly to the server.
VLAN 4 - wifi. - I don't remember. Must have something to do with virtualization, or so I thought back then. It has the VLAN number associated with it. This is getting even more confusing.
- Yes they do. My phone does at least.
- Yes. The switch is set up like this:
-
@Octopuss said in VLAN not getting internet access:
@JKnott
about 23 hours ago@JKnott I don't understand the rules :( Denying access to WAN means no internet access, right?
I think it's hopeless. I just don't understand anything from the above. Why do you specify the interface in half the rules and just use * in the others?Yes, blocking WAN means no internet.
There are different ways of specifying addresses. * means any address. When I specify the interface, I specify either "address", which means the specific interface address or "net", which means any address within that subnet.
-
@JKnott And does pfSense work on the "what's undefined is blocked" basis or not? As in, do I even need to create rules to block something?
Basically I have a VLAN with DHCP range where all the smartphones (along with stuff I don't want to, but that will be chapter 2) are, but I only want these to access the internet, not the LAN. What do I do?
-
Use something like my rules. My guest WiFi uses a VLAN, which separates guest traffic from my LAN. You set up your access point for a 2nd SSID, which connects to the VLAN. The cell phones would then connect to that 2nd SSID.
-
@JKnott Oh I get it. I don't need any rules when I just throw all the stuff into a new separate subnet. I also completely forgot I was smart enough to buy an AP (Ruckus R610) that can do this.
How about when I want all the system devices to reside in one IP range, but are connected to the wifi? Like the printer downstairs. It's connected to the downstairs AP, but that's in wifi 192.168.4.x subnet. All the "server-like" stuff is in 192.168.2.x. I guess that's not possible.
-
You have to use addresses within the subnet. I'm assuming the printers are in a different subnet from the phones. You can't have the same subnet on different interfaces. For example, my main LAN is 172.16.0.0 /24, but the guest WiFi subnet is 172.16.3.0 /24.
-
@JKnott They are currently in the same subnet, I'm just trying to figure out how to do this, if possible.
The usual server and devices stuff is all in VLAN 2. The AP is plugged into a port that's on VLAN 4. So what are you saying is it's impossible to have one of the clients connected to the AP to somehow end up on the intended subnet?
Or maybe the other way around - if I plug the AP into VLAN 2, is there any way to get smartphones get IPs from the VLAN 4 subnet?Last question is, why do I have to have a tagged port from VLAN 2 (Where pfSense is) in VLAN 4? I tried googling a definition of tagged port and it's a pure confusing mess.
-
- You can't have the same subnet on more than one interface.
- Configure your AP with a 2nd SSID, which then connects to a VLAN.
- Configure pfSense and any managed switches to use the same VLAN.
- Here's the Wikipedia article on VLANs. The tag is what separates the VLAN from the main LAN and other VLANs. You can have up to 4094 VLANs, though your hardware may limit you to far less.
- When you configure that VLAN on pfSense, you then treat it exactly the same as any other interface for DHCP, etc..
-
@JKnott Can you elaborate on point 2? What VLAN should the AP be primarily connected to then, and what do you mean SSID connecting to a VLAN? I am completely lost here.
- I still don't get it. The wiki article is just confusing.
I while ago I found this article https://networkdirection.net/articles/network-theory/taggeduntaggedandnativevlans/ that I thought was what I was looking for, but it made absolutely no sense in the end and I couldn't understand my situation based on the explanation of tagging given there.
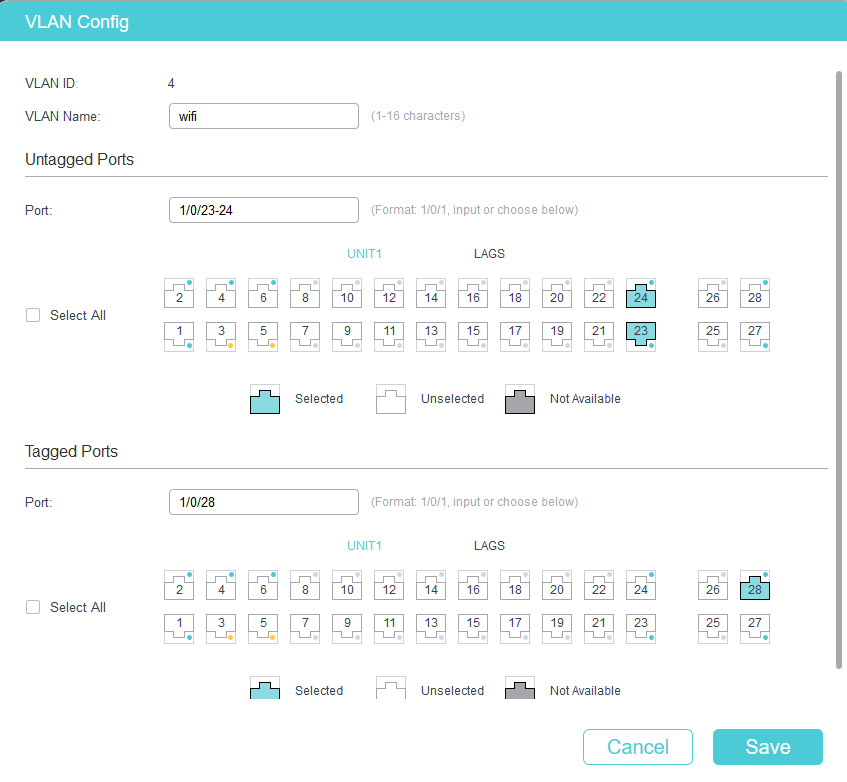
This is the wifi VLAN's settings on the switch.
Port 28 is part of VLAN 2 where all the local network including pfSense is.
Can you explain why I only get connection on the wifi devices when the port 28 is tagged?
- I still don't get it. The wiki article is just confusing.
-
@Octopuss said in VLAN not getting internet access:
Can you explain why I only get connection on the wifi devices when the port 28 is tagged?
How would pfsense know what traffic is what if there was no tag to tell it - hey this traffic is vlan 4.. When more than one network is going to run on the same physical interface/wire.. And you want a device to keep them separate you can have one native vlan, but the others need to be tagged..
Lets say I have 3 networks, X is just on the physical interface on pfsense.. This would be vlan X on my switch, this might just be the default vlan 1 on your switch, or it could be any other vlan you create on the switch and assign to a port, etc. And then 2 other "vlans" Y and Z that I you create on pfsense with which are tagged and ride on the same physical interface that X is on.
So between pfsense and the switch X would be Untagged (U in the drawing) and Y and Z would be Tagged (T in the drawing) to and from the switch and pfsense.
Now the switch knows oh no tag this is vlan X traffic, oh that has Y tag, oh that has Z tag.. If I connect a PC that would only be in one of the vlans xy or z.. Then this would be untagged traffic - because the switch knows hey all traffic in and out of this port is vlan xy or z..
Now if I want to send multiple networks to say another switch on the same wire.. I can only have 1 untagged network, all other traffic would need to be tagged so this other switch knows what is what. you could tag all 3 if you wanted on this connection. As long as both switches know hey expect tagged traffic for specific vlan traffic.
If your AP understands vlans - then its really just like a switch.. Where it knows hey if traffic when I send traffic from more than 1 network I need to tag Y and Z so the switch knows this is traffic on vlan Y or Z..
Maybe this drawing will help?
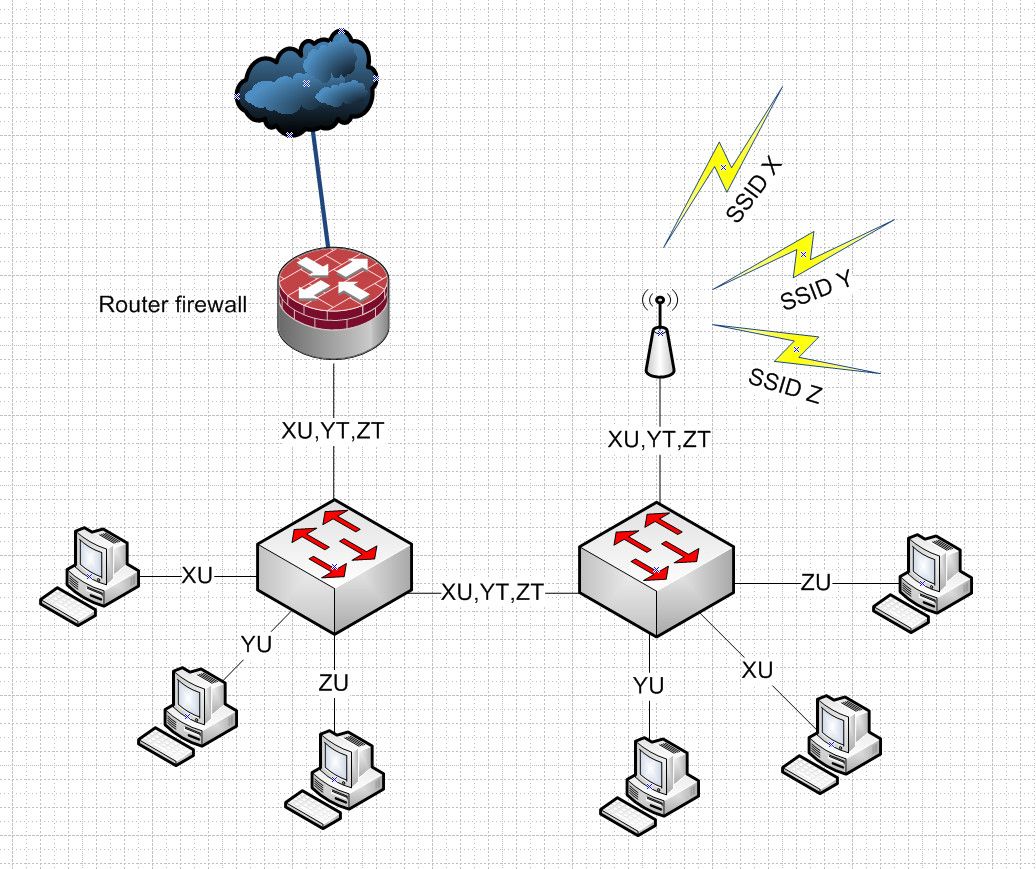
When you carry more than one vlan over the same physical interface or wire.. You have to tag the different vlans.. You can only ever have 1 vlan/network on the wire/interface if its going to be untagged. If you carry more than 1, sure one can be untagged - but the others need to be tagged to let the device know what is what.. You can if you want tag all 3.. But whenever more than one network/vlan flow over the same wire - they can not be all untagged. Or how would pfsense or another switch or an AP know which traffic is in X or Y or Z.
U is untagged and T is tagged in the drawing.
So in the connections between switches, and the connection to the AP.. It doesn't really matter which vlan xy or z is untagged. you just can not have more than 1 untagged network on the same wire. Or you could if you want tag all 3 of these on those connections.
But if pfsense has this X network native just right on the interface then it would need to be untagged. But if you wanted to you could not put a network native on the interface, and create a vlan for X.. And then X would also be tagged talking to and from the switch pfsense is connected too.
Think of it this way.. if I hand you an envelope with say money in it.. And me and you both know your suppose to give that envelope to billy.. We both understand each other.. Now if give you 2 envelopes and say this one is for billy and this one is for susan.. How would you know if both are blank?? But if I label one with susan on it.. Then you would know hey no label for billy, label is for susan..
So I can hand you a bunch of envelopes - no label they go to billy, ones for susan would say susan on them.. Same goes when you hand me envelops back - ones with no label are for billy, ones labeled susan are for susan.
We can than start adding more names.. We both know no label on the envelope its for billy.. But others would need to be labeled to who they belong. Susan or Kevin, or billys brother bob ;)
Now you being the switch.. And someone else hands you as envelope for susan but doesn't label it, say that pc connect to port in vlan Y.. You as the switch will prob label it susan so you can keep track when you put them in the pile to hand out to some other person. Now if your going to hand it to someone else to give to susan that also you give other evelopes for billy and bob, etc. You leave the label on the susan envelope. but when your going to hand it directly to "susan" you can take it out of the envelope. ie no tag.
-
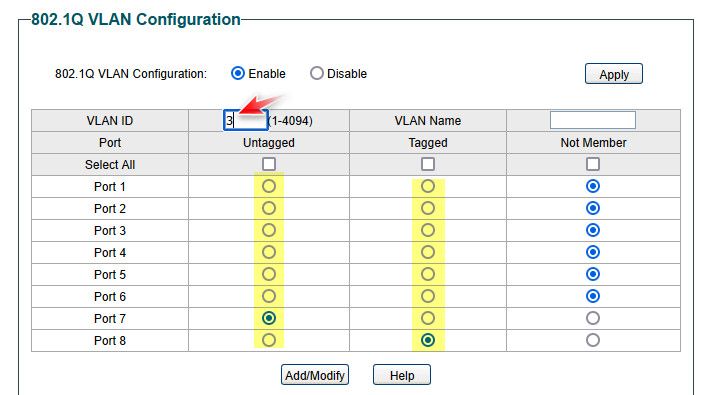
@johnpoz Ok that makes a little more sense but I am still confused. You are talking about tagging VLANs, but I can only tag a specific port on my switch in individual VLAN settings, as per the screenshot.
I can't get past this point in processing the information unfortunately.You must think I am a complete retard and I indeed am, and english not being my native language certainly doesn't help despite me understanding what you write.
-
@Octopuss said in VLAN not getting internet access:
but I can only tag a specific port on my switch in individual VLAN setting
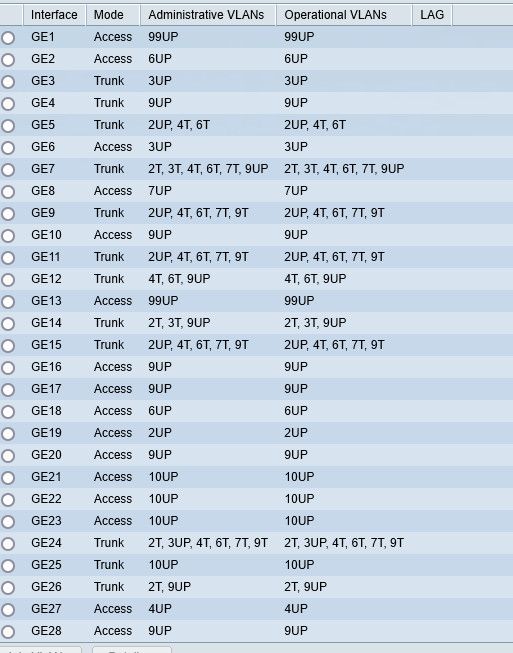
you can tag multiple vlans on any port on any vlan capable switch.. If you could not then the switch would be useless.. Your showing only what is tagged for vlan 4 in that screenshot.
example here is one of my switches.. All the vlan IDs with T on them are tagged.. Ones with U are untagged and the P means that is the pvid set on the port as well.
-
@johnpoz You don't understand (and neither do I, obviously). I can't find anything like "tagging a VLAN" in the GUI of my switch. I only can open the settings for a VLAN and tag individual ports there, but I cannot specify a VLAN or anything.
-
@Octopuss said in VLAN not getting internet access:
@JKnott Can you elaborate on point 2? What VLAN should the AP be primarily connected to then, and what do you mean SSID connecting to a VLAN? I am completely lost here.
Pick a number for the VLAN tag. I use 3 for mine. As I mentioned above, there are over 4000 to choose from. An access point that supports multiple SSIDs will also support VLANs. When you set up the 2nd SSID on your AP, you will tell it what VLAN to use. If you have a managed switch, you will also have to enable that VLAN on the ports connected to the AP and also to pfSense. Your main SSID would normally connect to the main LAN, which means untagged.
-
@Octopuss said in VLAN not getting internet access:
but I cannot specify a VLAN or anything.
You show port 28 tagged on vlan 4.. If you want vlan X also tagged on port 28 then open up vlan X and set it to be tagged on port 28 as well..
Here like this cheap switch... for vlan 3! see the box were I set 3 - I can then put a port as either tagged or untagged on vlan 3..
You don't understand
I have been working with vlans since they have even been a thing... I am quite sure I understand how vlans work ;) hahahaha
-
@johnpoz I meant you didn't understand what I didn't understand. lol
This is probably an extremely simple thing from technical point of view, but different wording across different interfaces and different ways to explain it just prevents me from understanding it.I will have another coffee and try to read it all again. I really feel like an idiot over what's a one click in a GUI somewhere. I mean, jesus.
-
@Octopuss on your switch - how did you get to vlan 4..
Click whatever port you want the vlan 4 to be untagged or tagged in..
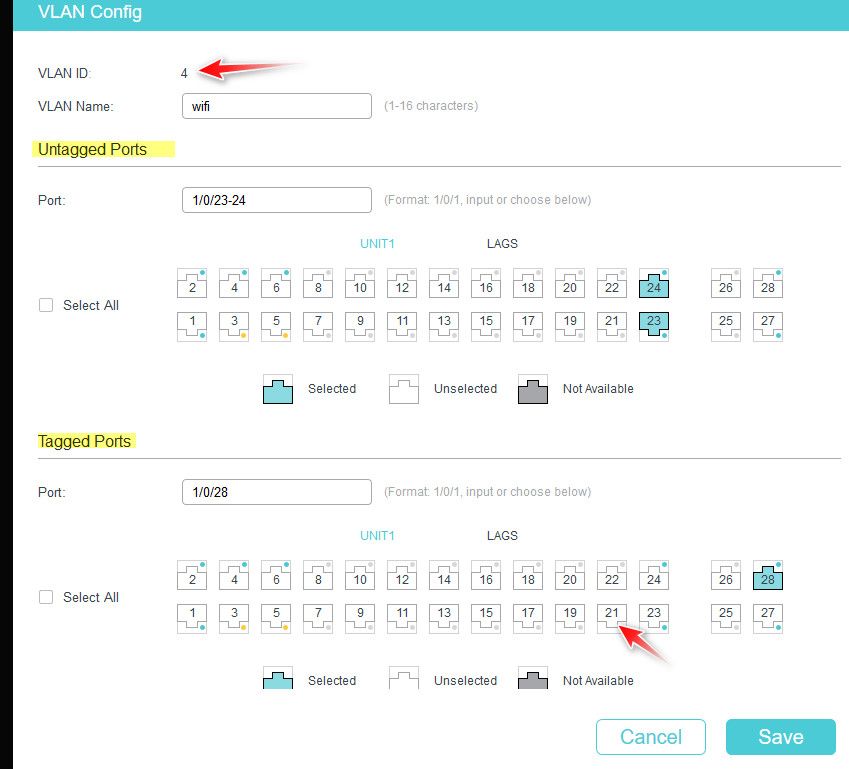
Say for example you wanted vlan 4 to be also tagged on port 21.. Click that little icon.
If you want to edit vlan 3.. Then call up that vlan 3 on your switch and click the buttons you want vlan 3 to be untagged or tagged in.. Or edit the listt port box to do the setting for you..
See how untagged you show 1/0/23-24, and tagged you show 1/0/28 in the boxes
-
@johnpoz Oh you know what? I AM an idiot. I wasn't thinking in the correct direction, or maybe thinking at all and overcomplicating it.
All I'm doing is adding frigging VLAN 4's tag to port 28, and it does not matter what VLAN 28 is in.All the stupid articles I tried reading that were numerous pages long confused the hell out of me and I couldn't think in a simple way. OMG!
edit: Yep, I was kind of thinking about it backwards: Last question is, why do I have to have a tagged port from VLAN 2 (Where pfSense is) in VLAN 4? What a simple shit and I just couldn't wrap my head around it.
-
@Octopuss said in VLAN not getting internet access:
I couldn't think in a simple way.
Which is why I tried to use the envelope example.. Once it clicks yeah you will feel stupid for not getting it before ;)