some services show can't start
-
table <gfwsite> { 124.160.136.236 8.8.8.0/24 8.8.4.0/24 172.217.0.0/16 149.154.0.0/16 1.192.0.0/10 104.237.160.0/19 103.245.0.0/16 103.25.178.0/24 103.53.0.0/16 104.131.0.0/16 104.149.0.0/16 104.244.40.0/21 104.223.0.0/17 172.217.22.0/24 216.58.211.0/24 216.58.192.0/19 216.239.32.0/19 203.208.32.0/19 173.194.0.0/16 170.149.128.0/17 162.249.104.0/21 157.240.0.0/17 157.240.7.0 154.35.0.0/16 154.35.128.0/17 142.4.0.0/19 139.162.0.0/19 128.0.0.0/15 124.248.160.0/19 120.136.32.0/20 118.140.0.0/14 117.56.0.0/16 115.84.64.0/18 115.84.108.0/24 115.68.0.0/16 114.199.74.0/24 113.196.0.0/16 109.201.128.0/19 108.171.240.0/20 108.171.192.0/19 108.177.0.0/17 107.191.108.0/22 107.178.192.0/18 106.187.64.0/18 74.125.0.0/16 104.16.0.0/12 104.27.144.0/20 209.85.128.0/17 192.229.220.0/24 64.233.160.0/19 64.13.192.0/18 93.184.220.0/24 130.158.0.0/16 8.0.0.0/8 208.67.222.0/24 74.82.0.0/18 216.73.80.0/20 216.252.220.0/22 209.107.176.0/20 209.107.182.0/23 208.81.188.0/22 208.68.108.0/22 207.223.160.0/20 199.223.232.0/21 199.192.112.0/22 192.178.0.0/15 192.158.28.0/22 192.104.160.0/23 185.150.148.0/22 185.25.28.0/23 173.255.112.0/20 172.253.0.0/16 172.110.32.0/21 172.102.8.0/21 162.222.176.0/21 162.216.148.0/22 146.148.0.0/17 142.250.0.0/15 130.211.0.0/16 108.170.192.0/18 108.59.80.0/20 107.167.160.0/19 104.196.0.0/14 104.154.0.0/15 104.133.2.0/23 104.0.0.0/8 74.114.24.0/21 72.14.192.0/18 70.32.128.0/19 66.249.64.0/19 66.102.0.0/20 35.204.0.0/15 35.200.0.0/14 35.192.0.0/13 35.184.0.0/13 23.251.128.0/19 23.236.48.0/20 168.95.0.0/16 4.0.0.0/8 204.194.232.0/24 203.80.64.0/18 72.21.81.0/24 192.0.32.0/22 192.0.43.0/24 208.77.188.0/22 69.195.0.0/16 104.244.0.0/16 185.45.6.0/23 192.133.76.0/22 199.16.156.0/22 216.58.217.0/24 216.58.216.0/24 172.217.3.0/24 1.1.1.0/24 } gfwsite = "<gfwsite>" table <hack> persist file "/var/db/aliastables/hack.txt" hack = "<hack>" table <mycnip> { 2602:fed6:7021::/48 2a0d:2416:511::/48 2406:846:f101::/48 2a10:2f05:100::/48 2a12:3fc8::/48 2a12:3fc8:8000::/48 2a0f:85c2:100::/48 } mycnip = "<mycnip>" table <mydns> { 2602:fed6:7021::8 } mydns = "<mydns>" table <myimap> { 195.88.45.150 72.52.82.17 23.129.32.90 91.228.53.165 134.195.121.55 185.154.154.130 36.40.0.0/13 } myimap = "<myimap>" table <mymail> { 2602:fed6:7021::2 } mymail = "<mymail>" table <myv6cn> { 2602:fed6:7021::/48 2a0d:2416:511::/48 2406:846:f101::/48 2a10:2f05:100::/48 } myv6cn = "<myv6cn>" table <myweb> { 2602:fed6:7021::3 } myweb = "<myweb>" table <ns1> { 185.112.145.12 45.76.37.222 204.42.254.5 174.37.196.55 208.43.71.243 192.237.164.47 159.65.168.111 69.164.207.210 66.175.221.62 178.79.148.169 45.76.136.88 45.32.180.186 93.95.226.52 185.112.145.13 93.95.226.53 79.98.145.34 202.5.31.48 35.229.160.89 45.79.211.52 106.186.121.42 139.162.211.108 128.199.213.165 45.63.94.117 45.77.29.133 119.252.20.56 88.198.106.11 109.233.63.63 188.165.175.200 109.233.59.138 66.232.125.112 66.232.97.8 66.175.212.236 198.101.252.231 93.95.224.6 109.233.58.138 198.27.126.130 103.13.122.142 202.157.182.142 193.70.13.218 35.169.39.140 216.117.186.93 195.24.128.164 195.24.156.218 84.201.39.17 } ns1 = "<ns1>" table <spam_1> persist file "/var/db/aliastables/spam_1.txt" spam_1 = "<spam_1>" table <v401> { 192.168.101.3 192.168.101.5 192.168.101.6 } v401 = "<v401>" table <vps> { 91.228.53.165 72.52.82.17 23.129.32.90 2602:fed6:7020:a::/64 195.88.45.0/24 2602:fed6:7022:d::/64 2001:67c:12a0:8007::2 2001:67c:12a0:ad::2 2602:fed6:7020::/48 2602:fed6:7023::/48 2602:fed6:7025::/48 185.154.154.130 2a0d:2416:512::/48 2602:fed9:ca1:a::/64 134.195.121.55 2602:fed6:7022::/48 2a0d:2416:512:a::/64 2602:fed9:ca1::/48 2602:fed6:fc0::/48 2406:846:f100::/48 2602:fd50:20:9::/64 2a07:8dc1:20:74::/64 2602:fed6:7020:ca::/64 194.156.188.65 2a0d:2416:510::/48 fe80::/10 2a07:8dc0:19:18c::1 185.10.17.74 2602:fe69:217::/64 104.224.52.122 2602:fed6:7025::/48 2a0d:2416:513:a::/64 10.18.3.0/24 210.173.170.254 198.8.58.55 116.163.46.146 2406:846:13:d::1 2a06:8184:1:21::/64 181.215.32.156 2a0f:85c1:101::/48 2a0d:2416:510::/44 } vps = "<vps>" table <vps1> { 194.28.99.172 } vps1 = "<vps1>" GWWAN_DHCP6 = " route-to ( pppoe2 fe80::7a1d:baff:fecf:2d59%pppoe2 ) " GWWAN_PPPOE = " route-to ( pppoe2 10.1.72.1 ) " GWwg0 = " " GWFMT = " route-to ( tun_wg1 2602:fed6:7020:ca:: ) " GWFMTZHU = " route-to ( tun_wg2 2602:fed9:ca1:b::10 ) " GWFMTv = " route-to ( tun_wg1 10.10.2.1 ) " GWwg0GW = " " GWwg3GW = " route-to ( tun_wg2 10.15.1.1 ) " GWOPT7GW = " route-to ( tun_wg5 10.17.2.1 ) " GWOPT7GWv6 = " route-to ( tun_wg5 2602:fed6:7025:a::10 ) " GWFRVPN_VPNV6 = " route-to ( ovpnc12 2a0d:2416:512:a::2 ) " GWFRVPN_VPNV4 = " route-to ( ovpnc12 10.16.0.1 ) " GWDEVPN_VPNV4 = " " GWDEVPN_VPNV6 = " " GWFMTVPN_VPNV4 = " " GWFMTVPN_VPNV6 = " " GWDEwg = " route-to ( tun_wg4 2602:fed6:7022:b::10 ) " GWDEwgGW = " route-to ( tun_wg4 10.11.0.1 ) " GWZHUVP_VPNV6 = " route-to ( ovpnc5 2602:fed9:ca1:a::2 ) " GWZHUVP_VPNV4 = " route-to ( ovpnc5 10.15.0.1 ) " GWSEAVPN_VPNV6 = " " GWSEAVPN_VPNV4 = " " GWUKWG = " route-to ( tun_wg3 10.18.1.1 ) " GWUKWGv6 = " route-to ( tun_wg3 2a0d:2416:513:a::10 ) " GWvp = " route-to { ( ovpnc12 10.16.0.1 ) ( ovpnc5 10.15.0.1 ) } round-robin " GWFRVP = " route-to { ( ovpnc12 10.16.0.1 ) } " GWEUv4 = " route-to { ( ovpnc12 10.16.0.1 ) } " GWUSv4 = " route-to { ( ovpnc5 10.15.0.1 ) } " set loginterface vtnet1 set skip on { pfsync0 } /tmp/rules.debug:194: syntax error tonatsubnets = "{ 127.0.0.0/8 ::1/128 10.50.0.0/16 }" /tmp/rules.debug:593: syntax error pfctl: Syntax error in config file: pf rules not loaded -
Nothing there tells me what those failing lines are.
-
@stephenw10
That's all the command displays.23.09-RC (amd64)
built on Fri Oct 27 9:51:00 CST 2023
FreeBSD 14.0-CURRENTIn this version, ipv4 routing on the WAN interface does not work at all.
-
What command? We just need to see what is on those lines in the rules.debug file.
-
-
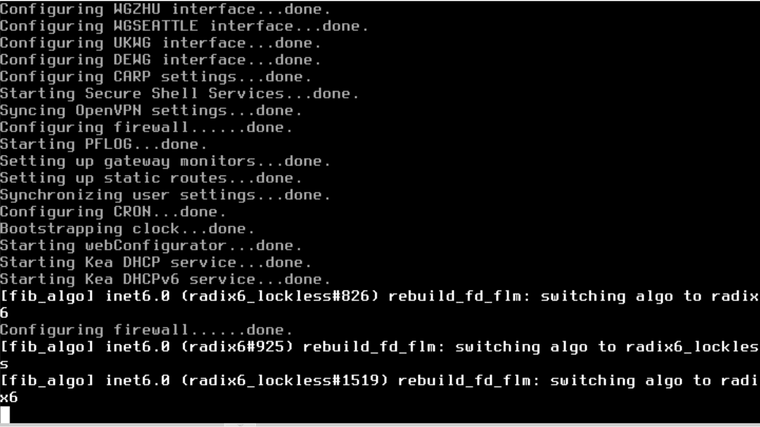
That is the result of running pfctl -v -f /tmp/rules.debug in the previous version.
-
That looks like a screenshot of the boot logs.
We need to see what is on lines 194 and 593 in rules.debug. Since that is the error shown.
-
no found lines 194 and 593 in rules.debug on that time.
-
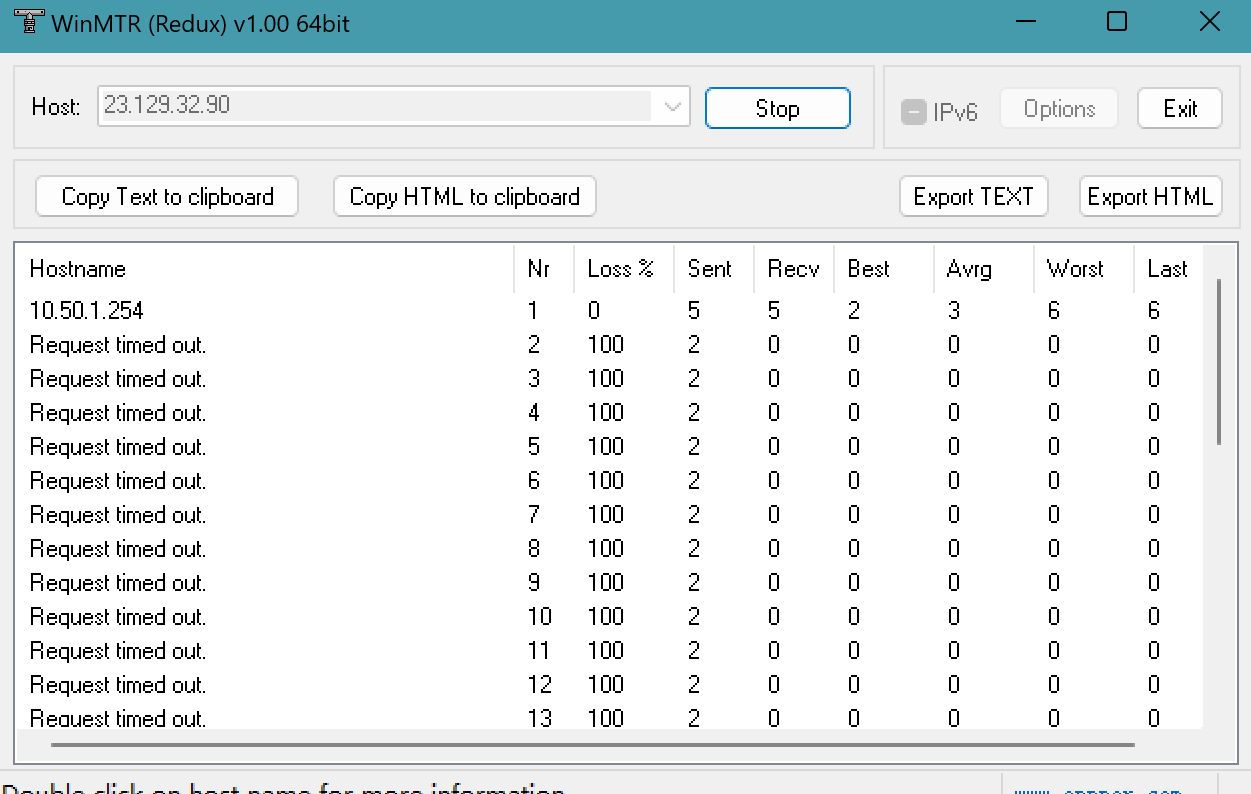
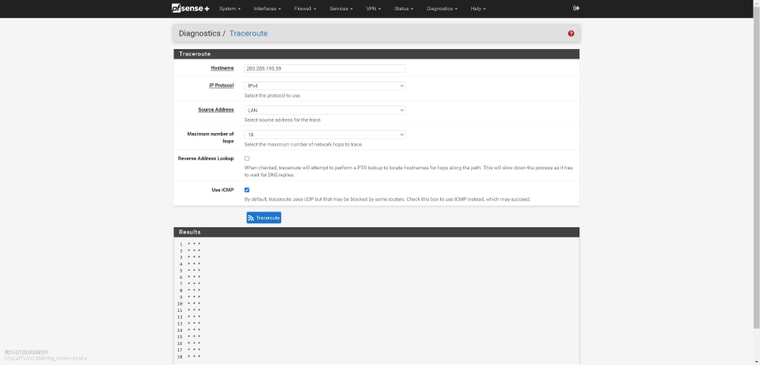
v23.09 WAN route is null,WAN routing is not accessible at all from LAN
-
-
No default IPv4 route?
-
i have setup default ipv4 route via wg0, but some ips setup via ISP WAN. now it is can't via WAN route out.
-
So you have added some static routes via WAN and traffic is not following those? How are you adding them?
Does it go out via the wg gateway incorrectly?
-
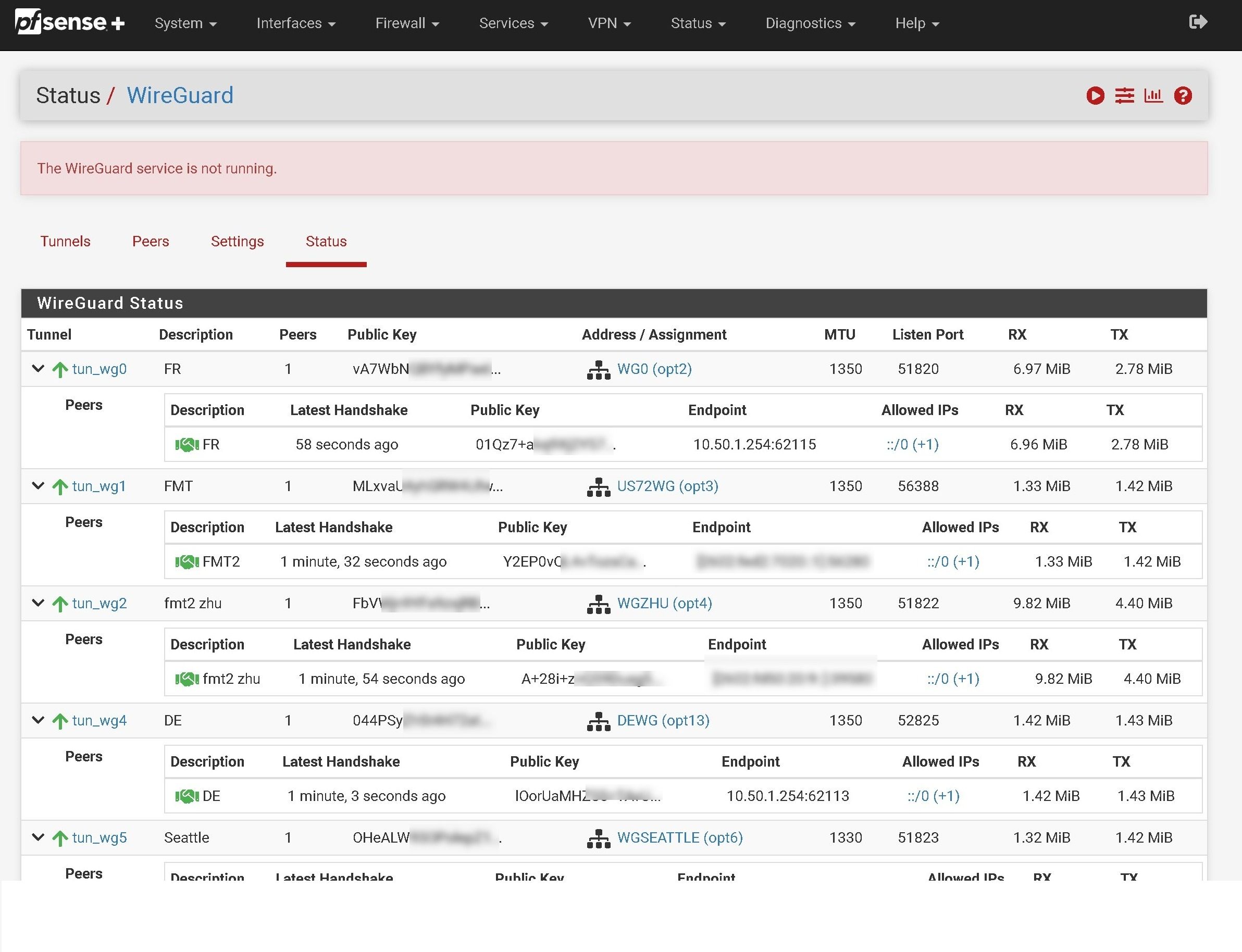
I am having similar issues on the 2.7.1 concerning wireguard. I am using as a lab environment at home. It is a fresh install in which I restored from a previous backup. The wireguard service does not start and I am unable to manually start it.
I am a bit concerned about updating our company firewalls which are currently running on 23.05.1 since we heavily rely on wireguard tunnels. Quite a few sites are quite far away to drive if we face a major failure.
The log includes the following errors:
Nov 19 17:30:28 php-cgi 467 rc.bootup: The command '/sbin/route -n6 get 'default' 2>/dev/null | /usr/bin/egrep 'flags: <.*PROTO.*>'' returned exit code '1', the output was '' Nov 19 17:30:36 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: The command '/sbin/route -n6 get 'default' 2>/dev/null | /usr/bin/egrep 'flags: <.*PROTO.*>'' returned exit code '1', the output was '' Nov 19 17:30:36 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Applied package default settings as necessary. Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed Unbound ACL group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed Unbound ACL group (WireGuard). Nov 19 17:30:35 check_reload_status 432 Syncing firewall Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed interface group (WireGuard). Nov 19 17:30:35 check_reload_status 432 Syncing firewall Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed interface group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed earlyshellcmd(s). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed earlyshellcmd(s). Nov 19 17:30:35 kernel tun_wg0: link state changed to UP Nov 19 17:30:35 kernel wg1: changing name to 'tun_wg0' Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Applied package default settings as necessary. Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed Unbound ACL group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed Unbound ACL group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed interface group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed interface group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed earlyshellcmd(s). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed earlyshellcmd(s). Nov 19 17:30:35 kernel wg0: changing name to 'tun_wg1' Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Applied package default settings as necessary. Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed Unbound ACL group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed Unbound ACL group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed interface group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed interface group (WireGuard). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed earlyshellcmd(s). Nov 19 17:30:35 php_wg 82338 /usr/local/pkg/wireguard/includes/wg_service.inc: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed earlyshellcmd(s). Nov 19 17:30:35 kernel tun_wg0: link state changed to DOWN Nov 19 17:30:34 kernel tun_wg1: link state changed to DOWN Nov 19 17:30:34 php-fpm 18459 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] Applied package default settings as necessary. Nov 19 17:30:34 php-fpm 18459 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed Unbound ACL group (WireGuard). Nov 19 17:30:34 php-fpm 18459 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed Unbound ACL group (WireGuard). Nov 19 17:30:34 php-fpm 18459 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed interface group (WireGuard). Nov 19 17:30:34 php-fpm 18459 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed interface group (WireGuard). Nov 19 17:30:34 check_reload_status 432 Syncing firewall Nov 19 17:30:34 php-fpm 18459 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed earlyshellcmd(s). Nov 19 17:30:34 check_reload_status 432 Syncing firewall Nov 19 17:30:34 php-fpm 18459 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed earlyshellcmd(s). Nov 19 17:30:34 php-fpm 18459 /rc.start_packages: Restarting/Starting all packages. Nov 19 17:30:43 php-fpm 86806 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] Applied package default settings as necessary. Nov 19 17:30:43 php-fpm 86806 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed Unbound ACL group (WireGuard). Nov 19 17:30:43 php-fpm 86806 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed Unbound ACL group (WireGuard). Nov 19 17:30:43 php-fpm 86806 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed interface group (WireGuard). Nov 19 17:30:43 php-fpm 86806 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed interface group (WireGuard). Nov 19 17:30:43 check_reload_status 432 Syncing firewall Nov 19 17:30:43 php-fpm 86806 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] Installed earlyshellcmd(s). Nov 19 17:30:43 check_reload_status 432 Syncing firewall Nov 19 17:30:43 php-fpm 86806 /rc.start_packages: Configuration Change: (system): [pfSense-pkg-WireGuard] De-installed earlyshellcmd(s). Nov 19 17:30:43 php-fpm 86806 /rc.start_packages: Restarting/Starting all packages. Nov 19 17:30:42 syslogd kernel boot file is /boot/kernel/kernel Nov 19 17:30:42 syslogd exiting on signal 15 Nov 19 17:30:42 kernel done.Interesting is that everything runs fine as soon as I dis- and re-enable one of the wireguard interfaces. Maybe that is some kind of help?
-
Hmm, the only thing that actually looks like an error there is that route command and that could be because it's run at boot.
What new errors do you see if you try to start the service after boot?
What if you manually run:
/sbin/route -n6 get 'default'Steve
-
@stephenw10
First of all thanks for your almost instant reply :-)@stephenw10 said in some services show can't start:
What if you manually run: /sbin/route -n6 get 'default'
route: route has not been found: No error: 0We do not have a default gateway IPv6 set though - we solely use IPv4 for our uplinks.
@stephenw10 said in some services show can't start:
What new errors do you see if you try to start the service after boot?
Actually none in the logs at least and none in the gui as well. Do you want me to check out a certain log?Interesting enough is that wireguard is actually working and I can ping the wg host on the other side. Pfsense just doesn't bring up the gateway for the static routes since the wireguard service is down.
[2.7.1-RELEASE][admin@labgate]/root: ps aux | grep php_wg root 63787 0.0 0.1 12752 2388 0 S+ 21:07 0:00.00 grep php_wg [2.7.1-RELEASE][admin@labgate]/root: -
Update on the wirguard issue:
I am pretty sure I hit bug #14613 (https://redmine.pfsense.org/issues/14613).
The wireguard gui part is not responsive and cannot be started.
[2.7.1-RELEASE][admin@labgate]/root: fstat /var/run/wireguardd.pid USER CMD PID FD MOUNT INUM MODE SZ|DV R/W NAME root dpinger 59313 10 /var/run 57 -rw-r--r-- 5 rw /var/run/wireguardd.pid root dpinger 58892 10 /var/run 57 -rw-r--r-- 5 rw /var/run/wireguardd.pid root dpinger 58557 10 /var/run 57 -rw-r--r-- 5 rw /var/run/wireguardd.pidAs soon as I do a
[2.7.1-RELEASE][admin@labgate]/root: /usr/local/bin/php_wg -f /usr/local/pkg/wireguard/includes/wg_service.inc stopI can start the wireguard gui through the webinterface and php_wg is running:
[2.7.1-RELEASE][admin@labgate]/root: ps aux | grep php_wg root 61681 0.0 2.3 68272 46144 - Ss 21:47 0:00.06 php_wg: WireGuard service (php_wg) root 23988 0.0 0.1 12752 2392 0 S+ 21:51 0:00.00 grep php_wg -
Ah, interesting. But you only saw this after upgrading to 2.7.1?
This should probably be in a new thread.
-
@stephenw10
Actually it is a fresh install of 2.7.0 and I restored from a backup. Since I immediately updated to 2.7.1 I cannot really tell. Everything worked until the first reboot… -
Ah, well it would be interesting to test that if you can. If this is a new issue in 2.7.1 it's probably not the same as the one you linked to.