Unresolvable source alias after upgrade to 23.09
-
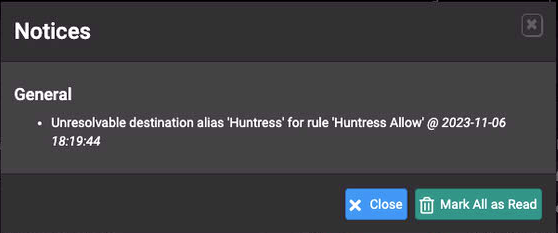
I am also having simaler problem after updating. I have created a Custom Alias called Huntress and use the below URL to pull URl's from my GitHub. I get an error that says "Unresolvable destination alias 'Huntress' for rule 'Huntress Allow'". This rule was working before I upgraded (Previous v23.05.1).
https://raw.githubusercontent.com/csardoss/pflist/main/huntrss.io_list.txt
-
re: ZFS filling the drive:
https://forum.netgate.com/topic/181961/netgate-4100-out-of-diskbectl list
bectl destroy auto-default-20230629155043after freeing space, one can revert and re-upgrade:
https://docs.netgate.com/pfsense/en/latest/backup/zfsbe/loader.html -
Don't want to hijack the troubleshooting here, but just wanted to chime in that the exact same thing happened on my device after doing the upgrade to 23.09 as well. I get the error on all my regular url aliases, but not on my url table ones. Seems like this is happening to multiple people. (No pfBlockerNG here either). The aliases themselves update just fine, seems like it is just the firewall not able to get them properly.
-
@LinkP said in Unresolvable source alias after upgrade to 23.09:
Unresolvable source alias
FWIW they have four fixes for aliases:
https://docs.netgate.com/pfsense/en/latest/releases/23-09.html#aliases-tables¯\_(ツ)_/¯
Edit: meaning the code changed, may have broken something
-
Someone with this can file a report at redmine.pfsense.org
-
@csardoss said in Unresolvable source alias after upgrade to 23.09:
I am also having simaler problem after updating. I have created a Custom Alias called Huntress and use the below URL to pull URl's from my GitHub. I get an error that says "Unresolvable destination alias 'Huntress' for rule 'Huntress Allow'". This rule was working before I upgraded (Previous v23.05.1).
https://raw.githubusercontent.com/csardoss/pflist/main/huntrss.io_list.txt

Got the same error when my Alias was using URL (IPs). Then I change TYPE from URL (IPs) to URL Tables (IPs) and error gone.
-
Reported here: https://redmine.pfsense.org/issues/14947
-
S SteveITS referenced this topic on
-
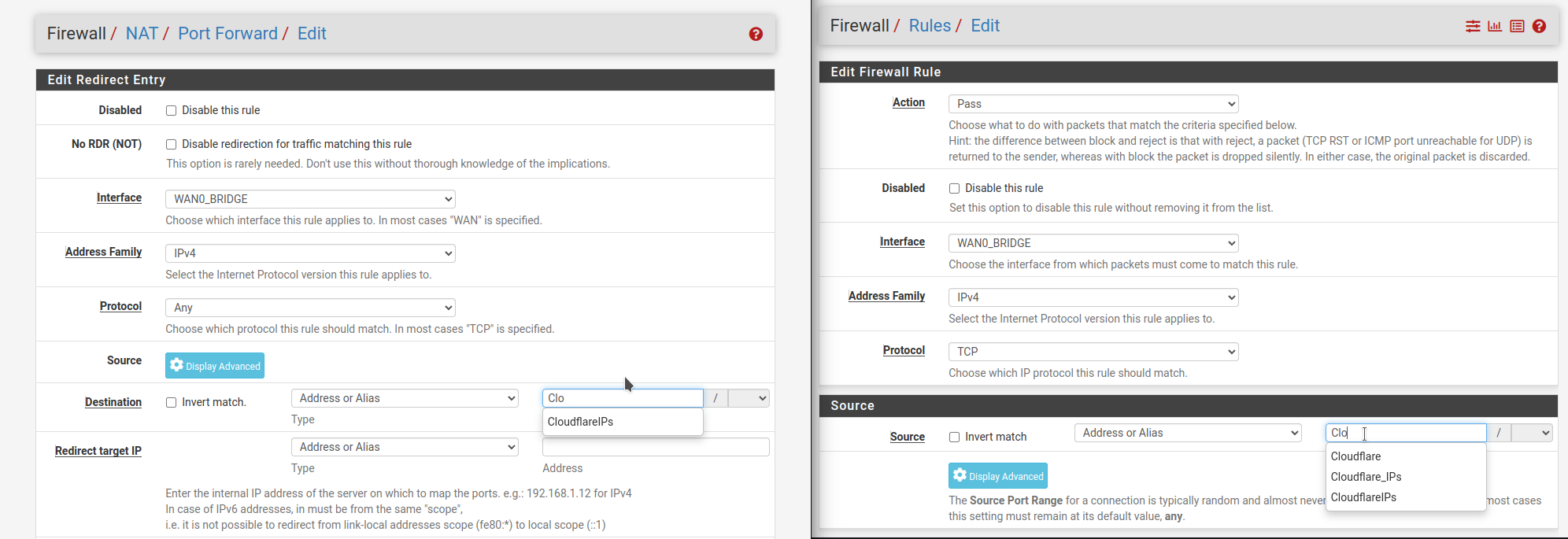
Same issue here. URL Aliases can no longer be selected when creating a NAT rule, but can be selected when creating a firewall rule.
We had a NAT rule allowing only Cloudflare to access our on-prem webserver, which was broken by the update. In the meantime we have created a new alias with the IP's entered manually rather than pulling from https://www.cloudflare.com/ips-v4
Please could this be added to breaking changes here: https://docs.netgate.com/pfsense/en/latest/releases/23-09.html
-
Hi,
I don't have any problems like that on any of my Alias.
What is the different between "URL (IPs)" and "URL Table (IPs) in the Alias on the TYPE?This is an example of my Cloudflare Alias I use.
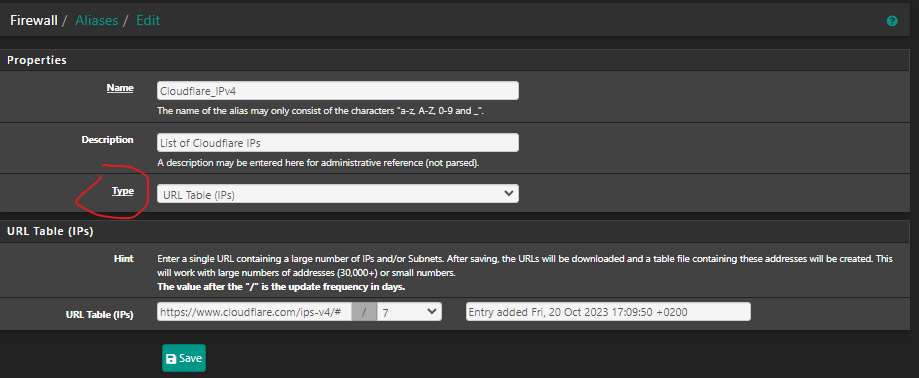
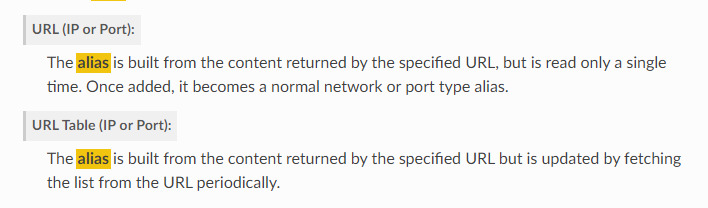
EDIT: Found it :)
-
@MoonKnight Ah, yes! URL Table(IPs) work, URL (IPs) does not!
Difference is explained here: https://docs.netgate.com/pfsense/en/latest/firewall/aliases.html#url-aliases
That's a much better workaround, thanks!
-
There's a patch in the above redmine so someone can test this by using System Patches and the ID in the redmine, a6cf534d0fa0297547f1e587a12729f9d7066bae.
-
@SteveITS This patch worked for me. Thank you
-
The patch works for me, too. Thanks for the quick turnaround.
-
I would think it would show up in a System Patches package update in the next week or two. Another reason I wait a week or two to upgrade...
 Jim usually posts in https://forum.netgate.com/category/16/pfsense-packages.
Jim usually posts in https://forum.netgate.com/category/16/pfsense-packages.I didn't have anything to do with the patch, I just posted it for y'all. If you set up a redmine account you can Watch an open case for updates.
re: table aliases, they also can have over 3000 entries.
-
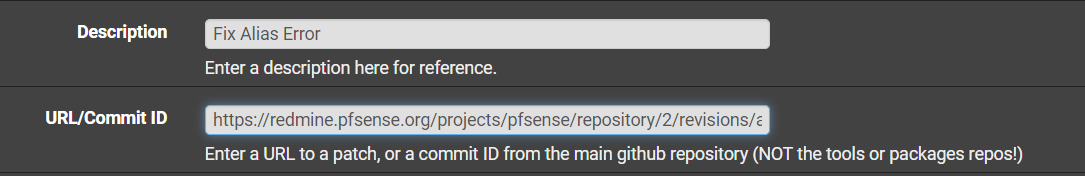
@LinkP How do you apply the patch using System Patches? I added the url https://redmine.pfsense.org/projects/pfsense/repository/2/revisions/a6cf534d0fa0297547f1e587a12729f9d7066bae to a custom patch, but it fails. What am I missing?
-
@infamousbug Just use the ID there: a6cf534d0fa0297547f1e587a12729f9d7066bae
There's a URL for the actual patch file somewhere in Github but it's easier to use the ID.
-
@infamousbug, as @SteveITS has pointed out, you only need use the commit ID. The patch system knows to use the correct Github repo.
I added a description of
Support URL IP aliases in alias_expand()that I gleaned from the commit and enabled the Auto Apply checkbox before I saved it.Once you have fetched and applied the patch, you will need to reload the firewall. I disabled and re-enabled my rule that used the affected alias to trigger the Apply Changes button to appear.
-
@SteveITS said in Unresolvable source alias after upgrade to 23.09:
@infamousbug Just use the ID there: a6cf534d0fa0297547f1e587a12729f9d7066bae
There's a URL for the actual patch file somewhere in Github but it's easier to use the ID.